Leaderboard
Popular Content
Showing content with the highest reputation since 10/04/2021 in all areas
-
ProxHTTPSProxy and HTTPSProxy in Windows XP for future use 0. Table of Contents 0. Table of Contents 1. Introduction 2. Purpose of ProxHTTPSProxy and HTTPSProxy 3. Area of application 4. The TLS protocols and their cipher suites 5. Certificates - CA and Root Certificates 5.1. The CA certficate of ProxHTTPSProxy 5.2. The Root Certificates of Windows XP 6. The TLS 1.2 proxies ProxHTTPSProxy and HTTPSProxy 6.1. Prerequisites 6.1.1. Detailed information 6.2. Installation 6.3. Configuration 6.3.1. Configuration of ProxHTTPSProxy 6.3.2. Configuration of HTTPSProxy 6.3.3. Configuration of these proxies to access the MU website successfully nowadays 6.4. Usage 6.4.1. Usage of ProxHTTPSProxy 6.4.2. Usage of HTTPSProxy 6.5. Maintenance of ProxHTTPSProxy and HTTPSProxy for future use 7. The TLS 1.2 proxy ProxHTTPSProxy's PopMenu 3V1 7.1. Prerequisites 7.2. Purpose and components of ProxHTTPSProxy's PopMenu 3V1 7.3. Features of ProxHTTPSProxy's PopMenu 3V1 7.4. Changelog of ProxHTTPSProxy's PopMenu 3V1: 7.5. Installation and configuration of ProxHTTPSProxy's PopMenu 3V1 7.6. Tranferring all settings of an existing ProxHTTPSProxy's installation 7.7. Usage of ProxHTTPSProxy's PopMenu 3V1 8. The TLS 1.3 proxy ProxyMII 8.1. Prerequisites 8.2. General information about ProxyMII 8.3. Specific information about the different ProxyMII releases 8.3.1 ProxyMII (20220717) 8.3.2 ProxyMII (20230813) 8.4. How to set up and use the TLS 1.3 proxy ProxyMII 9. The TLS 1.3 proxy ProxHTTPSProxy's PopMenu TLS 1.3 9.1. Prerequisites 9.2. General information about ProxHTTPSProxy's PopMenu TLS 1.3 9.3. ProxHTTPSProxy's PopMenu TLS 1.3 3V3 9.3.1. Features of ProxHTTPSProxy's PopMenu TLS 1.3 3V3 9.3.2. Changelog of ProxHTTPSProxy's PopMenu TLS 1.3 3V3 9.3.3. Installation and start of ProxHTTPSProxy's PopMenu TLS 1.3 3V3 10. Versions 10.1. Versions of the TLS 1.2 proxies ProxHTTPSProxy, HTTPSProxy, and ProxHTTPSProxy's PopMenu 10.2. Versions of the TLS 1.3 proxies ProxyMII and ProxHTTPSProxy's PopMenu TLS 1.3 11. Downloads 11.1. Archived Downloads {obsolete}: 11.2. Latest Downloads 11.2.1. Downloads related to the TLS 1.2 proxies 11.2.1.1. Downloads related to ProxHTTPSProxy 11.2.1.2. Downloads related to HTTPSProxy 11.2.2. Downloads related to the TLS 1.3 proxies 11.2.3. Downloads related to cacert.pem Certificate Update 11.2.4. Downloads related to Root Certificate Updates 12. Update notifications 13. Conclusion 14. Disclaimer 1. Introduction: The idea of this thread is to provide information and recent findings I've made relating to the TSL proxies ProxHTTPSProxy and HTTPSProxy. Due to the fact that I don't use other older NT based Operation Systems (OSs) except Windows XP Professional all my observations and explanations are referring to both proxies in Windows XP only. So, please do not comment off-topic in this thread! I am AstroSkipper, a member of MSFN since 2010, and was involved in restoring of access to the Microsoft Update (MU) website in Windows XP (and some other OSs). This is the thread: https://msfn.org/board/topic/178377-on-decommissioning-of-update-servers-for-2000-xp-and-vista-as-of-july-2019/ While restoring MU in my own Windows XP Professional system, I had to solve a lot of problems and had among other things some significant findings relating to ProxHTTPSProxy and HTTPSProxy, too. The above mentioned thread is now over 140 pages long and unfortunately very bloated. In most cases visitors or members of MSFN don't want to read that much of pages for getting information they have looked for. A lot of comments are part of conversations which no longer can be retraced or understood easily by people who weren't participated. Therefore, I wanted to make my own findings accessible to all interested people in a clear, short way. That's why I decided to make my own thread to provide some facts, tips and especially news referring to these proxies. It is an unfortunate circumstance that the creators of ProxHTTPSProxy and HTTPSProxy, @heinoganda and @Thomas S., haven't been here for a long time and no further development of these proxies has been made the last years. Of course, we thank both creators explicitly for these outstanding proxies, we are very glad to have them, but they have to be used as they are. For this reason, we have to ask ourselves whether they'll continue doing their job in the future or not. But maybe some of you don't really know what actually their job is. 2. Purpose of ProxHTTPSProxy and HTTPSProxy: Originally, ProxHTTPSProxy was created for Proxomitron as an SSL Helper Program. Proximotron is a local HTTP web-filtering proxy. Here are two links about Proxomitron: http://www.buerschgens.de/Prox/index.html (German website, use Google Translator if necessary) and https://msfn.org/board/topic/183295-web-browser-proxomitron-reborn-ptrongui-a-how-to-guide/. This is a quotation from a post of the developer called "whenever" who had made ProxHTTPSProxy originally: Source link: https://prxbx.com/forums/showthread.php?tid=1618. Here is an image to show how ProxHTTPSProxy works: ProxHTTPSProxy and HTTPSProxy were created by our members mentioned above to provide modern nag-free HTTPS connections for an HTTP proxy. The main purpose in Windows XP is in adding modern ciphers to HTTPS connections of the Internet Explorer (IE) to improve either its missing TLS 1.2 functionality or its rudimentary TLS 1.2 functionality last added by Microsoft after installing some relevant POSReady updates (KB4230450, KB4316682 and KB4019276). Here is a link with further information how TLS 1.1 and TLS 1.2 can be enabled in Windows XP: https://msfn.org/board/topic/178092-enable-tls-11-and-12-in-windows-xp-correctly/?do=findComment&comment=1158544. The original ciphers of IE are outdated and therefore a lot of websites can't be accessed or they don't work properly due to SSL issues. More information about these proxies you can find in the original thread: https://msfn.org/board/topic/176344-problems-accessing-certain-sites-https-aka-tls/. 3. Area of application: As already said, the main purpose of these proxies is in adding modern ciphers to HTTPS connections of IE to improve either its missing TLS 1.2 functionality or its rudimentary TLS 1.2 functionality last added by Microsoft after installing some relevant POSReady updates. Therefore, ProxHTTPSProxy or HTTPSProxy is often used in combination with IE to access websites which couldn't be called up by IE without it. Some programs use Internet Explorer's browser engine called Trident to get data from Internet, to search something or to check for updates. For example my favourite movie database program All My Movies™ checks for updates using IE engine. Without one of these proxies it will fail. Some e-mail clients like eM Client or Eudora are using IE engine too. Some browsers like 360 Extreme Explorer are able to use IE engine for surfing. Another new purpose is to access Microsoft Update to look for updates. As I mentioned above I was involved in restoring of access to the Microsoft Update (MU) website in Windows XP (and some other OSs), and we were successful by now. If you're interested in restoring MU functionality, I've written a little guide with the title "Complete guide for restoring IE's access to WU/MU website using ProxHTTPSProxy or HTTPSProxy in Windows XP" which can be found here: https://msfn.org/board/topic/183498-general-and-specific-solutions-for-problems-regarding-auwumu-in-windows-xp/?do=findComment&comment=1216509 This thread is about different proxies to establish secure connections to servers or, more generally, to the internet. You often read about TLS, cipher suites, and certificates here. Therefore, I disseminate here some information about these "termini technici" for those who do not know exactly what is meant by them. 4. The TLS protocols and their cipher suites If you research the term TLS on the internet, you will get a lot of information, sometimes very simply presented, sometimes very technical, more for IT experts. With this small article, which can be seen more as a summary, I try to provide a little more transparency in this stuff. Transport Layer Security, abbreviated TLS, is a protocol for the authentication and encryption of Internet connections. For this purpose, TLS is inserted as its own layer between TCP and the protocols of the application layer. Here is a linked graphic to make it more clear: The individual tasks include authentication, certification, key exchange, integrity assurance and encryption. The main tasks are to guarantee the authenticity of the contacted remote stations, in most cases a server, by means of a certificate and to encrypt the connection between the remote stations. Here is a second linked graphic to demonstrate the actions and reactions in the communication between a client and a server: The used protocol defines the basic communication for the connection and is as crucial for a secure connection as the encryption protocol itself. Due to a series of vulnerabilities, the SSL2 and SSL3 protocols must be considered a security vulnerability and should be avoided at all costs. The successor to SSL3, TLS 1.0 should also be avoided, as the protocol offers a method to downgrade an established TLS 1.0 connection to SSL3. Thus, the connection is again vulnerable to the vulnerabilities that affect SSL3. Unfortunately, its successor TLS 1.1 is also no longer up to date and should be rather avoided nowadays. For a long time, the TLS 1.2 protocol was considered secure and therefore recommended. It offers a number of improvements that should ensure the security of connections again. In general, each new SSL or TLS version has brought additional features and options, making configuration a little more confusing, implementation more error-prone and handling more tedious. Overall, the use of TLS has become more insecure. With TLS 1.3, this should change, at best. Or, this was and is the actual goal, at least. For this reason, every single function of TLS has been tested for its security benefits and risks. In the process of development and in regard to the present knowledge, some parts were removed that no longer offer security and some of which are now also considered insecure. At the same time, security was improved with new procedures. Furthermore, measures for performance optimisation and preventive hardening measures for future attacks were taken into account. TLS 1.3 breaks backwards compatibility for the first time, which unfortunately causes some problems in practice. Connections with TLS 1.3 can be interrupted either because the connection is not accepted en route or due to a defective web server. Anyway, the protocols TLS 1.2 and, above all, TLS 1.3 are recommended as secure protocols nowadays. Here is a list of typical protocols and their cipher suites used by the TLS 1.3 proxy of my current program package ProxHTTPSProxy's PopMenu TLS 1.3 3V3 as an example. It's a screenshot taken from the website https://browserleaks.com/ssl: In the screenshot above, you can see many so called cipher suites belonging to specific TLS protocols. A cipher suite is a standardised collection of cryptographic procedures (algorithms) for encryption. In the Transport Layer Security (TLS) protocol, the cipher suite specifies which algorithms are to be used to establish a secure data connection. A cipher suite is generally displayed as a long string of seemingly random information but each segment of that string contains essential information. Generally, this data string is made up of several key components: The used protocol, in most cases TLS. The key exchange algorithm dictates the manner by which symmetric keys will be exchanged such as RSA, DH, DHE, ECDH, ECDHE. The authentication algorithm dictates how server authentication and (if needed) client authentication will be carried out such as RSA, DSA, ECDSA. The bulk encryption algorithm dictates which symmetric key algorithm will be used to encrypt the actual data such as AES, 3DES, CAMELLIA. The Message Authentication Code (MAC) algorithm dictates the method the connection will use to carry out data integrity checks such as SHA, SHA256, MD5. In some cases, there is an Elliptic Curve Cryptography (ECC) which is an encryption technique that provides public-key encryption similar to RSA. While the security strength of RSA is based on very large prime numbers, ECC uses the mathematical theory of elliptic curves and achieves the same security level with much smaller keys. Here are three linked graphics to illustrate these strings with examples: 5. Certificates - CA and Root Certificates Although Windows XP was abandoned and updates of root certificates were not provided anymore by Microsoft for this OS, we still found ways to update them. And, if we want to install one of our TLS proxies, we have to install a CA certificate to get them working. In both cases, certificates are needed, and this short article is intended to shed some light on this certificate jungle with regards to our TLS proxies. 5.1. The CA certficate of ProxHTTPSProxy A certificate authority (CA) is a trusted entity that issues digital certificates. These are files that cryptographically link an entity to a public key. Certificate authorities are an important part of the Internet's Public Key Infrastructure (PKI) because they issue the Secure Sockets Layer (SSL) certificates that browsers use to authenticate content sent from web servers. All popular web browsers use web servers' SSL certificates to keep content delivered online secure. They all need to trust certificate authorities to issue certificates reliably. SSL certificates are used in conjunction with the Transport Layer Security (TLS) protocol to encrypt and authenticate data streams for the HTTPS protocol, and are therefore sometimes referred to as SSL/TLS certificates or simply TLS certificates. The first time ProxHTTPSProxy is started, it creates the keys for a certificate authority in its program directory if there is none. This file CA.crt is used for on-the-fly generation of dummy certificates for each visited website which are stored in the subfolder Certs. And, there is a second file called cacert.pem located in ProxHTTPSProxy's program directory. This file cacert.pem contains the currently valid root certificates (will be considered in more detail below) used by the proxy to verify the server connections. Since your browser won’t trust the ProxHTTPSProxy's CA certificate out of the box, you will either need to click through a TLS certificate warning on every domain, or install the CA certificate once so that it is trusted. It has to be installed in the Trusted Root Certification Authority of Windows XP and in some cases additionally in the Certificate Manager of a browser as in the cases of New Moon, Pale Moon, Firefox, and others. The Internet Explorer doesn't possess an own certificates store and uses the Trusted Root Certification Authority of Windows XP. Typically, digital certificates contain data about the entity that issued the certificate and cryptographic data to verify the identity of the entity, including the entity's public key and expiration date for the certificate, as well as the entity's name, contact information, and other information associated with the certified entity. Web servers transmit this information when a browser establishes a secure connection over HTTPS. In doing so, they send to it the certificate and the browser authenticates it using its own root certificate store. The following graphic illustrates the structure of a Certificate Authority as for example GlobalSign: SSL/TLS certificates are based on PKI as mentioned above, and there are a few key parts that need to be in place for the SSL certificate to work: A digital certificate (for example, an SSL/TLS certificate) that proves the website’s identity. A certificate authority that verifies the website and issues the digital certificate. A digital signature that proves the SSL certificate was issued by the trusted certificate authority. A public key that your browser uses to encrypt the data sent to the website. A private key that the website uses to decrypt the data sent to it. Here is another graphic to illustrate the role that a certificate authority (CA) plays in the Public Key Infrastructure (PKI): When installing such CA certificates in Windows XP manually, then there is something else to note. It can be of crucial importance whether one installs a root certificate under the account of the Current User or Local Computer. In this article a little further down, you can find more information on that. Furthermore, exiting ProxHTTPSProxy completely, deleting the old CA.cert file in ProxHTTPSProxy's program directory, and restarting ProxHTTPSProxy will result in the generation of a new CA.crt that will be valid for another ten years. In addition, the certificate bundle cacert.pem should be updated, at best regularly. You can do that with the tool cacert Updater Fixed which can be found in the download section 11.2.3. Downloads related to cacert.pem Certificate Update. This tool is also included in my program package ProxHTTPSProxy's PopMenu. And, that is the moment to note something very important. Any change to a ProxHTTPSProxy installation regarding the CA certificate or a severe system crash while one of the proxies is running in the background always requires a reset of all dummy certificates in the Certs subfolder. The word "reset" at this point means deleting all certificates that have been created in the Certs folder, manually by the user. The next time the proxy is started correctly, all necessary certificates will be created again when the corresponding websites are accessed. Here are a few screenshots of ProxHTTPSProxy's CA certificate (German edition of Windows XP, sorry!): 5.2. The Root Certificates of Windows XP In cryptography and computer security, a root certificate is a public key certificate that identifies a root certificate authority (CA). Root certificates are self-signed and form the basis of an X.509-based PKI. Either it has matched Authority Key Identifier with Subject Key Identifier, in some cases there is no Authority Key identifier, then Issuer string should match with Subject string (RFC 5280). For instance, the PKIs supporting HTTPS for secure web browsing and electronic signature schemes depend on a set of root certificates. A certificate authority can issue multiple certificates in the form of a tree structure. A root certificate is the top-most certificate of the tree, the private key which is used to "sign" other certificates. All certificates signed by the root certificate, with the "CA" field set to true, inherit the trustworthiness of the root certificate. A signature by a root certificate is somewhat analogous to "notarizing" identity in the physical world. Such a certificate is called an intermediate certificate or subordinate CA certificate. Certificates further down the tree also depend on the trustworthiness of the intermediates. The following graphic illustrates the role of a root certificate in the chain of trust: The root certificate is usually made trustworthy by some mechanism other than a certificate, such as by secure physical distribution. Root certificates are distributed in Windows XP by Microsoft and located in special certificate stores. These certificate stores may be viewed through the Certificates snap-in Certmgr.msc in the Microsoft Management Console (MMC). You can open the Certificates console focused on the Current User on a Windows XP computer by executing Certmgr.msc in the Run dialog box. Here is a screenshot of what you see running this command (German edition of Windows XP, sorry!): The root certificates of Windows XP can be updated by @heinoganda's Certificate Updater, @Thomas S.'s CAupdater, or by my self-created Root Certificate and Revoked Certificate Updaters, in all cases to the most recent ones provided by Microsoft. These updaters can be found in the download section under 11.2.4. Downloads related to Root Certificate Updates. There is no automatism for this updating. It must be done manually by the user and, if possible, regularly. @heinoganda's Certificate Updater is also included in my program package ProxHTTPSProxy's PopMenu. And now, back to our proxies. 6. The TLS 1.2 proxies ProxHTTPSProxy and HTTPSProxy 6.1. Prerequisites: A CPU with SSE2 instruction set is required to run the more recent versions of these TLS 1.2 proxies under Windows XP. 6.1.1. Detailed information: Testing system: Windows XP Professional SP3 POSReady with an AMD Athlon XP 3200+ (Thoroughbred), an old CPU providing SSE, but lacking of SSE2 instruction set. After testing of all proxies mentioned in this article, I can confirm that all @heinoganda's releases ProxHTTPSProxy REV3b, ProxHTTPSProxy REV3d, ProxHTTPSProxy REV3e and @Thomas S.'s release HTTPSPoxy in version HTTPSProxy_Launcher_v2_2018-11-06 require a CPU with SSE2 instruction set. All these proxies crashed when starting 'ProxHTTPSProxy.exe' or 'HTTPSProxy.exe'. But @whenever's release ProxHTTPSProxyMII 1.3a could be started without crashing, and after testing I can confirm this proxy is fully compatible with a CPU possessing SSE instruction set only. Therefore, this proxy can be used in such old systems, but only if absolutely necessary. For safety reasons. More detailed information below in the section 10.1. Versions of the TLS 1.2 proxies ProxHTTPSProxy, HTTPSProxy, and ProxHTTPSProxy's PopMenu. 6.2. Installation: The program packages provide documents and instructions, actually sufficient. Both proxies do not need any installation. There is no setup installer. They are fully portable with a few exceptions. The user has to edit the config file according to his needs, he should update a special certificate called 'cacert.pem' and he has to install the proxy's root certificate properly in any case. But to avoid unnecessary repetitions, I'll come back to that later in the section 6.3. Configuration. The location of their program folder can be chosen freely. For this purpose, I've created a folder "Portable" in my system partition. I have created this folder to remind me that programs inside folder Portable do not have to be uninstalled. 6.3. Configuration: The configurations of these proxies are a bit different. 6.3.1. Configuration of ProxHTTPSProxy: - Install ProxHTTPSProxy's root certificate 'CA.crt' under the Trusted Root Certification Authority manually or apply 'ProxHTTPS Cert Install.exe'. Alternatively you can use the more recent ProxHTTPSProxy Cert Installer which has been modified and updated by me. You can find it in the section 11.2.1.1. Downloads related to ProxHTTPSProxy. - Edit the config file 'config.ini' according to your needs. More detailed explanations at the end of this section. - Update the certificate 'cacert.pem' by downloading and inserting it manually (see cacert Update.txt) or automatically by applying 'cacert_Updater.exe'. Due to the circumstance that @heinoganda's original cacert Updater doesn't work anymore, I have fixed it. This "cacert Updater Fixed" can be downloaded in the section 11.2.3. Downloads related to cacert.pem Certificate Update. 6.3.2. Configuration of HTTPSProxy: - Generate a new HTTPSProxy's root certificate 'HTTPSProxyCA.crt' by opening 'HTTPSProxy.exe' and closing its window when the process is over. - Install HTTPSProxy's root certificate 'HTTPSProxyCA.crt' under the Trusted Root Certification Authority manually. Alternatively you can use the brand new HTTPSProxy Cert Installer which has been created by me. You can find it in the section 11.2.1.2. Downloads related to HTTPSProxy. - Edit the config files 'config.ini' and 'Launcher.ini' according to your needs. More detailed explanations at the end of this section. - Update the certificate 'cacert.pem' by downloading from url https://curl.se/ca/cacert.pem and inserting it manually (see Installation-Update_EN.txt) or automatically by clicking cacert.pem update in Launcher's menu. - Execute the reg file 'Inet_CurUser_ProxySettings.reg'. Both proxies have got a config file called 'config.ini'. The following parameters of the proxy can be specified there:: ProxAddr, FrontPort, BackPort, LogPort and LogLevel. Look into this file and you'll get short descriptions of these parameters. Furthermore there are special sections titled [SSL No-Verify], [BLACKLIST], [SSL Pass-Thru] and [BYPASS URL]. In these sections url addresses can be inserted letting the proxy know how to perform them. HTTPSProxy has a second config file called 'Launcher.ini'. Here you can set up the Launcher of HTTPSProxy. A short description can be read at the beginning of each file section. Here you can see HTTPSProxy's config file similar to the one of ProxHTTPSProxy: More detailed information about the parameters and sections can be found in their doc files. Both proxies can be set as system-wide proxies using the executable proxycfg.exe. Here are proxycfg's command line parameters: The command proxycfg displays the current WinHTTP proxy settings. The command proxycfg -d specifies that all HTTP and HTTPS servers should be accessed directly. Use this command if there is no proxy server. The command proxycfg -p proxy-server-list optional-bypass-list specifies one or more proxy servers, and an optional list of hosts that should be accessed directly. If a proxy server is not specified for a given protocol and that server is not in the bypass list, the -p option specifies that the server cannot be accessed at all. The command proxycfg -d -p proxy-server-list optional-bypass-list specifies one or more proxy servers, and an optional list of hosts that should be accessed directly. If a proxy server is not specified for the given protocol, the -d option specifies that the server should be accessed directly instead. The command proxycfg -u imports the Internet Explorer proxy settings of the current user. WinHTTP does not support auto-discovery and configuration script-based proxy settings. So far so good, but unfortunately that's not the whole truth. 6.3.3. Configuration of these proxies to access the MU website successfully nowadays: The MU website can be accessed only by IE, but nowadays it needs the more recent cryptographic protocol TLS 1.2. That's the reason why MU wasn't available in the past. Therefore we have to use one of these proxies to gain access. If all steps of my Complete guide for restoring IE's access to WU/MU website using ProxHTTPSProxy or HTTPSProxy in Windows XP have been performed properly, you would like to call up MU website. But in some cases problems could occur. One of them is to get a MU website with output of error code 0x80072f8f (hexadecimal notation). I had examined this error deeply and could solve it. But what does that have to do with our proxies? Of course a lot, otherwise I wouldn't have mentioned it. Here you can read my short post "Final fix of error code 0x80072f8f while accessing WU or MU website": https://msfn.org/board/topic/178377-on-decommissioning-of-update-servers-for-2000-xp-and-vista-as-of-july-2019/?do=findComment&comment=1213188 The steps in order: Delete the old CA.cert file in ProxHTTPSProxy's program folder. Delete all certificates in ProxHTTPSProxy's certs subfolder. Update the certificate cacert.pem. Run the executable ProxHTTPSProxy.exe. A new ProxHTTPSProxy CA certificate CA.crt valid for another ten years has been generated. Import this new ProxHTTPSProxy CA certificate to Trusted Root Certification Authority but under the account local computer. And exactly here lies the problem. You have to import this certificate in a special way to ensure it is really installed in Trusted Root Certification Authority under the account local computer. Otherwise, it can happen that this certificate is installed in Trusted Root Certification Authority under the account current user. And that is definitely the cause of error code 0x80072f8f. No one had told us where this certificate has to be installed to. No hints in the doc files of both proxies. And, how can we do that? Here are the detailed steps using the Microsoft Management Console: Open console by typing mmc. Add a snap-in for certificates. Choose for local computer. Import your recently generated ProxHTTPSProxy CA certificate to Trusted Root Certification Authority. Finished. Now, we have to modify the config file. Alternatively you can use my pre-configured config files in the section 11.2.1. Downloads related to the TLS 1.2 proxies. Open the file config.ini in an editor of your choice. Add these urls under the section [SSL No-Verify]: urs.microsoft.com c.microsoft.com* *one.microsoft.com* download.windowsupdate.com cc.dcsec.uni-hannover.de fe2.ws.microsoft.com *update.microsoft.com ds.download.windowsupdate.com - Save your changes. - Finished. Of course, same procedure for HTTPSProxy with one exception: HTTPSProxy's root certificate is named HTTPSProxyCA.crt. Fixing error code 0x80072f8f leads to fixing another problem and that is the validity of Proxy's root certificate. From now on a freshly generated root certificate of ProxHTTPSProxy or HTTPSProxy valid for another ten years will be fully functional because we finally know where it exactly has to be imported to. Maybe, you understand now how important it is to configure these proxies properly. Otherwise, they wouldn't work flawlessly. In the section 11.2.1. Downloads related to the TLS 1.2 proxies, I provide separate CA Certificate Installer and Uninstaller for both proxies. They have been created by me for the people who do not dare to generate and install certificates themselves. Due to a modification made by me, these installers and uninstallers do now their job properly, i.e. the certificate installation will be definitely performed in the Trusted Root Certification Authority under the account local computer. If you asked me which kind of certificate installation you should choose, I would recommend the manual method. For security reasons only. The installers contain a pre-generated root certificate of its proxy which will be installed properly. But as a result all users of these installers will have got the same certificate unfortunately. Normally, no good. But, do we really want to spy each other? I don't think so. On the other hand, using the manual method we all will have an unique certificate without any risks. So it's up to you! 6.4. Usage: The usage of these proxies is very simple but a bit different. 6.4.1. Usage of ProxHTTPSProxy: The best way to start ProxHTTPSProxy is to execute the file ProxHTTPSProxy_PSwitch.exe. In this case, ProxHTTPSProxy will set up itself automatically and delete its settings when closing. You can check the settings of ProxHTTPSProxy in Internet Options of IE. Here is a screeshot of ProxHTTPSProxy's program window: 6.4.2. Usage of HTTPSProxy: The way to start HTTPSProxy is a bit different. For starting it, you have to simply drag the executable HTTPSProxy.exe onto a second executable Launcher.exe by drag & drop and a new system tray icon appears. Via this icon, all available options of HTTPSProxy's Launcher are accessible. There are a lot of options: HTTPSProxy exit, HTTPSProxy restart, HTTPSProxy show, HTTPSProxy hide, HTTPSProxy launch with Windows, config.ini edit, cacert.pem update, HTTPSProxy enabled - settings - log, Update Windows root CAs, Launcher.ini edit and so on. Here are some screenshots of HTTPSProxy: Launcher's menu: HTTPSProxy - switched on and switched off: HTTPSProxy's program window: HTTPSProxy while accessing MU: If connection errors occur, you can check the settings of HTTPSProxy in Internet Options of IE and set them manually or automatically by applying reg file 'Inet_CurUser_ProxySettings.reg'. And now one important hint. If you want to use both proxies in your system, you mustn't run them in RAM at same time! Otherwise the selected proxy won't work at all. You have to close the unused proxy to use the other. Keep that in mind! 6.5. Maintenance of ProxHTTPSProxy and HTTPSProxy for future use: We have to carry out a bit of maintenance to ensure that these proxies are working properly. First of all, the system's root certificates should be updated every three months. If you have not done that yet, you can use one of the root certificate updater in the section 11.2.4. Downloads related to Root Certificate Updates where different online and offline versions can be downloaded from. Then you should check following list: Regular update of the file 'cacert.pem'. Maintenance and check of the file config.ini according to your needs. Checking the validity of the proxy's root certificate. Deleting of all certificates in the folder 'Certs' if the proxy isn't working properly. Checking the state of the Proxy in IE or in your system. 7. The TLS 1.2 proxy ProxHTTPSProxy's PopMenu 3V1 7.1 Prerequisites: A CPU with SSE2 instruction set is required to run this TLS 1.2 proxies under Windows XP. 7.2. Purpose and components of ProxHTTPSProxy's PopMenu 3V1: This is the first release of ProxHTTPSProxy's PopMenu 3.0 in version 1.0.0.0 shortened 3V1. ProxHTTPSProxy's PopMenu 3V1 is a one-click menu in systray to access and control @heinoganda's ProxHTTPSProxy REV3e. ProxHTTPSProxy's PopMenu 3V1 is a synthesis of self-programmed executables, a very few commands, credits to @AstroSkipper at MSFN, and the freeware PopMenu 3.0, credits to Jochanan Agam at freeware.persoft.ch. All the information I spread about ProxHTTPSProxy in the sections above is of course also valid for ProxHTTPSProxy's PopMenu. 7.3. Features of ProxHTTPSProxy's PopMenu 3V1: ProxHTTPSProxy's PopMenu is not a classical launcher, it is rather a systray popup menu. It can be totally customized and continuously extended according to user's needs due to its modular structure, therefore much more flexible than a classical, compiled launcher. More features can be added easily without touching existent code. Due to ProxHTTPSProxy's PopMenu's modular structure the user can change, add, delete and reorder features. Even the icons in menu can be changed easily by the user. Here is the complete list of features implemented in ProxHTTPSPoxy's PopMenu 3v1: Start ProxHTTPSPoxy Stop ProxHTTPSPoxy Hide ProxHTTPSPoxy Show ProxHTTPSPoxy Check if ProxHTTPSPoxy is running (in RAM) cacert.pem Update Root Certificates Update Open IE Proxy settings Close IE Proxy settings Check system proxy status Enable ProxHTTPSProxy system-wide Disable ProxHTTPSProxy system-wide Edit config.ini Read documentation And here is a screenshot of ProxHTTPSProxy's PopMenu 3V1: ProxHTTPSPoxy's PopMenu is provided together with ProxHTTPSProxy REV3e. This new archive called "ProxHTTPSProxy_REV3e_PopMenu_3V1" has been additionally updated by me. These are the changes to original package of @heinoganda: 7.4. Changelog of ProxHTTPSProxy's PopMenu 3V1: @heinoganda's Certificate Updater 1.6 added. Old CA Root Certificate CA.crt replaced by new one valid until 02/19/2032. ProxHTTPSProxy CA Certificate Installer and Uninstaller replaced by more recent ones corresponding to pre-generated CA Root Certificate valid until 02/19/2032. Old cacert Updater removed, recreated cacert Updater Fixed added. cacert.pem updated to most recent one. Alternative latest cacert.pem dated of 2022-04-26 from Mozilla added with download url. All self-programmed executables of ProxHTTPSPoxy's PopMenu 3v1 created in two different versions, UPX and noUPX, following the spirit of ProxHTTPSPoxy's creator. 7.5. Installation and configuration of ProxHTTPSProxy's PopMenu 3V1: 1. Unpack archive and copy the complete folder ProxHTTPSProxy_REV3e_PopMenu_3V1_noUPX or ProxHTTPSProxy_REV3e_PopMenu_3V1_UPX (or its complete content) to desired location. 2. Although both, ProxHTTPSProxy REV3e and ProxHTTPSPoxy's PopMenu 3V1, are fully portable, the config file of program PopMenu has to be adjusted to new location. This can be done manually or much more comfortable automatically by a tool I created for this purpose only. Go to subfolder PopMenu and execute "Configure PopMenu.exe". This procedure will always set the menu back to default settings. If you modified the menu in the past to your needs, you have to adjust the config file "PopMenu.ini" manually, otherwise you'll lose your modifications. In any case the paths in config file "PopMenu.ini" have to be adjusted when the complete program folder (or its complete content) was copied to a new location. 7.6. Tranferring all settings of an existing ProxHTTPSProxy's installation: Copy the files "CA.crt" and "config.ini" from old installation folder to new one. Same with complete subfolder "Certs". Doing it in that way you won't lose any old settings. 7.7. Usage of ProxHTTPSProxy's PopMenu 3V1: To start ProxHTTPSPoxy's PopMenu, just apply "ProxyPopMenu.exe" in main program folder ProxHTTPSProxy_REV3e_PopMenu_3V1_noUPX or ProxHTTPSProxy_REV3e_PopMenu_3V1_UPX. ProxHTTPSPoxy's PopMenu can be set to "Start automatically at Windows startup" in context menu item "Settings" which is called up by right-clicking systray icon. Here the PopMenu can be configured generally. ProxHTTPSPoxy's PopMenu has been pre-configured by me. The provided functions (items) corresponding to their labels are in most cases self-programmed executables and in a very few inserted commands. All items of ProxHTTPSPoxy's PopMenu are generally self-explanatory. Feel free to click on them and test them! If you click on item "Enable ProxHTTPSProxy system-wide", my program checks whether ProxHTTPSProxy is running or not. If not, it will be started immediately. This is necessary to set ProxHTTPSProxy to mode system-wide or setting process would fail. And one recommendation: Do not change or modify files in subfolder PopMenu and keep the file or folder structure inside main folder, otherwise the ProxHTTPSProxy's PopMenu won't work properly! If you want to modify the menu, do it in PopMenu's "Settings". But you have to know what you do otherwise ProxHTTPSPoxy's PopMenu won't work as expected. ProxHTTPSProxy's PopMenu itself has a very low usage of RAM. It's only about 2 MB. The download link of ProxHTTPSProxy's PopMenu 3V1 can be found in the section 11.2.1.1. Downloads related to ProxHTTPSProxy. 8. The TLS 1.3 proxy ProxyMII 8.1. Prerequisites: ProxyMII was created by Python 3.7.1 which requires Microsoft Visual C++ 2015 Redistributable or Microsoft Visual C++ 2015-2019 Redistributable (latest version 14.28.29213.0). Check if it is installed in your system! 8.2. General information about ProxyMII: ProxyMII is a proxy based on ProxHTTPSProxy which was originally created by whenever. It was enhanced in terms of the TLS 1.3 protocol and its cipher suites by @cmalex who recently created it using Python 3.7.1. Again, a big thanks for that to @cmalex! ProxyMII provides all TLS protocols from TLS 1.0 up to TLS 1.3 and its corresponding cipher suites. It differs from @heinoganda's ProxHTTPSProxy in its file structure and does not provide a comparable program like ProxHTTPSProxy_PSwitch.exe to activate or deactivate the proxy settings automatically, when the proxy is started or closed. This has to be done manually by the user. If you want to use ProxyMII as it is without any additional comfort, then read the following instructions to get it running. 8.3. Specific information about the different ProxyMII releases: 8.3.1 ProxyMII (20220717): Hardware requirements: A CPU with SSE2 instruction set is not required anymore, SSE only is sufficient. ProxyMII (20220717) is now based on OpenSSL 3.0.5, dated from 2022-07-05, and Cryptography 3.4.8, dated from 2021-08-24. 8.3.2. ProxyMII (20230813): Hardware requirements: A CPU with SSE2 instruction set is now required., SSE only is not sufficient anymore. ProxyMII (20230813) is now based on OpenSSL 3.1.2, dated from 2023-08-01, and Cryptography 40.0.2, dated from 2023-04-14. Here are the changelogs: Changes from OpenSSL 3.0.5 to OpenSSL 3.1.2: Changes from Cryptography 3.4.8 to Cryptography 40.0.2: 8.4. How to set up and use the TLS 1.3 proxy ProxyMII: Unpack the archive and copy the folder ProxyMII to a location of your choice. Install the file CA.crt to Trusted Root Certification Authority under the account local computer manually. I use the certificate generated by ProxHTTPSProxy REV3e, provided in my release of ProxHTTPSProxy's PopMenu 3V1. Or use my contained ProxHTTPSProxy CA Certificate Installer and Uninstaller to do that automatically. If so, you have to overwrite the already existing CA.crt in ProxyMII's program folder by the one of my release. Enable the proxy settings of IE in the Internet Options -> LAN settings, i.e., check mark "Use a proxy server for your LAN", and click on Advanced. Go to the entry Secure and enter the Proxy address 127.0.0.1 and the port 8079. Update the file cacert.pem to have the most recent one by using my cacert Updater Fixed (Recreated). Start the proxy by executing the file ProxHTTPSProxy.exe. Ensure that your firewall doesn't block this proxy. Add it to your exclusions list or allow its connection. Do not forget to disable the proxy settings of IE when ProxyMII has been closed. The download links of ProxyMII and cacert Updater Fixed can be found respectively in the sections 11.2.2. Downloads related to the TLS 1.3 proxies and 11.2.3. Downloads related to cacert.pem Certificate Update. ProxyMII is the TLS 1.3 proxy on which my program package ProxHTTPSProxy's PopMenu TLS 1.3 is based from now on. 9. The TLS 1.3 proxy ProxHTTPSProxy's PopMenu TLS 1.3 9.1. Prerequisites: ProxHTTPSProxy's PopMenu TLS 1.3 is based on ProxyMII, which was created by Python 3.7.1, and requires Microsoft Visual C++ 2015 Redistributable or Microsoft Visual C++ 2015-2019 Redistributable (latest version 14.28.29213.0). Furthermore, Microsoft .NET Framework 4.0 is now additionally required to run the program package ProxHTTPSProxy's PopMenu TLS 1.3 under Windows XP. Check if both are installed in your system! A CPU with SSE2 instruction set is not required anymore, SSE only is sufficient. 9.2. General information about ProxHTTPSProxy's PopMenu TLS 1.3 The main feature of my program package ProxHTTPSProxy's PopMenu TLS 1.3 is @cmalex's ProxyMII, a TLS 1.3 proxy. I replaced @heinoganda's TLS 1.2 proxy from my last release of ProxHTTPSProxy's PopMenu REV3e 3V1 by @cmalex's TLS 1.3 proxy. This sounds simple, but, unfortunately, it wasn't. A lot of problems had to be solved to implement this proxy completely, enhance functionality, and get control of it as convenient as the old one. ProxHTTPSProxy's PopMenu TLS 1.3 is a one-click menu in systray to access and control the brand new TLS 1.3 proxy ProxyMII, better known as ProxHTTPSProxy, credits to @cmalex and its original creator whenever. @cmalex's ProxyMII, dated from 2022-07-17, is now based on OpenSSL 3.0.5 and Cryptography 3.4.8. It provides all TLS protocols from TLS 1.0 up to TLS 1.3 and its corresponding ciphers. 9.3. ProxHTTPSProxy's PopMenu TLS 1.3 3V3 ProxHTTPSProxy's PopMenu TLS 1.3 3V3 is the third release of ProxHTTPSProxy's PopMenu 3.0, now in version 3.0.0.0, shortened 3V3. It is a synthesis of the excellent, brand new TLS 1.3 proxy ProxyMII, dated from 2022-07-17, credits to @cmalex at MSFN, several self-programmed executables and a very few commands, credits to @AstroSkipper at MSFN, the freeware PopMenu 3.0, credits to Jochanan Agam at freeware.persoft.ch, the open source utility Min2Tray v1.7.9, credits to Junyx at junyx.breadfan.de, and the program Certificate Updater 1.6, credits to @heinoganda at MSFN. If you wonder when the second version was released, the answer is very simple: never. This version was unofficial. ProxHTTPSProxy's PopMenu is not a classical launcher, it is rather a systray pop-up menu. It can be totally customized and continuously extended according to the user's needs due to its modular structure, therefore, much more flexible than a classical, compiled launcher. More features can be added easily without touching the existent code. Due to ProxHTTPSProxy's PopMenu's modular structure, the user can change, add, delete and reorder features. Even the icons in the menu can be changed easily by the user. Here is a screenshot: 9.3.1 Features of ProxHTTPSProxy's PopMenu TLS 1.3 3V3: Here is the complete list of features implemented in ProxHTTPSProxy's PopMenu TLS 1.3 3V3 and a short explanation of them: Start ProxHTTPSPoxy – Activates the proxy's settings in IE LAN Settings, starts the proxy, and deactivates and cleans its settings after closing, all automatically. Stop ProxHTTPSPoxy – Stops the proxy and closes its status window. Minimize ProxHTTPSProxy to systray – Minimizes ProxHTTPSProxy's status window to systray and shows its icon there. Restore ProxHTTPSProxy from systray – Restores ProxHTTPSProxy's minimized status window from systray. Hide ProxHTTPSPoxy – Hides ProxHTTPSProxy's status window completely. Show ProxHTTPSPoxy – Shows ProxHTTPSProxy's hidden status window again. Check if ProxHTTPSPoxy is running (in RAM) – Checks if ProxHTTPSPoxy is running in the background. cacert.pem Update – Performs an update of the file cacert.pem. Root Certificates Update – Performs an update of the system's Root Certificates. Open IE Proxy settings – Opens the tab LAN Settings in IE's Internet Options. Close IE Proxy settings – Closes the tab LAN Settings and IE's Internet Options completely. Check system proxy status – Checks whether the proxy is used system-wide or the system has direct access. Enable ProxHTTPSProxy system-wide – Permits the whole system to use this proxy. In this mode, services can route their traffic through the proxy, too. Disable ProxHTTPSProxy system-wide – The proxy can be used only locally if it is running, generally all have direct access to their servers or the internet. Edit config.ini – Opens the file config.ini with the editor Notepad to check or modify the proxy's configuration. Read documentation – Opens the documentation with the editor Notepad to get quickly information. In the screenshot above, you can see a red arrow which points to the icon of ProxHTTPSPoxy, minimized to systray. It's a new feature, and the green marked items have been added to the pop-up menu since last release. ProxHTTPSPoxy's PopMenu is provided together with ProxyMII from 2022-07-17, created by @cmalex and branded by me as ProxHTTPSProxy 1.5.220717. This new archive called ProxHTTPSProxy TLS 1.3 1.5.220717 PopMenu 3V3 has been additionally updated by me. These are the changes to the previous version of ProxHTTPSPoxy's PopMenu: 9.3.2 Changelog of ProxHTTPSProxy's PopMenu TLS 1.3 3V3: @heinoganda's ProxHTTPSProxy REV3e replaced by @cmalex's ProxHTTPSProxy 1.5.220717 with a brand new TLS 1.3 support. New starter program StartProxy.exe created to activate the proxy settings, start the proxy, and deactivate its settings after closing, all automatically. cacert.pem updated to the most recent one. Alternative cacert.pem from Mozilla, updated to the most recent version dated 2022-07-19. The open source utility Min2Tray has been fully implemented by the new configuration tools Configure PopMenu.exe and Setup Min2Tray.exe, all automatically. After the setup procedure, the programs PopMenu and Min2Tray are started automatically. All self-created files are not UPX-compressed. Therefore, the version is a noUPX only. Two new items added to the pop-up menu: Minimize ProxHTTPSProxy to systray and Restore ProxHTTPSProxy from systray. All unnecessarily embedded files have been removed from my self-created executables. Changes in calling up other programs. In all my affected programs, protection against code injection has been improved. This leads to preventing of future "space bugs", too! Different issues, which could have been noticed only in very rare cases, have been fixed. All unnecessary code has been removed. New bugs I additionally found have been fixed. Autostart entries of PopMenu and the new Min2Tray, automatically added to the registry by my configuration program, have been fixed in regard to the "space bug". All message windows of my programs have been resized and adjusted for a better visibility. All my self-created program files have been recompiled by using a different compiler. @cmalex's original ProxyMII wasn't modified by me, except a replacement of ProxHTTPSProxy.EXE's program icon, back to the old one and an update of the file config.ini to get access to the Microsoft Updates (MU) website with this proxy. 9.3.2 Installation and start of ProxHTTPSProxy's PopMenu TLS 1.3 3V3: Check if Microsoft Visual C++ 2015 Redistributable or Microsoft Visual C++ 2015-2019 Redistributable (latest version 14.28.29213.0) is installed in your system. Check if Microsoft .NET Framework 4.0 is installed in your system. Unpack the archive and copy either the complete folder ProxHTTPSProxy_TLS_1_3_1_5_220717_PopMenu_3V3 or its complete content to your desired location. Install the file CA.crt, located in the main program folder, to Trusted Root Certification Authority under the account local computer, or use the program ProxHTTPSProxy Cert Installer, provided in the archive. Go to the subfolder PopMenu and execute the program Configure PopMenu.exe. PopMenu and Min2Tray will be started automatically. A more detailed documentation, titled Documentation of ProxHTTPSProxy's PopMenu 3V3, can be found in the subfolder Docs of my program package and should be read before using ProxHTTPSProxy's PopMenu in any case. All features and more are described there. The programs PopMenu and Min2Tray have a very low usage of RAM. It's only about 2 MB and 4 MB respectively. The download link of ProxHTTPSProxy's PopMenu TLS 1.3 3V3 can be found in the section 11.2.2. Downloads related to the TLS 1.3 proxies. 10. Versions: 10.1. Versions of the TLS 1.2 proxies ProxHTTPSProxy, HTTPSProxy, and ProxHTTPSProxy's PopMenu: Last known version of ProxHTTPSProxyMII, created by @whenever and released in June of 2018: ProxHTTPSProxyMII 1.5 (20180616) ProxHTTPSProxyMII 1.3a (20150527) was released in May of 2015. Here are two links: https://prxbx.com/forums/showthread.php?tid=2172&pid=17686#pid17686 and https://prxbx.com/forums/showthread.php?tid=2172&pid=18454#pid18454 Due to support of SHA1 for signing certificates ProxHTTPSProxyMII 1.3a can be used in a Windows XP Professional x64 system to access MU successfully. More recent versions use SHA256 to sign certificates and fail while accessing MU. But that also means ProxHTTPSProxyMII 1.3a is not secure and should only be used if there is no other option. Here is a link to the post with necessary instructions and a screenshot of successful access to MU using ProxHTTPSProxyMII 1.3a in Windows XP Professional x64, credits to @maile3241: https://msfn.org/board/topic/178377-on-decommissioning-of-update-servers-for-2000-xp-and-vista-as-of-july-2019/?do=findComment&comment=1214098 Last known version of ProxHTTPSProxy released in November of 2019: ProxHTTPSProxy REV3e. Here is a link: https://msfn.org/board/topic/176344-problems-accessing-certain-sites-https-aka-tls/?do=findComment&comment=1173585 Last known version of HTTPSProxy released in November of 2018: HTTPSProxy_Launcher_v2_2018-11-06 Here are two links: https://msfn.org/board/topic/176344-problems-accessing-certain-sites-https-aka-tls/?do=findComment&comment=1155858 and https://msfn.org/board/topic/176344-problems-accessing-certain-sites-https-aka-tls/?do=findComment&comment=1156032 Last version of ProxHTTPSProxy's PopMenu released in May of 2022: ProxHTTPSProxy's PopMenu 3V1 (20220510) Here is the link to my post of this initial release: https://msfn.org/board/topic/183352-proxhttpsproxy-and-httpsproxy-in-windows-xp-for-future-use/?do=findComment&comment=1218622 10.2. Versions of the TLS 1.3 proxies ProxyMII and ProxHTTPSProxy's PopMenu TLS 1.3: ProxyMII released in July of 2022: ProxyMII (20220717). It was rebranded by me to ProxHTTPSProxy 1.5.220717. Here is the link to @cmalex's original post: https://msfn.org/board/topic/183684-looking-for-a-person-with-python-programming-skills-to-implement-tls-13-functionality-in-proxhttpsproxy-rev3e/?do=findComment&comment=1222235 Latest version of ProxyMII released in August of 2023: ProxyMII (20230813). Here is the link to @cmalex's original post: https://msfn.org/board/topic/183352-proxhttpsproxy-and-httpsproxy-in-windows-xp-for-future-use/?do=findComment&comment=1250552 Latest version of ProxHTTPSProxy's PopMenu TLS 1.3 3V3 released in August of 2022: ProxHTTPSProxy's PopMenu TLS 1.3 3V3 (20220817). Here is the link to the post of its official release: https://msfn.org/board/topic/183352-proxhttpsproxy-and-httpsproxy-in-windows-xp-for-future-use/?do=findComment&comment=1224184 11. Downloads: 11.1. Archived Downloads {obsolete}: ProxHTTPSProxyMII 1.3a can be downloaded here: http://www.proxfilter.net/proxhttpsproxy/ProxHTTPSProxyMII 1.3a.zip. Credits to @whenever. ProxHTTPSProxyMII 1.5 can be downloaded here: http://jjoe.proxfilter.net/ProxHTTPSProxyMII/files/ProxHTTPSProxyMII 1.5 advanced 34cx_freeze5.0.1urllib3v1.22Win32OpenSSL_Light-1_0_2o-1_1_0h.zip. Credits to @whenever. ProxHTTPSProxy REV3d can be downloaded here: https://www.mediafire.com/file/r23ct8jd2ypfjx5/ProxHTTPSProxyMII_REV3d_PY344.7z/file. Credits to @heinoganda. Root Certificate and Revoked Certificate Updater of 02/24/2022 created by @AstroSkipper: https://www.mediafire.com/file/n4ea8nbijox88o3/Roots_Certificate_Updater_24.02.22.7z/file Root Certificate and Revoked Certificate Updater (AIO version!) of 02/24/2022 created by @AstroSkipper: https://www.mediafire.com/file/8ler7d9z8aesz08/rootsupd.exe/file Root Certificate and Revoked Certificate Updater of 04/28/2022 created by @AstroSkipper: https://www.mediafire.com/file/7e6jw2mdp6bi3u0/Roots_Certificate_Updater_28.04.22.7z/file Root Certificate and Revoked Certificate Updater (AIO version!) of 04/28/2022 created by @AstroSkipper: https://www.mediafire.com/file/m6n7481wdq546ad/rootsupd.EXE/file Root Certificate and Revoked Certificate Updater of 05/24/2022 created by @AstroSkipper: https://www.mediafire.com/file/aob1fkpf6f3vyhd/Roots_Certificate_Updater_24.05.22.7z/file Root Certificate and Revoked Certificate Updater (AIO version!) of 05/24/2022 created by @AstroSkipper: https://www.mediafire.com/file/vkopcjfymnei5cn/rootsupd.exe/file Root Certificate and Revoked Certificate Updater of 06/28/2022 created by @AstroSkipper: https://www.mediafire.com/file/2eowvtl8r56q8tx/Roots_Certificate_Updater_28.06.22.7z/file Root Certificate and Revoked Certificate Updater (AIO version!) of 06/28/2022 created by @AstroSkipper: https://www.mediafire.com/file/h1460guuxqklkk5/rootsupd.exe/file Root Certificate and Revoked Certificate Updater of 08/23/2022 created by @AstroSkipper: https://www.mediafire.com/file/nxt11m8m39fnc1k/Roots_Certificate_Updater_23.08.22.7z/file Root Certificate and Revoked Certificate Updater (AIO version!) of 08/23/2022 created by @AstroSkipper: https://www.mediafire.com/file/0o2h3y16ekmtv2o/rootsupd.EXE/file Root Certificate and Revoked Certificate Updater of 09/27/2022 created by @AstroSkipper: https://www.mediafire.com/file/d4mtrexun8ao81l/Roots_Certificate_Updater_27.09.22.7z/file Root Certificate and Revoked Certificate Updater (AIO version!) of 09/27/2022 created by @AstroSkipper: https://www.mediafire.com/file/44suzv2x2fbrret/rootsupd.EXE/file Root Certificate and Revoked Certificate Updater of 10/25/2022 created by @AstroSkipper: https://www.mediafire.com/file/naxyauof6fs0p88/Roots_Certificate_Updater_25.10.22.7z/file Root Certificate and Revoked Certificate Updater (AIO version!) of 10/25/2022 created by @AstroSkipper: https://www.mediafire.com/file/nmzw6l4lzmxn8wx/rootsupd.EXE/file Root Certificate and Revoked Certificate Updater of 11/29/2022 created by @AstroSkipper: https://www.mediafire.com/file/cnlbxdffjq9beva/Roots_Certificate_Updater_29.11.22.7z/file Root Certificate and Revoked Certificate Updater (AIO version!) of 11/29/2022 created by @AstroSkipper: https://www.mediafire.com/file/pctxthjlcb6croc/rootsupd.EXE/file Root Certificate and Revoked Certificate Updater of 02/28/2023 created by @AstroSkipper: https://www.mediafire.com/file/6chiibdsdoh4i22/Roots_Certificate_Updater_28.02.23.7z/file Root Certificate and Revoked Certificate Updater (AIO version!) of 02/28/2023 created by @AstroSkipper: https://www.mediafire.com/file/rmjyq3pak60jayz/rootsupd.EXE/file Root Certificate and Revoked Certificate Updater of 04/25/2023 created by @AstroSkipper: https://www.mediafire.com/file/xgmi98u15ikerrn/Roots_Certificate_Updater_25.04.23.7z/file Root Certificate and Revoked Certificate Updater (AIO version!) of 04/25/2023 created by @AstroSkipper: https://www.mediafire.com/file/dxtxkgqdk6xlfb9/rootsupd.EXE/file Root Certificate and Revoked Certificate Updater of 08/22/2023 created by @AstroSkipper: https://www.mediafire.com/file/53fv86ouqgonm7f/Roots_Certificate_Updater_22.08.23.7z/file Root Certificate and Revoked Certificate Updater (AIO version!) of 08/22/2023 created by @AstroSkipper: https://www.mediafire.com/file/9xhsy3i2bphtf0i/rootsupd.EXE/file Root Certificate and Revoked Certificate Updater of 11/28/2023 created by @AstroSkipper: https://www.mediafire.com/file/361ux1ogvmokuhf/Roots_Certificate_Updater_28.11.23.7z/file Root Certificate and Revoked Certificate Updater (AIO version!) of 11/28/2023 created by @AstroSkipper: https://www.mediafire.com/file/6o1rfz4oqnh0din/rootsupd.EXE/file Root Certificate and Revoked Certificate Updater of 02/27/2024 created by @AstroSkipper: https://www.mediafire.com/file/7awvvb37in89op1/Roots_Certificate_Updater_27.02.24.7z/file Root Certificate and Revoked Certificate Updater (AIO version!) of 02/27/2024 created by @AstroSkipper: https://www.mediafire.com/file/55c7c574pyem2vg/rootsupd.EXE/file Root Certificate and Revoked Certificate Updater of 03/26/2024 created by @AstroSkipper: https://www.mediafire.com/file/a1oil6g5cane3bu/Roots_Certificate_Updater_26.03.24.7z/file Root Certificate and Revoked Certificate Updater (AIO version!) of 03/26/2024 created by @AstroSkipper: https://www.mediafire.com/file/6hcuv2r715l8nnm/rootsupd.EXE/file 11.2. Latest Downloads: 11.2.1. Downloads related to the TLS 1.2 proxies: 11.2.1.1. Downloads related to ProxHTTPSProxy: ProxHTTPSProxy REV3e can be downloaded here: https://www.mediafire.com/file/me5l9dydomgwa0h/2005536469_ProxHTTPSProxyMIIv1.5Rev3ePython3.44OriginalFiles.7z/file. Credits to @heinoganda. ProxHTTPSProxy's PopMenu 3V1 can be downloaded here: https://www.mediafire.com/file/djg5n0n9osqco7m/ProxHTTPSProxy_REV3e_PopMenu_3V1_CheckedByAstroSkipper.7z/file. Password: CheckedByAstroSkipper. Credits to @AstroSkipper. ProxHTTPSProxy CA Certificate Installer and Uninstaller with a freshly pre-generated root certificate valid until 02/19/2032 modified and built by @AstroSkipper: https://www.mediafire.com/file/9tnonnlymrp98f8/ProxHTTPSProxy_Cert_Installer_%2B_Uninstaller_%2B_CA_valid_until_02-19-2032.7z/file ProxHTTPSProxy's config file to access MU website successfully, modified by @AstroSkipper: https://www.mediafire.com/file/vr1klatuzjh6v5c/ProxHTTPSProxy_-_config.ini/file 11.2.1.2. Downloads related to HTTPSProxy: HTTPSProxy in the version of HTTPSProxy_Launcher_v2_2018-11-06 can be downloaded here: https://www.mediafire.com/file/ku859ikt2t79cgl/HTTPSProxy_Launcher_v2_2018-11-06.7z/file. Credits to @Thomas S.. HTTPSProxy CA Certificate Installer and Uninstaller with a freshly pre-generated root certificate valid until 02/19/2032 created by @AstroSkipper: https://www.mediafire.com/file/sx1i6w2c6f1hvwm/HTTPSProxy_Cert_Installer_%2B_Uninstaller_%2B_CA_valid_until_02-19-2032.7z/file HTTPSProxy's config file to access MU website successfully, modified by @AstroSkipper: https://www.mediafire.com/file/6emtdvx2vmw4iz8/HTTPSProxy_-_config.ini/file 11.2.2. Downloads related to the TLS 1.3 proxies: ProxyMII (20220717) = ProxHTTPSProxy 1.5.220717 can be downloaded here: https://www.mediafire.com/file/zbkz37dh0wjgnml/ProxyMII_220717_CheckedByAstroSkipper.7z/file. Password: CheckedByAstroSkipper. Credits to @cmalex. ProxyMII (20230813) can be downloaded here: https://www.mediafire.com/file/8oir8zsg0ffjs6u/ProxyMII_230813_CheckedByAstroSkipper.7z/file. Password: CheckedByAstroSkipper. Credits to @cmalex. ProxHTTPSProxy's PopMenu TLS 1.3 3V3 can be downloaded here: https://www.mediafire.com/file/4sqkixfd2waaypt/ProxHTTPSProxy_TLS_1_3_1_5_220717_PopMenu_3V3_CheckedByAstroSkipper.7z/file. Password: CheckedByAstroSkipper. Credits to @AstroSkipper. ProxHTTPSProxy CA Certificate Installer and Uninstaller with a freshly pre-generated root certificate valid until 02/19/2032 modified and built by @AstroSkipper: https://www.mediafire.com/file/9tnonnlymrp98f8/ProxHTTPSProxy_Cert_Installer_%2B_Uninstaller_%2B_CA_valid_until_02-19-2032.7z/file ProxHTTPSProxy's config file to access MU website successfully, modified by @AstroSkipper: https://www.mediafire.com/file/vr1klatuzjh6v5c/ProxHTTPSProxy_-_config.ini/file 11.2.3. Downloads related to cacert.pem Certificate Update: cacert Updater Fixed, fixed and recreated by @AstroSkipper: https://www.mediafire.com/file/y98gtqf8ewr6zz4/cacert_Updater_Fixed_Recreated.7z/file. Credits to @heinoganda. 11.2.4. Downloads related to Root Certificate Updates: Root Certificate and Revoked Certificate Updater of 05/28/2024 created by @AstroSkipper: https://www.mediafire.com/file/qo3w3h9n2zumb2o/Roots_Certificate_Updater_28.05.24.7z/file Root Certificate and Revoked Certificate Updater (AIO version!) of 05/28/2024 created by @AstroSkipper: https://www.mediafire.com/file/v3bokp223uen5ta/rootsupd.EXE/file Certificate Updater 1.6: https://www.mediafire.com/file/nmoqrx8vwc8jr6l/jveWB2Qg1Lt9yT5m3CYpZ8b8N4rH.rar/file. Credits to @heinoganda. Archive password: S4QH5TIefi7m9n1XLyTIZ3V5hSv4se1XB6jJZpH5TfB6vkJ8hfRxU7DWB2p CAupdater 1.0.0.1: https://www.mediafire.com/file/z34fifg2a09fzxo/CAupdater.7z/file. Credits to @Thomas S.. The installers created by myself or built by me will be updated from time to time if necessary. All files in my offered archives are definitely virus-free and clean, although some AV scanners produce false positives. I recommend adding the complete folder to the exclusion list of your security program(s), only if you trust me, of course. Apart from that, you can also check positive reported files on VirusTotal, though. 12. Update notifications: 02/26/2022: Both versions of Root Certificate and Revoked Certificate Updater have been updated and are now of 02/24/2022. 03/16/2022: The functionality of @heinoganda's cacert Updater has been restored. cacert Updater Fixed can be downloaded in the section 11.2.3. Downloads related to cacert.pem Certificate Update. 04/23/2022: cacert Updater Fixed has been completely recreated due to false alarms of some virus scanners and can be downloaded in the section 11.2.3. Downloads related to cacert.pem Certificate Update. 05/10/2022: ProxHTTPSProxy's PopMenu 3V1 has been released. Here is the link to my post of the initial release with the download link: https://msfn.org/board/topic/183352-proxhttpsproxy-and-httpsproxy-in-windows-xp-for-future-use/?do=findComment&comment=1218622 05/16/2022: Both versions of Root Certificate and Revoked Certificate Updater have been updated and are now of 04/28/2022. 06/05/2022: Both versions of Root Certificate and Revoked Certificate Updater have been updated and are now of 05/24/2022. 06/30/2022: Both versions of Root Certificate and Revoked Certificate Updater have been updated and are now of 06/28/2022. 07/17/2022: ProxyMII has been released. Here is the link to the post of its official release: https://msfn.org/board/topic/183684-looking-for-a-person-with-python-programming-skills-to-implement-tls-13-functionality-in-proxhttpsproxy-rev3e/?do=findComment&comment=1222235. 08/17/2022: ProxHTTPSProxy's PopMenu TLS 1.3 3V3 has been released. Here is the link to the post of its official release: https://msfn.org/board/topic/183352-proxhttpsproxy-and-httpsproxy-in-windows-xp-for-future-use/?do=findComment&comment=1224184 09/05/2022: Both versions of Root Certificate and Revoked Certificate Updater have been updated and are now of 08/23/2022. 10/06/2022: Both versions of Root Certificate and Revoked Certificate Updater have been updated and are now of 09/27/2022. 11/06/2022: Both versions of Root Certificate and Revoked Certificate Updater have been updated and are now of 10/25/2022. 12/09/2022: Both versions of Root Certificate and Revoked Certificate Updater have been updated and are now of 11/29/2022. 03/04/2023: Both versions of Root Certificate and Revoked Certificate Updater have been updated and are now of 02/28/2023. 05/09/2023: Both versions of Root Certificate and Revoked Certificate Updater have been updated and are now of 04/25/2023. 08/13/2023: ProxyMII has been updated. Here is the link to the post of its official release: https://msfn.org/board/topic/183352-proxhttpsproxy-and-httpsproxy-in-windows-xp-for-future-use/?do=findComment&comment=1250552. 09/01/2023: Both versions of Root Certificate and Revoked Certificate Updater have been updated and are now of 08/22/2023. 12/11/2023: Both versions of Root Certificate and Revoked Certificate Updater have been updated and are now of 11/28/2023. 04/05/2024: Both versions of Root Certificate and Revoked Certificate Updater have been updated and are now of 02/27/2024. 04/05/2024: Both versions of Root Certificate and Revoked Certificate Updater have been updated and are now of 03/26/2024. 08/20/2024: Both versions of Root Certificate and Revoked Certificate Updater have been updated and are now of 05/28/2024. 14/01/2025: Four download links renewed due to false positives by MediaFire. These four files are now password-protected to stop MediaFire from spreading even more nonsense. 13. Conclusion: At the beginning of this post, I said we had to ask ourselves whether these proxies would continue doing their job in the future or not. After all these observations and explanations, the answer to this question is quite clear: Yes, of course. And especially since we have our new TLS 1.3 proxies. But we have to avoid misconfiguration of these proxies, and in addition, we know they won't work properly without updating and carrying out maintenance. Doing all these things leads to a general, positive side effect for those loving their Windows XP. If all is done correctly, we are now able to use a freshly generated 10 years valid root certificate of ProxHTTPSProxy or HTTPSProxy at any time as long as Windows XP, Internet Explorer access to WWW, TLS 1.2 or TLS 1.3 functionality, Microsoft Update for Windows XP, or the user himself still exist. 14. Disclaimer: All information that I spread here corresponds to my level of knowledge. Most of it has been carefully researched by me. I tested all programs of the section 11. Downloads extensively, and they worked properly in my system. Nevertheless, I do not assume any guarantee either for the correctness and completeness or for the implementation of my tips. The same applies to the application of my tools in the section 11. Downloads. Therefore, all at your own risk! You can use the commenting zone below to tell us about your experiences, problems and questions or to provide further tips and recommendations. Any discussions about these proxies are explicitly welcome. If this article has not been able to resolve any issues related to these proxies, and you need further assistance with configuring or running them, I will try to help you as much as I can. But one thing must be clear, everything should relate to the topic of this thread. That means please stay on-topic! If you enjoyed this article or maybe, you found it interesting and helpful, I would be pleased about any reaction by liking, upvoting, and of course, commenting. Kind regards, AstroSkipper23 points
-
Here is the future of Chromium on Windows 7: https://github.com/win32ss/supermium I have been closely tracking the many changes made to Chromium since November 2022, made with the intent of dropping support for Windows 7 and 8.x. As of version 111, it became very difficult to keep the newest versions running on Vista with the extended kernel; shared memory allocation changes made it impossible to do so as subtle changes to the API (which were done in kernel mode) prevented stable operation of the browsers. So I decided to build my own Chromium. I discovered that a further change was made to the shared memory allocation which broke it even further; the successor to mojo, IPCZ, was forced on by default. It only works properly with Windows 8.1+'s shared memory API. I disabled IPCZ for pre-8.1 and this made the sandbox work again on Vista and 7. Perhaps I will see exactly why IPCZ is broken (from the Windows API level) and try to fix it for the next release. The only win32 API link I can find is CreateFileMappingW, which I need to test with an IPCZ-enabled build on both 8 and 8.1 to see what makes it fail.19 points
-
Sad news for everyone here at MSFN. One of our forum supervisors, Dencorso, passed away on October 24th, after a long and courageous battle with cancer. Apparently he was still upbeat and optimistic about the future a few weeks before he passed. My memories of Den go back quite a few years. He was incredibly helpful to me with technical problems, which is what this board is all about of course, initially mainly with Windows 98, and latterly with Windows XP. He was immensely supportive too when I first became a moderator here, something I will always be grateful for. He was definitely one of the good guys, and will be sorely missed here. Please add your memories here of working with Den. Thanks, Dave.18 points
-
On behalf of xper, an explanation for MSFN being offline for the last few days. An ingress of water at the location of the server caused damage, fortunately not to the server itself, but to the room's UPS system batteries, which necessitated the removal of power and a physical move of the server to another location. This obviously took some time to do. Hopefully there will now be no further issues relating to this.16 points
-
Support for installing Chromium extensions, saving their settings, as well as keeping cookies and other settings has been implemented: The original objective was to fix the "CultureNotSupported"-related exceptions that prevented .NET Core 5 from working, but under the belief that the .NET and Chromium issues were connected, I worked on solving the issue using Chromium. It turns out that .NET's issues are unrelated.16 points
-
I will not continue with this project, I have outgrown it. Thank you for all your kind comments, advice, etc. My modified versions are removed - they are unsafe due to sandbox bypass, embeded videos do not work.15 points
-
This project make possible to compile ACPI 2.0 driver from leaked XP SP1 & W2003 RTM sources, has same functionality as existing acpi.sys v6666 (still missed integer/fields/memory 64 bit support/) Grab leaked XP SP1/W2003 RTM sources (google it) Use "XPSP1/NT" directory as basedir if you want to compile acpi.sys for Windows XP x32 Use "Win2K3/NT" directory as basedir for Windows 2003 x32 / Windows 2003 x64 / Windows XP x64 Download any GNU patch package for windows (gnuwin32.sourceforge.net, cygwin, mingw, msys2, ...) Open command console, change current dir to base\busdrv\acpi\ (Windows XP x32) Save text diff patch https://pastebin.com/C5NXwHbS (v7 update) to file base\busdrv\acpi\sp1_to_sp3(ACP2).patch (Windows 2003 x32 / Windows 2003 x64 / Windows XP x64) Save text diff patch https://pastebin.com/8QURrM49 (v7 update) to file base\busdrv\acpi\rtm_to_sp2(ACP2).patch (Windows 2003 x32 / Windows 2003 x64 / Windows XP x64) Rename Win2K3/NT/public to Win2K3/NT/public2 (Windows 2003 x32 / Windows 2003 x64 / Windows XP x64) Update compiler and headers to mix of W2003 DDK+WRK, unpack https://anonfiles.com/J1W9H1a8y1/W2003_tools_update_7z to basedir with overriding existing files Remove "read only" flag from base\busdrv\acpi directory including sub-dirs and files Apply patch to convert original SP1/RTM sources to SP3/SP2 with extended ACPi 2.0 syntax: patching file driver/amlinew/amlipriv.h patching file driver/amlinew/amlitest.c patching file driver/amlinew/data.c patching file driver/amlinew/misc.c patching file driver/amlinew/object.c patching file driver/amlinew/parser.c patching file driver/amlinew/proto.h patching file driver/amlinew/type1op.c patching file driver/amlinew/type2op.c patching file driver/inc/aml.h patching file driver/nt/debug.c patching file driver/nt/debug.h patching file driver/nt/devpower.c patching file driver/nt/internal.c patching file driver/nt/interupt.c patching file driver/nt/irqarb.c patching file driver/nt/osnotify.c patching file driver/nt/pciopregion.c patching file driver/nt/rangesup.c patching file driver/nt/root.c patching file driver/nt/wake.c Change current dir to basedir (Windows XP x32 / Windows 2003 x32) Run razzle environment setup: (Windows 2003 x64 / Windows XP x64) Run razzle environment setup Change current dir to base\busdrv\acpi\driver\ Complie ACPI driver: build /Dcegbw Compiled acpi.sys.sys will be in (x32) base\busdrv\acpi\driver\nt\obj\i386\ or (x64) base\busdrv\acpi\driver\nt\obj\amd64\ Project contains implementation of new ACPi 2.0 syntax: ToInteger ToString ToHexString Continue ConcatenateResTemplate ToDecimalString Mod ToBuffer CopyObject MidString QwordConst (inside ParseIntObj) Timer CreateQWordField(fake it as CreateDWordField) Know issues workarounds: BSOD 0xA5 (0x10006, ...) missing _DIS method for "PNP0C0F" (PCI Interrupt Link Devices) BSOD 0xA5 (0x02,xxx, 0x0, ...) ACPI vs E820 mem ranges conflict IOTRAPS I/O range 0xFF00-0xFFFF vs VGA (10-bit decode!) conflict BSOD 0xA5(0x03, ..., C0140008, ...) error in ValidateArgTypes() when reading 64-bit fields BSOD 0x7E(c0000005, ...) error in AcpiArbCrackPRT() when referencing null pointer BSOD 0xA5 (0x11, 0x08, ..., ...) error in _AMLILoadDDB() (zero lenght buffer) BSOD 0xA5 (0x11, 0x08, ..., ...) error in _AMLILoadDDB() (doubled device definition) BSOD 0xA5 (0x0000000D, ..., 0x4449555F, 0) absence _UID method BSOD 0xA5 (0x11, 0x08, ..., ...) error in _AMLILoadDDB() (Connection() opcode) CPU definition as Device with _HID=ACPI0007 BSOD 0xA5(0x03, ..., C0000034, ...) postponed SSDT loading on x64 platform (v8 update) Assertion Fail on loaddsdt.c, line 488 for x64 builds (v8 update) Unresolved issues: BSOD 0xA5 (0x0000000D, ..., ..., ...) duplicated/absence _HID/_UID method (AMD boards) BSOD 0xA5 (0x2001, 0x01, 0xC0000034, ...) failure to evaluate the _PIC method in NotifyHalWithMachineStates() Conflicted device names in Windows device manager (Code 42)14 points
-
Hello everyone. I'm sorry for the very long period of inactivity lately. I've had a lot going on outside of MSFN in my personal life that has kept me busy. I also walked away from an unhealthy relationship and have been taking steps to rebuild my life since then, which has kept me from being able to update the list for the past several months. In light of the recent announcement that MSFN is going offline, I will be moving my list over to a forum hosted by my friend Ryan: http://forum.eclectic4un.me/ This will take a while as I need to manually re-add all of the links and formatting, but I will post the link here when it is finished. Feel free to join our forum if you're looking for a new home once MSFN is no longer available! We're still grassroots at the moment, but we will be building a new legacy software community over there and we'd love to have you join us (@Ximonite& @win32 are already there and have pertinent posts related to Vista Extended Kernel & Win2000's KernelXE!). Thank you so much everyone here for your contributions to the list over the past 6 years. It has been my pleasure to help provide this information to Vista users for the past several years, and I like to believe our efforts have helped many Vista (and even XP) users over the years. I'm sad to see MSFN go, but all good things do come to an end. Best regards14 points
-
Yes, the page above is the official Supermium website. And the account was flagged for "spamming". as I found out when trying to export the repository directly from GitHub to GitLab. The repositories were not deleted, but they are hidden from public view along with my account itself. At the time of this incident, I had built Chromium 124-based Supermium and it worked on XP (x86 and x64). But I still had a few deficiencies to correct before even a pre-release, specifically graphical glitches with GPU enabled, some upstream UI bugs, plus other outstanding bugs reported recently. Other features such as a UA/UACH spoofer and UI customization were being worked on as well. I reiterate that there is no malware in Supermium, progwrp, its installer and its uninstaller.13 points
-
Hello everyone. I just finished re-adding GDI to Supermium. At first it would only work in --single-process mode, but I got it working in standard mode by ensuring that FontCache objects have the Skia GDI font manager when GDI is enabled. Then I want to fix TLS, readd D3D9 DXVA support, and link Supermium against a DLL with implementations of many newer functions. I have fixed my PMs if you are interested.13 points
-
12 points
-
Off-topic: while testing my GreenPad on ReactOS, I found some bugs and fixed some of them. And ReactOS twitter account mentioned me. :)12 points
-
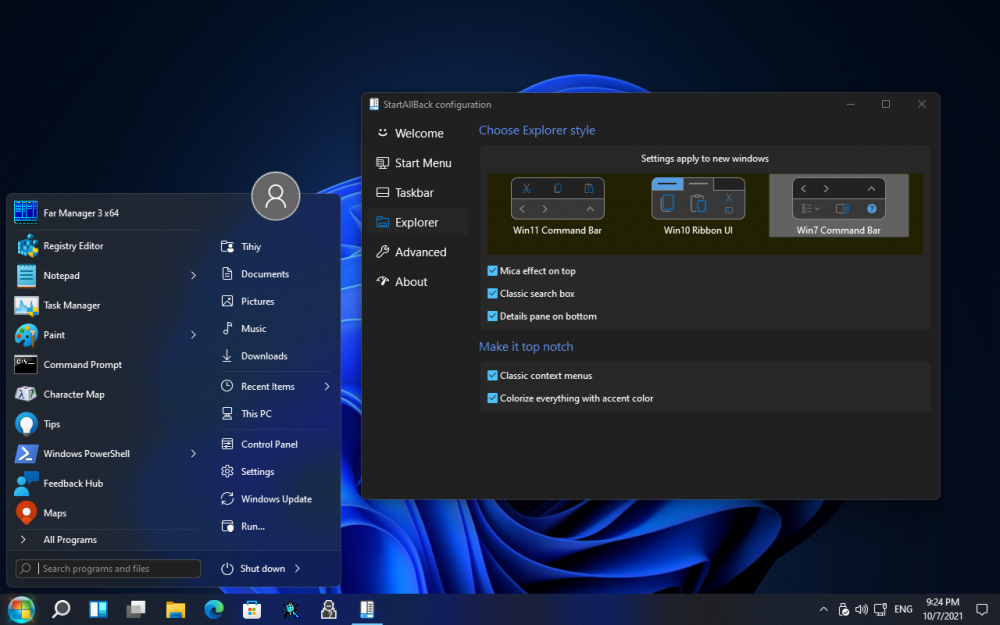
Introducing StartAllBack: an app to fix all Windows 11 UI issues! Restore taskbar functionality - Drag and drop, different icon sizes, different screen sides, widgets, new icons, old flyouts, oh my! Restore context menus - Win32 menus were never this sexy! Fix Windows Explorer - Ribbon UI and Command Bar made sexy and not slow; search box that works Top notch styling - Recolor everything: all UI elements in all apps don't have to be blue! - Fix broken Win32 styling in Win11 RTM version - Improved dark mode styling with Explorer And start menu: yes! - Windows 7 style all-signing, all-dancing yet again, refreshed with new look and functions It could be the last year you can enjoy Windows not crippled, so do it! https://www.startallback.com11 points
-
Those builds are originally for my private use and they are released because of my goodwill that I think they may help others. This bug doesn't affect me and so I don't have big intention on hunting and fixing it. If you want this to be fixed you at least need to find when the problem started to occur. and last but not least, stop gaslighting.11 points
-
Update of uBlock Origin Legacy to version 1.16.4.33 I have again updated my special mod uBlock Origin Legacy from version 1.16.4.32 to version 1.16.4.33. I fixed the loading errors of the filter list "Online Malicious URL Blocklist (AdGuard)" which only occur from time to time. Furthermore, I found some further strings which I edited according to the extension's name change performed in version 1.16.4.32. And I added new filter lists to different groups. The "StevenBlack/hosts" filter lists are very strong and restrictive. So in some cases, you have to set exclusions when using them. Here is a screenshot taken from the dashboard tab "Filter lists" of uBlock Origin 1.16.4.33 in New Moon 28: The filter lists outlined in green are the ones I have added in this release. A detailed changelog and the download link of uBlock Origin Legacy 1.16.4.33 can be found in my main article uBlock Origin Legacy - A special mod by @AstroSkipper. Greetings from Germany, AstroSkipper11 points
-
Off-Topic: so tomorrow is last day of my "sick leave" period caused by bicycle accident happened in 12 Nov 2022, I'll try to pick-up all upstream changes to my trees. Starting from 1 March I have to resume to my $DAYJOB and picking-up tasks that crated during the period that I was "missing" so it could be quite busy in following days/weeks. hope everything goes well and back to normal soon.11 points
-
New build of Serpent/UXP for XP! Test binary: Win32 https://o.rthost.win/basilisk/basilisk52-g4.8.win32-git-20251206-3219d2d-uxp-e4afc5655b-xpmod.7z Win64 https://o.rthost.win/basilisk/basilisk52-g4.8.win64-git-20251206-3219d2d-uxp-e4afc5655b-xpmod.7z source code that is comparable to my current working tree is available here: https://github.com/roytam1/UXP/commits/custom IA32 Win32 https://o.rthost.win/basilisk/basilisk52-g4.8.win32-git-20251206-3219d2d-uxp-e4afc5655b-xpmod-ia32.7z source code that is comparable to my current working tree is available here: https://github.com/roytam1/UXP/commits/ia32 NM28XP build: Win32 https://o.rthost.win/palemoon/palemoon-28.10.7a1.win32-git-20251206-d849524bd-uxp-e4afc5655b-xpmod.7z Win32 IA32 https://o.rthost.win/palemoon/palemoon-28.10.7a1.win32-git-20251206-d849524bd-uxp-e4afc5655b-xpmod-ia32.7z Win32 SSE https://o.rthost.win/palemoon/palemoon-28.10.7a1.win32-git-20251206-d849524bd-uxp-e4afc5655b-xpmod-sse.7z Win64 https://o.rthost.win/palemoon/palemoon-28.10.7a1.win64-git-20251206-d849524bd-uxp-e4afc5655b-xpmod.7z Win7+ x64 AVX2 https://o.rthost.win/palemoon/palemoon-28.10.7a1.win64-git-20251206-d849524bd-uxp-e4afc5655b-w7plus-avx2.7z Official UXP changes picked since my last build: - Issue #2489 - fix `color-mix` implementation. (103bd151c8) - Issue #2847 - Update tests and toolkit CSS to account for `windows-win11` (becf65d05a) - Issue #2869 - Make Purple Buffer additions check if cell is tenured. (34d1d5a650) No official Pale-Moon changes picked since my last build. No official Basilisk changes picked since my last build. My changes picked since my last build: - layout: restore xp theme names in test (c80b9fc1ea) - ffvpx: update ffmpeg to 3.4.14 ( https://github.com/FFmpeg/FFmpeg/commit/9983d098ff0ee54bc3b77676dd885883bfbe4ffb ) (83cd56dfbb) - nss: update certdata and bump ckbi version to 2.82 (d8a03301d4) - dns: update effective_tld_names.dat from https://publicsuffix.org/list/public_suffix_list.dat (e27800bb2a) - icu: update timezone data (cb88bccc0a) - security: update EV root data (c417312184) - icu: import backport of ICU-20558 (Fix regression in DateTimePatternGenerator) (dc67193fba) - icu: if langTag is empty, point it to root.txt as well (9e8e5fbd83) - icu-data: regenerate with icu_sources_data.py (e4afc5655b) Update Notice: - You may delete file named icudt*.dat inside program folder when updating from old releases. * Notice: From now on, UXP rev will point to `custom` branch of my UXP repo instead of MCP UXP repo, while "official UXP changes" shows only `tracking` branch changes.10 points
-
Solving BSODs 0xA5(..., ..., ..., ...): Windows XP/2003 supports only ACPI 1.0b syntax, last generation bioses uses ACPI 2.0+ To support ACPI 2.0 syntax need replace acpi.sys and apply additional patches to avoid known BSODs : - 0xA5 (0x03, ..., C0140001, ...) missing ACPI 2.0 syntax, 95% solved, solutions: 1) acpi.sys v.5048, sha1:a09c0d9f6b5cb63192e2cebada56db38d3870b29) from Vista Beta/Longhorn v.5048 Pro: - Has most of ACPI 2.0 syntax opcodes - All integers are 64-bit regarding ACPI 2.0 specification Cons: - beta, compiled for next generation of windows - failed implementation of some internal data types, _ValidateArgTypes generates BSOD 0xA5(0x03, xxx, C0140008, yyy) Patches: - Add pointer to _atDataObj struct for QWord Opcode (_OpcodeTable start at .data:00039848, _atDataObj struct at .data:000397A8, missing pointer at .data:00039880, dont forget add additional relocs) 2) acpi.sys v.6666 based on original Windows XP SP3 v.5512 with integrated acpi 2.0 syntax support Pro: - based on original v.5512, match binary/offsets Cons: - All integers are still 32-bit, any operations on 64-bit fields/variables will drop high part of QuadWord 3) acpi.sys compiled from leaked "XP SP1+W2003 RTM" sources Pro: - allow compile x64 build based on W2003 sources Cons: - same as v.6666 - 0xA5 (0x11, 0x08, ..., ...) unknow error in _AMLILoadDDB, probably fail after parsing DSDT/SSDT table, solved Patch (by Diderius): - Ignore status of _AMLILoadDDB in _ACPIInitializeDDB (v5512 jl short .text:00036214 => nop, nop) - 0xA5(0x03, ..., C0140008, ...) DSDT code have operation with unexpected type of arguments, partially solved This BSOD probably means some argument has datatype, allowed only in ACPI 2.0 v6666 & v5048 support only argument datatypes allowed in ACPI 1.0b specification Patch: - _ValidateArgTypes must always return "OK", even on realy wrong types (mov edi, 0xC0140008=>mov edi, 0x00000000 at head of _ValidateArgTypes) - 0xA5 (0x10006, ..., ..., ...), missing _DIS method for "PNP0C0F"s (PCI Interrupt Link Devices) in DSDT/SSDT table Patch (by Daniel_k): - Skip looking for PNP0C0F in _DisableLinkNodesAsyncWorker, (v5512 call strstr, ..., jz .text:0001BBBD => jmp .text:0001BBBD ) Intel Motherboards specific issues: 1) ACPI BSOD 0xA5 (0x02, ..., ..., ...), error in ACPIRangeValidatePciResources, ACPI vs E820 conflict, solved BSOD is generated by DSDT code like this: DWordMemory (ResourceProducer, PosDecode, MinFixed, MaxFixed, NonCacheable, ReadWrite, 0x00000000, // Granularity 0x00000000, // Range Minimum 0xDFFFFFFF, // Range Maximum 0x00000000, // Translation Offset 0xE0000000, // Length ,, _Y0E, AddressRangeMemory, TypeStatic) ... CreateDWordField (BUF0, \_SB.PCI0._Y0E._MIN, M1MN) // _MIN: Minimum Base Address CreateDWordField (BUF0, \_SB.PCI0._Y0E._MAX, M1MX) // _MAX: Maximum Base Address CreateDWordField (BUF0, \_SB.PCI0._Y0E._LEN, M1LN) // _LEN: Length M1LN = M32L /* External reference */ M1MN = M32B /* External reference */ M1MX = ((M1MN + M1LN) - One) Sometimes M1LN, M1MN, M1MX cannot be calculated properly and this code claim most of memory (E0000000 = 3.7Gb) as motherboard resource, this brings to conflict with E820 memory ranges list Patch: - memory check in ACPIRangeValidatePciResources must always return "OK" (v5512 jz short .text:0001E0BB => jmp short .text:0001E0BB) 2) Device Manager show conflict between Video Card and Motherboard resources Device IOTR(PNP0C02) claim 255 I/O adresses in range 0xFF00-0xFFFE, this range conflict with Video Card I/O range because vga has limitation to 10Bit I/O decoding. solved, two solutions: 1) Manual patching DSDT table, remove this lines inside method _CRS of IOTR device, so _CRS will return empty Local0: If ((ITS0 == One)) { ConcatenateResTemplate (Local0, BUF0, Local1) Local0 = Local1 } If ((ITS1 == One)) { ConcatenateResTemplate (Local0, BUF1, Local1) Local0 = Local1 } If ((ITS2 == One)) { ConcatenateResTemplate (Local0, BUF2, Local1) Local0 = Local1 } If ((ITS3 == One)) { ConcatenateResTemplate (Local0, BUF3, Local1) Local0 = Local1 } 2) Patch acpi.sys with injecting special code to override IOTR template buffer: In _Buffer opcode handler replace: mov eax, [ebx+14h] mov ecx, [ebp+arg_0] to call Check_IOTR_Buffer ... Check_IOTR_Buffer: cmp eax, 0Ah ; eax - size of buffer jnz short Skip mov eax, [ebx+30h] mov eax, [eax+10h] ; eax - buffer cmp dword ptr [eax], 00000147h ; need matching all 10 bytes jnz short Skip cmp dword ptr [eax+4], 0FF010000h jnz short Skip cmp word ptr [eax+8], 0079h jnz short Skip mov byte ptr [eax+7], 0 ; MAIN ACTION, set i/o range to 0 instead 255 Skip: mov eax, [ebx+14h] mov ecx, [ebp+arg_0] ret IOTR template defined as: Name (BUF0, ResourceTemplate () { IO (Decode16, 0x0000, // Range Minimum 0x0000, // Range Maximum 0x01, // Alignment 0xFF, // Length _Y21) }) in bytecode: 11 0D 0A 47 01 00 00 00 00 01 FF 79 00 3) No CPU power saving, most time CPU in C0 state even without cpu load Some part of acpi hardware is disabled, so CPU should not use nonexistent ACPI C2/C3 power savings, solved, two solutions (intelppm.sys): 1) C2/C3 States => C1 State : - in _InitializeAcpi2IoSpaceCstates replace offsets AcpiC2Idle and AcpiC3ArbdisIdle to offset AcpiC1Idle 2) C2/C3 States => C7+ States (default Windows 7 power saving mode, DPC Latency Checker shows significal increased latency in this mode): Replace Acpi2C3ArbdisIdle to: push ebx mov ebx, ecx push esi push 0 call _KeQueryPerformanceCounter mov [ebx], eax mov [ebx+4], edx mov eax, offset DummyMon xor ecx, ecx xor edx, edx monitor mov ecx, 1 mov eax, 60h mwait push 0 call _KeQueryPerformanceCounter mov [ebx+8], eax mov [ebx+0Ch], edx xor eax, eax pop esi pop ebx retn DummyMon - any unused 4 byes in .data segment Replace Acpi2C2Idle: push ecx push 0 call _KeQueryPerformanceCounter mov ecx, [esp+4+var_4] mov [ecx], eax mov [ecx+4], edx mov eax, offset DummyMon xor ecx, ecx xor edx, edx monitor mov ecx, 1 mov eax, 33h mwait push 0 call _KeQueryPerformanceCounter pop ecx mov [ecx+8], eax mov [ecx+0Ch], edx xor eax, eax retn 4) Programs show wrong timing results/works only first 3.5 sec Windows XP SP2+ uses disabled acpi timer, solved Skylake+ bioses by default disable ACPI hardware timer (register "ACPI Timer Control (ACPI_TMR_CTL)" in southbridge, see PDF), but WinXP SP2+ still uses disabled acpi timer for getting incremental time counter (acpi spec declare this counter as part of specification). WinXP detect existing this timer by checking special bit USE_PLATFORM_CLOCK in FACP ACPI table, modern bioses still set USE_PLATFORM_CLOCK=1 in acpi (mistake by programmers / inform Win7+ about existing HPET timer (not acpi timer!)) Patch (by Diderius) "HAL_acpitimer_fix" to use CPU TSC counter as performance timer/counter: - in HaliAcpiTimerInit force to ignore USE_PLATFORM_CLOCK and receive it always =0 (v.5512 jns short PAGE:8002934B => jmp short PAGE:8002934B) Compatibility fix ("HAL TSC frequency divider") Some programms do wrong calculation with high values of PerformanceCounter/PerformanceFrequency (HAL_acpitimer_fix set values to cpu freq), to avoid this problem values need to divide to much lesser value, Windows 7 just divide it to 1024, so timer frequency on 3600Mhz cpu is only 3.51Mhz Patch: - divide to 1024 values of PerformanceCounter/PerformanceFrequency, replace _HalpAcpiTimerQueryPerfCount to: 5) No driver for Intel SATA Controller - BSOD 0x7B(..,..,..,..) Windows XP/2003 support SATA controllers only in Legacy IDE mode, modern Intel chipsets has only AHCI mode, solved, many solutions: 1) Intel RST AHCI/RAID 11.2.0.1006 (iaStor.sys) 2) Intel RSTe AHCI/RAID 4.7.0.1098 backport by daniel_k (iaStorA.sys+iaStorF.sys) 3) StorAHCI by skulltera/OneCore (storahci.sys), compiled from Microsoft Windows 8.x DDK Samples, (require storport.sys from Windows 2003) 4) UniATA (opensource) 5) Intel RSTe AHCI/RAID 4.0.2.1019, for Windows 2003 only, enterprise controllers only(??) (iaStorA.sys+iaStorF.sys)) 6) StorAHCI from Windows 8 (require backported storport.sys from Windows 8) 7) StorAhci for Windows 2003, based on Microsoft Windows 8.x DDK Samples source code, https://sourceforge.net/projects/storahci-for-windows-2003/ Tip: Add PCI\VEN_8086&CC_0106 or PCI\VEN_8086&CC_010601 to *.inf as universal DEV_ID for any Intel AHCI Sata Controller AMD Motherboards Issues ACPI BSOD 0xA5 (0x0000000D, ..., ..., ...) duplicated _HID method Patch: - Skip DetectDuplicateHID processing (v5512 .text:00013F6C => jmp .text:00013F6C) BSOD 0x7E (..., ..., C0000005, ...) unknow error in AcpiArbCrackPRT Patch: (v5512 jnz short .text:0001BD6D => jmp short .text:0001BD6D) Intel USB3 Controller Drivers Intel released USB3.x drivers only for Windows 7/8/10, so there were many attempts to use drivers of other usb chip manufacturers. Most of them do not work at Intel hardware, some works, but have problems with PAE or USB3 ports. Following drivers confirmed to work in normal and PAE environment, solved, three solutions: 1) Microsoft Generic v6.2.9200.16384/v6.2.9200.22453 from Windows 8.0, recommended driver 2) AMD v1.1.0.0145 (need amdxhci_adresscalc_fix) 3) Fresco Logic v3.6.9.0 (extended to 32 ports) AMD and Fresco drivers have ssues with recognizing devices after plug<->unplug, sometimes ports go to power saving modes and can't back UAS (Attached SCSI Mass Storage) drivers also available, solved, many solutions: 1) UAS Driver from Windows 8 + storport.sys from Windows 2003, beta 2) UAS Driver from Windows 8 + storport.sys from Windows 7, beta 3) UAS Driver from Windows 8 + storport.sys from Windows 8, beta 4) VIA UAS Driver 5) Etron UAS Driver VIA and Etron UAS Drivers doesn't support Safe Remove, require fixes, solved (via_uas_fix, etron_uas_fix) By default VIA and Etron UAS works only with genuine vendor USB3.0 Driver, but they are generic(?) and can work with any USB3 driver vusbstor.inf: change USB_VIA\Class_08&SubClass_06&Prot_62 to USB\Class_08&SubClass_06&Prot_62 EtronXHCI.inf: change ENUSB\Class_08&SubClass_06&Prot_62 to USB\Class_08&SubClass_06&Prot_62 Patches for Microsoft Generic USB3 driver Windows 8 USB3 driver always report USB2 speed on inserted USB3 devices, MS call it "compatibility", but vendors driver report proper USB3 speed and dont have compatibility issues(?) Fix to report proper USB3 speed, usbhub3.sys (v6.2.9200.21180): .text:19C58: jnz 00019C63 => jmp 00019C63 (75 09 => EB 09) Patch for AMD driver (amdxhci_adresscalc_fix) This driver is known to have issues with PAE environment, need fix: - replace in amdxhc.sys: mov ecx, [esi+458h] ; esi+458h = store of 64bit adress mov eax, [esi+28h] mov [eax], ecx ; low part mov [eax+4], ebx ; dropped high part, ebx=zeroes..... to mov ecx, [esi+458h] mov eax, [esi+28h] mov [eax], ecx mov ecx, [esi+45Ch] ; HIGH part of 64bit mov [eax+4], ecx ; no more zeroes Patch for VIA UASP driver (via_uas_fix) Restore "Safe Remove": - replace in vusbstor.sys (v6.1.7600.4002): page:000209B4: mov [ebp+SurpriseRemovalOK], ebx -> NOPs (89 9D 70 FF FF FF 89 9D 68 FF FF FF => 90 90 90 90 90 90 89 9D 68 FF FF FF) Patch for Etron UASP driver (etron_uas_fix) Restore "Safe Remove": - replace in EtronSTOR.SYS (any version): OR dword ptr [eax+4], 0300h -> OR dword ptr [eax+4], 0000h 4GB+ RAM Support - Windows 2003 supports more than 4Gb RAM without additional actions, limited to some value depending "Edition" - Windows XP ServicePack1 supports more than 4Gb RAM without additional actions, limited to some value (16Gb ?) - Windows XP ServicePack2/3 don't support RAM above 4Gb, need patching, solved, many solutions: 1) PatchPae(v2) by wj32, remove limits only in kernel, lack of HAL_DMA patch 2) fix128/PatchPae(v3) by Evgen_b, contains unfinished HAL_DMA patch, kernel patch is OK 3) WinXPPAE(v2+) by Daniel_k, contains proper HAL_DMA patch, kernel patch is OK UEFI Boot - Bootmgr from some Vista Betas/Longhorns allow boot Windows XP x64 from UEFI x64, alpha, there is issues with Video card, https://www.betaarchive.com/forum/viewtopic.php?f=61&t=20327 - Boot Windows x32 on UEFI 32 UEFI32 on real hardware is rare, confirmed only on emulated environment, alpha, Guide LINK by Gelip - Quibble bootloader (experimental, opensource), alpha, no NTFS support, booting possible only if Windows installed on FAT partition, project page - https://github.com/maharmstone/quibble NVMExpress Drivers Many solutions: - Modified OFA 1.3/1.5 driver + storport.sys from Windows 2003 - MS Windows 7 NVMe Driver by daniel_k + backported storport.sys from Windows 7 - MS Windows 7 NVMe Driver + storport.sys from Windows 7 + Emu_Extender - Samsung NVMe driver + storport.sys GPT partitions Windows 2003 already supports GPT Partitions for non-booting disks, no need additional software Windows XP doesn't support GPT Partitions, solved for non-booting disks, one solutions: - Paragon GPT Loader enable access to 3TB+ Disks/GPT partitions (commercial product, currently not available for sale) Booting from GPT disk partially solved, need convert pure GPT to HybridMBR, Guide LINK by Levvon Saving crash dumps through storport based disk controller drivers To enable saving crash dumps with storport-based disk drivers on Windows XP need patch kernel (scsi support will be disabled) Disk Controller drivers written for Windows 8 mostly will not save crash dumps on disk, they use new API to get information from kernel about dump context List of patches: 1) IopGetDumpStack: Replace unicode string "scsiport.sys" to "storport.sys" This string is 3rd argument of "call _IopLoadDumpDriver@12" 2) IopGetDumpStack: Original XP kernel will disable loading storport emulator(diskdump.sys) if storport/miniport return "Device Object" This is not problem for Windows 2003/7/.., newer OS still load diskdump.sys even if storport/miniport return anything Replace "mov [ebp+ScsiDump], 0" with NOPs Example for ntkrpamp.exe v5512: PAGE:004A0E0F mov byte ptr [ebp-29h],0 -> NOP, NOP, NOP, NOP ]3) IopGetDumpStack: Storport doesnt use SCSI ports names and dont need to search name of driver, need to skip this block Example for ntkrpamp.exe v5512: in range PAGE:004A0F49-004A1018 replace first opcode with "jmp 4A1019" 4) Use diskdump.sys from Windows 2003 or Wondows 7 (Windows 8 version not tested) 5) IoInitializeCrashDump: XP kernel allocate for diskdump.sys buffer of 32Kb (same size in Windows 2000), diskdump.sys from Windows 2003+ expect buffer of 64Kb. To be compatible with new diskdump.sys need to increase buffer Replace "push 8000h" with "push 10000h" as 3rd arg of ExAllocatePoolWithTag call Modded AVX/AVX2 kernel Currently Proof-Of-Concept, only one kernel version supported LINK Projects for Developers/Advanced Users - Remote kernel debug over LAN or USB3 cable, https://github.com/MovAX0xDEAD/KDNET - ACPI DSDT/SSDT Patcher at boot time for any windows, https://github.com/MovAX0xDEAD/ACPI-Patcher - WinXP/W2003 ntoskrnl.exe Emu_Extender, https://github.com/MovAX0xDEAD/NTOSKRNL_Emu, https://msfn.org/board/topic/181615-ntoskrnl-emu_extender-for-windows-xp2003/ Research & Experiments Running Windows XP with "new generation" ACPI.sys taken from many Vista Beta/Longhorn version Running existing USB3 vendor's drivers on Intel USB3.0 controller Implementation of ACPI Timer/HPET on different windows generations Switching between DMA32/DMA64 under PAE Environment, Windows XP Switching between DMA32/DMA64 under PAE Environment, Windows 7 Unresolved Problems/Requested Features: - ACPI.SYS v.6666 lack 64-bit integers - ACPI.SYS v.6666 limits possible datatypes in arguments only to ACPI 1.0b Specification - Boot Windows XP/2003 x32 from UEFI x64 - Generating TRIM command for SSD in filesystem (NTFS/???) - Internal GPT support for x32 Windows XP by replacing disk.sys/partmgr.sys/??? from Windows 2003 - Boot Windows x32 XP/2003 from pure GPT - Restore full Windows XP SP1 implementation of PAE/DMA for Windows XP SP3 - Generic/Universal HDA Audio driver - CSM Emulator for UEFI x64 - DirectX 10/11 kernel support - NDIS 6.x for Windows XP/200310 points
-
The win32ss account on GitHub was flagged for an unspecified reason. I am going through the appeal process to restore it, but I will make sure the repository surfaces somewhere else such as GitLab even if GitHub does accept the appeal.10 points
-
OK everyone, take a deep breath and calm down. All new members of MSFN, or any other forum for that matter, should be treated with respect, and not have their initial contributions considered to be ignorant or naive. People come to forums like this to learn. As the strap line says here, "Where People Go To Know". As to whether this forum is 'obscure', I would venture that all technical forums are 'obscure' by their very nature, compared with the mass market options of social media. That does not make them any less valuable for those who choose to use them.10 points
-
Hi all and merry X-mass, I got bored and with the help of @Dixel and some amount of inspiration I sometimes get from @win32, I butchered the latest Opera 96 (110) to make it run on our beloved Vista ! This chinese browser Opera is based on the newest Chrome 110, which is officially supported only on Win 10 +. Also, I forced it to use its native hardware Skia engine 110. (which is now blocked on win 7 by default). For those who still drive their Sd.Kfz.8, Opera 95 and Chrome 109 are the last for win 7, so as of now, win 7 and the extended kernel for Vista are not able to run the 110 Chrome version. Please don't ask me about running it on WIn 7, I don't know (or won't tell) anything. In theory, it's possible for win 7 to run it. But only if you edit the browser code. (which is forbidden). Only Vista related questions. Thanks. Opera EULA says we can't edit their code, so I shall share my hacks/findings with @win32 and maybe he will be able to implement this in his next kernel release, so all of you could run it without the editing hacks.10 points
-
FWIW, there's nothing "standard" about NM27 here ; to add to what Mathwiz has posted: "Pale Moon" is an upstream browser application, which has a GUI from the pre-Australis Fx era; also, members here must understand the distinction between platform and application (Mozilla are the ones to blame for this confusion, because they had equated the Mozilla platform, not used solely by Fx, to their main browser, Firefox) ... When PM was at its major version 27 (did not support XP, Vista support was rudimentary), the platform it was built on was called Tycho, a fork of the Mozilla ESR 38 platform - the browser engine of PM27 was called Goanna version 3. The roytam1 fork derived from PM27 was/is New Moon 27 (NM27) ; as the web became more-and-more Googl-ised , PM27/Tycho started being crippled at loading many popular sites, so "upstream" (MCP) abandoned the Tycho platform and moved on, first to UXP Take 1 (aka Moebius), forked from a Mozilla 53.0a1 platform snapshot, and soon after to UXP Take 2 (just UXP now), forked from Mozilla ESR 52[.6] platform; PM27 became PM28; Pale Moon is currently at v33.0, but it's still built on UXP; both the paltform (UXP) and the browser application (PM) are being developed independently from Mozilla/Firefox... When upstream (MCP) abandoned Tycho (and PM27), roytam1 chose to keep his forked platform and browser (NM27) for the sake of Win2k/XP users on very old H/W, that doesn't support the SSE2+ instruction set ; as of this writing, NM27 and its browser engine, Goanna 3, is being "updated" based on a new "upstream", the developer (rmottola) behind the Artic-Fox project; this project aims to develop a (semi-)usable browser on old Macs, unsupported by Apple and the mainstream browser vendors; the project strives to "uplift" the browser from a Mozilla 38 platform snapshot (like in PM27/Tycho) to more recent versions, hence the large number of weekly updates (there's a lot of catching-up to do when you're still at a Fx mid-40s level) ... Also, Arctic-Fox isn't New Moon 27, hence several bugs that plague the latter are being reported by (the few?) NM27 users... To put it bluntly, I have now no need for this fork, because its web-compatibility is severely impaired in 2024; in addition to that, Roy is publishing SSE-compatible builds of NM28+St52, so if your old H/W can cope, it's advisable you use these instead of NM27... NM27 has inherited from PM27 a "status-4-ever" internal component, but as the platform is being updated by rmottola to Fx43+, this component has been partially BROKEN, breaking with it several download-related functions/extensions/userstyles/userscripts etc.; I have kept, for archival purposes, a NM27 build from 20220812, which seems to be the last with no such issues... As for NM28 (and St52), this is being updated mostly by backporting MCP code, especially in the platform aspect of it, and occasionally PM-specific (and Bk-specific) code is also being backported; and don't let the appVersion (28) confuse you ; Roy, for reasons he has explained in the past, decided to "freeze" the major version at 28, but latest NM28 embeds platform code to be found even in the latest PM33 "official" release ...10 points
-
New build of Serpent/UXP for XP! Test binary: Win32 https://o.rthost.win/basilisk/basilisk52-g4.8.win32-git-20221203-3219d2d-uxp-74a139ee2-xpmod.7z Win64 https://o.rthost.win/basilisk/basilisk52-g4.8.win64-git-20221203-3219d2d-uxp-74a139ee2-xpmod.7z source code that is comparable to my current working tree is available here: https://github.com/roytam1/UXP/commits/custom IA32 Win32 https://o.rthost.win/basilisk/basilisk52-g4.8.win32-git-20221203-3219d2d-uxp-74a139ee2-xpmod-ia32.7z source code that is comparable to my current working tree is available here: https://github.com/roytam1/UXP/commits/ia32 NM28XP build: Win32 https://o.rthost.win/palemoon/palemoon-28.10.6a1.win32-git-20221203-d849524bd-uxp-74a139ee2-xpmod.7z Win32 SSE https://o.rthost.win/palemoon/palemoon-28.10.6a1.win32-git-20221203-d849524bd-uxp-74a139ee2-xpmod-sse.7z Win64 https://o.rthost.win/palemoon/palemoon-28.10.6a1.win64-git-20221203-d849524bd-uxp-74a139ee2-xpmod.7z Official UXP changes picked since my last build: - Issue #2036 - Prevent GTK color picker from being frozen when launched from a modal XUL window (6d6d149b6) - Issue #2030 - (chore) refactor event dispatch functions (4d310562d) - Issue #2030 - Allow child nodes of button to participate in mouse hit tests (4354c7a1b) - Issue #2030 - Pref-gate default button event dispatch logic (3f073056d) - Issue #2030 - Dispatch click on common interactive ancestor if mousdown/up are not on the same element (b4dd10626) - Issue #2022 Follow-Up - Add autorelease to our manual NSView to prevent potential leaks. Also move titlebar overrides from BaseWindow to ToolbarWindow... This caused problems in Waterfox Classic on Ventura, while this didn't seem to be necessary in UXP... There is no need for those overrides in BaseWindow, so why risk potential problems. https://bugzilla.mozilla.org/show_bug.cgi?id=1576387 https://github.com/WaterfoxCo/Waterfox-Classic/commit/d7f5814dc089f615385a00db4dfe187c6aefa1af (e10eeed77) - No Issue - Fix building ldap on MacOS. Discovered this problem building Epyrus on MacOS, based on this Mozilla Bug: https://bugzilla.mozilla.org/show_bug.cgi?id=1652906 (7354cde3e) No official Pale-Moon changes picked since my last build. No official Basilisk changes picked since my last build. Update Notice: - You may delete file named icudt58l.dat inside program folder when updating from old releases. * Notice: From now on, UXP rev will point to `custom` branch of my UXP repo instead of MCP UXP repo, while "official UXP changes" shows only `tracking` branch changes.10 points
-
We are working with one of our friend from far East, Their soon gonna be a newer Chrome on XP , I will replace Boring SSL with OpenSSL [No need of Proxy for TLS1.3 and ECC] and port Angle Library to DirectX 9[ Smooth Scrolling] , He already got Chromium 92 working. Please Kindly have patience and i cannot reveal more as per my promise to him. Dont ask me when it is coming , but it is coming.10 points
-
The fact that Feodor has been able to do as much as he has, given the circumstances, is truly incredible. I admire his dedication and enthusiasm for the projects he's worked on over the years...his 'old' MyPal (29.3.0) is still one of my primary daily-use browsers in XP, and it's been very exciting to see the progress that has been made so far on the newer 68. He's one talented coder, as his 'resurrected' MyPal 68 has proven...it's a shame to look back on that whole fiasco nearly one year later, because the Pale Moon developers had an opportunity to take the highest of high roads by inviting Feodor to work with them and even help them restore official compatibility to benefit XP/Vista users, but instead they fought and alienated him and many others. In a more ideal world, there would have been a mutual respect that could have led to a long-term partnership, maybe even a friendship. I'm genuinely praying for him, his family, and all of his friends...and of course, I'm keeping Roy in my thoughts too as he's in Hong Kong. They both come from places that have been through so much, especially in recent times. To Roy and Feodor: thank you both VERY much for everything you have done. Your efforts have never, ever been in vain.10 points
-
Look's like CloudFlare nightmare soon may be over, Pale Moon community reach out to press and CloudFlare team apparently noticed they negative coverage in press: Moonchild wrote: The Register article title is hilarious: Cloudflare's bot bouncer blocks weirdo browsers We finally know what browsers we using - a weirdo browsers.9 points
-
ListDisk This tool provides detailed information about connected physical disks, including their partitions and volumes. Download https://github.com/GeorgeK1ng/ListDisk/releases Features Mounting/unmounting partitionsSetting partition labelsModifying MBR partition attributes Available Commands /mount - Mounts a partition to a specified drive letter./unmount - Unmounts a specified partition or drive letter./setlabel - Sets a new label for a specified partition./setactive - Sets or clears the bootable flag of a partition./settype - Changes the MBR type of a partition. Usage Examples /mount 0 1 U - Mounts Partition 1 on Disk 0 as U: drive./unmount 0 1 - Unmounts Partition 1 on Disk 0./unmount U - Unmounts U: drive./setLabel 0 1 Lbl - Sets 'Lbl' as the label for Partition 1 on Disk 0./setactive 0 1 - Marks Partition 1 on Disk 0 as bootable./setactive 0 1 80 - Sets the boot flag for Partition 1 on Disk 0./setactive 0 1 00 - Clears the boot flag for Partition 1 on Disk 0./settype 0 1 0x17 - Sets Partition 1 on Disk 0 to type NTFS Hidden (0x17)./settype 0 1 0x07 - Sets Partition 1 on Disk 0 to type NTFS (0x07). Requirements Operating System: Windows XP and newer. Note for Windows XP Users: This tool requires the installation of the Microsoft Visual C++ Redistributable. Please install it from this link.Compatible with Windows Preinstallation Environment (WinPE).Place ListDisk in %WinDir%\system32 to make it easy accessible from commandline! Note: Use this utility with caution. Incorrect usage may affect data integrity.9 points
-
9 points
-
People reported success by re-registering these dlls: softpub.dll, wintrust.dll, initpki.dll, dssenh.dll, rsaenh.dll, gpkcsp.dll, sccbase.dll, slbcsp.dll, mssip32.dll, cryptdlg.dll And reboot, of course, to apply changes.9 points
-
Dear Jody, and I mean this in a genuine way , you of all people shouldn't come back with the very same queries, because it was I who answered your similar queries in the not so distant past... What it all comes down to is: 1. do you have a grasp of what open source code is? 2. do you have a grasp of what a forked open-source code repo is? 3. do you have a grasp of what a platform and an application built on it is? If not, any answer you'll get from me won't make much sense to you, and I'm sorry to say that there's no simplistic yes/no answer to your re-iterated queries above... MCP maintain the official UXP application platform, its repo is hosted below in: https://repo.palemoon.org/MoonchildProductions/UXP/ There are several branches in that repo, main ones being master and release MCP maintain the official Pale Moon browser application, its repo is hosted in: https://repo.palemoon.org/MoonchildProductions/Pale-Moon/ Again, the two more important branches in that tree are master and release The official Pale Moon releases are being issued at least once a month, compiled from code from the UXP release platform branch and PM release application branch. Likewise, Basilisk-Dev maintains the official Basilisk browser application, its repo hosted in: https://repo.palemoon.org/Basilisk-Dev/Basilisk/ Two branches of note there, too; master and release The official Basilisk releases are being issued monthly, or as the dev's time permits, compiled from code from the UXP release platform branch (by MCP) and the Bk release application branch. OTOH, roytam1 maintains a somewhat different development scheme; he maintains a code "smorgasbord" below: https://github.com/roytam1/UXP This is a fork of the official UXP platform repo (see above); the tracking branch of that repo follows more closely the master branch of the official UXP platform (see above); the forked UXP repo, by now, is different to the original one in various ways, one of which is in restoring WinXP+Vista support (which also entails several lib differences, like in ffvpx), another one is keeping Mozilla features MCP have dumped long ago (e.g. Web Extensions, Tab Containers, half-baked e10s code, EME, e.a); also, the NSS lib in "our" browsers is somewhat different to the one MCP maintain; that is why profiles between the official apps and roytam1 apps aren't 100% interchangeable... The UXP repo by roytam1 also encompasses application-specific code, ported from the official PM master branch and the official Bk master branch, again chosen selectively (i.e. not all Pale Moon features end up in NM28, not all Bk features end up in St52, but most do). The custom branch of roytam1's UXP repo holds the code snapshots that get compiled weekly to produce the NM28 and St52 releases; if you're still following: It's difficult to directly compare the official releases to the roytam1 ones, because the first follow a different code development scheme + release schedules, but indeed all the vital code parts (features, bug/security fixes, etc) from the former find their way to the latter, sooner or later... As a rule, based on what I detailed above, the "latest NM28 release" should contain all the "applicable" platform/app code found in the last PM release, and then some (i.e. code in the official master branches authored after the release was cut) ; likewise, the "latest St52 release" should contain all the "applicable" platform/app code found in the last Bk release, and then some (i.e. code in the official master branches committed after the release was cut - on that note, it's sad that Basilisk-Dev has admitted elsewhere that he's withholding on purpose to publish Bk code in its master branch until "the very last moment", so that "we" here be incapable of using it "ahead of time"...). The only exception to the above is when "upstream" collectively (MCP/Basilisk-Dev) make a "mid-week release"; in that case, the builds released by roytam1 on the Saturday that immediately follows those mid-week upstream releases will have "caught up with them", so to speak... Jody and others, please bookmark this post and revisit it as needed, so that I don't get asked the same things again and again - and no, one "can't have one's cake and eat it, too"; if one wants to keep using "these" browsers, one must also "keep in touch" with how things are developing "here" ; the issue of "precious personal time" has come up many a times in the past, but be sure I'm just a volunteer here, my personal time is as precious (to me) as is yours... PS: Changelogs are NOT confusing, if one ever made a simple effort to understand what they do represent; they're made of git-commits between the previous and the current release, often times they're identical to the "upstream" commits they were ported from; so one can easily verify how far ahead of (or behind of or different to) the upstream code the current release happens to be...9 points
-
Some thing I have been work on in my very little free time. You know "Browservice" project right? He made a software that pushes endless stream of JPEG images to the browser that contain a website rendered by Chromium engine. Complete with fake address bar and front end JavaScript to capture keyboard and mouse. The idea sounds so ridiculous, so crazy, but it actually works on almost every OS and almost every old browser. Problem of "Browservice" is it doesn't feel convincing. IE constantly downloading images and status bar goes crazy (it appears that the memory leak exists). Also very slow when website has a animating. I did something similar but using RDP. Only for IE5 and IE6. Should work Win98/ME/2000/XP<SP3. I develop in XPSP2 IE6 and WinME IE 5.5 for now. Since it's ActiveX control, I am inside of IEXPLORE.EXE and have full control (that's how drive-by downloads installed spyware and virus back in the days). I use the power to intercept the menu, toolbar, address bar, status bar, etc. IE becomes only a bit of GUI under my control. All commands are redirected to remote server running Chromium engine there. RDP has the feature "Virtual Channel" to send messages (WTSVirtualChannelOpen etc.) My implementation so far browsing experience feels 99% like using real Internet Explorer because RDP protocol is much faster and get clipboard support, access to local hard drive, sound, video streaming, etc. for free by Microsoft. Unfortunately still very early in development. Downloads not yet work. History not yet work. Popup window not yet work (very difficult). But I hope that in a few months from now good old Win9x and Win2000 can join a modern Internet again. Backend in C#. Frontend in Visual Basic 6 with OLEEXP and patched SSUBTMR (just to prove it can be done, but it is painful). Maybe you will say that's the fake screenshot. Okay, you can do it. I don't have the argument at the moment. But soon I hope to show it running on real hardware.9 points
-
New build of Serpent/UXP for XP! Test binary: Win32 https://o.rthost.win/basilisk/basilisk52-g4.8.win32-git-20230805-3219d2d-uxp-65de5a7185-xpmod.7z Win64 https://o.rthost.win/basilisk/basilisk52-g4.8.win64-git-20230805-3219d2d-uxp-65de5a7185-xpmod.7z source code that is comparable to my current working tree is available here: https://github.com/roytam1/UXP/commits/custom IA32 Win32 https://o.rthost.win/basilisk/basilisk52-g4.8.win32-git-20230805-3219d2d-uxp-65de5a7185-xpmod-ia32.7z source code that is comparable to my current working tree is available here: https://github.com/roytam1/UXP/commits/ia32 NM28XP build: Win32 https://o.rthost.win/palemoon/palemoon-28.10.7a1.win32-git-20230805-d849524bd-uxp-65de5a7185-xpmod.7z Win32 IA32 https://o.rthost.win/palemoon/palemoon-28.10.7a1.win32-git-20230805-d849524bd-uxp-65de5a7185-xpmod-ia32.7z Win32 SSE https://o.rthost.win/palemoon/palemoon-28.10.7a1.win32-git-20230805-d849524bd-uxp-65de5a7185-xpmod-sse.7z Win64 https://o.rthost.win/palemoon/palemoon-28.10.7a1.win64-git-20230805-d849524bd-uxp-65de5a7185-xpmod.7z Official UXP changes picked since my last build: - Issue #2026 - Part 1 - Implement BigInt64 and BigUint64Array. https://bugzilla.mozilla.org/show_bug.cgi?id=1456569 (b64643e410) - Issue #2026 - Part 2a - Support BigInt in NumberFormat and toLocaleString. https://bugzilla.mozilla.org/show_bug.cgi?id=1543677 (d972016c23) - Issue #2026 - Part 2b - Format BigInts representable as int64_t without first converting them to strings. https://bugzilla.mozilla.org/show_bug.cgi?id=1543677 (3ce9cf4deb) - Issue #2026 - Part 3a - Add support for BigInt in devtools. (Server side) https://bugzilla.mozilla.org/show_bug.cgi?id=1527867 (e861cd3b3a) - Issue #2026 - Part 3b - Add BigInt Devtools support. (legacy frontend) (61efc86b21) - Issue #2026 - Part 3c - Add BigInt Devtools support. (new frontend) (9042881cea) - Issue #2026 - Part 4 - Fill in missing dense elements case and fix a comment. https://bugzilla.mozilla.org/show_bug.cgi?id=1456569 Skipped this during the initial implementation, not sure when or if this code path is used, but I figure it should be there just in case. Also fix debug builgs by removing an no longer valid MOZ_ASSERT. (b7e487bdf1) - Issue #1240 - Follow-up: Fix incorrect values in Number() constructor. https://bugzilla.mozilla.org/show_bug.cgi?id=1466893 Our code base was using the return value to create the Number object. However with the BigInt changes, it is no longer stored in rval, use args[0]. (df03810723) - Issue #1240 - Follow-up: Add missing JSVAL_TYPE_BIGINT cases in JitFrames.cpp. As pointed out by roytam1 during testing with Discord. (5c3cedb141) No official Pale-Moon changes picked since my last build. No official Basilisk changes picked since my last build. Update Notice: - You may delete file named icudt*.dat inside program folder when updating from old releases. * Notice: From now on, UXP rev will point to `custom` branch of my UXP repo instead of MCP UXP repo, while "official UXP changes" shows only `tracking` branch changes.9 points
-
New build of Serpent/UXP for XP! Test binary: Win32 https://o.rthost.win/basilisk/basilisk52-g4.8.win32-git-20230715-3219d2d-uxp-787a64cf9-xpmod.7z Win64 https://o.rthost.win/basilisk/basilisk52-g4.8.win64-git-20230715-3219d2d-uxp-787a64cf9-xpmod.7z source code that is comparable to my current working tree is available here: https://github.com/roytam1/UXP/commits/custom IA32 Win32 https://o.rthost.win/basilisk/basilisk52-g4.8.win32-git-20230715-3219d2d-uxp-787a64cf9-xpmod-ia32.7z source code that is comparable to my current working tree is available here: https://github.com/roytam1/UXP/commits/ia32 NM28XP build: Win32 https://o.rthost.win/palemoon/palemoon-28.10.7a1.win32-git-20230715-d849524bd-uxp-787a64cf9-xpmod.7z Win32 IA32 https://o.rthost.win/palemoon/palemoon-28.10.7a1.win32-git-20230715-d849524bd-uxp-787a64cf9-xpmod-ia32.7z Win32 SSE https://o.rthost.win/palemoon/palemoon-28.10.7a1.win32-git-20230715-d849524bd-uxp-787a64cf9-xpmod-sse.7z Win64 https://o.rthost.win/palemoon/palemoon-28.10.7a1.win64-git-20230715-d849524bd-uxp-787a64cf9-xpmod.7z Official UXP changes picked since my last build: - No Issue - Fix debug builds on ARM Mac. mach_override used by the IO Poisoner used in debug mode is not support on ARM. https://bugzilla.mozilla.org/show_bug.cgi?id=1658385 (ffa0c4d86) - Issue #2268 - Fix Mac packaging by making the individual parts configurable. Add --with-macbundle-entitlement= to specify alternate entitlements or "none" Add --with-macbundle-type=hybrid to use the old DMG format. (eb2cca724) - Issue #2255 - Add support for Maybe<T&> https://bugzilla.mozilla.org/show_bug.cgi?id=1620568 Make Maybe<T>::emplace() work when T is const https://bugzilla.mozilla.org/show_bug.cgi?id=1335780 (efde4d468) - Issue #2255 - Use Maybe<> in the Performance API. (1f5eaee10) - Issue #2255 - Fix build bustage on Linux. Need #include <utility> to ensure std::forward is available. (323007ec3) - Issue #2271 - Separate cloning of native and interpreted functions (3eb7729d0) - Issue #2271 - Use declared names of self-hosted functions for cloning (76052fcda) No official Pale-Moon changes picked since my last build. Official Basilisk changes picked since my last build: - [Basilisk] Add pref to control history menu length. (11d652975) - [Basilisk] Follow-up: Don't show link items when pref is less than 1. (ab1a1e893) - [Basilisk] Follow-up: Throw errors on invalid values. (803bde238) - [Basilisk] Front-end fixes (748cac6e8) My changes picked since my last build: - [Basilisk] fix missing closing brace in function HistoryMenu from previous commits (cf35c4742) pdate Notice: - You may delete file named icudt*.dat inside program folder when updating from old releases. * Notice: From now on, UXP rev will point to `custom` branch of my UXP repo instead of MCP UXP repo, while "official UXP changes" shows only `tracking` branch changes.9 points
-
New build of Serpent/UXP for XP! Test binary: Win32 https://o.rthost.win/basilisk/basilisk52-g4.8.win32-git-20230311-3219d2d-uxp-6f99b9744-xpmod.7z Win64 https://o.rthost.win/basilisk/basilisk52-g4.8.win64-git-20230311-3219d2d-uxp-6f99b9744-xpmod.7z source code that is comparable to my current working tree is available here: https://github.com/roytam1/UXP/commits/custom IA32 Win32 https://o.rthost.win/basilisk/basilisk52-g4.8.win32-git-20230311-3219d2d-uxp-6f99b9744-xpmod-ia32.7z source code that is comparable to my current working tree is available here: https://github.com/roytam1/UXP/commits/ia32 NM28XP build: Win32 https://o.rthost.win/palemoon/palemoon-28.10.6a1.win32-git-20230311-d849524bd-uxp-6f99b9744-xpmod.7z Win32 IA32 https://o.rthost.win/palemoon/palemoon-28.10.6a1.win32-git-20230311-d849524bd-uxp-6f99b9744-xpmod-ia32.7z Win32 SSE https://o.rthost.win/palemoon/palemoon-28.10.6a1.win32-git-20230311-d849524bd-uxp-6f99b9744-xpmod-sse.7z Win64 https://o.rthost.win/palemoon/palemoon-28.10.6a1.win64-git-20230311-d849524bd-uxp-6f99b9744-xpmod.7z Official UXP changes picked since my last build: - Issue #1693 - Use scoped enums for IDBTransaction. (c920f32df) - Issue #2135 - Bug 1430303: Implement ShadowRoot.pointerLockElement (3dfffeaec) - Issue #2135 - Bug 1430305: Implement ShadowRoot.fullscreenElement (e286eb8ad) - Issue #2135 - Bug 1413102: Ensure Shadow DOM boundaries are dealt properly in event handling (24572438a) - Issue #2135 - Bug 1413102 (Follow-up): Ignore current target because of shadow DOM retargeting (1bb2009f6) - Issue #2135 - Bug 1323815: FocusEvent.relatedTarget should work consistently with MouseEvent.relatedTarget (1185cfe3f) - Issue #2135 - Bug 1438129: Remove ShadowRoot.applyAuthorStyles. (3350af82c) - Issue #2135 - Bug 1430301: Implement ShadowRoot.elementFromPoint/elementsFromPoint (e64aeea52) - Issue #2135 - Bug 1356496: Don't use nsIDOM* in ConfirmSelectionInBody (b2c77e5ed) - Issue #2135 - Bug 1066965: Make contentEditable and spellchecking to work in Shadow DOM (010db07bf) - Issue #2135 - Bug 1453789: Remove Element.createShadowRoot (45c179d01) - Issue #2135 - Bug 1410578: Make <link rel="stylesheet"> work in shadow trees (588c2154a) - Issue #2135 - Bug 1455891/Part 1: Improve StyleChildrenIterator (263b719ef) - Issue #2135 - Implement sequential focus navigation for shadow DOM (56193120c) - Issue #2135 - Bug 1518795: Properly track responsive content in a connected ShadowRoot (7b395189a) - Issue #2135 - Bug 1329877: Optimize AncestorFilter usage in lazy frame construction (7924a2f60) - Issue #2135 - Bug 1414692: Adopt shadow roots when adopting a shadow host across documents (b72ddcf65) - Issue #2135 - Bug 1393806/Part 1: Change nsNodeUtils cloning/adopting stuff to use an ErrorResult for errors (e65a864a3) - Issue #2135 - Bug 1393806/Part 2: Modify AdoptNodeIntoOwnerDoc to use the non-XPCOM version of document.AdoptNode (3062964d2) - Issue #2135 - Bug 1393806/Part 3: Change dom::ReparentWrapper to take an ErrorResult (9f0fb9c16) - Issue #2135 - Bug 1425864: Ensure printing documents which have shadow DOM works (015148fcc) - Issue #2135 - Bug 1419803: Use GetComposedDoc instead of GetUncomposedDoc in ContentEventHandler (70d493586) - Issue #2135 - Bug 1433669/Part 1: Remove dead function (2f9186959) - Issue #2135 - Bug 1433669/Part 2: Flush the document instead of the shell in ContentEventHandler (4d778226e) - Issue #2135 - Follow-up: Fix crash for passing nullptr as an argument to the aNodesWithProperties parameter (c194fbf6a) - Issue #2135 - Follow-up: Fix typo (9cb33ab84) - Issue #2046 - correct debug assert for intl_FormatRelativeTime() (3fb11e542) - Issue #2135 - Follow-up: Fix potential crash if shadow root is null (ad929c5dd) - Issue #2136 - Part 1: Implement CSS inset property (21d468ee6) - Issue #2136 - Part 2: Regenerate devtools CSS database (ae26d8a04) - Issue #2143 - Implement CSS env() Environment Variables (2b903a20b) - Issue #2135 - Follow-up: Ensure document is not null in nsImageLoadingContent::BindToTree (cfef3fa48) - Issue #2148 - Root the RegExpShared in RegExpMacroAssembler. (1f0df8f42) Official Pale-Moon changes picked since my last build: - [Pale-Moon] Set compatversion for hardcoded overrides to 102.0 (5a627b6ce) - [Pale-Moon] Issue #1915 - [SSUAO] Add override for Instagram (c8488397e) Official Basilisk changes picked since my last build: - Revert "[Basilisk] Fade out tab label on overflow instead of ellipsis" (15e3a38b5) My changes since my last build: - [Basilisk] ported PM version of tab caption fading to here (2a32b18f4) - [Basilisk] add tab caption fading to CtrlTab (f159e44b2) - [Pale-Moon] add tab caption fading to CtrlTab (5db2ae1aa) - Revert "revert last rev (7faa37b7) and revert rev b7e45308 and 9824659d instead." (1b1d672dc) - Revert "reverting rev 22dc363c and 233802c9 for now since I got a crash in destructor of RegExpShared." (6f99b9744) Update Notice: - You may delete file named icudt58l.dat inside program folder when updating from old releases. * Notice: From now on, UXP rev will point to `custom` branch of my UXP repo instead of MCP UXP repo, while "official UXP changes" shows only `tracking` branch changes.9 points
-
@win32, @legacyfan Guys, you do understand you need to block Opera from spying, right ? Here I give you my ready-made scripts for netsh. This is for Windows Firewall. I traced the most important IPs were it leaks your data. Enjoy ! Advfirewall Firewall add rule name="OperaChinoSpy_OFF" dir=in profile=any localip=any remoteip=3.120.0.0/14,13.32.23.0/24,34.208.0.0/12,37.228.104.0/21,52.58.0.0/15,54.191.0.0/16,74.125.131.94,74.125.205.102,78.46.0.0/15,81.19.82.98,82.145.192.0/19,82.145.208.0/22,82.145.212.0/24,82.145.213.0/24,82.145.215.0/24,82.145.216.0/22,82.145.220.0/22,91.203.97.0/24,107.167.123.0/24,141.0.8.0/22,141.0.12.0/22,173.194.73.103,185.26.180.0/22,195.189.142.0/24,195.189.143.0/24,213.180.204.193 protocol=any action=block Advfirewall Firewall add rule name="Opera_Spy_block" dir=out profile=any localip=any remoteip=3.120.0.0/14,13.32.23.0/24,34.208.0.0/12,37.228.104.0/21,52.58.0.0/15,54.191.0.0/16,74.125.131.94,74.125.205.102,78.46.0.0/15,81.19.82.98,82.145.192.0/19,82.145.208.0/22,82.145.212.0/24,82.145.213.0/24,82.145.215.0/24,82.145.216.0/22,82.145.220.0/22,91.203.97.0/24,107.167.123.0/24,141.0.8.0/22,141.0.12.0/22,173.194.73.103,185.26.180.0/22,195.189.142.0/24,195.189.143.0/24,213.180.204.193 protocol=any action=block9 points
-
I found that there are ultimately four reasons why Chromium is broken on NT 6.x: 1. New imports in kernel32 and userenv. They can all be stubbed, not hard to fix. (Vista/7; 8.x has them) 2. Use of job object APIs in ways that are only supported on 8.x (without sandbox) and 10 (with sandbox) 3. Use of new NtQueryInformationProcess class for enumerating process handles; if it can't be used, the content process will be terminated (8.0 and below, sandbox only) 4. Use of new DirectWrite factories, like IDWriteFactory3, which was introduced in Windows 10 #1 is taken care of, I'm getting there with #2 and then I should be able to do #3. #4's solution is actually quite simple; copy over a Windows 10 DWrite.dll to use with Chromium using DLL redirection methods (I used 10.0.17763.1 and I think 10240 and up should work too). Then patch these DLL names in the import table with a hex editor or CFF explorer: api-ms-win-core-libraryloader-l1-2-0.dll -> kernel32.dll api-ms-win-core-localization-l1-2-2.dll -> kernel32.dll This is sufficient to run the latest Chromium browser snapshot on Windows 8: Right now there are truly missing functions on Windows Vista and 7, in api-ms-win-core-delayload-l1-1-0.dll and api-ms-win-core-delayload-l1-1-1.dll. Some of those return function pointers so they can't be stubbed.9 points
-
New build of Serpent/UXP for XP! Test binary: Win32 https://o.rthost.win/basilisk/basilisk52-g4.8.win32-git-20230114-3219d2d-uxp-12b3c5e5f-xpmod.7z Win64 https://o.rthost.win/basilisk/basilisk52-g4.8.win64-git-20230114-3219d2d-uxp-12b3c5e5f-xpmod.7z source code that is comparable to my current working tree is available here: https://github.com/roytam1/UXP/commits/custom IA32 Win32 https://o.rthost.win/basilisk/basilisk52-g4.8.win32-git-20230114-3219d2d-uxp-12b3c5e5f-xpmod-ia32.7z source code that is comparable to my current working tree is available here: https://github.com/roytam1/UXP/commits/ia32 NM28XP build: Win32 https://o.rthost.win/palemoon/palemoon-28.10.6a1.win32-git-20230114-d849524bd-uxp-12b3c5e5f-xpmod.7z Win32 IA32 https://o.rthost.win/palemoon/palemoon-28.10.6a1.win32-git-20230114-d849524bd-uxp-12b3c5e5f-xpmod-ia32.7z Win32 SSE https://o.rthost.win/palemoon/palemoon-28.10.6a1.win32-git-20230114-d849524bd-uxp-12b3c5e5f-xpmod-sse.7z Win64 https://o.rthost.win/palemoon/palemoon-28.10.6a1.win64-git-20230114-d849524bd-uxp-12b3c5e5f-xpmod.7z Official UXP changes picked since my last build: - Issue #2073 - m-c 1382683: Accelerate GIF decoding to SurfacePipe (7d75c2717) - Issue #2073 - m-c 1343341: Infrastructure necessary to allow discarding of animated images (squashed) (eac8afce3) - Issue #2073 - m-c 523950: Discard decoded frames of very large GIF animations (squashed) (e96122ede) - Issue #2073 - m-c 1383404: make SourceBuffer::Compact more efficient (squashed) (03a4a17cc) - Issue #2073 - m-c 1651587: Make image::Image release efficient on main thread (9a39001cc) - Issue #2073 - m-c 1546500: Avoid dispatching synchronous thread shutdown runnables (a6a420259) - Issue #2073 - m-c 1454149: Do not advance animated images which are not displayed (845411a7a) - Issue #2084 - Part 1: Remove CSSUnprefixingService.js and associated code (db3ce13f2) - Issue #2084 - Part 2: Simplify logic in CSSParserImpl::LookupKeywordPrefixAware (56e636d8e) - No issue - Fix invalid neq check on assert in RegExpParser (2f7f622cd) - Issue #2087 - Don't throw on lacking PresShell in SetFontInternal (efeb0e3e9) - Issue #80 - Re-unify some more missed sources in js/src (ee541a533) No official Pale-Moon changes picked since my last build. No official Basilisk changes picked since my last build. My changes since my last build: - turn on TLS_RSA_WITH_AES_128_GCM_SHA256 to fix download from mega (8f801c5c3) - [Basilisk] follow-up Issue UXP#2084 - remove CSSUnprefixingService from packaging (3ff80c5af) Update Notice: - You may delete file named icudt58l.dat inside program folder when updating from old releases. * Notice: From now on, UXP rev will point to `custom` branch of my UXP repo instead of MCP UXP repo, while "official UXP changes" shows only `tracking` branch changes.9 points
-
I am so sad. He was a great person. I knew him since my first days on MSFN, many, many years ago, and besides the public interactions on the board we had a lot of correspondence via PM's, both on computing and on a whole range of different topics, from cinema and TV to art and linguistics (he could read and understand very well Italian and I can understand a very little Portuguese, we had a common interest in Latin - as root of both languages - and we often exchanged opinions on these and many other things), I considered him a friend. I will greatly miss him and our exchanges. Besides his great work in helping and advising other people on technical matters, he was always polite and just (as a moderator), while often managing to keep a veil of humour in his posts. He told me about his illness, describing it as a "a quite mean cancer", from the tone of his latest messages he was fighting fiercely against it, and was hoping to defeat it only one month before, at the end of september. May he R.I.P. jaclaz9 points
-
Hello everyone. Glad to see MSFN is still online! I'm happy to announce that the list has been migrated over to the Eclecboard forum. Huge thanks to my best friend @docR for migrating it for me to his forum and making sure all the formatting is correct. Here's the link to the sister thread on EclecBoard: https://forum.eclectic4un.me/viewtopic.php?f=27&t=113 Don't worry, I will continue to update the list on MSFN & EclecBoard for as long as both forums remain online. I am going to resume updating it again soon as I've been extremely busy in my personal life lately (and thankfully am now in a healthy, loving relationship ). After leaving the toxicity I was in before, I feel much better and have regained interest in Vista and the list again and hope to get everything squared away with it within the next couple of weeks, as there's going to be a LOT of new changes made since October 2020... Hope everyone is doing well!9 points
-
This thread is a little bit confusing especially for people looking for help. So I have made a complete guide with all tips and steps which have to be performed to restore access to Microsoft Update web site and are working for me. Of course at your own risk without any guarantee! And just to clarify: I am not the author or contributor of these patches and tools. I am a user and have examined my problems while restoring MU in Windows XP. This guide is the result of my examinations to help other users. Of course I did some modifications due to the fact that some patches don't work properly or something is missing. If you want improvements of these tools and patches, please contact the authors! Complete guide for restoring Microsoft Update in IE To be successful in restoring of access to MU web site, you have to keep the order of following steps. Please, do not change this order! 1. Check BIOS and Windows date and time incl. correct time zone. Perform a time sync! 2. If you have used "WSUS server" in combination with "WUMT" in the past remove it completely by "Remove_wsus.cmd". This batch file does not work properly, so you have to remove this registry key manually: HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\WindowsUpdate. You can let "Remove_wsus.cmd" perform this by adding following line (without quotes): "reg delete "HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\WindowsUpdate" /f". Start Automatic Update service. In system panel Automatic Update may not be shown greyed out. 3. Go to Windows Services. Three system services are absolutely important for MU: bits, wuauserv and cryptsvc. These services should have been started and set to automatic. 4. Configure Internet Explorer. Internet Zone to standard, Trusted Zone to high with only these three urls related to MU: http://www.update.microsoft.com, https://www.update.microsoft.com and http://update.microsoft.com. Credits to @maile3241 and @AstroSkipper. Go to Internet Explorer Options, Advanced. Check if TLS 1.2 is enabled. Uncheck entry "Check for server certificate revocation". 5. Before installing updates apply "PosReady.reg" if not already done. 6. Install these four updates KB4467770, KB4019276, KB4493435, KB942288-V3. Credits to @maile3241. 7. Apply "Tls 1.2.reg". Credits to @maile3241 8. Execute "rootsupd.exe". 9. Install the latest Windows Update Agent 7.6. It's version 7.6.7600.256. Download link: http://download.windowsupdate.com/windowsupdate/redist/standalone/7.6.7600.320/WindowsUpdateAgent-7.6-x86.exe 10. Install "ProxHTTPSProxy". Download link: https://i430vx.net/files/XP/ProxHTTPSProxyMII_REV3d_PY344.7z, credits to @heinoganda. Here you have to edit the config file "config.ini". Under section [SSL No-Verify] I added fe2.update.microsoft.com and deleted update.microsoft.com under sections [SSL Pass-Thru] and [BYPASS URL]. This is working for me. 11. Download and install one of these packages: an English all in one version, credits to @Windows7fan from MDL, @xpandvistafan, @maile3241 and @AstroSkipper from MSFN: https://drive.google.com/u/0/uc?id=1z5NGORov8OS7iBkoFVsvWOTOE1_LCjoQ&export=download or a German all in one version, based on version above, modified and updated by @AstroSkipper: https://www.mediafire.com/file/0y1zmwv8z4lch9s/Restore_WU_XP_DE.7z/file. Credits to @Windows7fan from MDL, of course. Here you have to check if "install.cmd" did its job properly i.e. all commands in "install.cmd" should have been performed completely. Additionally you have to verify the existence of patched "wuaueng.dll" in both folders system32 and system32\dllcache in form of a binary comparison.. Be aware of SFC which tries to restore an original old version of this file! After patching restart your computer and recheck! Verify if really all registry entries have been added.i All bold files mentioned here are in these all in one versions included. They can be installed manually (all registry entries of "install.cmd" have to be added manually too) or automatically by applying "install.cmd". 12. If you have problems in configuring ProxHTTPSProxy, or you get error code 0x80072f8f while trying to access MU web site, have a look in my thread: 13. Use "CAupdater" or "Certificate Updater 1.6" to update your root certificates. Download link of Certificate Updater 1.6 can be found here: 14. If the button "Check for updates" doesn't work on MU, close Internet Explorer, open MU from Start Menu again and in most cases it will load successfully. 15. If you have a fresh installation or a reinstallation of Windows XP, it seems to be necessary to install MU ActiveX Control manually because it won't be downloaded automatically any longer. Without any confirmation by me (no opportunity to check it), here is a guide how you can do that. Credits to @maile3241: 16. If on MU web page error code 0x80072F78 appears, turn off your firewall temporarily. If MU is working now, add the program "wuauClt.exe" into the exception list of your firewall and turn your firewall back on. In any case ProxHTTPSProxy or HTTPSProxy must not be blocked by your firewall. Same for Internet Explorer, of course. If on MU web page other error codes appear, rename the windows folder "SoftwareDistribution" to "SoftwareDistribution.old" and let MU generate a fresh one. Maybe you have to disable a "HTTPS scanning" feature of your security software temporarily or make exclusions for MU related sites. 17. Do not use the same "DataStore.edb" in "SoftwareDistribution" for WSUS server/WUMT and MU web version. I have two DataStore.edb files, one for WSUS server and one for MU. One for all doesn't work in my system. 18. Use only http-links to open MU in IE. Direct link is http://fe2.update.microsoft.com/microsoftupdate/v6/default.aspx?ln=en or http://fe2.update.microsoft.com/microsoftupdate/v6/default.aspx?ln=en&g_sconsumersite=1 19. MU is only working if ProxHTTPSProxy is enabled. 20. For testing I add a link of my working ProxHTTPSProxy's config.ini: https://www.mediafire.com/file/vr1klatuzjh6v5c/ProxHTTPSProxy_-_config.ini/file 21. If completing all of these steps didn't help you at all, even after repeated execution, you may have a rather general problem relating to MU in your Windows XP installation. In this case you can try to manually reset Windows Update components. Here is my post how you can do that: After that kind of reset I recommend to perform all steps once again (from step 1 to 20 inclusive). Of course, some steps won't be necessary any more but checking which to perform or not will cost a lot of time, therefore senseless. Although I am not a friend of automatisms, I also offer a tool here to perform this reset of Microsoft or Windows Update automatically. Anyway, I recommend to backup your system partition completely at first. This tool called Reset Windows Update Tool (Script) is said to be working properly, but it has not been tested by me, so no guarantee of success and use at your own risk. The last XP compatible version is 10.5.3.7: https://www.mediafire.com/file/k48ll6e41eypogy/ResetWUEng10.5.3.7.zip/file and a less recent version 10.5.3.4 with a help file included: https://www.mediafire.com/file/wl0yrq98me8dfkj/ResetWUEng10.5.3.4.zip/file 22. If unfortunately none of all these 21 steps helped you, then you should presumably think about a complete reinstallation of Windows XP. I did all these steps (except steps 21 and 22) and for me MU is working flawlessly in my Windows XP Professional system. For further detailed instructions and missing files perform a search in this thread and enjoy the screenshots we all have uploaded! If you enjoyed this guide or maybe you found it interesting and helpful, I would be pleased about any reaction by liking or upvoting. Greetings from Germany, AstroSkipper PS: This guide will no longer be maintained. It will stay here just for historical purpose. The new, maintained and up-to-date version can be found here:9 points
-
New build of Serpent/UXP for XP! Test binary: Win32 https://o.rthost.win/basilisk/basilisk52-g4.8.win32-git-20211113-f94c0da-uxp-eedc02ee9-xpmod.7z Win64 https://o.rthost.win/basilisk/basilisk52-g4.8.win64-git-20211113-f94c0da-uxp-eedc02ee9-xpmod.7z source code that is comparable to my current working tree is available here: https://github.com/roytam1/UXP/commits/custom IA32 Win32 https://o.rthost.win/basilisk/basilisk52-g4.8.win32-git-20211113-f94c0da-uxp-eedc02ee9-xpmod-ia32.7z source code that is comparable to my current working tree is available here: https://github.com/roytam1/UXP/commits/ia32 NM28XP build: Win32 https://o.rthost.win/palemoon/palemoon-28.10.4a1.win32-git-20211113-ba47fad4d-uxp-eedc02ee9-xpmod.7z Win32 SSE https://o.rthost.win/palemoon/palemoon-28.10.4a1.win32-git-20211113-ba47fad4d-uxp-eedc02ee9-xpmod-sse.7z Win64 https://o.rthost.win/palemoon/palemoon-28.10.4a1.win64-git-20211113-ba47fad4d-uxp-eedc02ee9-xpmod.7z Official UXP changes picked since my last build: - remove OSX support (8fb608b22) - Bug 1730048, reorder the code in nsMenuFrame::PassMenuCommandEventToPopupManager a bit, r=mstange a=RyanVM (6bc10cbc9) - Bug 1735152 - Avoid using NS_ADDREF in nsSocketTransport. r=dragana, a=RyanVM (1920aae3d) - Bug 1606864 - Make mDoNotRetryToConnect atomic. r=decoder,dragana a=RyanVM Bug 1712671 - Make nsSocketTransport2::m{Input/Output}StreamClosed atomic. r=kershaw,decoder a=RyanVM (d025defb9) - backport Bug 1724233 - Make sure to run ConvertUTF8toACE before ConvertToDisplayIDN. r=dragana, a=RyanVM (0ffa8a018) - backport Bug 1729517 - Set up document correctly. r=freddyb,ckerschb a=RyanVM (537bcf5ea) - search: enlarge MAX_ICON_SIZE (fdb10cb2f) - Merge branch 'post-git-tracking' into tracking (2981ddf60) Official Basilisk changes picked since my last build: - [Basilisk] remove OSX related code (bd90dd917) Official Pale-Moon changes picked since my last build: - [Pale-Moon] remove OSX related code (e4da2ce4e) - [Pale-Moon] make sure anchor.top is not smaller than zero (7852cec48) - [Pale-Moon] remove Application prefix in enterTabbedMode method (16f07caa3) - [Pale-Moon] addons: replace Application.restart call with Services.startup.quit (7d223da9c) * Notice: From now on, UXP rev will point to `custom` branch of my UXP repo instead of now-dead MCP UXP repo, while "official UXP changes" shows only `tracking` branch changes. MCP Basilisk/Pale-Moon rev after datecode will be removed later.9 points
-
General and specific solutions for problems regarding AU/WU/MU in Windows XP List of used abbreviations: AU = Automatic Updates AV = Antivirus IE = Internet Explorer KB = Knowledge Base MDL = My Digital Life Forums. Link: https://forums.mydigitallife.net/ MKB = Microsoft Knowledge Base MU = Microsoft Update OS = operating system OSs = operating systems WU = Windows Update WUMT = Windows Update MiniTool We all are well informed about restoring WU/MU in Windows XP. A lot of threads and solutions to get access to WU/MU website. But we are here in a Windows XP forum. Therefore, this thread is targeted on Windows XP only and is meant to collect and provide solutions for general or specific problems which can occur after or while restoring update functionality. The main WU/MU related thread, which is targeted on Windows 2000, Windows XP and Windows Vista, is totally bloated and completely out of control, many post are definitely off-topic. To find general or specific solutions, you have to be a Sherlock Holmes or you'll need a lot of time to read tons of posts with no or low quality of information. And a lot of solutions are simply missing. I am no longer interested in posting new solutions or self-created fixes which can never be found again in such threads. From now on, I rather try to avoid posting in threads where people are talking permanently off-topic. Therefore, I decided to create my own one. Anyway, this main thread can be found here: https://msfn.org/board/topic/178377-on-decommissioning-of-update-servers-for-2000-xp-and-vista-as-of-july-2019/ The second post of this thread contains a numbered list of general solutions for problems regarding AU/WU/MU and methods of restoring WU/MU functionality in Windows XP. After performing these general solutions and methods, users are able to exclude errors or misconfiguration relating to AU/WU/MU in their Windows XP system. It is senseless to solve a specific problem if there is a general one. If WU/MU can't be restored generally and a user thinks about a reinstallation, the general solutions listed in second post can be tried first. There are different solutions to do this restoring successfully. General solutions: Link: https://msfn.org/board/topic/183498-general-and-specific-solutions-for-problems-regarding-auwumu-in-windows-xp/?do=findComment&comment=1216506 The third post of this thread contains a numbered list of specific solutions for problems regarding AU/WU/MU in Windows XP. These specific solutions will be provided with a meaningful title and a link to the creator's post in this thread. Specific solutions: Link: https://msfn.org/board/topic/183498-general-and-specific-solutions-for-problems-regarding-auwumu-in-windows-xp/?do=findComment&comment=1216507 The ninth post of this thread contains a numbered list of additional resources which can be helpful or informative to find an efficient solution for a specific problem. I'll only add resources relating to the topic of this thread. Additional resources: Link: https://msfn.org/board/topic/183498-general-and-specific-solutions-for-problems-regarding-auwumu-in-windows-xp/?do=findComment&comment=1216513 More solutions or resources can be added by posting in commenting zone. The idea is one solution, one post. The same applies to additional resources. Today I start to post some general solutions and methods, a brand-new specific solution and an additional resource. If you want to post an AU/WU/MU related solution or an additional resource in this thread, you can use the commenting zone to do this. Please post it by choosing a meaningful headline in bold and font size 18 for better visibility! If it seems to be a real solution (it's not my job to test them all) or an interesting resource, I will list it in second, third or ninth post with a link to the member's original comment for better overview. Due to the modular character of this thread each posted solution or resource can be upvoted or liked separately with credits to their poster. Any discussions or questions about these solutions or resources are explicitly welcome. But one thing must be totally clear, everything should relate to this topic. That means please stay on-topic! If you enjoyed this thread or maybe you found it interesting and helpful, we would be pleased about any reaction by liking or upvoting and of course commenting. Kind regards, AstroSkipper8 points
-
First of all, I think it's right and good that someone other than myself is also working on the great and very important extension uBlock Origin Legacy and developing it further. Since nothing has happened for years, I see my efforts here in relation to uBlock Origin Legacy as a kind of initial spark to maintain this extension again and bring it up to date. Based on the way a well-known American moron speaks I would say: "Make uBlock Origin Legacy great again!" @UCyborg has started a promising project on GitHub. I already had a look at it. An indirect collaboration has already taken place, as he has used my internal list of all standard filter lists, i.e. the assets.json file, as the basis for his one. But I cannot and will not comment on direct collaboration at this point. In any case, I will continue to maintain my version here for a while. The next version is coming up very soon. This means that the user now has the option of choosing their preferred version. As I have already said between the lines, a wider range of products generally stimulates "business". Cheers, AstroSkipper8 points
-
This is a continuation of my previous nVidia tutorial, but this time I decided to do it for folks with the extended kernel by @win32! As we know, the last officially supported driver was from the early May of 2016. This one is from 2017 ! Some may say it's a miracle , you betcha ! This driver was tested and confirmed fully working on 600, 700, 900 and 1000 series. Except the cheapest GT1030. You need the ex-kernel installed, I tested on a clean Vista with the updates up to 03.2019.+ the kernel. It's not allowed to share modded copyright protected material here, hence the new topic with the precise instructions follows. Tools you need :Driver Signature Enforcement Override, Universal Extractor and any HEX editor you like. Go and grab here: https://www.softpedia.com/get/Compression-tools/Universal-Extractor-Bioruebe.shtml Download here, here it is. NVIDIA - Display - 23-Feb-2017 12-00-00 AM - 21.21.13.7878 https://catalog.s.download.windowsupdate.com/d/msdownload/update/driver/drvs/2017/03/93376a87-7e31-472c-9236-b5f013236705_d5f668ad398d7409e8a2efa8c6d107ef7fbba1fe.cab and extract with Universal Extractor to an empty folder : In the nv_dispiwu.inf replace NTamd64.6.1 with NTamd64.6.0 and [NVIDIA_Devices.NTamd64.6.1] with [NVIDIA_Devices.NTamd64.6.0] Having difficulties to do so ? Then read how to Modify NVIDIA Driver .INF Files https://null-src.com/posts/nvidia-notebook-driver-inf-mod/post.php PATCHING : Extract nvlddmkm.sy_ file and patch the nvlddmkm.sys . 1 - search for and REPLACE 0000080000AAD5 with 00000800004B72 2 - search for and replace 84C0740AB8BB0000C0 with 84C0EB0AB8BB0000C0 and save. RENAME the patched file back to nvlddmkm.sy_ and place into the installer folder. Run CMD as ADMIN bcdedit.exe /set loadoptions DDISABLE_INTEGRITY_CHECKS bcdedit.exe /set TESTSIGNING ON bcdedit /set nointegritychecks on Reboot . Run SETUP.exe and install the driver. Do NOT restart . Run Driver Signature Enforcement Overrider and choose "sign a system driver" Sign this file ! C:\Windows\System32\Drivers\nvlddmkm.sys Reboot , go and play. DISCLAIMER Some might not like the use of additional software that may or may not be flagged by their KGB/FSB "antivirus". Per various sources inluding me , permanent disabling of drivers signature enforcement is just not possible since Vista , so you'd have to use Driver Signature Enforcement Overrider 1.3b and I'm not resposible in any way ! Optional : Run RemoveWatermarkX64 to remove the "test mode" watermark .REBOOT. If you share this topic , don't forget to tag me. @D.Draker Final thoughts : Vista lives. Supported Devices: NVIDIA_DEV.06C0 = "NVIDIA GeForce GTX 480" NVIDIA_DEV.06C4 = "NVIDIA GeForce GTX 465" NVIDIA_DEV.06CD = "NVIDIA GeForce GTX 470" NVIDIA_DEV.06D1 = "NVIDIA Tesla C2050 / C2070" NVIDIA_DEV.06D2 = "NVIDIA Tesla M2070" NVIDIA_DEV.06D8 = "NVIDIA Quadro 6000" NVIDIA_DEV.06D9 = "NVIDIA Quadro 5000" NVIDIA_DEV.06DD = "NVIDIA Quadro 4000" NVIDIA_DEV.06DE = "NVIDIA Tesla T20 Processor" NVIDIA_DEV.06DF = "NVIDIA Tesla M2070-Q" NVIDIA_DEV.0DC0 = "NVIDIA GeForce GT 440" NVIDIA_DEV.0DC4 = "NVIDIA GeForce GTS 450" NVIDIA_DEV.0DC5 = "NVIDIA GeForce GTS 450" NVIDIA_DEV.0DC6 = "NVIDIA GeForce GTS 450" NVIDIA_DEV.0DD8 = "NVIDIA Quadro 2000" NVIDIA_DEV.0DE0 = "NVIDIA GeForce GT 440" NVIDIA_DEV.0DE1 = "NVIDIA GeForce GT 430" NVIDIA_DEV.0DE2 = "NVIDIA GeForce GT 420" NVIDIA_DEV.0DE4 = "NVIDIA GeForce GT 520" NVIDIA_DEV.0DE5 = "NVIDIA GeForce GT 530" NVIDIA_DEV.0DE7 = "NVIDIA GeForce GT 610" NVIDIA_DEV.0DF8 = "NVIDIA Quadro 600" NVIDIA_DEV.0E22 = "NVIDIA GeForce GTX 460" NVIDIA_DEV.0E23 = "NVIDIA GeForce GTX 460 SE" NVIDIA_DEV.0E24 = "NVIDIA GeForce GTX 460" NVIDIA_DEV.0F00 = "NVIDIA GeForce GT 630" NVIDIA_DEV.0F01 = "NVIDIA GeForce GT 620" NVIDIA_DEV.0F02 = "NVIDIA GeForce GT 730" NVIDIA_DEV.0F03 = "NVIDIA GeForce GT 610" NVIDIA_DEV.0FC0 = "NVIDIA GeForce GT 640" NVIDIA_DEV.0FC1 = "NVIDIA GeForce GT 640" NVIDIA_DEV.0FC2 = "NVIDIA GeForce GT 630" NVIDIA_DEV.0FC6 = "NVIDIA GeForce GTX 650" NVIDIA_DEV.0FC8 = "NVIDIA GeForce GT 740" NVIDIA_DEV.0FC9 = "NVIDIA GeForce GT 730" NVIDIA_DEV.0FF3 = "NVIDIA Quadro K420" NVIDIA_DEV.0FF9 = "NVIDIA Quadro K2000D" NVIDIA_DEV.0FFA = "NVIDIA Quadro K600" NVIDIA_DEV.0FFD = "NVIDIA NVS 510" NVIDIA_DEV.0FFE = "NVIDIA Quadro K2000" NVIDIA_DEV.0FFF = "NVIDIA Quadro 410" NVIDIA_DEV.1001 = "NVIDIA GeForce GTX TITAN Z" NVIDIA_DEV.1004 = "NVIDIA GeForce GTX 780" NVIDIA_DEV.1005 = "NVIDIA GeForce GTX TITAN" NVIDIA_DEV.1007 = "NVIDIA GeForce GTX 780" NVIDIA_DEV.1008 = "NVIDIA GeForce GTX 780 Ti" NVIDIA_DEV.100A = "NVIDIA GeForce GTX 780 Ti" NVIDIA_DEV.100C = "NVIDIA GeForce GTX TITAN Black" NVIDIA_DEV.1021 = "NVIDIA Tesla K20Xm" NVIDIA_DEV.1022 = "NVIDIA Tesla K20c" NVIDIA_DEV.1023 = "NVIDIA Tesla K40m" NVIDIA_DEV.1024 = "NVIDIA Tesla K40c" NVIDIA_DEV.1026 = "NVIDIA Tesla K20s" NVIDIA_DEV.1027 = "NVIDIA Tesla K40st" NVIDIA_DEV.1028 = "NVIDIA Tesla K20m" NVIDIA_DEV.1029 = "NVIDIA Tesla K40s" NVIDIA_DEV.102A = "NVIDIA Tesla K40t" NVIDIA_DEV.102D = "NVIDIA Tesla K80" NVIDIA_DEV.103A = "NVIDIA Quadro K6000" NVIDIA_DEV.103C = "NVIDIA Quadro K5200" NVIDIA_DEV.1040 = "NVIDIA GeForce GT 520" NVIDIA_DEV.1042 = "NVIDIA GeForce 510" NVIDIA_DEV.1048 = "NVIDIA GeForce 605" NVIDIA_DEV.1049 = "NVIDIA GeForce GT 620" NVIDIA_DEV.104A = "NVIDIA GeForce GT 610" NVIDIA_DEV.104B = "NVIDIA GeForce GT 625 (OEM)" NVIDIA_DEV.104C = "NVIDIA GeForce GT 705" NVIDIA_DEV.107C = "NVIDIA NVS 315" NVIDIA_DEV.107D = "NVIDIA NVS 310" NVIDIA_DEV.1080 = "NVIDIA GeForce GTX 580" NVIDIA_DEV.1081 = "NVIDIA GeForce GTX 570" NVIDIA_DEV.1082 = "NVIDIA GeForce GTX 560 Ti" NVIDIA_DEV.1084 = "NVIDIA GeForce GTX 560" NVIDIA_DEV.1086 = "NVIDIA GeForce GTX 570" NVIDIA_DEV.1087 = "NVIDIA GeForce GTX 560 Ti" NVIDIA_DEV.1088 = "NVIDIA GeForce GTX 590" NVIDIA_DEV.1089 = "NVIDIA GeForce GTX 580" NVIDIA_DEV.108B = "NVIDIA GeForce GTX 580" NVIDIA_DEV.1091 = "NVIDIA Tesla M2090" NVIDIA_DEV.1094 = "NVIDIA Tesla M2075" NVIDIA_DEV.1096 = "NVIDIA Tesla C2075" NVIDIA_DEV.109B = "NVIDIA Quadro 7000" NVIDIA_DEV.1180 = "NVIDIA GeForce GTX 680" NVIDIA_DEV.1183 = "NVIDIA GeForce GTX 660 Ti" NVIDIA_DEV.1184 = "NVIDIA GeForce GTX 770" NVIDIA_DEV.1185 = "NVIDIA GeForce GTX 660" NVIDIA_DEV.1187 = "NVIDIA GeForce GTX 760" NVIDIA_DEV.1188 = "NVIDIA GeForce GTX 690" NVIDIA_DEV.1189 = "NVIDIA GeForce GTX 670" NVIDIA_DEV.118E = "NVIDIA GeForce GTX 760 (192-bit)" NVIDIA_DEV.118F = "NVIDIA Tesla K10" NVIDIA_DEV.1193 = "NVIDIA GeForce GTX 760 Ti OEM" NVIDIA_DEV.1194 = "NVIDIA Tesla K8" NVIDIA_DEV.1195 = "NVIDIA GeForce GTX 660" NVIDIA_DEV.11B4 = "NVIDIA Quadro K4200" NVIDIA_DEV.11BA = "NVIDIA Quadro K5000" NVIDIA_DEV.11C0 = "NVIDIA GeForce GTX 660" NVIDIA_DEV.11C2 = "NVIDIA GeForce GTX 650 Ti BOOST" NVIDIA_DEV.11C3 = "NVIDIA GeForce GTX 650 Ti" NVIDIA_DEV.11C4 = "NVIDIA GeForce GTX 645" NVIDIA_DEV.11C5 = "NVIDIA GeForce GT 740" NVIDIA_DEV.11C6 = "NVIDIA GeForce GTX 650 Ti" NVIDIA_DEV.11C8 = "NVIDIA GeForce GTX 650" NVIDIA_DEV.11CB = "NVIDIA GeForce GT 740" NVIDIA_DEV.11FA = "NVIDIA Quadro K4000" NVIDIA_DEV.1200 = "NVIDIA GeForce GTX 560 Ti" NVIDIA_DEV.1201 = "NVIDIA GeForce GTX 560" NVIDIA_DEV.1205 = "NVIDIA GeForce GTX 460 v2" NVIDIA_DEV.1206 = "NVIDIA GeForce GTX 555" NVIDIA_DEV.1207 = "NVIDIA GeForce GT 645" NVIDIA_DEV.1208 = "NVIDIA GeForce GTX 560 SE" NVIDIA_DEV.1241 = "NVIDIA GeForce GT 545" NVIDIA_DEV.1243 = "NVIDIA GeForce GT 545" NVIDIA_DEV.1244 = "NVIDIA GeForce GTX 550 Ti" NVIDIA_DEV.1245 = "NVIDIA GeForce GTS 450" NVIDIA_DEV.1249 = "NVIDIA GeForce GTS 450" NVIDIA_DEV.124B = "NVIDIA GeForce GT 640" NVIDIA_DEV.1280 = "NVIDIA GeForce GT 635" NVIDIA_DEV.1281 = "NVIDIA GeForce GT 710" NVIDIA_DEV.1282 = "NVIDIA GeForce GT 640" NVIDIA_DEV.1284 = "NVIDIA GeForce GT 630" NVIDIA_DEV.1286 = "NVIDIA GeForce GT 720" NVIDIA_DEV.1287 = "NVIDIA GeForce GT 730" NVIDIA_DEV.1288 = "NVIDIA GeForce GT 720" NVIDIA_DEV.1289 = "NVIDIA GeForce GT 710" NVIDIA_DEV.128B = "NVIDIA GeForce GT 710" NVIDIA_DEV.1380 = "NVIDIA GeForce GTX 750 Ti" NVIDIA_DEV.1381 = "NVIDIA GeForce GTX 750" NVIDIA_DEV.1382 = "NVIDIA GeForce GTX 745" NVIDIA_DEV.139D = "NVIDIA GeForce GTX 750 Ti" NVIDIA_DEV.13B9 = "NVIDIA NVS 810" NVIDIA_DEV.13BA = "NVIDIA Quadro K2200" NVIDIA_DEV.13BB = "NVIDIA Quadro K620" NVIDIA_DEV.13BC = "NVIDIA Quadro K1200" NVIDIA_DEV.13C0 = "NVIDIA GeForce GTX 980" NVIDIA_DEV.13C2 = "NVIDIA GeForce GTX 970" NVIDIA_DEV.13F0 = "NVIDIA Quadro M5000" NVIDIA_DEV.13F1 = "NVIDIA Quadro M4000" NVIDIA_DEV.1401 = "NVIDIA GeForce GTX 960" NVIDIA_DEV.1402 = "NVIDIA GeForce GTX 950" NVIDIA_DEV.1406 = "NVIDIA GeForce GTX 960" NVIDIA_DEV.1407 = "NVIDIA GeForce GTX 750" NVIDIA_DEV.1430 = "NVIDIA Quadro M2000" NVIDIA_DEV.17C2 = "NVIDIA GeForce GTX TITAN X" NVIDIA_DEV.17C8 = "NVIDIA GeForce GTX 980 Ti" NVIDIA_DEV.17F0 = "NVIDIA Quadro M6000" NVIDIA_DEV.17F1 = "NVIDIA Quadro M6000 24GB" NVIDIA_DEV.1B00 = "NVIDIA TITAN X (Pascal)" NVIDIA_DEV.1B06 = "NVIDIA GeForce GTX 1080 Ti" NVIDIA_DEV.1B30 = "NVIDIA Quadro P6000" NVIDIA_DEV.1B80 = "NVIDIA GeForce GTX 1080" NVIDIA_DEV.1B81 = "NVIDIA GeForce GTX 1070" NVIDIA_DEV.1B84 = "NVIDIA GeForce GTX 1060 3GB" NVIDIA_DEV.1BB0 = "NVIDIA Quadro P5000" NVIDIA_DEV.1BB1 = "NVIDIA Quadro P4000" NVIDIA_DEV.1C02 = "NVIDIA GeForce GTX 1060 3GB" NVIDIA_DEV.1C03 = "NVIDIA GeForce GTX 1060 6GB" NVIDIA_DEV.1C30 = "NVIDIA Quadro P2000" NVIDIA_DEV.1C81 = "NVIDIA GeForce GTX 1050" NVIDIA_DEV.1C82 = "NVIDIA GeForce GTX 1050 Ti"8 points
-
New build of Serpent/UXP for XP! Test binary: Win32 https://o.rthost.win/basilisk/basilisk52-g4.8.win32-git-20231007-3219d2d-uxp-e90473bdda-xpmod.7z Win64 https://o.rthost.win/basilisk/basilisk52-g4.8.win64-git-20231007-3219d2d-uxp-e90473bdda-xpmod.7z source code that is comparable to my current working tree is available here: https://github.com/roytam1/UXP/commits/custom IA32 Win32 https://o.rthost.win/basilisk/basilisk52-g4.8.win32-git-20231007-3219d2d-uxp-e90473bdda-xpmod-ia32.7z source code that is comparable to my current working tree is available here: https://github.com/roytam1/UXP/commits/ia32 NM28XP build: Win32 https://o.rthost.win/palemoon/palemoon-28.10.7a1.win32-git-20231007-d849524bd-uxp-e90473bdda-xpmod.7z Win32 IA32 https://o.rthost.win/palemoon/palemoon-28.10.7a1.win32-git-20231007-d849524bd-uxp-e90473bdda-xpmod-ia32.7z Win32 SSE https://o.rthost.win/palemoon/palemoon-28.10.7a1.win32-git-20231007-d849524bd-uxp-e90473bdda-xpmod-sse.7z Win64 https://o.rthost.win/palemoon/palemoon-28.10.7a1.win64-git-20231007-d849524bd-uxp-e90473bdda-xpmod.7z Official UXP changes picked since my last build: - Issue #2321 - Fall back to 0 if setInterval interval not supplied (e0e1542913) - Issue #2323 - Part 1: Add Min()/Max() methods to TimeDuration. (c78ecee3f2) - Issue #2323 - Part 2: Implement timer nesting and clamping for workers. (1b7df316c4) - Issue #2323 - Part 3: Exclude chrome workers from worker timer clamping. (2ca5715149) - Issue #1442 - Part 1: Change ArrayBufferCopyData self-hosting intrinsic to take a start offset for the destination. This will be needed to manage stream chunks. https://bugzilla.mozilla.org/show_bug.cgi?id=1272697 (90ca1f569a) - Issue #1442 - Part 2: Add a run-time preference for toggling the streams API. https://bugzilla.mozilla.org/show_bug.cgi?id=1272697 (62467428a3) - Issue #1442 - Part 3: Implement ReadableStream and associated classes in the JS engine. https://bugzilla.mozilla.org/show_bug.cgi?id=1272697 (54e84f0f1d) - Issue #1442 - Part 4: Add JSAPI functions for working with ReadableStream. https://bugzilla.mozilla.org/show_bug.cgi?id=1272697 (9b9075eef6) - Issue #1442 - Part 5: Implement WebIDL bindings for Streams. https://bugzilla.mozilla.org/show_bug.cgi?id=1128959 (0701dccaca) - Issue #1442 - Part 6: binding codegen naming alignment for Streams. https://bugzilla.mozilla.org/show_bug.cgi?id=1128959 (4c5775b621) - Issue #1442 - Part 7: Use of ReadableStream in WebIDL files. https://bugzilla.mozilla.org/show_bug.cgi?id=1128959 (dd2c9eb418) - Issue #1442 - Part 8: Fetch implementation of streams. https://bugzilla.mozilla.org/show_bug.cgi?id=1128959 +worker-friendly pref checking for the DOM API. (bff1f3bc60) - Issue #1442 - Part 9: Stream shutdown handling. https://bugzilla.mozilla.org/show_bug.cgi?id=1128959 (3979e4847c) - Issue #1442 - Part 10a - Unify body extraction in Fetch/Beacon/XHR. https://bugzilla.mozilla.org/show_bug.cgi?id=1329298 Pre-requisite for Part 11. (a4146b60a4) - Issue #1442 - Part 10b - Use nsIXHRSendable instead Blob/FormData/URLSearchParams. https://bugzilla.mozilla.org/show_bug.cgi?id=1329298 Pre-requisite for Part 11. (a9520b2a7a) - Issue #1442 - Part 10c - Use application/octet-stream for arrayBuffer in sendBeacon. https://bugzilla.mozilla.org/show_bug.cgi?id=1329298 Pre-requisite for Part 11. (772ab8ac41) - Issue #1442 - Part 11 - Response.body handling. https://bugzilla.mozilla.org/show_bug.cgi?id=1329298 Use BufferSource in webIDL. https://bugzilla.mozilla.org/show_bug.cgi?id=1337722 (a8a75090c0) - Issue #1442 - Part 12 - Label FetchBody. https://bugzilla.mozilla.org/show_bug.cgi?id=1363318 FetchSignal is not in our tree so this is a partial patch to get mOwner changes. Pre-requisite for Part 13. (346e8a87d7) - Issue #1442 - Part 12a - Allow idle worker shutdown to begin for an opt-in WorkerHolder mode. https://bugzilla.mozilla.org/show_bug.cgi?id=1362444 Pre-requisite for Part 13. (41216b88f6) - Issue #1442 - Part 12b - Allow idle worker shutdown while Cache/CacheStorage DOM objects exist, but block it during Cache operation. https://bugzilla.mozilla.org/show_bug.cgi?id=1362444 Pre-requisite for Part 13. (0b450a3def) - Issue #1442 - Part 13 - Implement FetchStreamReader. https://bugzilla.mozilla.org/show_bug.cgi?id=1329298 (ef550b2579) - Issue #1442 - Part 14 - Starting body consuming and passing the JSContext down from the binding entrypoints to where the ReadableStream could be read. https://bugzilla.mozilla.org/show_bug.cgi?id=1128959 (842b9d47b3) - Issue #1442 - Part 15 - Setting the correct global when ReadableStream.getReader() is called. https://bugzilla.mozilla.org/show_bug.cgi?id=1128959 (b124e54fc7) - Issue #1442 - Part 16 - Report stream errors during consumption. https://bugzilla.mozilla.org/show_bug.cgi?id=1128959 (529bc13f05) - Issue #1442 - Part 17 - Creating FetchStream as a out param in order to avoid JS hazards https://bugzilla.mozilla.org/show_bug.cgi?id=1128959 (e22845913d) - Issue #1442 - Part 18 - Cycle collect FetchStreamReader. https://bugzilla.mozilla.org/show_bug.cgi?id=1128959 (b898780bb1) - Issue #1442 - Part 19 - FetchStream must support multiple read requests. https://bugzilla.mozilla.org/show_bug.cgi?id=1395220 (0e1efcb273) - Issue #1442 - Part 20 - FetchStream should not have an extra JS::Heap<ReadableStream>. https://bugzilla.mozilla.org/show_bug.cgi?id=1390717 (b1a12de924) - Issue #1442 - Part 21 - Fix debug builds by removing an invalid assert. (375d7cf3b2) - Issue #1442 & #1691 Follow-up - Part 22 - Changes that came with Dynamic Module Import. At the time we did not have ReadableStreams in our tree so these changes were left out. https://bugzilla.mozilla.org/show_bug.cgi?id=1499140 Implement support for dynamic module import in the interpreter. (41409ab613) - Issue #1442 - Part 23 - Align FetchStream with Firefox 68ESR. https://bugzilla.mozilla.org/show_bug.cgi?id=1612308 https://bugzilla.mozilla.org/show_bug.cgi?id=1445587 Partial part 2 implementing synchronization changes. (836d36dc6d) - Issue #1442 - Part 24 - Prevent FetchStream from incorrectly running on the main thread. This prevents a deadlock and JSContext related crashes, however this should eventually be replaced by an EventTargetFor() call when the Dispatcher API is implemented. Also now that ReadableStream appears stable, toggle the preferences true by default. (f3991f9821) - Issue #1442 - Part 25 - Fix bustage on X11 platforms. (52572d5755) - Issue #1442 - Part 25b - Second try that hopefully doesn't break Windows. (04c9d661fa) - Issue #1442 - Part 26 - FetchStreamReader needs to cancel its reader when it encounters write errors. https://bugzilla.mozilla.org/show_bug.cgi?id=1416879 Part 5 Also same fix as in Part 24 for FetchStream but in FetchStreamReader. (f21cc50c03) - No Issue - Remove deprecation errors for obsolete RTCOfferOptions (6fdb3ac961) - Issue #2332 - Update to libvpx 1.6.1 (b860c5fe95) - Issue #2332 - libvpx upgrade followup part 1 (ed581885f8) - Issue #2332 - libvpx upgrade followup part 2 (cdc8770f5a) - Issue #2332 - libvpx upgrade followup part 3 (fcb078d794) - Issue #2332 - libvpx upgrade followup part 4 (ee5b062139) - Issue #2332 - libvpx upgrade followup part 5 (465ce802d1) - Issue #2332 - Remove unimplemented and non-spec getStreamById from RTCPeerConnection (7528b07555) - [DOM] Fix deprot in PerformanceMark.cpp (cdb890bdc3) Official Pale-Moon changes picked since my last build: - [Pale-Moon] No Issue - Don't build hunspell shared on SunOS. (28958637f9) - [Pale-Moon] Issue #1936 - Optionally leave Bookmarks menu open when spawning new tab. (56f5e8f283) Official Basilisk changes picked since my last build: - [Basilisk] Don't build hunspell shared on SunOS (ebf28e418f) - [Basilisk] Delete Firefox Dev Edition leftovers (1eca5a03c2) - [Basilisk] Update pdf.js to version 1.6.467 from Firefox 53.0.2 (328408759a) - [Basilisk] Update pdf.js to 1.7.348 from Firefox 54.0.1 (c5d109556c) - [Basilisk] Update PDF.js to 2.3.235 (21121b141b) - [Basilisk] Remove stubs and references. Remove some telemetry leftovers (32e4115055) - [Basilisk] Pref changes for old reports that no longer exist (6b8a4e9b72) - [Basilisk] Remove some mobile leftovers (77bc3513fd) - [Basilisk] Remove some android leftovers (c4f84bd3d5) - [Basilisk] Remove ios leftovers (3d339baec2) - [Basilisk] remove more mozilla spy garbage (6c88624503) - [Basilisk] Clean up an unused pref. Remove link to mozilla site from crash reporter (23ef0c81f7) - [Basilisk] Remove last bits of telemetry (b5a13a2a38) - [Basilisk] Remove obsolete documentation (a11b107f18) - [Basilisk] Remove unused functionality for reporting crashes to an external server (e73c73a426) - [Basilisk] Remove unused prefs for download of tiles on new tab page (3fa770bcba) - [Basilisk] Remove some leftover crashreporter stuff (264cd17e94) - [Basilisk] Remove browser.tabs.crashReporting.sendReport prefs (36ca1ce479) - [Basilisk] restore erroneously removed dom.ipc.reportProcessHangs pref ifdef (0be9ef65f6) - [Basilisk] Remove unsubmitted crash reporter from crash handlers (0ae5036656) - [Basilisk] Remove some unused crash report strings from localization data (04e9b40d4b) - [Basilisk] Report GTK version in about dialog for Linux builds (a03283044e) - [Basilisk] Issue #67 - begin porting over changes to stop using appconstants (e1e2d7e832) - [Basilisk] Fix issue with updater (2169356c67) - [Basilisk] Issue #67 - stop using appconst in aboutSessionRestore.js (fa1cbb6658) - [Basilisk] Dont preprocess files that dont need preprocessing (4c819bd3d5) My changes picked since my last build: - [Basilisk] some files in my tree still need preprocessing (4f9068fe23) - [Basilisk] pdfjs: Services.policies is not available in UXP, comment it out (d946fc6195) - [Basilisk] Revert "Update PDF.js to 2.3.235" as it breaks in e10s (e90473bdda) Update Notice: - You may delete file named icudt*.dat inside program folder when updating from old releases. * Notice: From now on, UXP rev will point to `custom` branch of my UXP repo instead of MCP UXP repo, while "official UXP changes" shows only `tracking` branch changes.8 points
-
For installing unsigned web extensions in Serpent 52 and 55 (moebius! ) they have first to be compatible with these browsers. Deleting any files from the folder META-INF of a xpi file does not do anything, and is therefore no solution. Furthermore, only setting the preference xpinstall.signatures.required to false, which is already the default setting in Serpent, is no solution, either. To install such an unsigned web extension permanently (there is no META-INF folder in its archive, or it has been removed) in Serpent, the file manifest.json has to be modified to assign a unique ID to this extension. For testing purpose, I did that in the case of the web extension save-as-ebook 1.4.2 loaded from https://github.com/alexadam/save-as-ebook/tree/master/web-extension which lacks of such an ID in its file manifest.json. After assigning a unique ID to it, I packed the complete extension into a zip file and renamed it to save-as-ebook-1.4.2.xpi. If done, it can be installed then as usual, works as it should and also survives the next browser restart. Without enabling add-on debugging which would only result in a temporary loading of the web extension anyway! As a unique ID, I chose user-save-as-ebook@email.com. Here is a screenshot as a proof: Cheers, AstroSkipper8 points
-
Agreed. The behavior in that thread was unacceptable. I locked the topic and made it clear that I won't allow that behavior in the forum section for my project. If you see something like this in the Basilisk section of the Pale Moon Forum again feel free to let me know directly.8 points
-
New build of Serpent/UXP for XP! Test binary: Win32 https://o.rthost.win/basilisk/basilisk52-g4.8.win32-git-20221126-3219d2d-uxp-de0b4ac20-xpmod.7z Win64 https://o.rthost.win/basilisk/basilisk52-g4.8.win64-git-20221126-3219d2d-uxp-de0b4ac20-xpmod.7z source code that is comparable to my current working tree is available here: https://github.com/roytam1/UXP/commits/custom IA32 Win32 https://o.rthost.win/basilisk/basilisk52-g4.8.win32-git-20221126-3219d2d-uxp-de0b4ac20-xpmod-ia32.7z source code that is comparable to my current working tree is available here: https://github.com/roytam1/UXP/commits/ia32 NM28XP build: Win32 https://o.rthost.win/palemoon/palemoon-28.10.6a1.win32-git-20221126-d849524bd-uxp-de0b4ac20-xpmod.7z Win32 SSE https://o.rthost.win/palemoon/palemoon-28.10.6a1.win32-git-20221126-d849524bd-uxp-de0b4ac20-xpmod-sse.7z Win64 https://o.rthost.win/palemoon/palemoon-28.10.6a1.win64-git-20221126-d849524bd-uxp-de0b4ac20-xpmod.7z Official UXP changes picked since my last build: - [Network, DOM] Align our implementation with the current CORS/Fetch spec. (37f0199c7) - WebSocketChannel::CleanupConnection should run on the socket thread (7fab5ebd1) - [network] Fix Mac buffer overflow. (6408291d7) - [XPCOM] Deal with lstat potentially lying in nsLocalFileUnix. (dc04d9f79) - Issue #2027 - Use reserved stack space instead of heap allocation in nsLocalFile (eb0c06101) - Issue #2029 - Part 1: Add preference for opening the protocol handling dialog as window modal (36ddeff63) - Issue #2029 - Part 2: Protocol handling dialog should be `dependent` if not `modal` (bbd05cb4c) - Issue #2019 - Follow-up: Make nsPluginInstanceOwner also listen to keypress events in the system event group. (f35ae1ce7) No official Pale-Moon changes picked since my last build. No official Basilisk changes picked since my last build. Update Notice: - You may delete file named icudt58l.dat inside program folder when updating from old releases. * Notice: From now on, UXP rev will point to `custom` branch of my UXP repo instead of MCP UXP repo, while "official UXP changes" shows only `tracking` branch changes.8 points
-
New build of Serpent/UXP for XP! Test binary: Win32 https://o.rthost.win/basilisk/basilisk52-g4.8.win32-git-20220528-3219d2d-uxp-0855ba43d-xpmod.7z Win64 https://o.rthost.win/basilisk/basilisk52-g4.8.win64-git-20220528-3219d2d-uxp-0855ba43d-xpmod.7z source code that is comparable to my current working tree is available here: https://github.com/roytam1/UXP/commits/custom IA32 Win32 https://o.rthost.win/basilisk/basilisk52-g4.8.win32-git-20220528-3219d2d-uxp-0855ba43d-xpmod-ia32.7z source code that is comparable to my current working tree is available here: https://github.com/roytam1/UXP/commits/ia32 NM28XP build: Win32 https://o.rthost.win/palemoon/palemoon-28.10.6a1.win32-git-20220528-d849524bd-uxp-0855ba43d-xpmod.7z Win32 SSE https://o.rthost.win/palemoon/palemoon-28.10.6a1.win32-git-20220528-d849524bd-uxp-0855ba43d-xpmod-sse.7z Win64 https://o.rthost.win/palemoon/palemoon-28.10.6a1.win64-git-20220528-d849524bd-uxp-0855ba43d-xpmod.7z Official UXP changes picked since my last build: - Bug 1679987 - Remove unused includes of nsCharSeparatedTokenizer.h. (62a140ab8) - Issue #1894 - Part 1: Implement coalesce JS opcode (3efa23472) - Issue #1894 - Part 2: Implement support for nullish coalescing in the JS parser (d7cdeaf31) - Issue #1894 - Part 3: Implement support for nullish coalescing in JS reflection (f282a4c05) - Issue #1894 - Part 4: Implement IonMonkey support for nullish coalescing (581272180) - Issue #1894 - Part 5: Implement bytecode for nullish coalescing (707867d16) - Issue #1894 - Part 6: Check for nullish values when folding coalesce nodes (9dde32ee9) - Issue #1894 - Part 7: Update tests (f0e208a86) - No issue - Add null check to send packet function in the developer tools server (2e975416b) - Issue #457 - Silence some GCC compiler warnings in FFmpeg code (5c61382da) - No issue - relax ctts flag checking in media/libstagefright (2f8131275) No official Pale-Moon changes picked since my last build. No official Basilisk changes picked since my last build. My changes picked since my last build: - libstagefright: relax ctts flags checking. (d9f111872) - [Basilisk] pdfjs: remove telemetry (0855ba43d) * Notice: From now on, UXP rev will point to `custom` branch of my UXP repo instead of MCP UXP repo, while "official UXP changes" shows only `tracking` branch changes.8 points