Leaderboard
Popular Content
Showing content with the highest reputation since 02/03/2026 in all areas
-
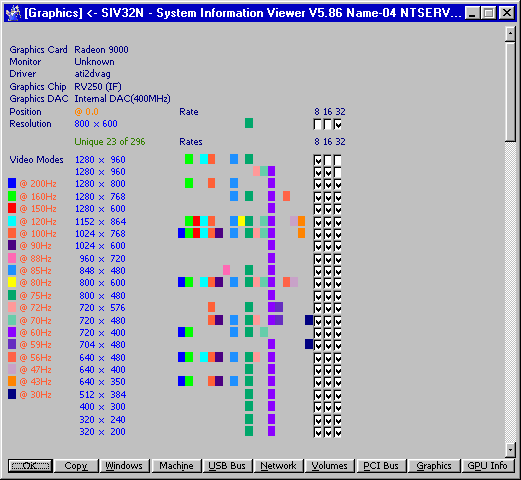
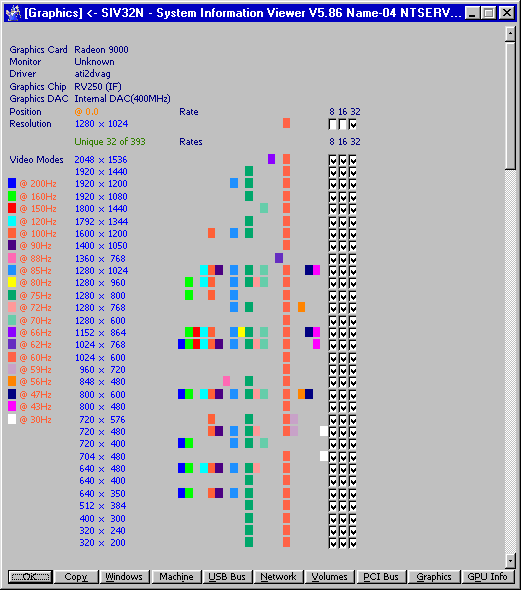
All revisions (ALPHA/I386/MIPS/PPC) of Windows NT 4.0 and Windows NT 3.51 has issue with maximum possible total video mode count limit and it is around 296 modes. Any mode provided by driver above 296 will be cutted down. It is not depended on driver issue, this bug is inside Windows NT system itself. Windows 2000 and later does not have such issue. Here it is a binary patch for Windows NT 4.0 (I386, any SP/edition, language) for SYSTEM32\WIN32K.SYS : Change 0x68 0xB8 0x00 0xFF 0x00 0x00 0x6A to 0x68 0xB8 0x00 0xFF 0x03 0x00 0x6A Change 0x68 0xB8 0x00 0xFF 0x00 0x00 0xFF to 0x68 0xB8 0x00 0xFF 0x03 0x00 0xFF Recalculate checksum, f.e. EDITBIN.EXE WIN32K.SYS /RELEASE Here it is a binary patch for Windows NT 3.51 (I386, any SP/edition, language) for SYSTEM32\WINSRV.DLL : Change 0x68 0xB8 0x00 0xFF 0x00 0x00 0xA1 to 0x68 0xB8 0x00 0xFF 0x03 0x00 0xA1 Change 0x68 0xB8 0x00 0xFF 0x00 0x00 0xFF to 0x68 0xB8 0x00 0xFF 0x03 0x00 0xFF Recalculate checksum, f.e. EDITBIN.EXE WINSRV.DLL /RELEASE This will increase total limit to 1190 modes. Below are results in screenshots, before and after.4 points
-
I agree as a general off-topic observation that while you do, of course, need to have a general awareness of security and privacy issues when working online, there's really no need to be paranoid about it.3 points
-
Unapplicable legal snippets. msfn.org is an international forum, not a USA forum. My Ancient Version of Kaspersky is definitely not an unlawful program for me or for the great majority here at msfn.org. Why don't you wear a head scarf in your msfn.org picture, to obey Iranian Islamic Law, to avoid offending strict Moslems? Maybe you should tell your fellow Canadians to stop travelling to Cuba in winter, because U.S. laws declare tourism to Cuba as illegal. There are good laws and bad laws. Would you have obeyed in 1935, as a good Canadian, the German Nuremburg Laws https://en.wikipedia.org/wiki/Nuremberg_Laws and betrayed Jews to German concentration camps? Would you have obeyed in 1964, as a good Canadian, the United States Jim Crow laws https://en.wikipedia.org/wiki/Jim_Crow_laws ordaining racial segregation and racial discrimination? There is no need to commiserate here with the lack of freedom of U.S. subjects. This is an international technical forum. Hopefully, U.S. subjects will eventually get their freedom back. And no more unapplicable legal advice from a U.S. fifth column in Canada.3 points
-
@genieautravail The ungoogled version has the flags #disable-encryption and #disable-machine-id. Enabling them will disable encryption and machine ID creation, allowing you to transfer your profile to another computer. The developer will not transfer them to the regular version, leaving the functionality completely stock. Therefore, for the regular version, use third-party tools to create a portable version.3 points
-
Well... That's the latest official 'xidel-0.9.9.20230616.8842.e14a96920e01.openssl.win32.zip' on https://sourceforge.net/projects/videlibri/files/Xidel/Xidel development/. Or 'xidel-0.9.9_2025-02-22-git-3e7e88a62307-openssl-win32.7z' on https://rwijnsma.home.xs4all.nl/files/xidel/personal_builds/, which I compiled myself. On Linux Xidel by default requires OpenSSL to open https urls at all. On Windows the normal win32/win64 binary relies on Microsoft's SChannel SSP (Secure Channel Security Service Provider) to do that. On Windows XP SChannel is limited to TLS 1.1, while practically all websites nowadays use TLS 1.2 and newer. So Benito, Xidel's author, created the openssl-win32 build especially for WinXP users. Xidel supports all OpenSSL versions. If you'd like to know what Xidel can do, I suggest you have a look at StackOverflow here or here. Obviously every piece of software that requires the OpenSSL dlls for internet connectivity can use these.3 points
-
Of course it is! They are different sessions, different cookies. I'm failing to understand the obsession. I'm done here, I really do not need the obsession.3 points
-
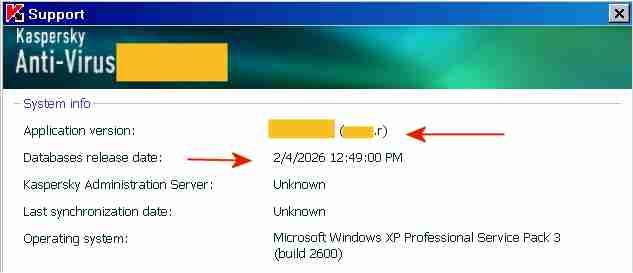
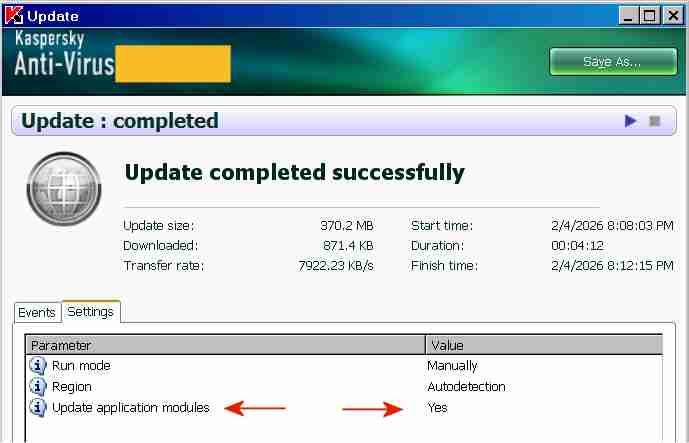
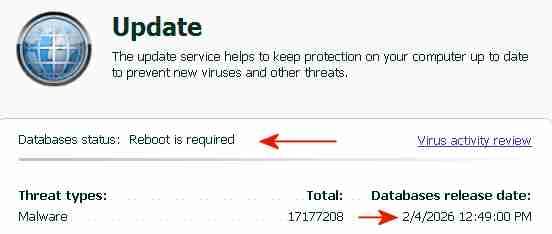
The "AutoPatches" for My Ancient Version of Kaspersky I succeeded in updating both the application modules and the signatures of My Ancient Version of Kaspersky with a single combined update, without a license key and without activation. By installing the final AutoPatches, My Ancient Version of Kaspersky has been updated to the ultimate final version, with the most recent program file digitally signed OK 26May2014. The screenshot above indicates the final AutoPatch "r" next to "Application version" and the Database release date "2/4/2026". Once knowing how-to, preparing future combined updates will be quite easy. The term "AutoPatches" by Kaspersky corresponds roughly to the term "Hotfix" by Microsoft. The screenshot above indicates "Update completed successfully" and "Update application modules: Yes". The signature updates were from a Kaspersky Lab update server, the application updates ("AutoPatches") were from my personal archive. Signature updates and application updates ("AutoPatches") were combined into a single update folder. The screenshot above indicates signatures of 2/4/2026 and the message: "Database status: Reboot is required". This message "Database status: Reboot is required" is displayed by My Ancient Version of Kaspersky when the update of the application modules via AutoPatches is pending. A tiny red square is added to the Kaspersky icon in the System Tray, indicating that AutoPatches are pending. During the reboot after the update, the Kaspersky driver updates and installs the program files contained in the AutoPatches and updates the registry, completely hidden and invisible to the user. StartUp Organizer, for example, which I use as a watch dog, does NOT notice any changes before, during and after the reboot. After rebooting and AutoPatching, the Kaspersky icon in the System Tray looks normal again, without a tiny red square. The successful installation of the AutoPatches is indicated in the About screen above by the display of "r" [=version of the AutoPatches] next to the Version (Note: the About screen is displayed by right-clicking on the Kaspersky icon in the System Tray -> About) and in the Support window (1st screenshot, at the top of this posting). Also, LastSuccessfulUpdate in the registry contains a hex value (Unix timestamp), which confirms that the update was successful. Furthermore, virus-checking with the updated application module and the new signatures works fine. The installation of the final AutoPatches plus a signature update of My Ancient Version of Kaspersky had faced three challenges: 1) The files of the final AutoPatches were removed from the Kaspersky Lab update servers and are most likely not available anywhere in the internet. 2) Kaspersky Lab does not provide license keys for My Ancient Version of Kaspersky anymore, which would permit multiple updates. My Ancient Version of Kaspersky is an unexpiring trial version and can only be updated once. An initial update with the final AutoPatches followed by a second update with current signatures is therefore not possible. Only one update is possible, either an update of the signatures from the Kaspersky Lab server or an update of the application module from my personal archive, but not both.. 3) The digital signature of the .xml file in the subfolder \index\ in the update folder impedes the combining of AutoPatches and current signatures into a single update folder. Before August 2019 the online updates from Kaspersky Lab of My Ancient Version of Kaspersky had consisted of three sub-folders: \AutoPatches\, \bases\ and \index\. After August 2019 no sub-folder \AutoPatches\ is created when downloading updates. The sub-folder \AutoPatches\ contained updates of the installed application modules, \bases\ contained the signature updates and \index\ contained only a .xml file validating \AutoPatches\ and \bases\. The .xml file in \index\ contains at the end a string which is an encoded digital signature generated using the private signing key of Kaspersky Lab. Changing text in the .xml file without updating the signature at the bottom will result in the error message "Invalid file signature" when trying to update. The final release of December 2012 of My Ancient Version of Kaspersky had been updated by several sets of "AutoPatches" supported by Kaspersky until 2017, identified by a letter of the alphabet appended to the build number of Kaspersky Anti-Virus. The last AutoPatch for My Ancient Version of Kaspersky is "r" and contains for example an updated basegui.dll, digitally signed OK 26May2014. The AutoPatches for My Ancient Version of Kaspersky were available from the Kaspersky Lab update servers until about 2018. When I tried to update in August 2019, all files of the AutoPatches for My Ancient Version of Kaspersky had been removed from the Kaspersky Lab update servers and My Ancient Version of Kaspersky could not be updated to release "r" (about 26May2014) anymore. The application modules of My Ancient Version of Kaspersky consequently remained those of the final release of December 2012, without any AutoPatches applied.. In addition Kaspersky Lab removed the text string which identified My Ancient Version of Kaspersky, from the digitally signed .xml file in \index\ downloaded from Kaspersky. Kaspersky Lab must have decided by August 2019 to definitely stop supporting My Ancient Version of Kaspersky, because they removed the application update files from their update servers and made it generally impossible to update the program with AutoPatches by removing the string permitting updates of My Ancient Version of Kaspersky from the digitally signed .xml in \index\. The final AutoPatches, including "r", probably also improve the Protection Components of My Ancient Version of Kaspersky. I have used My Ancient Version of Kaspersky only as an on-demand scanner, I have no need for the Protection Components. Nevertheless, I may eventually add the Protection Components to the installation, for further testing and to see whether activation is required to get the Protection Components to work. According to the User Guide of My Ancient Version of Kaspersky, if you select "Activate later" after installation, "you will have access to all the application's features, except for updates (only one application update will be available)".2 points
-
I think inserting the brackets is logical and correct.2 points
-
I have updated my old guide about compiling Chromium. Now it only applies to compiling clear Chromium. A new one will be created for building with e3kskoy7wqk patches.2 points
-
Sorry to resurrect this again but I think the yt-dlp4vlc script has an error. I think the probe function is incorrect . . . function probe() -- Check if the input is a YouTube link return vlc.access == "http" or vlc.access == "https" and (string.match(vlc.path, "youtube%.com") or string.match(vlc.path, "youtu%.be")) . . . should be . . . function probe() -- Check if the input is a YouTube link return (vlc.access == "http" or vlc.access == "https") and (string.match(vlc.path, "youtube%.com") or string.match(vlc.path, "youtu%.be")) . . . notice the brackets around the first 'or' pair. Bit marginal but without those brackets any http url will return true. Ben.2 points
-
Sure ; it loads fine: yt-dlp_x86 -v => [debug] Command-line config: ['-v'] [debug] Encodings: locale cp1253, fs utf-8, pref cp1253, out cp1253 (No VT), error cp1253 (No VT), screen cp1253 (No VT) [debug] yt-dlp version nicolaasjan/yt-dlp@2026.02.01.063416 (win7_x86_exe*) [debug] Python 3.14.2 (CPython x86 32bit) - Windows-Vista-6.0.6003-SP2 (OpenSSL 3.6.1 27 Jan 2026) [debug] exe versions: none [debug] Optional libraries: Cryptodome-3.23.0, brotli-1.2.0, certifi-2026.01.04, mutagen-1.47.0, requests-2.32.5, sqlite3-3.50.4, urllib3-2.6.3, websockets-16.0, yt_dlp_ejs-0.4.0 [debug] JS runtimes: none [debug] Proxy map: {} [debug] Request Handlers: urllib, requests, websockets [debug] Plugin directories: none [debug] Loaded 1856 extractors Usage: yt-dlp_x86 [OPTIONS] URL [URL...] yt-dlp_x86: error: You must provide at least one URL. Type yt-dlp --help to see a list of all options. and: yt-dlp_x86 -vF "jxm5zcK27qo" --js-runtime quickjs [debug] Command-line config: ['-vF', 'jxm5zcK27qo', '--js-runtime', 'quickjs'] [debug] Encodings: locale cp1253, fs utf-8, pref cp1253, out utf-8 (No VT), error utf-8 (No VT), screen utf-8 (No VT) [debug] yt-dlp version nicolaasjan/yt-dlp@2026.02.01.063416 (win7_x86_exe*) [debug] Python 3.14.2 (CPython AMD64 32bit) - Windows-Vista-6.0.6003-SP2 (OpenSSL 3.6.1 27 Jan 2026) [debug] exe versions: ffmpeg 5.0 (fdk,setts) [debug] Optional libraries: Cryptodome-3.23.0, brotli-1.2.0, certifi-2026.01.04, mutagen-1.47.0, requests-2.32.5, sqlite3-3.50.4, urllib3-2.6.3, websockets-16.0, yt_dlp_ejs-0.4.0 [debug] JS runtimes: quickjs-ng-0.11.0 [debug] Proxy map: {} [debug] Request Handlers: urllib, requests, websockets [debug] Plugin directories: none [debug] Loaded 1856 extractors [debug] [youtube] [pot] PO Token Providers: none [debug] [youtube] [pot] PO Token Cache Providers: memory [debug] [youtube] [pot] PO Token Cache Spec Providers: webpo [debug] [youtube] [jsc] JS Challenge Providers: bun (unavailable), deno (unavailable), node (unavailable), quickjs [youtube] Extracting URL: jxm5zcK27qo [youtube] jxm5zcK27qo: Downloading webpage [debug] [youtube] Forcing "main" player JS variant for player 3510b6ff original url = /s/player/3510b6ff/player_es6.vflset/en_US/base.js [youtube] jxm5zcK27qo: Downloading android vr player API JSON [debug] [youtube] jxm5zcK27qo: android_vr player response playability status: UNPLAYABLE [youtube] jxm5zcK27qo: Downloading web embedded client config [debug] [youtube] jxm5zcK27qo: Detected experiment to bind GVS PO Token to video ID for web_embedded client [youtube] jxm5zcK27qo: Downloading player 3510b6ff-main [youtube] jxm5zcK27qo: Downloading web embedded player API JSON [youtube] jxm5zcK27qo: Downloading web safari player API JSON [debug] [youtube] jxm5zcK27qo: Detected a 6s ad skippable after 5s for web_safari [youtube] [jsc:quickjs] Solving JS challenges using quickjs [debug] [youtube] [jsc:quickjs] Using challenge solver lib script v0.4.0 (source: python package, variant: minified) [debug] [youtube] [jsc:quickjs] Using challenge solver core script v0.4.0 (source: python package, variant: minified) WARNING: [youtube] [jsc:quickjs] QuickJS-NG is missing some optimizations making this very slow. Consider using upstream QuickJS instead. [debug] [youtube] [jsc:quickjs] Running QuickJS: '<redacted>\yt-dlp\Builds\Nightly\nicolaasjan\py3.14\2026.02.01.63416\PyInst-6.18\qjs.EXE' --script 'C:\Users\<redacted>\AppData\Local\Temp\tmpfsvkg2za.js' [youtube] jxm5zcK27qo: Downloading m3u8 information [debug] Sort order given by extractor: quality, res, fps, hdr:12, source, vcodec, channels, acodec, lang, proto [debug] Formats sorted by: hasvid, ie_pref, quality, res, fps, hdr:12(7), source, vcodec, channels, acodec, lang, proto, size, br, asr, vext, aext, hasaud, id [info] Available formats for jxm5zcK27qo: ID EXT RESOLUTION FPS CH | FILESIZE TBR PROTO | VCODEC VBR ACODEC ABR ASR MORE INFO ---------------------------------------------------------------------------------------------------------------------------- sb3 mhtml 48x27 0 | mhtml | images storyboard sb2 mhtml 80x45 0 | mhtml | images storyboard sb1 mhtml 160x90 0 | mhtml | images storyboard sb0 mhtml 320x180 0 | mhtml | images storyboard 249 webm audio only 2 | 44.09MiB 51k https | audio only opus 51k 48k [en] low, WEB-E, webm_dash 250 webm audio only 2 | 57.96MiB 67k https | audio only opus 67k 48k [en] low, WEB-E, webm_dash 140 m4a audio only 2 | 112.28MiB 129k https | audio only mp4a.40.2 129k 44k [en] medium, WEB-E, m4a_dash 251 webm audio only 2 | 113.71MiB 131k https | audio only opus 131k 48k [en] medium, WEB-E, webm_dash 91 mp4 256x144 24 | ~153.75MiB 177k m3u8 | avc1.4D400C mp4a.40.5 [en] WEB-S 160 mp4 256x144 24 | 58.06MiB 67k https | avc1.4d400c 67k video only 144p, WEB-E, mp4_dash 278 webm 256x144 24 | 63.73MiB 73k https | vp9 73k video only 144p, WEB-E, webm_dash 394 mp4 256x144 24 | 61.83MiB 71k https | av01.0.00M.08 71k video only 144p, WEB-E, mp4_dash 92 mp4 426x240 24 | ~276.63MiB 319k m3u8 | avc1.4D4015 mp4a.40.5 [en] WEB-S 133 mp4 426x240 24 | 111.89MiB 129k https | avc1.4d4015 129k video only 240p, WEB-E, mp4_dash 242 webm 426x240 24 | 120.41MiB 139k https | vp9 139k video only 240p, WEB-E, webm_dash 395 mp4 426x240 24 | 101.99MiB 118k https | av01.0.00M.08 118k video only 240p, WEB-E, mp4_dash 93 mp4 640x360 24 | ~697.64MiB 804k m3u8 | avc1.4D401E mp4a.40.2 [en] WEB-S 134 mp4 640x360 24 | 196.77MiB 227k https | avc1.4d401e 227k video only 360p, WEB-E, mp4_dash 18 mp4 640x360 24 2 | ≈308.67MiB 356k https | avc1.42001E mp4a.40.2 44k [en] 360p, WEB-E 243 webm 640x360 24 | 247.24MiB 285k https | vp9 285k video only 360p, WEB-E, webm_dash 396 mp4 640x360 24 | 182.68MiB 211k https | av01.0.01M.08 211k video only 360p, WEB-E, mp4_dash 94 mp4 854x480 24 | ~919.27MiB 1060k m3u8 | avc1.4D401E mp4a.40.2 [en] WEB-S 135 mp4 854x480 24 | 357.67MiB 412k https | avc1.4d401e 412k video only 480p, WEB-E, mp4_dash 244 webm 854x480 24 | 327.75MiB 378k https | vp9 378k video only 480p, WEB-E, webm_dash 397 mp4 854x480 24 | 262.34MiB 303k https | av01.0.04M.08 303k video only 480p, WEB-E, mp4_dash 95 mp4 1280x720 24 | ~ 1.17GiB 1387k m3u8 | avc1.4D401F mp4a.40.2 [en] WEB-S 136 mp4 1280x720 24 | 621.36MiB 717k https | avc1.4d401f 717k video only 720p, WEB-E, mp4_dash 247 webm 1280x720 24 | 538.63MiB 621k https | vp9 621k video only 720p, WEB-E, webm_dash 398 mp4 1280x720 24 | 425.20MiB 490k https | av01.0.05M.08 490k video only 720p, WEB-E, mp4_dash 96 mp4 1920x1080 24 | ~ 3.12GiB 3685k m3u8 | avc1.640028 mp4a.40.2 [en] WEB-S 137 mp4 1920x1080 24 | 1.34GiB 1577k https | avc1.640028 1577k video only 1080p, WEB-E, mp4_dash 248 webm 1920x1080 24 | 830.37MiB 958k https | vp9 958k video only 1080p, WEB-E, webm_dash 399 mp4 1920x1080 24 | 641.86MiB 740k https | av01.0.08M.08 740k video only 1080p, WEB-E, mp4_dash Do note, though, that "my Vista" system (SP2 32-bit) is fully updated till Vista SP2's EoL, with very little WS2008 updates and no ESU ones ; but the Win10 UCRT update (a Vista SP2 one) is indeed installed here ...2 points
-
@VistaLover I have uploaded an updated Vista+ compatible PyInstaller here. Could you test if the yt-dlp built with it works well on your Vista system?2 points
-
With version 3.6.0 new functionality has been added (3.6.1 is mainly a security release):2 points
-
2 points
-
You're right. I take it back what I said earlier. I have actually changed the build_openssl3() function locally to automate the process of creating the shared- as well as the static-release. And in the process I forgot to strip both dlls. The filesizes are now identical to what you ended up with. I re-uploaded 'openssl-3.6.1-win32-shared-dev-xpmod-sse.7z'.2 points
-
Hi Isolar, long time no see. About your question: there are two possibilities, or their combination. 1) Your HD Audio controler needs a nosnoop bit set, you can check with WPCREdit. 2) The parser of WDMHDA identified some verbs you didn't use in your HDAICOUT.HDA. Possible candidates: 'opening' inputs (mixer?), EAPD or GPIO. Search in this thread for verbs.1 point
-
Hi Drew, With initial help from Deomsh over at the 'Audio driver for Realtek HD Audio' thread, I have been using Watler's driver to get HD Audio working on Windows 98 laptops for a while, and came across one that I had some trouble with. Currently I have managed to get SoundMax AD1981HD working on a HP6710b laptop, IDT 92HD75B3X5 working on a HP 6550b laptop, and Realtek ALC272 working on a Lenovo S10-3 laptop with Watler's. Attempting a Lenovo S20-30 proved difficult as the codec was identified as 10EC 0280 of which I could not locate a datasheet for. I used HDAICIN responses to identify all NID's/CAPS and found the connection path to be the same as ALC 272 (and most other Realtek codecs from the looks of things) with $01 = AFG, $02 = DAC, $0C = Audio Out connected to NID $14, and NID $14 = Line Out. I managed to create a working HDAICOUT.HDA file but no sound. I had stumbled across your driver (great work I can see this being invaluable in the future!) and trialed v16, but sadly no sound to start with. So I re-installed Watler's to try some other options. What I notice is that your driver, although removed from device manager and 're-installed' to Watler's, is maybe still using the registry entries, so when I go to multimedia settings I can see the WDM driver still listed as an option, along with the midi/volume control, however Watler's is selected and installed. The HDA.SYS driver file still exists in windows\system32. The veeeery interesting thing here is that this combination has helped me to get sound working (although buggy) on the S20-30 laptop! I have no idea how or why this works but hoping you could shed some light on it, or I can provide you some more info that may be able to help you with development? I did try to rename HDA.SYS to HDA.BAK and rebooted but got no sound at reboot which indicates to me that although Watler's driver is installed it is still somehow using HDA.SYS in combination with HDA2.DLL to route the sound to the speaker - I am good with verbs but not with codec initialization, CORB, RIRB etc. To note: HDAcfg.ini from Watler's driver shows codec index $2 is active, which is incorrect (this is the HDMI audio out, whereas the 10EC 0280 codec is on index $0) so how I am getting any sound at all is a mystery.. At boot I get a high pitched squeal through the speakers until the initial windows start sound finishes, then I can go to sounds and play the sound samples. DirectX 9C is installed and runs the tests all okay. Happy to assist here with any information I can provide to get you further and help me understand why sound works with this combination, just let me know if anything is required. All the best and I will be following your progress. Cheers!1 point
-
I did find a site which had links to many downloads of AutoPatches: https://filemood.com/result?q=autopatches Unfortunately, there were no AutoPatches for my Ancient Version of Kaspersky and the download links are dead bittorrent magnet links. Kaspersky Lab has 30+ products with signature updates, with different versions etc, so the chance is exceedingly small that the relevant AutoPatches are still available anywhere in the internet. Maybe in archives of corporate users of Kaspersky of 10+ years ago, although I doubt that corporations archive old stuff that long. OT: When I looked into my own personal archive I have found an AutoPatch containing avp.exe v6.0.3.851 for the last version of Kaspersky Anti-Virus for Windows 98. klif.sys in this newly-found AutoPatch is digitally signed OK 1Apr2009. I had previously thought that Kaspersky Anti-Virus v6.0.3.844 (28Apr2008) was the last version for Windows 98, but this newly-found AutoPatch may update the last Win98-compatible build of Kaspersky Anti-Virus even further. This AutoPatch seems to be a major final update, it contains 27 files. What confuses the matter is that this newly-found AutoPatch was in a sub-folder \6.0.3.830\ with a lower version number than Kaspersky Anti-Virus v6.0.3.844 (28Apr2008) for Windows 98. Eventually I will have to check whether this newly-found AutoPatch can be installed under Win98 and whether the resulting ultimate final build for Win98 can be updated with current signatures.1 point
-
I understand you weren't addressing me specifically, and your general observations may well be correct. Yet, I think it's rather telling of a person's character when they let something little like "Micro$oft" get them riled up. To be clear, I use many Micro$oft products, and I actually like some of them! But I haven't found much to like in Windows versions beyond 7 (well, 8.1 wasn't too bad). Unfortunately, neither 7 nor 8.1 is supported any longer. I have no problem with that - few companies can afford to support decades-old products - but M$'s business model depends on them not giving me the choice to remain on an unsupported OS, even though I knowingly accept any security risks from doing so. Thus, I choose both to visit sites like MSFN, in order to keep Win 7 going; and to mildly protest M$'s attempts to force me to pay them for an OS I strongly dislike, with that little dollar sign.1 point
-
@ED_Sln Just to confirm that the flags works with the latest Ungoogled Chromium (144.0.7559.133). Regards1 point
-
Stuttering and freezing on YouTube is not a "bug". It's expecting too much of an old processor, an old OS, and backported browsers to NOT stutter and freeze. There are userscripts that can force h.264 and to force less-resource-hungry resolutions. Again, expecting too much is not a "bug", it's a "reality check". Another thing that I find helpful is to *INTENTIONALLY* "throttle" my internet speed. It does not cause "lags", it forces the streaming service to NOT send me UN-NEEDED 4K.1 point
-
@Slavich Shazam has already been fixed. Stuttering and freezing of sound and video on YouTube is usually associated with a weak processor that lacks the power to process 1080 video, especially if it is VP9 and even more so AV1.1 point
-
No; newer OpenSSL branches introduce API incompatibilities with the older branches/versions; one would have to modify the source of a given application (relying on OpenSSL 1.0.2) to implement support there for a later OpenSSL branch and recompile the source anew... FTR, the 1.0.2 branch was publicly EoL'ed in the end of 2019, with OpenSSL-1.0.2u (1.0.2.21); this LTS branch is still under Premium Support for enterprises not able to update to later branches, however the needed fee for such support is beyond the reach of private individuals; if you scavenge Russian forums, you may stumble upon some compiled leaked sources, e.g. I did find myself OpenSSL-1.0.2.zi (1.0.2.34) binaries there, but, ofc, I'm not going to post links for them here ...1 point
-
The way I see it, we now have this ... https://github.com/e3kskoy7wqk/Firefox-for-windows-71 point
-
Redirect link and tracking link are two different matters. The garbage you see after = is a unique tracking stamp. Most likely contains your IP, PC specs obtained via GetOEMCP ans so on. https://learn.microsoft.com/en-us/windows/win32/api/winnls/nf-winnls-getoemcp1 point
-
The tracker will be different with each browsing session. Google is tracking your searches, not your browser. I never said that the tracker will be "identical". It is generated BY GOOGLE each and every first visit per COOKIE. Delete the cookie and you get a new "tracker". First cookie: Delete first cookie, let Google set second cookie:1 point
-
1 point
-
https://github.com/e3kskoy7wqk/Chromium-for-windows-7-REWORK/issues/71 point
-
https://github.com/e3kskoy7wqk/Chromium-for-windows-7-REWORK He made few reworked versions. It also can support XP and Vista without extended kernels1 point
-
I see that there is a need for a more detailed explanation. You need: Vista SP2 x64 (you may need to upgrade it to 2017 EOL) kernel33.dll from Vista extended kernel v2023-03-09. p_advp32, p_ole, pwp_shl, p_user from Supermium 132 R4. (for convenience you can name them advapi33, ole33, shell33, user33 etc) In the chrome.exe file, change kernel32.dll to kernel33.dll in the import table using CFF Explorer In the chrome.dll file, change the same import. Then open this file in HxD and search for advapi32, ole32, shell32, user32 - they may be in several places, change the ones that are full import table looking like below: In the chrome_elf.dll file, as you rightly pointed out, change NtOpenKeyEx to the NtOpenKey version.1 point
-
How to force Aero on vista RTM "the reg hacks were disabled in the final release, so as far as I know there will be no way to enable" https://www.experts-exchange.com/questions/22128056/How-to-force-Aero-on-vista-RTM.html1 point
-
1 point
-
Actually this bug is present on Vista, too. It's not "XP-only", like someone there tried to imply. Therefore, you're in the wrong right repository, Dave, you can edit the post and include Vista so they get out of your hair. They have no respect to the famous moderator!1 point
-
1 point
-
Hi, at first read carefully my "Complete guide for restoring Microsoft Update in IE" in this post: If you have trouble with ProxHTTPSProxy, then you can find everything about it in this post:1 point
-
Hi to all, I have updated the content of my article in first post. Due to the fact that some of you had problems when running ProxHTTPSProxy or HTTPSProxy in older systems I have examined the correlation of crashes with the SSE2 capability of a CPU. The current results can be found in sections Prerequisites and Versions. Furthermore both versions of Root Certificate Updater have been updated and are now of 02/24/2022. Regards, AstroSkipper1 point
-
In your linked post the solution was to check if Microsoft Client Network is properly installed.1 point
-
This thread is about Root Certificates and Revoked Certificates for Windows XP. You can update your Root Certificates automatically by using the Certificate Updater 1.6 or manually by using the Root Certificate and Revoked Certificate Updater of 02/24/2022 created by me in section Downloads It works perfectly and is intended to keep your system as recent as possible regarding your Root Certificates. Kind regards, AstroSkipper1 point
-
Thank you for providing a download link of ProxHTTPSProxy REV3e! I have added your link to my article above in section Downloads so that the reader has a better overview.1 point
-
@WULover This thread is a support thread about Microsoft Update (MU) or Windows Update (WU). So we have reached a point where everything regarding hardware extensions is unfortunately off-topic. If you have further questions relating to your hardware, you must open your own thread with a topic of your choice. Here we can only discuss problems accessing MU. I hope I could help you and if so, I would be pleased about any reactions. Kind regards1 point
-
Of course, if you can change it, do it! It should be a SSE2 capable CPU But more RAM would be important too. But be aware, your mainboard meaning the onboard socket and the current BIOS have to support the new CPU! Does the WSUS method work in your system?1 point
-
I think you mean registry key it isn't a directory. But thanks for tip! We have to check all again and again and again....1 point
-
Newer browsers do not need HTTPSProxy or ProxhttpsProxy. I use these tools only for accessing web sites using IE or IE engine. Some programs use IE looking for updates or providing other services. Same for email clients. Most of the time HTTPSProxy is disabled in my system.1 point
-
Of course but I don't trust such features anyway and in case of Malwarebytes Premium for Windows 3.5.1.2522 even more. Your log looks fine until warning and error code 0x801901f6 appears, a cold comfort unfortunately. Please check if my provided config.ini is used and check Trusted Zone if only the three provided urls related to Microsoft exist. Check your Internet Zone too, maybe lower restrictions i.e. lower security level.1 point
-
@maile3241 Fine but is your folder male? :)1 point
-
Yes , exactly the same less amount (in Vista) with Nvidia HD audio almost everywhere. I only need DTS HD MA , I don't care about the other though. By the way , when I install Nvidia driver on Vista , it only adds simple "DTS-Audio" to supported formats (device properties) , while on Win7 it adds plenty of formats . It is intentional , I mean what prevents it to add more formats , it "sees" my HD capable devices (videocard and receiver) , so should be no problem , yet Nvidia doesn't want us to listen HD audio on Vista. I'm looking for a simple solution to unlock it. P.S. Much loved MPC-HC , apparently, hates Vista. When I manually choose and force playback of 5.1 HD tracks , it just plays them as poor quality 2.0 audio and blocks direct bypass completely ! So much for the popular player . I'm not sure what they have against Vista.1 point
-
Your observation is absolutely right , Vista audio drivers sound much better than the drivers that were meant for 7 , but not to the point of full satisfaction , not even close. In fact, Asus D2 Vista driver can be used without signature enforcement on 7 , but yet again , the audio is not punchy . It still sounds sandy and flat . Did you notice that Vista's audio drivers use DX10 when running on 7 ? Perhaps this is the reason they somewhat sound better. P.S. I had noticed many issues with 7 (like literally trembling opened windows , to the point where I can't even close them and the whole explorer just hangs up) Sorry . I'm not gonna argue about the other Win7 issues , like taskbar , if you choose to use Win7 (or whatever) - it's your choice . Yet again , in this topic we discuss our pleasant experience with Vista , not 7 or the such.1 point
-
I'm sorry , I do not agree . I use Windows starting from Win 93 , and I do not agree . In my opinion the best are Win 2000 (for it's time) and Vista. Always hated XP . XP is like oversaturated and bloated Win 2000. Win 7 is somewhat like Vista after unsuccessful plastic surgery and filled with toxins after that (I guess explains why it is slower).1 point
-
Opera 72 with these latest files "SHAssocEnumHandlersForProtocolByApplication not found in SHELL32.dll".1 point








.thumb.jpg.e861836bb05fe824ad8ec1930061ee43.jpg)