Dave-H last won the day on January 13
Dave-H had the most liked content!
About Dave-H

- Currently Viewing Forums Index
- Birthday 03/31/1953
Profile Information
-
OS
XP Pro x86
Recent Profile Visitors
Dave-H's Achievements
2k
Reputation
-
Edge appears to be the same, so I guess it's a Chromium thing?
-

Firefox 52 no longer working on XP
Dave-H replied to Dave-H's topic in Browsers working on Older NT-Family OSes
Thanks very much for the explanation! -

Firefox 52 no longer working on XP
Dave-H replied to Dave-H's topic in Browsers working on Older NT-Family OSes
Thanks @roytam1. Yes, I'm aware that the runtime version I'm using isn't an official XP-compatible version. It was brought to my attention by @Monroe in another thread here. I think it was developed unofficially to help with some games which would not otherwise work on XP. Presumably, as I've now found, it can also cause compatibility problems with some other programs! I will probably keep it installed as a system runtime, but be aware that if any other program now fails to run, that might be the cause. Hopefully all I will need to do then, as with Firefox, is put compatible versions of the necessary runtime DLLs in the program's folder. -

Firefox 52 no longer working on XP
Dave-H replied to Dave-H's topic in Browsers working on Older NT-Family OSes
OK, it's fixed! The portable version worked fine, and in fact if I ran the firefox.exe in the portable version's program folder, rather than firefoxportable.exe, it opened fine using my normal Firefox profile! So, I started comparing the two installations, and found that some DLLs in my Firefox program folder appeared to have been disabled by renaming 'DLL' to 'D~L'. That's my normal way of disabling a file, changing the middle character of the extension to '~'. Why I had done that is lost in the mists of time in this case, but one disabled DLL file stood out, and that was msvcp140.dll, which is a C++ Runtime file of course. That reminded me that I had recently updated my C++ 2015-2019 Runtime to 14.29.30139, following a recommendation elsewhere on MSFN. Thinking perhaps this could be the issue, I simply renamed the msvcp140.dll file in the Firefox folder back to normal, and everything came good! So, I guess the new system runtime file versions may not actually be compatible with all programs, so I will now be on the lookout for any other seldom-used programs which no longer work. Thanks everyone for the help as always! Cheers, Dave. -

Firefox 52 no longer working on XP
Dave-H replied to Dave-H's topic in Browsers working on Older NT-Family OSes
No, Firefox was not open when I uninstalled Malwarebytes. I hardly ever use it now. Thanks for the link to the portable version, I will give it a try and report back. -

Firefox 52 no longer working on XP
Dave-H replied to Dave-H's topic in Browsers working on Older NT-Family OSes
OK, I tried disabling the current Firefox profile (by renaming its folder and making a new empty folder with the same name). Firefox still didn't start, with the same immediate error. I think that means the issue is nothing to do with anything in the profile. -
There is no noticeable increase in startup time with 22.03.05 on my machine, it seems perfectly normal as it was before Panda was installed, so I can only assume that it just doesn't run well on your particular hardware.
- 1,440 replies
-
2
-
- Security
- Antimalware
-
(and 3 more)
Tagged with:
-

Firefox 52 no longer working on XP
Dave-H replied to Dave-H's topic in Browsers working on Older NT-Family OSes
I did wonder about extensions, I haven't changed those on FF 52 for years, but they do update themselves so it's possible that an incompatibility has crept in. It won't run in Firefox 'safe mode' either though, which I thought was supposed to not load any extensions or plugins. I'll try with a new clean profile which should eliminate this possibility. -

Firefox 52 no longer working on XP
Dave-H replied to Dave-H's topic in Browsers working on Older NT-Family OSes
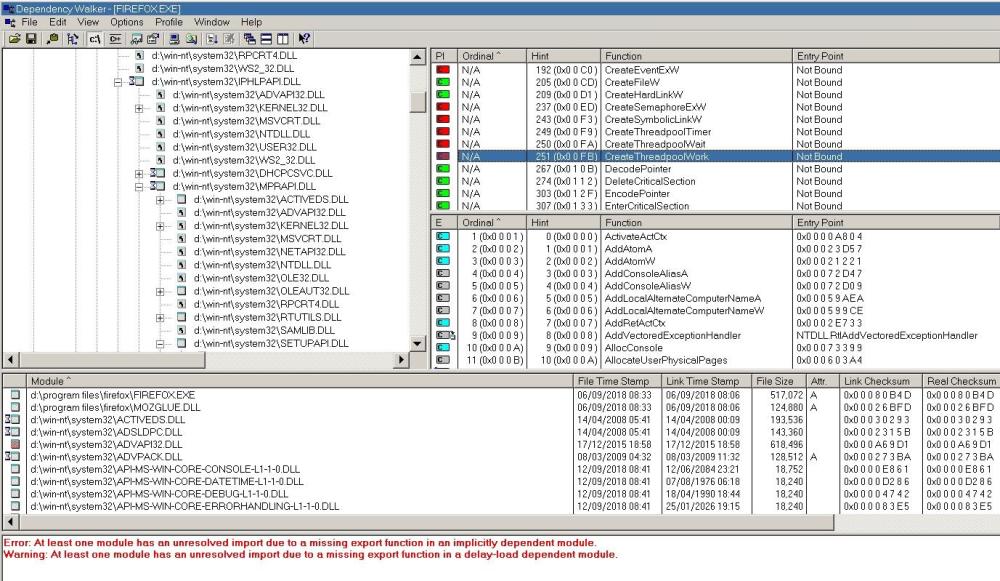
Here's what Dependency Walker says. CreateThreadpoolWork is indeed showing an error, but so are several other functions, and they're not stopping it from running! Incidentally, why does it say 'Not Bound'? Should that actually be 'Not Found' or is that terminology correct? Sorry, I'm no expert on this sort of thing! -

Firefox 52 no longer working on XP
Dave-H replied to Dave-H's topic in Browsers working on Older NT-Family OSes
Thanks everyone, and sorry for the delay in replying. I was having terrible problems accessing the site yesterday, which i hope is now fixed. @NotHereToPlayGames I ended up uninstalling Malwarebytes in Safe Mode because when I tried in normal mode, when I said yes to 'do you want to uninstall' the machine immediately rebooted! Rather than try again and probably have the same thing happen, I then tried in Safe Mode, and it immediately uninstalled, very quickly indeed. Why the machine rebooted, I have no idea. I doubt this has anything to do with Firefox now failing to run, but you never know! @schwups @NotHereToPlayGames I'm not running any form of extended kernel. @ED_Sln Firefox.exe looks to be OK. Very strange. Just to add that Firefox won't run in its own 'safe mode' either. -

Firefox 52 no longer working on XP
Dave-H replied to Dave-H's topic in Browsers working on Older NT-Family OSes
I do have Revo installer, if you remember I used it to give AstroSkipper a list of .NET updates in another thread. I don't think I've ever actually used it to uninstall anything though! If I did, it would have been a very long time ago, so not related to this issue I'm sure. I have recently uninstalled Malwarebytes 3.5.1 though, using the normal uninstallation routine in Safe Mode. I wonder if there's any connection there? -
PortableRegistrator 1.5 certainly works with XP, I don't know about any later versions. I can upload it for you if you can't get a version which works. FWIW I use the Classic Blue theme, which always looks very pleasing to me, but it may not help with your issue of course.
-
Dave-H started following Firefox 52 no longer working on XP
-

Firefox 52 no longer working on XP
Dave-H posted a topic in Browsers working on Older NT-Family OSes
I've had Firefox 52.9.1.6822 installed on the XP side of my machine for many years, as the last Firefox version which will run on XP. I don't use it often now as I use a much more up-to-date version of Supermium. However, I tried to run it today, and it won't run any more. I just get a popup saying - "The procedure entry point CreateThreadpoolWork could not be located in the dynamic link library KERNEL32.dll." Anyone any idea why it would have stopped working? I've not knowingly changed anything relevant since I last used it. The Firefox files seem to be as they have always been, and no system files have been knowingly changed either. -
That would certainly make sense and explain things. Version 21 presumably uses IE's proxy settings, and version 22 (and presumably 23) do not, which is why I had to manually set version 22 to use the proxy to get access to my account in its interface.
- 1,440 replies
-
- Security
- Antimalware
-
(and 3 more)
Tagged with: