Leaderboard
Popular Content
Showing content with the highest reputation on 05/12/2023 in all areas
-
The issue have been fixed in v113.0.12 points
-
1 point
-
New build of post-deprecated Serpent/moebius for XP! * Notice: This repo will not be built on regular schedule, and changes are experimental as usual. ** Current moebius patch level should be on par with 52.9, but some security patches can not be applied/ported due to source milestone differences between versions. Test binary: Win32 http://o.rthost.win/basilisk/basilisk55-win32-git-20230513-557bd3b25-xpmod.7z Win64 http://o.rthost.win/basilisk/basilisk55-win64-git-20230513-557bd3b25-xpmod.7z repo: https://github.com/roytam1/basilisk55 Repo changes: - import from UXP: Issue #2232 - Parse exported async functions. (9693552c) (023d1d00c) - import from UXP: Issue #2234 - Part 1: Create async function wrapper when instantiating module functions (ab1c0a38) (8cc249be3) - import from UXP: Issue #2234 - Part 2: Ensure that the created async function wrapper is valid (e52da470) (7e609ff07) - import from UXP: Issue #2234 - Part 3: Update tests (2d6c4196) (e4c048b85) - js/jit: IonControlFlow: have to follow WaterfoxClassic rev 6d15d320 to abort Ion when hitting SRC_LOGICASSIGN to prevent JSOP_GOTO runs inside IonBuilder and crash. (ef905bcee) - import from UXP: Issue #2236 - Fix import.meta module error in lambdas by moving parseGoal() into SharedContext. Based on M1604792 Also remove ParseGoal being passed through Parser introduced in #1691 Part 2. (1c70f64e) (61eee537b) - import from UXP: No Issue - Updates to Mac packaging for notarization. Add Mac entitlements. Switch to using "create" instead of "makehybrid" when creating the disk image. This fixes bogus extended attributes which interfere with the code signature. Finally add any -bin or dylibs in the Resources folder since --deep skips that folder. (fae36a95) (abe8bd4fc) - import from UXP: No issue - Limit JPEG decoder memory allocation to surface cache size. (cc6ef1f3) (9888024e0) - import from UXP: [widget] Rewrite data-read loop in OnDataAvailable. (500af2fe) (728741fc2) - import from UXP: No issue - Disable ms-cxh and ms-cxh-full protocol handling. (ea32d13d) (eecf98199) - import from UXP: No issue - block a few problematic DLLs. (e39dc9d9) (77d7456f5) - import from UXP: [Basilisk] Issue MoonchildProductions/UXP#1451 - Follow-up: Only copy hunspell shared library if we're not building against system Hunspell. (6b13231b) (557bd3b25)1 point
-
New build of BOC/UXP for XP! Test binary: MailNews Win32 https://o.rthost.win/boc-uxp/mailnews.win32-20230513-73569c73-uxp-1e37e713c-xpmod.7z BNavigator Win32 https://o.rthost.win/boc-uxp/bnavigator.win32-20230513-73569c73-uxp-1e37e713c-xpmod.7z source repo (excluding UXP): https://github.com/roytam1/boc-uxp/tree/custom Changes: - [Mail] Issue MoonchildProductions/UXP#1451 - Follow-up: Only copy hunspell shared library if we're not building against system Hunspell. (b359e7ad) - [Navigator] Issue MoonchildProductions/UXP#1451 - Follow-up: Only copy hunspell shared library if we're not building against system Hunspell. (73569c73) * Notice: the profile prefix (i.e. parent folder names) are also changed since 2020-08-15 build, you may rename their names before using new binaries when updating from builds before 2020-08-15. -- New build of HBL-UXP for XP! Test binary: IceDove-UXP(mail) https://o.rthost.win/hbl-uxp/icedove.win32-20230513-id-656ea98-uxp-1e37e713c-xpmod.7z IceApe-UXP(suite) https://o.rthost.win/hbl-uxp/iceape.win32-20230513-id-656ea98-ia-93af9a0-uxp-1e37e713c-xpmod.7z source repo (excluding UXP): https://github.com/roytam1/icedove-uxp/tree/winbuild https://github.com/roytam1/iceape-uxp/tree/winbuild Changes: - [IceDove] Issue MoonchildProductions/UXP#1451 - Follow-up: Only copy hunspell shared library if we're not building against system Hunspell. (d5e08d7) - [IceApe] Issue MoonchildProductions/UXP#1451 - Follow-up: Only copy hunspell shared library if we're not building against system Hunspell. (360d9b0) for UXP changes please see above.1 point
-
New build of Serpent/UXP for XP! Test binary: Win32 https://o.rthost.win/basilisk/basilisk52-g4.8.win32-git-20230513-3219d2d-uxp-1e37e713c-xpmod.7z Win64 https://o.rthost.win/basilisk/basilisk52-g4.8.win64-git-20230513-3219d2d-uxp-1e37e713c-xpmod.7z source code that is comparable to my current working tree is available here: https://github.com/roytam1/UXP/commits/custom IA32 Win32 https://o.rthost.win/basilisk/basilisk52-g4.8.win32-git-20230513-3219d2d-uxp-1e37e713c-xpmod-ia32.7z source code that is comparable to my current working tree is available here: https://github.com/roytam1/UXP/commits/ia32 NM28XP build: Win32 https://o.rthost.win/palemoon/palemoon-28.10.6a1.win32-git-20230513-d849524bd-uxp-1e37e713c-xpmod.7z Win32 IA32 https://o.rthost.win/palemoon/palemoon-28.10.6a1.win32-git-20230513-d849524bd-uxp-1e37e713c-xpmod-ia32.7z Win32 SSE https://o.rthost.win/palemoon/palemoon-28.10.6a1.win32-git-20230513-d849524bd-uxp-1e37e713c-xpmod-sse.7z Win64 https://o.rthost.win/palemoon/palemoon-28.10.6a1.win64-git-20230513-d849524bd-uxp-1e37e713c-xpmod.7z Official UXP changes picked since my last build: - Issue #2232 - Parse exported async functions. (9693552c5) - Issue #2234 - Part 1: Create async function wrapper when instantiating module functions (ab1c0a384) - Issue #2234 - Part 2: Ensure that the created async function wrapper is valid (e52da4707) - Issue #2234 - Part 3: Update tests (2d6c41966) - Issue #2236 - Fix import.meta module error in lambdas by moving parseGoal() into SharedContext. Based on https://bugzilla.mozilla.org/show_bug.cgi?id=1604792 Also remove ParseGoal being passed through Parser introduced in #1691 Part 2. (1c70f64e7) - No Issue - Updates to Mac packaging for notarization. Add Mac entitlements. Switch to using "create" instead of "makehybrid" when creating the disk image. This fixes bogus extended attributes which interfere with the code signature. Finally add any -bin or dylibs in the Resources folder since --deep skips that folder. (fae36a95e) - No issue - Limit JPEG decoder memory allocation to surface cache size. (cc6ef1f3b) - [widget] Rewrite data-read loop in OnDataAvailable. (500af2fe5) - No issue - Disable ms-cxh and ms-cxh-full protocol handling. (ea32d13dc) - No issue - block a few problematic DLLs. (e39dc9d9b) Official Pale-Moon changes picked since my last build: - [Pale-Moon] Issue MoonchildProductions/UXP#1451 - Follow-up: Only copy hunspell shared library if we're not building against system Hunspell. (aadd6244c) - [Pale-Moon] No issue - Silence tab closing animation assert if the tabbrowser is not visible (4a9e6100e) - [Pale-Moon] No issue - Ensure window.location exists before checking against the browser URL (a39686b91) - [Pale-Moon] No issue - Remove invalid key attribute on Permissions menu item (1ae0d6ff7) No official Basilisk changes picked since my last build. My changes since my last build: - [Basilisk] Issue MoonchildProductions/UXP#1451 - Follow-up: Only copy hunspell shared library if we're not building against system Hunspell. (6b13231b9)1 point
-
I don't expect Windows 7 support for much longer than a year from now anyway, but more testing might leave us with a slightly better final version indeed. And yes, it's a nice surprise that the hotfix is out already.1 point
-
Greetings. Thanks. Package "python3" is a python 3.4.3 with a bunch of patches (look at source package). http://cygwinxp.cathedral-networks.org/x86/release/python3/ At first look - strange problem in Makefile Lines in Makefile 028: VERSION= 3.4 043: LDVERSION= $(VERSION)$(ABIFLAGS) 196: LDLIBRARY= libpython$(LDVERSION).dll.a 199: DLLLIBRARY= libpython$(LDVERSION).dll But 655: $(DLLLIBRARY) libpython$(VERSION).dll.a: $(LIBRARY_OBJS) So it will build "libpython3.4.dll.a", but "libpython3.4m.dll" and search for linking with "libpython3.4m.dll.a" Please try to replace "$(VERSION)" with "$(LDVERSION)" in 655 string of Makefile or 641 of Makefile.pre.in PS. Sorry, i need some more time to understood Cygwin. UPD: 3.4-distutils-soname.patch:21 ! UPD2: With patches from 3.4.3 (last - python3-3.4.3-1.src.patch - must be applued with "-f") 3.4.10 compiles and works under Cygwin. Best regards.1 point
-
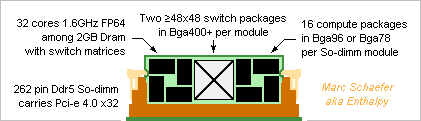
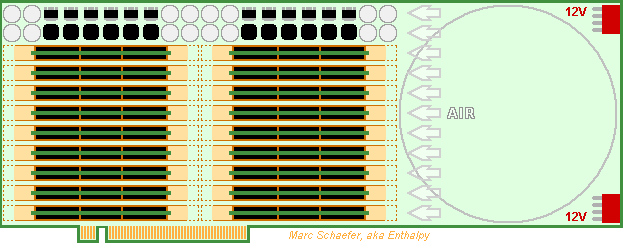
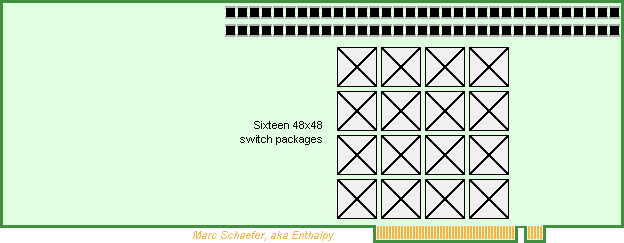
Using the already described technologies, a Pci-e number cruncher card can make money until supercomputers reuse its development effort. Here's a competitor to Nvidia's Hopper (30TFlops on 64b MAdd) and Amd's Instinct M210 (22.3TFlops as Pci-e card), much easier to program efficiently. 64b 1.6GHz scalar cores with FP64 MAdd compute everything. No Sse, Avx nor HT. Mmx-style parallelism welcome for vector 60TFlops FP32, 120TFlops FP16, INT32, Int16, Int8. A core uses the same power and area to multiply 2*2 32b numbers for matrix 120TOps, 4*4 16b 480TOps, 8*8 8b, and accumulate the columns, as complex numbers too. Enough complexity for the instruction set, sequencer, the compiler, the programmer! Consider faster 32b cores taking a few cycles on 64b. Arm, i64, a64, Mips, Risc, Sparc... make little difference. 32 such cores and chips access 1/32 of a 2GB Dram chip in one compute package, as already described. The MI210 and the Hopper offer only 8MB/core at identical Flops. Scaled as the Flops, 64MB Dram make 2GB for a 3GHz Avx256 quad-core, but 8MB make only 1/4 GB behind one Pci-e connector. The Dram provides 3*read+1*write/MAdd throughput for easy programming, plus the already described data shuffling for Fft and database. The Hopper's Dram reads or writes 0.1 FP64/MAdd and the MI210's 0.05. The cores have registers and L1 but no L2, L3... thanks to snappy Dram. 64 cores at 0.8GHz would cut the latency /4. The cores communicate over full switch matrices in a compute package. The Dram can integrate several >32*32 matrices or carry switch chips identical to the ones packages for the boards. For instance 8 parallel matrices at 16GT/s transfer one 64b data every core cycle between every core pair simultaneously. Alas, the boards carry fewer lanes, so the compute packages communicate with the outer world over their internal matrices for flexible bandwidth allocation, as in a fat tree network. The matrices, possibly Asics, communicate per Pci-e to serve between recycled Xeons too. 2GB/s Pci-e 4.0, of if possible Pci-e 5.0. A >48*48 full switch matrix takes little silicon in a Bga400+ and can use smaller packages where fewer lanes suffice. Each matrix connects all compute packages on one module, two matrices route x6 parallel lanes, this carries only 1 word per compute package in 1 cycle, or if spread evenly, 1 word per core in 34 cycles. The address is sent first, and upon knowing it, the matrices forward the data. Error detection happens later. The smallest message, about 64b, is but bigger than an address. The number of lanes used, sometimes over indirect paths, depends on the message size. Add operation modes to the Pci-e standard. The connector carries x32 lanes, So-dimm are denser. At least Amphenol sell vertical ones. 64GB/s provide 1 word per compute package in 3.2 cycles, or 1 word per core in mean 100 cycles. Each compute package passes x2 lanes through the connectors: the matrices first spread big messages among the compute packages. 18 modules fit on a double-slot Pci-e card to pack 9216 cores, 30TFlops and 0.56TB. The centrifugal blower cools easily 2W per compute package but 576W is much for one card. At the card's center, the blower would be quieter and ease routing but inject 300W heat in the tower. Each matrix connects the 18 modules, 16 matrices route x32 parallel lanes. Procuring standard Ddr5 2GB chips would cost 1.5kusd according to module price on eBay while the competing cards sell for 10kusd. Stacked Dram doubles the capacity but quadruples the cost, 1GB Dram costs half as much: product line. The tiny core chips are cheap and easily made. The matrices should add little and may well exist already. Marc Schaefer, aka Enthalpy aka Pointertovoid1 point
-
Chances are that eScanAV Anti-Virus Toolkit (MWAV) will even run on systems whose CPU has no more than the SSE instruction set. However, since the program is portable, compatibility can easily be checked. @Dušan Vićić Here are the system requirements for the commercial version of eScanAV Anti-Virus: Minimum Hardware Requirements: Component Requirement Processor Intel or AMD single core x86 or x64 CPU. 1 GHz recommended RAM 1 GB recommended Disk Space 1GB recommended Due to the fact that an AMD single core x86 is listed, I think it might run on hardware with a CPU which has no more than the SSE instruction set. Kind regards, AstroSkipper1 point
-
Finally, something that i was searching for a loooooong time. I don't mind it it's offline, but i think it is not a demanding one. It seems that i can't find any system requirements on their website, for some reason. For the layout of the antivirus i sincerely hope that it can run on the non SSE processors cuz it feels like those old antivirus programs from 9x/ME.1 point
-
1 point
-
Apologies I'm not participating in this discussion as much as I would've hoped ; dealing with solicitors/lawyers/civil servants/government employees/etc. over inheritance issues in RL currently, all that "torture" sucks the life (and serious money) out of you and, consequently, spare time to devote on internet forums... In the background, I've been doing my own research, too ... ... Oh yes, the drawbacks of on-line/web installers and the very reason I detest them vehemently ; they become worthless when the stuff they're supposed to fetch vanishes into thin (digital) air ... I have several archived KFA19 web installers on a spare external HDD that were downloaded at the time the app was current (mid-2018 to mid-2019), which correspond to different localisations/Kaspersky patch levels (e.g [a.b], [a.b.c.d]); download links for these I now simply lost or (the ones I have bookmarked) return 404s... Kaspersky did publish a FULL offline installer (which, sadly, I haven't archived) for KFA2019 around its initial release, but soon they moved on to a web-installer-only scheme, a practice still kept for the subsequent KFA releases (kfa20, kfa21, targeting Win7SP1+; these two seem to have been remodeled, based on a newer "Cloud" engine/product: Kaspersky Security Cloud, KSC). Of those stub KFA2019 installers, one (kfa19.0.0.1088ab_en-gb_14833.exe) produced below message: I guess the same one @mina7601 encountered ... But another one (kfa19.0.0.1088abcd_en-US_fr-CA_es-US.exe) ended up with a different message: however, that was a misleading error ; unable to retrieve the now missing files for KFA19, it proceeded to download a web installer of KFA20 (v20.0.14.1085.0.6449.0), which, when executed, threw the error about the incompatible OS - all this was found out via inspecting the log file generated inside %TEMP% ... A third stub installer (kfa19.0.0.1088a_en-gb_14166.exe) produced, yet again, a different error: In that last case (resolved by inspecting log files), the stub installer proceeded to fetch a second stub installer of KFA21 (v21.3.10.391.0.2008) which, predictably, failed to install.. My research has also unearthed a 2018 malwaretips post, in which it was documented that the KFA2019 web installers of the era (for en-GB locale) would actually download below list of files/archives: KFA 2019: http://dm.kaspersky-labs.com/bases/kavkis2019/KIS/corebases.cab http://dm.kaspersky-labs.com/bases/kavkis2019/KIS/corebasesx64.cab http://dm.kaspersky-labs.com/bases/kavkis2019/KIS/corebasesx86.cab http://dm.kaspersky-labs.com/bases/kavkis2019/KIS/instx64.z http://dm.kaspersky-labs.com/bases/kavkis2019/KIS/instx86.z http://dm.kaspersky-labs.com/bases/kavkis2019/KIS/productbases.cab http://dm.kaspersky-labs.com/en-GB/KFA/19.0.0.1088/common.z http://dm.kaspersky-labs.com/en-GB/KFA/19.0.0.1088/coreproductnogdpr.z http://dm.kaspersky-labs.com/en-GB/KFA/19.0.0.1088/coreproductgdpr.z http://dm.kaspersky-labs.com/en-GB/KFA/19.0.0.1088/coreproduct.z http://dm.kaspersky-labs.com/en-GB/KFA/19.0.0.1088/coreproductx64.z http://dm.kaspersky-labs.com/en-GB/KFA/19.0.0.1088/eula_en-gb.txt http://dm.kaspersky-labs.com/en-GB/KFA/19.0.0.1088/ipm.cab http://dm.kaspersky-labs.com/en-GB/KFA/19.0.0.1088/ksde_ksn_en-gb.txt http://dm.kaspersky-labs.com/en-GB/KFA/19.0.0.1088/product.cab.z http://dm.kaspersky-labs.com/en-GB/KFA/19.0.0.1088/product.msi.z http://dm.kaspersky-labs.com/en-GB/KFA/19.0.0.1088/rdp_en-gb.txt http://dm.kaspersky-labs.com/en-GB/KFA/19.0.0.1088/startup.exe http://dm.kaspersky-labs.com/en-GB/KFA/19.0.0.1088/x64.cab.z http://dm.kaspersky-labs.com/en-GB/KFA/19.0.0.1088/ztuu.z http://dm.kaspersky-labs.com/kleaner/InteractiveNew/Global/kleaner.cab The "http://dm.kaspersky-labs.com/bases/kavkis2019/KIS/*" dir appears to be still alive today, as well as access to last archive kleaner.cab, but, as already posted by others, dir "http://dm.kaspersky-labs.com/en-GB/KFA/19.0.0.1088/*" has been now purged ... Some savvy people had concocted self-made "full" (off-line) installers at the time, based on lists similar to the above; I myself have an archived "RePack" which I won't share, because it's only in the Russian locale and made by, well, a Russian repacker (LcHNextGen) of that era... I haven't yet tested Astroskipper's repacked RePack (), hopefully we'll soon hear results from mina7601 (many thanks BTW ) ... It might not be the case after all ... During my research, I found some posts inside the nsaneforums forum (due to the "dubious" nature of said site, I won't provide exact links), an installation scenario might involve the following procedure: 1. Download the off-line installer for KIS2019 (Kaspersky Internet Security): https://arc-products.s.kaspersky-labs.com/homeuser/kis2019/19.0.0.1088abcd/english-INT-0.5887.0/3137353438307c44454c7c35/KIS19.0.0.1088_en_full.exe 2. Install the application as required (decline any offers to install newer versions; no other AV suite should be present, all H/W and S/W requirements for KIS2019 should have been observed/applied). 3. After the necessary OS restarts post initial install, try (for good measure) to update the Virus Definitions - you can only do so once without a valid licence; the app may or may not be activated now with a trial (30d) licence, this is at Kaspersky's discretion - if you do get a trial licence, you may continue to use the product fully until the trial ends - else (or after the trial expires): 4. Proceed to uninstall the application; if my "sources" were correct, one of the options offered during uninstall is to "turn the application into Kaspersky Free 2019"; if you select that, upon OS restart you'll end up with a KFA2019 installation; if you don't now have a 365d worth "free" key, you should first create a "My Kaspersky Account" to then get one (YMMV - my sources are from 2019 ) ...1 point
-
eScanAV Anti-Virus Toolkit (MWAV) eScanAV Anti-Virus Toolkit (MWAV) is an offline virus scanner from MicroWorld Technologies Inc., free for private and home use. And yes, it is still fully XP-compatible. MWAV provides the ability to scan for and remove any virus, spyware, adware or other malware on your computer. The database is continuously updated to detect new spyware and adware, and the scanning engine is constantly improved for faster and smarter detection. It requires no installation and can be run directly from your computer, on whatever media. It can also run when other antivirus software is installed on your computer. To "install" MWAV on the computer, I recommend extracting the installer manually to the desired target directory and calling the executable file mexe.com or MWAVL.exe there. Reason: If the installer is called directly, all files are extracted to the system's temporary folder. For me, this is not an option. MWAV is available in English, German, French, Nederlands, Italian, Portuguese, Spanish, Turkish, Chinese Simplified, Chinese Traditional, Greek, Korean, Norwegian, Russian, Polish and Latin Spanish. Homepage: https://www.escanav.com/en/mwav-tools/download-free-antivirus-toolkit.asp Version number: 22.0.60 Date of release: 26.04.2023 System requirements: Windows® 2012 R2 / 2012 / 2008 R2 / 2008 / 2003 R2 / 2003 / 10 / 8.1 / 8 / 7 / Vista / XP (32 & 64 bit OS compatible) Minimum Hardware Requirements: Processor: Intel or AMD single core x86 or x64 with SEE2 instruction set, 1 GHz recommended RAM: 1 GB recommended Disk Space: 1GB recommended Review: https://www.majorgeeks.com/files/details/escanav_antivirus_toolkit.html Download link of MWAV: https://www.escanav.com/en/antivirus-downloadlink/downloadcounter.asp?pcode=MWAV&src=english_dwn&type=alter Download link of the (weekly) offline virus database updater: http://www.microworldsystems.com/akdlm/download/tools/esupdatebd.exe Screenshots: eScanAV Anti-Virus Toolkit (MWAV) is a free utility that helps Windows users to scan and remove viruses, spyware, adware and other malware that have infected their computers. It's free of charge and still compatible with Windows XP. The virus databsse can be updated online and even offline if the computer is not connected to the internet. Additionally, commercial products are offered which were tested by AV-Test and Virus Bulletin with very good results. I can definitely recommend this tool without any concerns. Cheers, AstroSkipper1 point
-
Kaspersky Free Antivirus 19.0.0.1088 For all who are interested in KFA 19 (not me )! I found a download link to an offline installer for Kaspersky Free Antivirus 19.0.0.1088. I sent the link to @Dave-H to give his assessment whether I am allowed to post it here or not. He found an unwanted program inside reported by MBAM. Therefore, I decompressed (SFX-compressed) and unpacked the installer with UniExtract. Then I analyzed the installer. The installer was repacked by SolidShare. That's indeed a common practice by a lot of these websites. There was an SFX script inside which forced to start the file kur.exe. This file was not original and therefore deleted by me (and also the SFX script). I checked all files inside with MBAM, and they were clean except of course kur.exe, harmless, though, but nevertheless unwanted. I packed the files of the cleaned folder into a new 7-Zip archive KFA 19.0.0.1088.7z and uploaded it for you. Here is the download link: https://www.mediafire.com/file/5b41tc67a29vvbm/KFA_19.0.0.1088.7z/file The installation has to be started with the original file startup.exe. One thing is clear: all at your own risk. The archive is clean, but I didn't test the original files from Kaspersky. And I won't do that as I already mentioned here in this thread. Have fun! Cheers, AstroSkipper1 point
-
Link already sent via PM.1 point
-
If it's a private upload on a hosting site such as Mega or Dropbox it's probably OK. However if it's on a download site that contains warez it certainly isn't! PM me the link and I will check it out.1 point
-
Norton was actually spun off from Symantec before merging with Avast, so Symantec is not part of Gen Digital. There has long been a need for consolidation in the antimalware industry because there were too many unprofitable vendors competing. Now that the typical Windows 10 user simply relies on Microsoft’s excellent antimalware, Gen Digital just might be big enough to survive! I thought you disapproved of “discussions about concerns regarding the country of origin”? You make an exception for Russia, but apparently imagine that China exists to benefit Windows XP diehards.1 point
-
Exactly. Luckily we're on an old version that won't get any changes anyway. I just hope they won't kill it. Ah and by the way, the merger has only been approved by the European regulator few days ago, so they were still effectively two separate companies. Anyway, it saddens me a bit to see avast end up in the hands of Symantec (which is actually broadcom). So now we have Piriform (Speccy, CCleaner etc), Norton, Symantec, Avira, AVG and Avast all under one single company, Gen Digital. P.s I saw the whole discussion about Kaspersky, but to be fair, the last thing I wanna do in this historical period is install a Russian antivirus on my computer. I mean... it's probably ok, but these days you never know...1 point
-
It should work on regular Windows 7 with SP1 (it always worked in my VM with nothing but SP1, but some users complained about it not loading because of missing delay-load module; my second release should solve that). Vista needs the extended kernel however.1 point
-
for DPI, you still need installing a Root Cert in browser's Cert Store in order to make it "look-like" transparent. without doing this, users end-up getting "Unknown Issuer" security warning page instead.1 point
-
have to follow WaterfoxClassic here and it is workarounded for now. https://github.com/roytam1/basilisk55/commit/ef905bceeccc41328613c0a831a52e99d5541a9c1 point
-
A temporary workaround: disabling javascript.options.ion stops the crash.1 point
-
it hits a code path (about JSOP_GOTO) that it shouldn't (as it should be handled in IonControlFlow, not in IonBuilder) so it needs more investigations. maybe hitting this: https://github.com/WaterfoxCo/Waterfox-Classic/commit/6d15d320de43f57fe549b44052941c8a6808f6ce but it is ported correctly, but why JSOP_GOTO goes to elsewhere?1 point
-
It just seems to be happening in Serpent 55.0 only and only if javascript is on. Probably other sites are affected as well.1 point
-
Spectrum is coming in again so it continues to get better. There is a crash with this site using Serpent 55: http://www.legacy.com/news/celebrity-deaths/notable-deaths?affiliateId=1859 The failure is with mozjs.dll. The last April 15th build was good so it just started. 52.0 is no problem.1 point
-
XP is old but millions of people around the world still use it because they have to for whatever reason. Heck I still boot into it on occasion because perfectly good software like Nero 7.5 won't install on Windows 7+. That was intentional to force users to purchase upgrades. Now Microsoft has upped the game with Windows 11 and unrealistic OS requirements for literally hundreds of millions. Hopefully they'll get slapped with antitrust lawsuits and fines once Win 10 has expired.1 point