Leaderboard
Popular Content
Showing content with the highest reputation on 03/02/2024 in all areas
-
I found an alternative way to update uBlock Origin Legacy when the user still decides to install over an existing installation: Backup all your settings using the "Back up to file" button on the page "Settings". Install the new version of uBlock Origin Legacy over the existing one. Reset your installation using the "Reset to default settings" button on the page "Settings". Restore all settings from your backup file. This method can only be used for updates with the same extension ID, i.e. from version 1.16.4.32 and higher or from version 1.16.4.31 and lower. The reason for this is the change of the extension ID in version 1.16.4.32 I have performed. But one thing is clear. A clean install is the best method that causes the fewest problems. Greetings, AstroSkipper4 points
-
3 points
-
... That's NOT accurate to say ; while both OSes are NT 6.0, per your linked documentation: Windows Vista SP2 x86 & x64 Official Extended Support was EoL'ed on Apr 11th, 2017 : https://learn.microsoft.com/en-us/lifecycle/products/windows-vista It is indeed true that the WS 2008 SP2 targeting updates released some two years after Vista's official End of Extended Support can be installed manually on the OS and bestow SHA-2 support on it, but this practice isn't considered "official" by either the vendor (Microsoft) or the rest of the third party vendors (Norton in this case ) ... Kindest regards ...2 points
-
NortonLifeLock has announced that they will stop supporting Norton Security v22.15.x products on Vista and other older OSs that do not support SHA-2 code signing as of 22-May-2024. See employee Gayathri_R's 01-Mar-2024 announcement End-of-Life announcement for Norton security software on Windows XP, Windows Vista, and Windows 7 (SP0) for more information. Note that Win 7 SP0 is Win 7 without Service Pack 1. NortonLifeLock threatened to end support for Norton Security v22.15.x a few years ago and reversed their decision after customers complained but I think they intend to stick to the 22-May-2024 end-of-life date this time.2 points
-
@Damnation nt!KiDispatchInterrupt+0x393: 804dcbe5 3b6d00 cmp ebp,dword ptr [ebp] 11: kd> p nt!KiDispatchInterrupt+0x396: 804dcbe8 740d je nt!KiDispatchInterrupt+0x3a5 (804dcbf7) 11: kd> p nt!KiDispatchInterrupt+0x3a5: 804dcbf7 83bb2801000000 cmp dword ptr [ebx+128h],0 11: kd> p nt!KiDispatchInterrupt+0x3ac: 804dcbfe 74d7 je nt!KiDispatchInterrupt+0x385 (804dcbd7) 11: kd> p Packet failed authentication. Please make sure the host and target encryption keys match exactly. Also make sure you don't have multiple target machines pointed at the same network port on your host. Bad packet sent from 192.168.2.102. Run nslookup 192.168.2.102 from a command prompt to get the machine name. Packet failed authentication. Please make sure the host and target encryption keys match exactly. Also make sure you don't have multiple target machines pointed at the same network port on your host. Bad packet sent from 192.168.2.102. Run nslookup 192.168.2.102 from a command prompt to get the machine name. Packet failed authentication. Please make sure the host and target encryption keys match exactly. Also make sure you don't have multiple target machines pointed at the same network port on your host. Bad packet sent from 192.168.2.102. Run nslookup 192.168.2.102 from a command prompt to get the machine name. nt!KiDispatchInterrupt+0x38d: 804dcbdf f390 pause 10: kd> p2 points
-
@Damnation This is Bsod surrounding without any breakpoint, Windbg continous with "p", F10, Dietmar https://ufile.io/b5j6aq0z2 points
-
@Damnation I have your hal.pdb integrated. Now I get this, looks like kind of loop, or if something cant be found Dietmar https://ufile.io/310s052p2 points
-
@Damnation Yes, I fixed everything that is possible on the HP 255 g6 board. Now, there is ACPI-Multprocessor with mostly all drivers. A lot of other notebooks boot with the same idea XP SP3 now, which show before Bsod, not direct related to acpi.sys. All those Bsods happen because of their VGA settings in DSDT and their internal VGA cant be disabled via Bios. Now I am just setting up a new XP SP3 on my Asrock z370 k6 board. Without any extra driver, just naked and ready for debug. This is possible, because it can use PS/2 for mouse and keyboard. Then I add your acpi.sys, hal.dll and ntoskrn8.sys. Soon I report Dietmar2 points
-
i had some time to look at it his function is bugged up basicly he write it himself "// hacky but works: small number is command id, large is submenu (a pointer)"" that indicates he tryed to trick it and had to do "hacky solutions" he use a endless while true loop with ends escapes and continues, also goto´s,calls to the same functions in a function, and then seperators for his menu to fix how he called it "bad seperators" this ended up in a os specific solution you useally dont do that because the operating system can might change the relevant codes over time (such as 7 to 10, or 98 to nt) - something like this already happend in the past but the solution to this problem is possible as the author use multiple fixes all over around (probaly to compensate the problems) it is easy to add that fix - anyways it actually was a bit weird to find it out in win10 its just a flag, that was found like very quickly - but no in xp it didnt do that and gave very weird results even turned off xp was working ok while on 10 it did what it suppose to do - it was turned off as the code suppose to was changed to let me know if it works now! the .avif file (and heic) format dont work for me, neither on xp nor on 10 nor on 7 (both unchanged from the official download page and the changed version) https://www.file-upload.net/download-15277606/SumatraPDF_WINXP_3.5.2_3.zip.html https://www.mediafire.com/file/a4mtyf33ozs6q63/SumatraPDF_WINXP_3.5.2_3.zip/file1 point
-
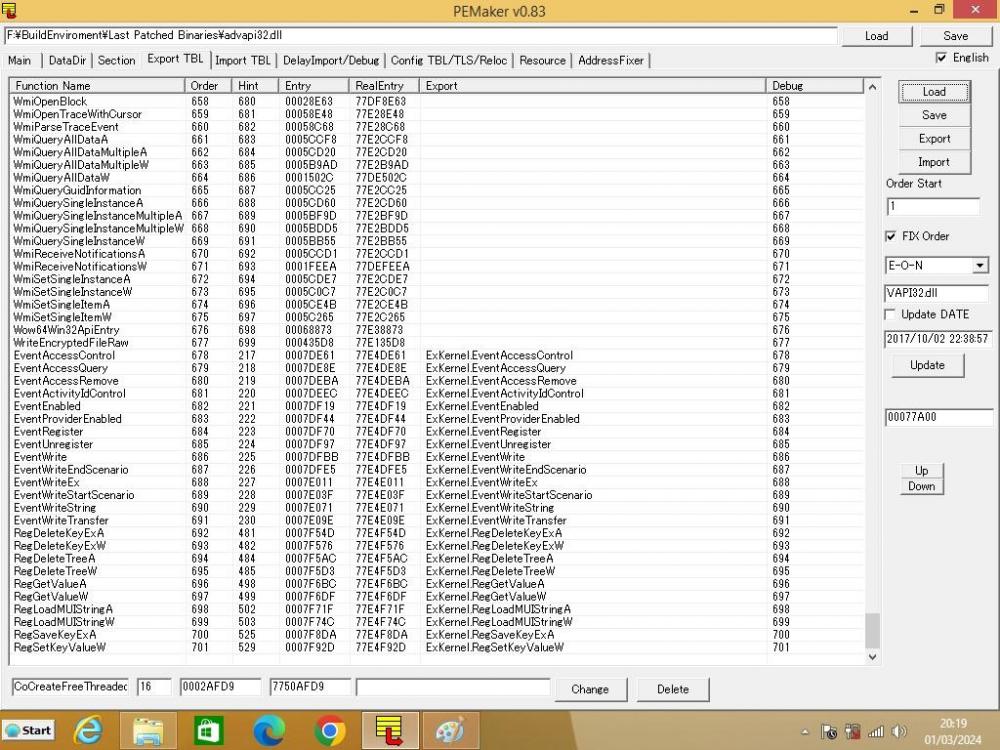
I thought that I ought to push things along with this project with this post. The objective is to update Dibya's last patched binaries so that they are based on the last POSReady 2009 updates of these modules. It ought to be possible to patch other system files using the same techniques. The approach that Dibya has used is to patch the export table of these binaries so that API calls to NT6 functions are forwarded to an external dynamic link library that acts as a container for all the additional NT6 functions for the patched kernel32.dll, advapi32.dll, ole32.dll, shell32.dll and user32.dll. This external dynamic link library is called ExKernel.dll. I have provided a screen shot of the patched advapi32.dll opened in PE Maker here: Exkernel.dll is built by dissasembling Microsoft and Wine binaries to extract the subroutines for the additional NT6 functions to make the asm file ExKernel.asm which is then assembled with nasm.exe to produce the object file ExKernel.obj. ExKernel.obj is passed to golink.exe to link Exkernel to advapi32.dll, shell32.dll, kernel32.dll, and ntdll.dll. The ExKernel.asm file contains a table for imports as in the sample below: ; IMPORT TABLE EXTERN RtlEnterCriticalSection EXTERN RtlLeaveCriticalSection EXTERN WaitForSingleObject ;EXTERN _alloca_probe EXTERN RtlInitializeCriticalSection EXTERN SetEvent EXTERN RtlSetLastWin32Error EXTERN RtlTryEnterCriticalSection EXTERN GetLastError EXTERN GetProcessHeap EXTERN RtlAllocateHeap EXTERN ExitThread EXTERN CreateEventA EXTERN LoadLibraryA The table for exports is shown in the sample below: ; EXPORT TABLE GLOBAL AcquireSRWLockExclusive EXPORT AcquireSRWLockExclusive GLOBAL AcquireSRWLockShared EXPORT AcquireSRWLockShared GLOBAL InitializeSRWLock EXPORT InitializeSRWLock GLOBAL ReleaseSRWLockExclusive EXPORT ReleaseSRWLockExclusive GLOBAL ReleaseSRWLockShared EXPORT ReleaseSRWLockShared GLOBAL TryAcquireSRWLockExclusive EXPORT TryAcquireSRWLockExclusive GLOBAL TryAcquireSRWLockShared EXPORT TryAcquireSRWLockShared GLOBAL InterlockedCompareExchange64 EXPORT InterlockedCompareExchange64 Here is a sample of a subroutine in assembly included in ExKernel.asm FindNextStreamW: ;blackwingcat KB935839 2017.04 push ebp mov ebp,esp mov ecx,[ebp+08h] mov edx,[ecx+04h] add edx,[ecx+0Ch] mov eax,[ecx+08h] cmp eax,edx jnz L77EA5881 push 3221225489 ;C0000011h call SUB_L77E5826D xor eax,eax jmp L77EA58D4 L77EA5881: mov ecx,[eax+08h] mov edx,[ebp+0Ch] mov [edx],ecx mov ecx,[eax+0Ch] mov [edx+04h],ecx mov ecx,[eax+04h] push ebx push esi mov ebx,ecx push edi shr ecx,02h lea esi,[eax+18h] lea edi,[edx+08h] rep movsd mov ecx,ebx and ecx,00000003h rep movsb mov ecx,[eax+04h] shr ecx,1 and word [edx+ecx*2+08h],0000h mov eax,[eax] test eax,eax pop edi pop esi pop ebx jbe L77EA58C5 mov ecx,[ebp+08h] add [ecx+08h],eax jmp L77EA58D1 L77EA58C5: mov eax,[ebp+08h] mov ecx,[eax+04h] add ecx,[eax+0Ch] mov [eax+08h],ecx L77EA58D1: xor eax,eax inc eax L77EA58D4: pop ebp retn 0008h Here are some issues that I am unclear about and I would like Dibya or someone to clarify: Can someone supply instructions on how to use PE Maker to add additional entries to the export table? How do you know if there is sufficient space in the binary to be patched to accommodate these new entries in the export table without over-writing some of the existing code? Is there some way of creating extra space in the binary to to accommodate these new entries? What tool is recommended to extract functions as assembly from Microsoft and Wine binaries? Why criteria would you use to choose either Microsoft, Wine or BWC binaries as a source for these extracted functions? If you decide not to use an external dynamic link library as a container for the additional NT6 functions how would you insert them into the binary to be patched? Would you dissasemble the binary to be patched and paste the dissasembled NT6 functions into it's asm file then assemble it, or could you extract the NT6 functions as hex and paste them into a hex dump of the binary to be patched? ExKernel.asm1 point
-
My previous post must have seemed naive to an expert like VistaLover, but I had anticipated that the CDM client would calculate a checksum of it's main dll to detect tampering, and if the checksum did not match the correct one in the client's code a signal would be sent to the widevine server to halt the download of the encrypted keys. Castlabs are now offering a free service for Widevine/VMP signing of application packages derived from official releases of Electron. They also offer a commercial VMP certification of custom Chromium/Electron adaptations which sounds like it is not free. Perhaps VistaLover could study this page Electron for Content Security VMP signing service and make some recommendations to the Supermium developer.1 point
-
... I launched my Kafan MiniBrowser (KMB) copy (Chromium 87 based) on my Vista SP2 x86 OS with below command-line argument: --user-agent="Mozilla/5.0 (Windows NT 6.1) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/109.0.0.0 Safari/537.36" Then I navigated to: https://chromewebstore.google.com/detail/ublock-origin/cjpalhdlnbpafiamejdnhcphjbkeiagm?hl=en Guess what? Yes, the previous banner: no longer displayed, but ONLY to be replaced by a new banner, stating: WT... ?1 point
-
New regular/weekly KM-Goanna release: https://o.rthost.win/kmeleon/KM76.5.1-Goanna-20240302.7z Changelog: Out-of-tree changes: * update Goanna3 to git ce0ac6811d...86eaa55e65: - fix passwordManager.dtd encoding error (60b86c75d9) - import changes from `dev' branch of rmottola/Arctic-Fox: - Bug 1254108 - Remove incorrect assertion about heap size r=terrence (a98d1df06b) - Bug 1244412 - Make ZoneCellIter work correctly whether called under GC or not r=terrence (cec67ebbd3) - Bug 1244412 - Remove ZoneCellIterUnderGC now it's no longer needed and refactor r=terrence (3b98615a8b) - Bug 1244412 - Fix suprious GC hazard r=me (bfbdee71b0) - Bug 1253461 - Fix race condition in Shape::fixupDictionaryShapeAfterMovingGC r=terrence (3f15dd893c) - Bug 1224038 - Part 1: Add infallible versions of uid and hashcode getters; r=sfink (c8a7bac9b5) - Bug 1252329 - Fix interaction between AutoClearTypeInferenceStateOnOOM and compacting GC r=terrence (3f35df9bad) - Bug 1224038 - Part 2: Use stable hashing for NewTable; r=sfink (1046b72221) - Bug 1224050 - Use stable hashing for the IntialShapesTable; r=jonco (08aa726019) - Bug 1227035 - Tighten the check in ObjectGroup::useSingletonForClone a bit more. r=bhackett (c817b1a595) - Bug 1257903 - Compact arenas containing shapes r=terrence (bc7f90586b) - Bug 1235572 - Enforce SRI if content signature is enforced r=francois (1f0723fccf) - Bug 1254856 - Use a better window for 3rd-party checks. r=sicking, r=billm (9160d94db5) - Bug 1253575 - Annotate the crash report on failure in opening the process handle for plugin or content process. r=billm (8940f5247c) - No bug. Make it easier to work on specific functions in the XDB files (01cd0735cc) - Bug 1251703 - Always resolve virtual calls to known callees, r=mccr8 (b042b74487) - Bug 1250709 - Implement shell-only hazard analysis job, r=garndt (a11947ad0d) - Bug 1253466 - Don't pass --enable-threadsafe to js/src/configure. r=mshal (ed2fd1554b) - Bug 1246804 - Switch to using in-source annotations. Use C++ inheritance information when describing GC types. Add a test suite., r=terrence (f5fddd8dad) - Bug 1257979 - Use a GCHashSet for a hash in the JSON stringifying algorithm. r=sfink (e6baa61177) - Bug 1242810. r=jandem (fca11d1b92) - Bug 1253099. r=arai, r=efaust (9972e18152) - Address review comments from bug 1246804 (f36a5d29df) - Bug 1226928 - dochsell changes for content-signing on remote about:newtab, r=bz,mconley (da3ecffcd4) - Bug 1226928 - content-signature verification tests for about:newtab, r=mconley (8f77c22596) - Bug 1257730 - Fix ping when no URI is available. r=sicking (67d3a9541d) - Bug 518805 - Don't do meta refreshes when backgrounded r=bz (609b2c0a2c) - Bug 513129 - Dont reuse connections after security prefs change r=hurley (379e74d1f1) - Bug 1256248 - allow disabling content-signatures for about:newtab on certain channels, r=mayhemer (35fadec30f) - Bug 1234896 - refptrs for httphandler.cpp r=valentin.gosu (7aff77f88e) - Bug 1242926 - Increase the max retry attempt number. r=mcmanus (9085644f4e) - Bug 1144040 - Coverity detected uninitialized nsHttpHandler members, r=mcmanus (8ec1e49577) - Bug 1231416 - fix Mulet UA string generation rule. r=fabrice. (d952dd06e2) - Bug 1220061 - Android UA is not correct when MOZ_UA_OS_AGNOSTIC is set r=gerv (e007b6f1a3) - Bug 962358 - Provide an observer event to close persistent connections. r=arthuredelstein (903d2fa203) - Bug 1226526 - NS_ENSURE_ARG_POINTER on result to remove warning added by scan-build. r=mcmanus (7d87d1502b) - Bug 1248452: Rewrite NS_IsHSTSUpgradeRedirect to use HttpBaseChannel::GetSecureUpgradedURI. r=jduell (f806456238) - Bug 1249450 part 1: Move GetSecureUpgradedURI from HttpBaseChannel to nsNetUtil. r=mcmanus (70b023486b) - Bug 1249450 part 2: Convert some nsIURI SetScheme("https") calls to use NS_GetSecureUpgradedURI instead. r=mcmanus (6dea15dd6b) - Bug 451081 - Introduce ORIGIN_IS_FULL_SPEC protocol handler flag, r=bz+standard8 IGNORE IDL (e7d651c6b7) - Bug 991016 - Check return value of a setDelegate call. r=efaust. (4bf66d532f) - Bug 1240414 - Fix ThrowUninitializedThis to do the right thing for eval and arrow function frames. r=efaust (a04625b047) - Bug 1254349 - Remove unused error messages. r=mrrrgn (58fd90f345) - Bug 1256464 - Use LPSTR instead of LPVOID to avoid C4477 on VS2015; r=froydnj (ec57a4894e) - bug 1250486 - make some xpconnect wrapper ctors constexpr to get rid of static constructors r=bz (7681e3102f) - Bug 1250192 - Do not synthesize a var binding for Annex B.3.5 if there is an arg binding of the same name. (r=jorendorff) (601ac2528c) - Bug 1237588 - One of the File::Create methods is not used, r=smaug (ac6f036ceb) - Bug 1173317 - Change the string argument for Directory::GetName from nsString to nsAString. r=sicking (1e670db10d) - Bug 1244782 - Removed non-used variables in Directory.cpp, r=smaug (0f01c9747a) - Bug 1234192 - part 1 - FileSystemBase should not be thread-safe, r=smaug (1d24a83a75) - Bug 1234192 - part 2 - Directory should unlink/traverse the OSFileSystem in order to unlink/traverse the window, r=smaug (acea1d57d6) - Bug 1251723 - remove ScopedDeletePtr; r=Waldo (eb6af862a5) - Bug 1252153 - use UniquePtr instead of ScopedDeletePtr in HeapCopyOfStackArray; r=jrmuizel (1ffb6c113f) - Bug 1251715 - use UniquePtr instead of ScopedDeletePtr in dom/media/; r=gerald (910c698731) - Bug 1239870 - Part 1: Remove declaration of test_utils from header. r=bwc (d295b3a379) - Bug 1239870 - Part 2: Split out NrIceCtx initialization. r=bwc (a399a76d59) - Bug 1239870 - Part 3: Add a base mtransport gtest. r=bwc (5d0a79a54d) - Bug 1239870 - Part 4: Disable broken proxy tunnel tests. r=bwc (8c24c01723) - Bug 1239870 - Part 5: Switch over mtransport tests to mozilla gtests. r=bwc (0e00f9e97d) - Bug 1251714 - use UniquePtr instead of ScopedDeletePtr in media/; r=jesup (a274b4172e) - Bug 1251718 - use UniquePtr instead of ScopedDeletePtr in WebGLElementArrayCache; r=baku (39ebd0f02f) - Bug 1251716 - use UniquePtr instead of ScopedDeletePtr in DrawTargetCairo; r=jrmuizel (fe889eaff3) (baacd3ba62) - import changes from `dev' branch of rmottola/Arctic-Fox: - Bug 1212114 - Stop using dom::Promise::MaybeRejectBrokenly() in various FileSystemTaskBase subclasses. r=baku (9f6ea5db27) - Bug 1253534 - Suspicious code with probably reversed parms in call to IsSingleLineTextControl, r=mounir (1a5ee1fd1e) - Bug 769117 - Mochitests for youtube flash -> html5 rewriting; r=bz r=hsivonen (6324471dd9) - Bug 1250148 - FormData should treat empty input type=file as empty string in FormData and as unnamed Blob in HTML submission, r=smaug (7043113247) - Bug 1173320 - patch 1/8 - Implement Directory object as string and not as BlobImpl, r=smaug (eca4bec6ea) - Bug 1173320 - patch 2/8 - Proper naming for the FileSystem path serialization, r=smaug (e1604ff2b1) - Bug 1173320 - patch 3/8 - Improve the Windows path management, r=smaug (f8da8541b5) - Bug 1252347 - Provide missing implementations of nsIBaseWindow::SetPositionDesktopPix. r=emk (97f9b92465) - Bug 1235066 - SVG elements should not display title attributes as tooltips. r=enndeakin (a77e809688) - Bug 1251809 - Add input[type=file] tooltip support for e10s. r=ehsan (9f72cf3cd2) - Bug 1173320 - patch 4/8 - Directory in FileList, r=smaug (c09d445043) - Bug 1246244 - Regression test. r=jaws,Margaret (8de084f9db) - Bug 1224105 - Allow windowless chrome docshells containing content docshells (r=smaug) (3343a2a966) - Bug 1230267 - Inconsistent display of SVG title as tooltip when multi-process is enabled. r=jst (b3fc298b7f) - Bug 1173320 - patch 5/8 - Cleanup manual string path management, r=smaug (8f6f0c4e44) - Bug 1250403 - Part 1. Define ARCH_CPU_ARM64 instead of ARCH_CPU_AARCH64. r=billm (d93a0b54da) - Bug 1250403 - Part 2. Import crbug #354405 for aarch64. r=billm (9dca949bcc) - Bug 1246501 - Add ppc specific atomic operations to ipc/chromium. r=Waldo (8054b612be) - Bug 1257305 - Avoid VS2015 about casting int to void*. r=dvander (6234acf6fc) - Bug 1207401 - Send B2G sandbox logging to both stderr and logcat. r=kang (ae404aa5ca) - Bug 1173320 - patch 6/8 - Make FileList clonable to workers if it doesn't contain Directories, r=smaug (ea6ba42f31) - Bug 1173320 - patch 7/8 - Tests for FileList and Directories, r=smaug (3f11503300) - Bug 1222522, part 1 - Make most dom/devicestorage/ tests work with e10s. r=dhylands (3cc7e339a5) - Bug 1173320 - patch 8/8 - Fix e10s tests for DeviceStorage API, r=smaug (949454bae7) - Bug 1222522, part 2 - Inline devicestorage_cleanup() in dom/devicestorage/ tests. r=dhylands (bcdee11385) - Bug 1258137 - OSFileSystem should not be kept alive by more than 1 Directory, r=smaug (225775f48d) - Bug 1255867. Remove some unnecessary AutoJSAPI uses. r=bholley (618cf018e8) - Bug 1237173 - Part2: Change type of duration to Maybe<StickyTimeDuration>. r=birtles (6b83473e05) - Bug 1238469 - Part 1: Refactor b2g emulator tests to remove the usage of custom mozharness configs; r=ahal (a128c8a8bb) - Bug 1238469 - Part 2: Refactor b2g mulet tests to remove the usage of custom mozharness configs; r=ahal (6c7ced3419) - Bug 1238469 - Part 3: Use b2g_emulator_unittest.py for b2g marionette tests; r=ahal (5fdb88b0e1) - Bug 1237173 - Part3: Throw TypeError if duration is NaN, negative value or not 'auto' string. r=birtles, r=smaug (d60b0318d2) - Bug 1136567 - Marionette test for selection carets' positions after changing orientation of device. r=Automatedtester (e7b25b1e4f) - Bug 1138839 - Part1 - Marionette test for selecting text inside an iframe. r=automatedtester (45db397a94) - Bug 1138839 - Part2 - Fix naming issue in marionette test for selection carets. r=automatedtester (c54850d9d3) - Bug 1198542: Update Marionette element IDs to be valid UUID. r=ato This allows WebDriver compatibility to create valid URI. (1b3de245de) - Bug 1204496: When searching by link text start from the startNode and not the rootNode; r=ato (0dfa3b8830) - Bug 1157725 - Rewrite test_mouse_action.py to be more robust. r=ato (40273abca2) - Bug 1141519: added test that puts marionette into a position that can cause hangs when in content scope; r=jgriffin (c99d8cf325) - Bug 1246407 - Rename parent directories for Marionette client and test harness; r=automatedtester (79d4e521fd) - Bug 1253989 Part 3 - Use @parameterized to rewrite selection mode tests. r=mtseng (baf189f1d5) - Bug 1253989 Part 4 - Rename AccessibleCaret test files. r=mtseng (d562edc8f4) - Bug 1251519 Part 3 - Add regression tests for caret dragging. r=mats (048dd5f103) - Bug 1253989 Part 5 - Remove touch caret and selection carets naming. r=mtseng (9929425b6d) - Bug 1253989 Part 6 - Refactor open_test_html(). r=mtseng (25a2424ca1) - Bug 1251519 Part 4 - Add tests for dragging caret to content boundary. r=mats (489b47269b) - Bug 1251519 Part 5 - Use union rect of child frames for clamping. r=mats (5520416749) - Bug 1216924 - Don't align to tiles (either real or virtual) if displayport suppression is enabled. r=BenWa (d470d188e4) - Bug 1254273 - Align the displayport to a max of 256 pixels even if the layer is larger. r=BenWa (0cf8cc0b6c) - Bug 1257938 part 3: Remove support for the "layout.css.sticky.enabled" pref (so we'll unconditionally support "position: sticky"). r=corey (fe12efd18f) - Bug 1257938 part 1: Adjust automated tests to assume position:sticky is unconditionally supported. r=corey (e749ac579e) - Bug 1257938 part 2: Remove separation between test_position_sticky.html & its helper-file, now that it doesn't need to tweak a pref. r=corey (631edab31a) - Bug 1257491 - Ensure that if the peek-messages code modifies the displayport, we schedule a repaint. r=BenWa (d6fb6ff96c) - Bug 1255006 - Ensure the displayport rect takes priority over a suppressed-margins displayport. r=kats (aa6cbc0250) - Bug 1259235 - Add IsScrollFrameWithSnapping to speed up event regions. r=mstange (2a744c311e) - Bug 1185140 - [css-grid][flexbox] Make grid/flex item blockification happen before creating table pseudos, per the latest specs. r=dholbert (dddb8b17ef) - Bug 1224424 - Replace mask-mode:auto keyword by mask-mode:match-source; r=dbaron (5a51b3b301) - Bug 1252039 - corrected MOZ_ASSERT expression in SeparatorRequiredBetweenTokens. r=dbaron (08790aa514) - Bug 1243734 - Part 1. Use MOZ_ENABLE_MASK_AS_SHORTHAND to define the type of mask property; r=dbaron (d8cd3a1c4a) - Bug 1243734 - Part 2. Set up gCSSProperties depends on mask-as-shorth and; r=dbaron (aa6b0259d8) - Bug 1243734 - Part 3. Set mask-mode reftest as failure before enable mask-as-shorthand; r=dbaron (6a326fbaf2) - Bug 1243734 - Part 5. Add MOZ_ENABLE_MASK_AS_SHORTHAND compile flag; r=ted r=dbaron (fcc1344ac8) - Bug 1142531: Check more bits in nsStyleContext::MoveTo assertion. r=heycam (8b62b139df) - Bug 1258147 - Pierce through display:contents style context ancestors when looking for CB context to compare our writing-mode to. r=jfkthame (956d8c25e5) - Bug 823483 patch 1 - Check for percentage max-width in addition to percentage width when deciding to ignore intrinsic min-width of replaced elements. r=dholbert (f88cb5f6a8) - Bug 823483 patch 3 - Limit effect of percentage width and max-width on intrinsic size to elements with replaced element sizing. r=dholbert (2573c3cfff) - Bug 823483 patch 4 - Make a percentage max-width override a fixed width for replaced element intrinsic size computation. r=dholbert (dda859f06c) - Bug 823483 patch 5 - Make (again) percentage width on text inputs make intrinsic minimum width be 0. r=dholbert (d46ada73ef) - Bug 1247929 patch 2 - Hard-code the Web-compatible set of form controls whose intrinsic minimum inline-size shrinks to 0 when inline-size (width) is specified as a percentage. r=dholbert (e4f0c80fcb) - Bug 1254968 - Add support for running JS builtins' constructors over Xray wrappers without unwrapping the newTarget. r=bholley,f=bz (56213ae395) - Bug 1249123 - Add telemetry for __defineGetter__/__defineSetter__ |this| values. data-review=bsmedberg r=till (52c5fd3488) - Bug 1232639 - Implement Object.{values,entries} in C++ to avoid native call overhead in tight loop. r=jorendorff (7262497283) - Bug 1254966 - Disambiguate JS Telemetry macro names. r=evilpie (781d0916c4) - Bug 1254384: Use generic shell switch syntax in js/src/jit-test tests. r=nbp (6f5975cc55) - Bug 1253016 - Remove legacy __defineGetter__/__defineSetter__ this behavior. r=till (cf1b7ad28c) - Bug 1253016 - Implement and test the new spec for legacy functions. r=till (1ff7762e3e) (cf2d7d1ae9) - import changes from `dev' branch of rmottola/Arctic-Fox: - Bug 1251999 - [css-grid] Update <fixed-size> parsing to the latest spec. r=dholbert (07f68007b7) - Bug 1151243 part 5 - [css-grid] Reftests for abs. pos. static-position. (f9a3b24508) - Bug 1242053 part 1 - [css-grid] Fix parsing / serialization of grid-template subgrid values. r=dholbert (39576c2f6d) - Bug 1242053 part 2 - [css-grid] Enable subgrid support for tests. r=dholbert (6da4aeb35a) - Bug 1240956 part 2 - [css-grid] Update tests due to the changed column/row value order for 'grid', 'grid-template' and 'grid-gap' properties. (16d2258d3a) - Bug 1253529 part 1 - [css-grid] Replace uses of the 'grid-template' shorthand with 'grid'. (f847bfa554) - Bug 1253529 part 2 - [css-grid] Remove the 'grid-template' shorthand. r=dholbert (d553c2f623) - Bug 594933 - Part 1: Let calc() supports number. r=dbaron (e4bc39b5f0) - Bug 594933 - Part 2: Add support for calc() to line-height. r=dbaron (901227bacb) - Bug 1253189 part 5 - Import reftests of css-values. r=dbaron (4599431827) - Bug 1253189 part 4 - Add skip.list for skipping imported tests. r=dbaron (014f7ca7de) - Bug 1253189 part 1 - Make import-tests.py compatible with Windows. r=dbaron (a22c3e4f7f) - Bug 1253189 part 2 - Update import-tests.py script to work on the current repo. r=dbaron (7535b38b71) - Bug 1253189 part 3 - Update existing received w3c reftests. r=dbaron (0fa2d6e2de) - Bug 1253189 followup - Update skip.list to match the directory name on CLOSED TREE (019b55c3c9) - Bug 968761 - Treat nested calc() as plain parenthesis. r=dbaron (537506f4e5) - Bug 1248371 - [css-grid] Require that each track has a definite min- or max-sizing function when the track list contains a repeat(auto-fill/fit) track. r=dholbert (330dd37427) - Bug 1244638 - Part 1:implement AnimationEffectTiming iterationStart. r=birtles, r=smaug (d0217068ac) - Bug 1244638 - Part 2: Throw TypeError if iterationStart is NaN, negative value or Infinity. r=birtles, r=smaug (f631e261a0) - Bug 1238845 - Implement UUID helper - dom/bluetooth & dom/webidl & layout/build change. r=jocelyn, r=bz (3ddfa8cccf) - Bug 1252790 - Remove RuleHashTableOps. r=dbaron. (b52d9e2613) - Bug 1252375 - Fix up jemalloc stats reporting. r=erahm. (dbecb54598) - Bug 1249503 - Make WindowsAddressSpaceReporter bloat memory reports less. r=erahm. (3bfb6932cb) - Bug 1253085 - Remove the |PLDHashTable*| argument from PLDHash{HashKey,MatchEntry}. r=froydnj. (1331fd9ea0) - Bug 1251127 - Gracefully handle multiple calls to nsMemoryReporterManager::Init(). r=erahm. (c51f57907e) - Bug 1234540 - verify the validity of hashEntry, if it's null return with NS_ERROR_FAILURE. r=michal (f44bd269db) - Bug 1112499 - Set up shutdown pipe before new thread starts. r=keeler (73b9a56196) - Bug 1245059 - Disable NotifyIpInterfaceChange use for now. r=mcmanus (ab11fd8507) - Bug 1251873 - Store the trimmed referrer URL on HTTP channel if a trimming referrer policy is in effect; r=mcmanus (3f43d5b351) - more bits of bug 366559 - patch 7, content-encoding brotli for https (f127a97450) - Bug 1250115 - initialized pollInterval with 0 in order to prevent garbage value if Poll(..) doesn't get called. r=dragana (af55e06789) - Bug 1251493 - Remove remaining references to MOZILLA_XPCOMRT_API from netwerk. r=mcmanus (43d711d2d6) - Bug 1242452 - only if PR_GetIdentitiesLayer return valid pointer continue and pass it's result to PR_GetIdentitiesLayer. r=mcmanus (61a2785337) - Bug 1251595 - Check if mNetAddr is set before sending ipv4/6 telemetry. r=mcmanus (9d081bc0b9) - Bug 1252755: increase maximum UDP packet size to 9216 bytes for jumbo frames. r=jesup (3d629473ea) - Bug 1194259: warnings-as-errors bustage fix rs=bustagn a CLOSED TREE (5b8288ff6d) - Bug 1227781 - Fix crash with bogus STUN parameters. r=bwc (7d132a37ff) - Bug 1231196: Fix init of PeerConnectionImpl::mThread for unit-tests and similar. r+drno (60f11ed191) - Bug 1230184 - plumb setParameters down to JsepTrack. r=bwc, r=mrbkap (fdeaafb737) - Bug 1231507 - Part 1: selectSsrc chrome-only API for SSRC-based filtering of receive tracks. r=drno, r=smaug (c24ce1a76e) - Bug 1221837 - Accept hard coded codec numbers without rtpmaps. r=bwc (89b81c861c) - Bug 1231507 - Part 2: added mochitest SimulCast offer test case r=jib (05d838960f) - Bug 1230184 - setParameters webidl. r=smaug (6319cdfca7) - Bug 1230184 - add input parameter validation to setParameters. r=bwc (c0740c142a) - Bug 1230184 - add media.peerconnection.simulcast pref. r=bwc (99b1a4978d) - Bug 1247619 - add console warning about OAuth for STUN not yet supported. r=jesup,smaug (801eaa66e1) - Bug 1241153: Stop blocking addTrack on GMP init, and update codecs on existing tracks when GMP init finishes. r=jesup (3473dfe0ce) - Bug 1251737 - Remove remaining references to MOZILLA_XPCOMRT_API from media. r=jesup (7b32d9d191) - Bug 1218326: Prevent datachannel operations on closed PeerConnections. r=jesup a=lizzard (5d20d7dd7f) - Bug 1211091 - use upper boundary for streams per data channel. r=bwc (7f9462c434) - Bug 1188391 - separate immediate ICE failures from failures after checking. r=bwc, r=vladan (9095c58656) - Bug 1227708 - Differentiate ICE_SUCCESS_RATE telemetry for loop vs webrtc r=jesup (399406c872) - Bug 1232082 - fix removal of remote tracks to update receivers. r=jesup (81998ed355) - Bug 1244913 - Add test_peerConnection_scaleResolution.html r=bwc,jesup (8ac2d8a363) - Bug 1249860 - Add simulcast test for resolution scaling. r=bwc (c7753bf02b) - Bug 1247622 - Make RTCRtpSender.setParameters return a promise. r=jesup,smaug (4c2504adc8) (86eaa55e65) * Notice: the changelog above may not always applicable to XULRunner code which K-Meleon uses. A goanna3 source tree that has kmeleon adaption patch applied is available here: https://github.com/roytam1/palemoon27/tree/kmeleon761 point
-
Thanks for the replies. I guess I have a slightly newer version. It seems to be working OK. I'm more up on Windows XP than Windows 7 ... so it's all good.1 point
-
Update notification! As already reported , the Root Certificates have been updated and are now from 27-02-2024. Here are screenshots of both updaters: Therefore, my self-created, offline Root Certificate Updaters in the section 11.2.4. Downloads related to Root Certificate Updates (in the first post of this thread) will also be updated as soon as possible. Cheers, AstroSkipper1 point
-
What happens if you sign the driver with my solution? System level signing is, like explained in this topic... Install the driver. Sign before reboot! "permanently bypass driver signature verification" https://msfn.org/board/topic/185975-got-vista-to-run-on-nvme-with-one-of-george-kings-drivers-but-its-unsigned-any-way-to-permanently-bypass-driver-signature-verification-at-boot/1 point
-
@Damnation Break instruction exception - code 80000003 (first chance) nt!KiDispatchInterrupt+0x38d: 804dcbdf f390 pause 1: kd> g Break instruction exception - code 80000003 (first chance) ******************************************************************************* * * * You are seeing this message because you pressed either * * CTRL+C (if you run console kernel debugger) or, * * CTRL+BREAK (if you run GUI kernel debugger), * * on your debugger machine's keyboard. * * * * THIS IS NOT A BUG OR A SYSTEM CRASH * * * * If you did not intend to break into the debugger, press the "g" key, then * * press the "Enter" key now. This message might immediately reappear. If it * * does, press "g" and "Enter" again. * * * ******************************************************************************* nt!DbgBreakPointWithStatus+0x4: 804e2a42 cc int 3 0: kd> g *** Fatal System Error: 0x0000007e (0xC0000005,0x00000000,0xF789E168,0xF789DE64) Break instruction exception - code 80000003 (first chance) A fatal system error has occurred. Debugger entered on first try; Bugcheck callbacks have not been invoked. A fatal system error has occurred. Connected to Windows XP 2600 x86 compatible target at (Thu Feb 29 19:05:36.031 2024 (UTC + 1:00)), ptr64 FALSE Loading Kernel Symbols .............................. Loading User Symbols ******************************************************************************* * * * Bugcheck Analysis * * * ******************************************************************************* Use !analyze -v to get detailed debugging information. BugCheck 7E, {c0000005, 0, f789e168, f789de64} Probably caused by : NDIS.sys ( NDIS!ndisMQueryNetworkAddress+23 ) Followup: MachineOwner --------- nt!RtlpBreakWithStatusInstruction: 804e2a42 cc int 3 11: kd> !analyze -v ******************************************************************************* * * * Bugcheck Analysis * * * ******************************************************************************* SYSTEM_THREAD_EXCEPTION_NOT_HANDLED (7e) This is a very common bugcheck. Usually the exception address pinpoints the driver/function that caused the problem. Always note this address as well as the link date of the driver/image that contains this address. Arguments: Arg1: c0000005, The exception code that was not handled Arg2: 00000000, The address that the exception occurred at Arg3: f789e168, Exception Record Address Arg4: f789de64, Context Record Address Debugging Details: ------------------ EXCEPTION_CODE: (NTSTATUS) 0xc0000005 - Die Anweisung "0x%08lx" verweist auf Speicher bei "0x%08lx". Die Daten wurden wegen eines E/A-Fehlers in "0x%081x" nicht in den Arbeitsspeicher bertragen. FAULTING_IP: +1f451c801f451e8 00000000 ?? ??? EXCEPTION_RECORD: f789e168 -- (.exr 0xfffffffff789e168) ExceptionAddress: 00000000 ExceptionCode: c0000005 (Access violation) ExceptionFlags: 00000000 NumberParameters: 2 Parameter[0]: 00000000 Parameter[1]: 00000000 Attempt to read from address 00000000 CONTEXT: f789de64 -- (.cxr 0xfffffffff789de64;r) eax=00000000 ebx=80702790 ecx=54445358 edx=00000001 esi=f7472b20 edi=807026c0 eip=00000000 esp=f789e230 ebp=f789e250 iopl=0 nv up ei pl zr na pe nc cs=0008 ss=0010 ds=0023 es=0023 fs=0030 gs=0000 efl=00010246 00000000 ?? ??? Last set context: eax=00000000 ebx=80702790 ecx=54445358 edx=00000001 esi=f7472b20 edi=807026c0 eip=00000000 esp=f789e230 ebp=f789e250 iopl=0 nv up ei pl zr na pe nc cs=0008 ss=0010 ds=0023 es=0023 fs=0030 gs=0000 efl=00010246 00000000 ?? ??? Resetting default scope DEFAULT_BUCKET_ID: DRIVER_FAULT PROCESS_NAME: System ERROR_CODE: (NTSTATUS) 0xc0000005 - Die Anweisung "0x%08lx" verweist auf Speicher bei "0x%08lx". Die Daten wurden wegen eines E/A-Fehlers in "0x%081x" nicht in den Arbeitsspeicher bertragen. EXCEPTION_PARAMETER1: 00000000 EXCEPTION_PARAMETER2: 00000000 READ_ADDRESS: 00000000 FOLLOWUP_IP: NDIS!ndisMQueryNetworkAddress+23 bac63a56 e6ff out 0FFh,al FAILED_INSTRUCTION_ADDRESS: +23 00000000 ?? ??? BUGCHECK_STR: 0x7E ANALYSIS_VERSION: 6.3.9600.17237 (debuggers(dbg).140716-0327) x86fre LAST_CONTROL_TRANSFER: from 00000000 to 00000000 SYMBOL_ON_RAW_STACK: 1 STACK_ADDR_RAW_STACK_SYMBOL: fffffffff789d9e0 STACK_COMMAND: dps fffffffff789d9e0-0x20 ; kb STACK_TEXT: f789d9c0 6c674a6f f789d9c4 6e666e67 f789d9c8 ee776a67 f789d9cc 6a676a67 f789d9d0 7e647a66 f789d9d4 7b667866 f789d9d8 38063a0e f789d9dc bac63a56 NDIS!ndisMQueryNetworkAddress+0x23 f789d9e0 3a063a06 f789d9e4 3a063206 f789d9e8 91ea67db f789d9ec c37cf2f2 f789d9f0 f1ea779b f789d9f4 e3ff5070 f789d9f8 b1eb67d3 f789d9fc e3fed2f2 f789da00 00008070 f789da04 00000000 f789da08 8071e0fe hal!HalpGetFeatureBits+0x52 [e:\xpsp1\nt\base\hals\halmps\i386\mphal.c @ 1097] f789da0c 00000001 f789da10 f78feb3c f789da14 f78feb38 f789da18 f78feb38 f789da1c 00008070 f789da20 00000000 f789da24 00000000 f789da28 756e6547 f789da2c 49656e69 f789da30 6c65746e f789da34 00d1e300 f789da38 00000000 f789da3c 00000000 SYMBOL_NAME: NDIS!ndisMQueryNetworkAddress+23 FOLLOWUP_NAME: MachineOwner MODULE_NAME: NDIS IMAGE_NAME: NDIS.sys DEBUG_FLR_IMAGE_TIMESTAMP: 48025d03 IMAGE_VERSION: 5.1.2600.5512 FAILURE_BUCKET_ID: 0x7E_NULL_IP_NDIS!ndisMQueryNetworkAddress+23 BUCKET_ID: 0x7E_NULL_IP_NDIS!ndisMQueryNetworkAddress+23 ANALYSIS_SOURCE: KM FAILURE_ID_HASH_STRING: km:0x7e_null_ip_ndis!ndismquerynetworkaddress+23 FAILURE_ID_HASH: {6cac7e57-f19c-4081-7e29-9f6a6f30cf6b} Followup: MachineOwner ---------1 point
-
1 point
-
And here is the shortest way to update the installation of uBlock Origin Legacy properly: Backup all your settings using the "Back up to file" button on the page "Settings". Uninstall uBlock Origin Legacy and delete the ublock0.sqlite file in your profile subfolder extension-data. Restart the browser and install the new version of uBlock Origin Legacy. Restore all settings from your backup file. Greetings, AstroSkipper1 point
-
@Damnation A first run shows only the same error as you have, that someone tries to write in forbidden memory Dietmar *** Fatal System Error: 0x0000007e (0xC0000005,0x00000000,0xF789E168,0xF789DE64) Break instruction exception - code 80000003 (first chance) A fatal system error has occurred. Debugger entered on first try; Bugcheck callbacks have not been invoked. A fatal system error has occurred. Connected to Windows XP 2600 x86 compatible target at (Wed Feb 28 18:25:27.820 2024 (UTC + 1:00)), ptr64 FALSE Loading Kernel Symbols .............................. Loading User Symbols ******************************************************************************* * * * Bugcheck Analysis * * * ******************************************************************************* Use !analyze -v to get detailed debugging information. BugCheck 7E, {c0000005, 0, f789e168, f789de64} Probably caused by : Unknown_Image ( ANALYSIS_INCONCLUSIVE ) Followup: MachineOwner --------- nt!RtlpBreakWithStatusInstruction: 804e2a42 cc int 3 11: kd> !analyze -v ******************************************************************************* * * * Bugcheck Analysis * * * ******************************************************************************* SYSTEM_THREAD_EXCEPTION_NOT_HANDLED (7e) This is a very common bugcheck. Usually the exception address pinpoints the driver/function that caused the problem. Always note this address as well as the link date of the driver/image that contains this address. Arguments: Arg1: c0000005, The exception code that was not handled Arg2: 00000000, The address that the exception occurred at Arg3: f789e168, Exception Record Address Arg4: f789de64, Context Record Address Debugging Details: ------------------ EXCEPTION_CODE: (NTSTATUS) 0xc0000005 - Die Anweisung "0x%08lx" verweist auf Speicher bei "0x%08lx". Die Daten wurden wegen eines E/A-Fehlers in "0x%081x" nicht in den Arbeitsspeicher bertragen. FAULTING_IP: +150b5800150b78 00000000 ?? ??? EXCEPTION_RECORD: f789e168 -- (.exr 0xfffffffff789e168) ExceptionAddress: 00000000 ExceptionCode: c0000005 (Access violation) ExceptionFlags: 00000000 NumberParameters: 2 Parameter[0]: 00000000 Parameter[1]: 00000000 Attempt to read from address 00000000 CONTEXT: f789de64 -- (.cxr 0xfffffffff789de64;r) eax=00000000 ebx=80702790 ecx=54445358 edx=00000001 esi=f7472b20 edi=807026c0 eip=00000000 esp=f789e230 ebp=f789e250 iopl=0 nv up ei pl zr na pe nc cs=0008 ss=0010 ds=0023 es=0023 fs=0030 gs=0000 efl=00010246 00000000 ?? ??? Last set context: eax=00000000 ebx=80702790 ecx=54445358 edx=00000001 esi=f7472b20 edi=807026c0 eip=00000000 esp=f789e230 ebp=f789e250 iopl=0 nv up ei pl zr na pe nc cs=0008 ss=0010 ds=0023 es=0023 fs=0030 gs=0000 efl=00010246 00000000 ?? ??? Resetting default scope DEFAULT_BUCKET_ID: DRIVER_FAULT PROCESS_NAME: System ERROR_CODE: (NTSTATUS) 0xc0000005 - Die Anweisung "0x%08lx" verweist auf Speicher bei "0x%08lx". Die Daten wurden wegen eines E/A-Fehlers in "0x%081x" nicht in den Arbeitsspeicher bertragen. EXCEPTION_PARAMETER1: 00000000 EXCEPTION_PARAMETER2: 00000000 READ_ADDRESS: 00000000 FOLLOWUP_IP: +150b5800150b78 00000000 ?? ??? FAILED_INSTRUCTION_ADDRESS: +150b5800150b78 00000000 ?? ??? BUGCHECK_STR: 0x7E ANALYSIS_VERSION: 6.3.9600.17237 (debuggers(dbg).140716-0327) x86fre LAST_CONTROL_TRANSFER: from 00000000 to 00000000 STACK_TEXT: f789e22c 00000000 00000000 00000000 f74774fc 0x0 STACK_COMMAND: kb SYMBOL_NAME: ANALYSIS_INCONCLUSIVE FOLLOWUP_NAME: MachineOwner MODULE_NAME: Unknown_Module IMAGE_NAME: Unknown_Image DEBUG_FLR_IMAGE_TIMESTAMP: 0 IMAGE_VERSION: FAILURE_BUCKET_ID: 0x7E_NULL_IP_ANALYSIS_INCONCLUSIVE BUCKET_ID: 0x7E_NULL_IP_ANALYSIS_INCONCLUSIVE ANALYSIS_SOURCE: KM FAILURE_ID_HASH_STRING: km:0x7e_null_ip_analysis_inconclusive FAILURE_ID_HASH: {dfedf0b5-2624-ece8-95fa-645295e3260a} Followup: MachineOwner ---------1 point
-
Enter the BIOS, Switch off "Attempt to fix sporadic PCI errors" , or whatever they call it in your BIOS. It helped me when my sound card was conflicting with my LAN card. It too hanged up on the BIOS title screen.1 point
-
It works with Vista x64, x86, I checked myself. Though, it can't boot from it. I have a classic BIOS from 2009 (without films and games in it).1 point
-
Here's a fully working ASM1061 PCI-E Cards to SATA 3.0 with two internal ports, works with Vista without any additional drivers. https://www.ebay.co.uk/itm/355467151767 https://www.ebay.co.uk/itm/126046738088 Manufacturer claims full support. https://www.asmedia.com.tw/product/77BYq58SX3HyepH7/58dYQ8bxZ4UR9wG51 point
-
I am not doing this, I considered doing it to prevent buggy code being pushed to roytam1's users, but I never decided to actually go forward with it. What's sad is that roytam1 continues to release code to his users that has not been verified as production ready. Code in the master branch of upstream UXP or upstream Basilisk is not always production ready. I have seen issues reported on MSFN for roytam1's builds because he was pulling code from master branches before they were ready. He is doing a disservice to his users by giving them potentially buggy code.1 point
-
This is not the reference edition I was talking about. Reference is slim, but long. https://www.tweaktown.com/reviews/7170/nvidia-geforce-gtx-980-ti-reference-video-card-review/index.html1 point
-
True, Supermium has already been discussed elsewhere at MSFN; but still I welcome @westpoint‘s first-ever post here (although his account was created two years ago). This forum certainly needs some new members. Supermium 119 actually supported Vista before any Windows XP support was added, so the Vista forum was a logical place for a post.1 point
-
For me, ESET never was, not only it marked legit copy protection game files as "viruses", it also deleted important files on my XP pc and put them to "quarantine" forever, I was not surprised to see it still does! To be fair, I gave it a chance in the past. I remember, I even lost my online registration for the DVD check of Sacred 2 (based on securom). As for your OT question, I fail to understand, why would you be interested, if you discarded ESET anyway? I could only guess, but If you want to be recruited or renew some previous pre-1991 arrangements, I'm sure there's no need to go to Bratislava, and I'm definitely not the one to talk to! NOD32 "Such file could contain valuable information, and losing it is certainly not what you’d wish for" https://hetmanrecovery.com/recovery_news/how-to-return-files-if-eset-nod-deleted-or-placed-them-in-quarantine.htm1 point
-
Of course, Avast Premier's self-protection was deactivated before I started the uninstall routine. Everyone who wants to completely remove an AV programme that has such a self-protection function should know this. But that did not help at all. It was the same with Eset NOD32 Antivirus in the past. The uninstall routine of Avast 18.8 was inadequately programmed and therefore rubbish. And AvastClear 18.8 is not much better. The way I described in the article "Why I switched from Avast! to WiseVector StopX" I quoted above, on the other hand, worked excellently, but is not readily accessible and recommended for an inexperienced user. PS: The reader should not be confused by the title of my article. In the meanwhile, WiseVector StopX has been abandoned by the manufacturer and is therefore history.1 point
-
No, Vistapocalypse warned us about the dangers coming from the KGB(FSB) or whatever they call Russian spies these days, and I'm grateful for that warning! It makes me wonder, why do you even assume, a fellow American, such as him, would be afraid of the NSA, right @Vistapocalypse, you aren't afraid of the NSA or their alleged "backdoor" in Avast or anywhere else?1 point
-
it's made in china just like the last working and stable web browsers for XP. google, intel, nvidia, M$... and many others who don't support XP anymore are not chinese companies AFAIK Read this quotation from my introductory post containing the conditions for posting here in this thread: No more off-topic posts in my thread! This is my last warning. AstroSkipper1 point
-
@Dixel! Hello and welcome to my thread! Glad to hear you like my thread! I have been using Panda Free Antivirus for several months. I am generally amazed at how little resources it uses and how it protects my Windows XP computer completely satisfactorily. I hope you will find what you are looking for here. My list of all presented security programmes in the second post of this thread is just under construction, but will be maintained by me and constantly expanded, if my real life allows it and I have not to waste my time commenting on programmes that have long since been sufficiently discussed and put ad acta. Greetings from Germany to The Netherlands, AstroSkipper1 point
-
Hello, jasonjulius1122! Welcome to MSFN! MSFN is rather exclusive, it's the place for the strong! If you're strong, you'll enjoy it.1 point
-
AstroSkipper, greetings! It's so great to see you're still here and provide us with top-notch software only! I'm actually amazed and intrigued at the same time! They still have such a nice all-in-one security European software package for XP, and I didn't know about it! What would I do without you! I'll intsall it on my mother's laptop as soon as I visit her. The name Panda was confusing though)))) I thought it was Chinese, now I see it's European, and I'll not hesitate to use it!1 point
-
The Giant Matrix home page disappeared in 2015. Their last version seems to be 9.0.1 from 2013. I assume that Anti Tracks' VPN feature doesn't work anymore in these days. For me, no problem, I use paid VPN services. In any case, I will check this programme more deeply when I have more time. First, I will add it to my internal list.1 point
-
Already happened in November of 2022, Google had pulled the plug. https://msfn.org/board/topic/184046-future-of-chrome-on-windows-71 point
-
Thanks ! Is it any faster than the 471 ? They said it has no gaming improvements, only "security".1 point
-
Well, 2021 games don't work, like I wrote just now. RDR2 is 2019. I'm pretty sure you got the wrong impression, It would be easier if they worked on win 7 ! I don't even have win 8/10 and not going to. The "fact" is debatable, to say the least. We shall see how folks will try to survive without chrome, audacity, MKVtoolnix, etc. My 26 y.o. girlfriend says Windows 7 is a system for pensioners, lol. I wonder what the next younger one would say !1 point
-
Why would I read an article from early 2017 for such obsolete hardware ? We shall have 2023 in a couple of weeks. I don't know people who would voluntarily purchase a 6 years old laptop just to be able (possibly, without any hard proof) use Win 7. From what I know, that trick worked only for some early Kaby-lake models.1 point