Leaderboard
Popular Content
Showing content with the highest reputation on 08/01/2023 in Posts
-
Oh, it's fine, like I said, I can live without seeing the attachments, thank you, I know how to change the IP, I even tried with a very famous VPN (that everyone knows, they usually unblock everything), I tried right now, all the same.2 points
-
... Right; so it's something along the lines of: Apologies for misinterpreting your post, but, in my defense, it was "just an image" post; the imgur links continue to display properly for me here, thus my IP has not abused their servers ; if you're impatient, you could restart your modem/router to get a new IP address from your ISP (if possible), or use some other means to evade imgur's block (assuming it's IP-based); also, several privacy-enhancing extensions/settings are known to not go down well with third party services like image-hosters ... I always upload to imgur as an unregistered/anonymous user, I have no account with them; if a "view limit" is being imposed, then it's solely on their side ...2 points
-
@Monroe! Thanks again for reporting that Malwarebytes v1.75.0.1300 is able to receive most recent definition updates in 2023! That are really great and good news. Although updating of definitions failed initially when instalIing this version, I found yet a way to get the update function of this version working again under Windows XP. It was a bit tricky but it works now such as you reported. I will write an article about that very soon. Thanks again! You are simply great.2 points
-
How to install Office 2021 on Windows 8.1: 1. You must have installed Windows 8.1 (it can be both 32-bit and 64-bit), this workaround won't work on Windows 8.0 and earlier as of now 2. Have an extracted C2R copy of Office 2021 32-bit/64-bit (it must be Professional Plus and/or Visio Pro and/or Project Pro) handy 3. Install OfficeC2RExtender 4. Copy wotok_mdl.cmd to the root of Office 2021 C2R folder 5. Run wotok_mdl.cmd (no need to run as admin as it will ask for admin privileges itself) 6. Select option 3 7. Select default option 8. Select option 64 (if you have 64-bit copy) or 32 (if you have 32-bit copy) 9. Select option 2 (if present, if not, select option 1) 10. Select default option 11. Type "ProPlus2021Retail" (if you installing Professional Plus) or "VisioPro2021Retail" (if you installing Visio Pro) or "ProjectPro2021Retail" (if you installing Project Pro) P.S. The Volume variants are untested, so, I strongly recommend you to choose Retail ones 12. Select default option 13. Press "1" 14. Wait till it will be installed 15. And you should get this: 16. If you got this, then voila, you will get fully working Office 2021 (except for automatic updates, but that's not critical) Office_C2R_Extender_W81.zip wotok_mdl.cmd1 point
-
In the last few weeks there has been a lot of concerns about Google's new Web Environment Integrity proposal and its possible effects on web freedom. One particular concern that I don't feel can be addressed is the fact that old versions of Windows (and other unsupported operating systems) are likely to not be certified meaning only "supported" systems will be able to access large amounts of the internet if the proposal is successful. Expect large amounts of sites to use it, including banking websites, paywalled news sites, DRM'd video sites and social networks that could potentially be blocked from being accessed. Since remote attestation will be used and possibly be enforced by TPMs and signed drivers it might be impossible to get say Windows 7 to be certified for a WEI protected site. If you want to be able to continue to browse the web on older operating systems please oppose the proposal for WEI.1 point
-
... and: ... Today was less hot here , thus I had a second chance to research this more diligently ... According to MDN: https://developer.mozilla.org/en-US/docs/Web/CSS/:where#browser_compatibility the ":where()" pseudo-selector was first implemented in Mozilla Firefox 78 and Chrome 88; but, as most of us know, Kafan MiniBrowser was based on Chromium 87 ; some investigation revealed that my own copy of it is able to display properly the MediaMarkt laptop/notebook entries because, in tweaking my MiniBrowser copy, I had enabled below flag: chrome://flags/#enable-experimental-web-platform-features Turns out that flag activates (among other things) CSS features that have been officially introduced in Chromium 88+; indeed, with that flag disabled (the default setting): but with it enabled (i.e. how I have it myself): Sorry for any eventual misunderstanding ...1 point
-
New Google Chrome browser security plan slammed by experts1 point
-
Cross-posting this here: https://msfn.org/board/topic/184944-could-web-enviornment-integrity-block-old-operating-systems/1 point
-
When I create a new post containing own images, I always upload them to an image hoster before. I think a post should also be able to be understood by readers in the future. Especially, if one, as for example me, has created articles with information which should be preserved for as long as possible. And I personally am not too lazy to insert the golden rule:1 point
-
Because those browsers and the OS they were developed for, they all matched perfectly. Modern Chrome was never meant to run on XP and shitload of compromises are made for them to run on it. That's what all these backports really are, a bunch of compromises, inefficiencies and half-baked or non-working features.1 point
-
It was @VistaLover, it's not the first time I see his attachments show up like this, No offence, I don't read his posts, mostly because we don't share the same interests, it's just an observation. This time I decided to look at them.1 point
-
They show like that for me, if I go there directly, they say you got a view limit on them. "The HTTP 429 Too Many Requests response status code indicates the user has sent too many requests in a given amount of time ("rate limiting")."1 point
-
1 point
-
1 point
-
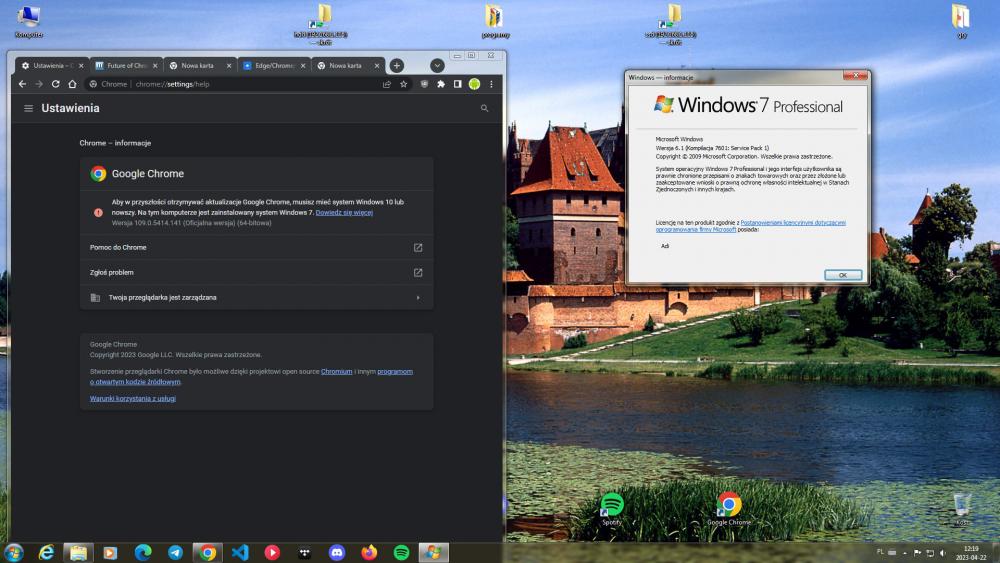
... Please read my previous post here and try the same "laptop" entries in: https://www.mediamarkt.de/de/category/notebooks-362.html I've tried myself ca. an hour ago and the same issue (image overlap on text) manifests itself in the Ch86-based forks : ; additionally, if you had paid closer attention to the screengrab UCyborg posted here, you'd have spotted the still missing images of the notebooks themselves: Since those laptop entries display OK in [Chr]Edge 94, the CSS/JS feature "mediamarkt.de" rely on was implemented between Chromium 87-94 ... But, guess what? Kafan MiniBrowser seems to display correctly those laptop photos (I have enabled dark mode there): ... so, by pure chance, we now have an answer to your previous question in another subforum : So, it's a feature first implemented in Chromium 87 (actually, in Chromium 88; kindly read this followup ...)1 point
-
Semiconductor Lab Facility of Indian Space Research Organization to make ASIC & microprocessor uses Windows XP https://youtu.be/azGFzi1UrKY?t=1005 If XP is good enough for sending Asia's first satellite to Mars , so why give it up?1 point
-
As requested, the link to the Installer of Malwarebytes Anti-Malware 1.75.0.1300 has been changed by me although it was the official link from Malwarebytes itself. Now, all readers who want to download this installation programme must click on this link themselves. Of course, I already wrote about that in this thread.1 point
-
Since July 10 (made public since July 11) I have managed to run Windows XP x64 SP2 (built using XP2ESD) from UEFI Class 3 on Coffee Lake Windows 11 laptop on winload.efi 16497 using FlashBoot 3.3n bootmgfw.efi and Windows 7 generic VGA drivers by modifying the contents of mounted devices and enum key. I have used the XP2ESD build which contains the backported generic drivers and ACPI 2.0 drivers (from here) to get this to work. So far I tested acpibit64crack.sys from Dietmar. The fact that I managed to boot XP on such new hardware means that the ACPI 2.0 worked! Touchpad doesn't work because there aren't any working XP drivers for Intel Serial IO I2C Host Controller (9DE8 and 9DE9 in my case) to get the Elan1200 I2C Hid device to install using the backported generic touchpad driver from windows 8. USB XHCI controller and USB 3.0 root hub work without problems so I can use external mouse (for the cursor) and USB wireless adapter (for internet). I don't know if it's caused by ACPI incompatibility but I have tried to backport the Intel Serial IO I2C Host Controller from Windows 7 and it still wouldn't work even with Mov's ntoskrnl emu extender files! I have provided the device manager entries of my XP installation (from the enum key) so you can see the information on the drivers installed in my working XP OS.Useful's-XP-device-manager-entries.txt1 point
-
@Monroe! Thanks again for reporting that Malwarebytes v1.75.0.1300 is able to receive most recent definition updates in 2023! That are really great and good news. Although updating of definitions failed initially when instalIing this version, I found yet a way to get the update function of this version working again under Windows XP. It was a bit tricky but it works now such as you reported. I will write an article about that very soon. Thanks again! You are simply great. And here is the proof in form of screenshots: Cheers, AstroSkipper1 point
-
Thank you very much for uploading screenshots! As far as I understood you correctly, you didn't change any settings, and you didn't modify anything. Right? Another question: Do you have one of the last offline definition updaters for this version? Mine is from 2019. In any case, it seems I have to test it once again all from scratch.1 point
-
Thanks for posting such a typical case! That's a very good example what I meant in terms of security programmes. Finding strange processes is the best everyone can do first. You can't seriously hand over all security tasks blindly to an anti-malware programme or whatever. You have to take a look at what's going on inside a computer yourself.1 point
-
Yep! We all have our tactics. But Process Hacker is not a normal Task Manager. It provides additional security features I already described sufficiently. And here is your System Information window taken from my installation of the version 2.39: Hitting Ctrl-I and bam, there it is. One additional click on CPU or I/O, you see all further information. Of course, it is not three-in-one but the version 2.39 is much more recent. Always important in terms of fixing old bugs. But as I already said, to each their own!1 point
-
Observing the background processes, noticing new and possibly malicious threats and getting systray notifications when new drivers or services are installed, all that can be done by Process Hacker. Here is a quotation from Process Hacker's homepage: And here is my assessment: That's what I call a security programme at its best. If you don't know what's going on in your system, you don't need to worry about security and possible measures. Then you will just have to blindly trust other programmes and leave the security of your system to them. I personally would never do that. But, to each their own!1 point
-
Do you refer to the systray icon(s) or the main programme view when talking about a three-in-one view? In my main programme view, I see all of this information about processes, RAM, and CPU. And I have configured Process Hacker to see two separate icons in my systray, one for used RAM and one for the CPU history.1 point
-
I presented Process Hacker with a lot of additional information here in my thread. Additionally, I have given my experience and assessment about this programme. Now, I would like to hear from Windows XP users about their experiences and opinions in terms of this programme. So if you should use Process Hacker under Windows XP, feel free to let us know what you think about it! Greetings, AstroSkipper1 point
-
I am still using the official last XP-compatible version Sandboxie 5.22. I checked Sandboxie's compatibility in terms of Windows XP, too. Indeed, the developer David Xanatos compiled a special, last XP-compatible version Sandboxie 5.40 after it had become open source. This version does not need a licence anymore. Here is a download link: https://github.com/sandboxie-plus/Sandboxie/releases/download/v5.40/SandboxieInstall32_xp.exe However, I do have a licence, therefore, I am not really interested in.1 point
-
I do every task such as testing software, downloading files, or surfing the web in my real Windows XP machine. I never had a serious infection. The reason I created this thread was indeed to present, collect and preserve all possible security programmes which are still available for Windows XP to secure such a real machine and protect it against malicious threats.1 point
-
Of course! Sandboxie belongs to the topic of this thread and is already on my internal list. It was installed in all my Windows XP partitions from the very first. I use the last XP-compatible version 5.22 and I love it. I use it regularly for testing tools I do not trust at first sight. In the past, the best news about Sandboxie was that it no longer required a licence and was declared open source in 2020. https://web.archive.org/web/20200425220152/https://community.sophos.com/products/sandboxie/f/forum/119641/important-sandboxie-open-source-code-is-available-for-download1 point
-
Browser should prevent screensaver/sleep naturally when playing videos, seems that part is simply broken in 360Chrome. In JavaScript, WakeLock may be requested to block screensaver/sleep for other use cases. You can try this test: https://reillyeon.github.io/scraps/wakelock.html But it won't work if the browser is broken.1 point
-
https://chromereleases.googleblog.com/2023/04/stable-channel-desktop-update.html new version for 2012r2, probably works on 7 as previous one, will try install and report EDIT: works fine, links here: x64: https://dl.google.com/release2/chrome/okwuqsvyf2bgppzm2557sokhb4_109.0.5414.141/109.0.5414.141_chrome_installer.exe x86: https://dl.google.com/release2/chrome/accqbpi5rq2su3yx4qzgu2zdrl4q_109.0.5414.141/109.0.5414.141_chrome_installer.exe1 point
-
Why ProxHTTPSProxy 1.5 doesn't work in IE6 but works in IE8?1 point
-
Hello @RainyShadow! Thanks for your hint! Frankly, I'd know exactly what I would have to do to port my program package ProxHTTPSProxy's PopMenu TLS 1.3 3V3 to Windows 7. For checking or changing the system's proxy status, this OS has also corresponding, native commands which probably could be easily implemented in my program modules. But at the moment, it's not an issue for me.1 point
-
Certificates - CA and Root Certificates Although Windows XP was abandoned and updates of root certificates were not provided anymore by Microsoft for this OS, we still found ways to update them. And, if we want to install one of our TLS proxies, we have to install a CA certificate to get them working. In both cases, certificates are needed, and this short article is intended to shed some light on this certificate jungle with regards to our TLS proxies. The CA certficate of ProxHTTPSProxy A certificate authority (CA) is a trusted entity that issues digital certificates. These are files that cryptographically link an entity to a public key. Certificate authorities are an important part of the Internet's Public Key Infrastructure (PKI) because they issue the Secure Sockets Layer (SSL) certificates that browsers use to authenticate content sent from web servers. All popular web browsers use web servers' SSL certificates to keep content delivered online secure. They all need to trust certificate authorities to issue certificates reliably. SSL certificates are used in conjunction with the Transport Layer Security (TLS) protocol to encrypt and authenticate data streams for the HTTPS protocol, and are therefore sometimes referred to as SSL/TLS certificates or simply TLS certificates. The first time ProxHTTPSProxy is started, it creates the keys for a certificate authority in its program directory if there is none. This file CA.crt is used for on-the-fly generation of dummy certificates for each visited website which are stored in the subfolder Certs. And, there is a second file called cacert.pem located in ProxHTTPSProxy's program directory. This file cacert.pem contains the currently valid root certificates (will be considered in more detail below) used by the proxy to verify the server connections. Since your browser won’t trust the ProxHTTPSProxy's CA certificate out of the box, you will either need to click through a TLS certificate warning on every domain, or install the CA certificate once so that it is trusted. It has to be installed in the Trusted Root Certification Authority of Windows XP and in some cases additionally in the Certificate Manager of a browser as in the cases of New Moon, Pale Moon, Firefox, and others. The Internet Explorer doesn't possess an own certificates store and uses the Trusted Root Certification Authority of Windows XP. Typically, digital certificates contain data about the entity that issued the certificate and cryptographic data to verify the identity of the entity, including the entity's public key and expiration date for the certificate, as well as the entity's name, contact information, and other information associated with the certified entity. Web servers transmit this information when a browser establishes a secure connection over HTTPS. In doing so, they send to it the certificate and the browser authenticates it using its own root certificate store. The following graphic illustrates the structure of a Certificate Authority as for example GlobalSign: SSL/TLS certificates are based on PKI as mentioned above, and there are a few key parts that need to be in place for the SSL certificate to work: A digital certificate (for example, an SSL/TLS certificate) that proves the website’s identity. A certificate authority that verifies the website and issues the digital certificate. A digital signature that proves the SSL certificate was issued by the trusted certificate authority. A public key that your browser uses to encrypt data sent to the website. A private key that the website uses to decrypt the data sent to it. Here is another graphic to illustrate the role that a certificate authority (CA) plays in the Public Key Infrastructure (PKI): When installing such CA certificates in Windows XP manually, then there is something else to note. It can be of crucial importance whether one installs a root certificate under the account of the Current User or Local Computer. In the first post of my thread, you can find more information on that. Furthermore, exiting ProxHTTPSProxy completely, deleting the old CA.cert file in ProxHTTPSProxy's program directory, and restarting ProxHTTPSProxy will result in the generation of a new CA certificate CA.crt that will be valid for another ten years. In addition, the certificate bundle cacert.pem should be updated, at best regularly. You can do that with the tool cacert Updater Fixed which can be found in the download section under Downloads related to cacert.pem Certificate Update in the first post of this thread. This tool is also included in my program package ProxHTTPSProxy's PopMenu. And, that is the moment to note something very important. Any change to a ProxHTTPSProxy installation regarding the CA certificate or a severe system crash while one of the proxies is running in the background always requires a reset of all dummy certificates in the Certs subfolder. The word "reset" at this point means deleting all certificates that have been created in the Certs folder, manually by the user. The next time the proxy is started correctly, all necessary certificates will be created again when the corresponding websites are accessed. Here are a few screenshots of ProxHTTPSProxy's CA certificate (German edition of Windows XP, sorry!): The Root Certificates of Windows XP In cryptography and computer security, a root certificate is a public key certificate that identifies a root certificate authority (CA). Root certificates are self-signed and form the basis of an X.509-based PKI. Either it has matched Authority Key Identifier with Subject Key Identifier, in some cases there is no Authority Key identifier, then Issuer string should match with Subject string (RFC 5280). For instance, the PKIs supporting HTTPS for secure web browsing and electronic signature schemes depend on a set of root certificates. A certificate authority can issue multiple certificates in the form of a tree structure. A root certificate is the top-most certificate of the tree, the private key which is used to "sign" other certificates. All certificates signed by the root certificate, with the "CA" field set to true, inherit the trustworthiness of the root certificate. A signature by a root certificate is somewhat analogous to "notarizing" identity in the physical world. Such a certificate is called an intermediate certificate or subordinate CA certificate. Certificates further down the tree also depend on the trustworthiness of the intermediates. The following graphic illustrates the role of a root certificate in the chain of trust: The root certificate is usually made trustworthy by some mechanism other than a certificate, such as by secure physical distribution. Root certificates are distributed in Windows XP by Microsoft and located in special certificate stores. These certificate stores may be viewed through the Certificates snap-in Certmgr.msc in the Microsoft Management Console (MMC). You can open the Certificates console focused on the Current User on a Windows XP computer by opening Certmgr.msc in the Run dialog box. Here is a screenshot of what you see running this command (German edition of Windows XP, sorry!): The root certificates of Windows XP can be updated by @heinoganda's Certificate Updater or by my self-created Root Certificate and Revoked Certificate Updaters, in both cases to the most recent ones provided by Microsoft. These updaters can be found in the download section under Downloads related to Root Certificate Updates in the first post of this thread. There is no automatism for this updating. It must be done manually by the user and, if possible, regularly. @heinoganda's Certificate Updater is also included in my program package ProxHTTPSProxy's PopMenu. Greetings from Germany, AstroSkipper1 point
-
@SC7601! Using ProxHTTPSProxy with browsers that already support TLS 1.2 or 1.3 is not the purpose of it. Generally, these TLS proxies are needed to access Windows Update or Microsoft Update, for example. Or, for updating programs that require the old Internet Explorer. Or, for email programs that cannot set up such connections themselves, e.g. eM Client or Eudora, and so on. But, all this has nothing to do with the fact that you actually just wanted to test my software package on a time-period correct system. Didn't it? BTW, you can test it with browsers already supporting TLS 1.2 and 1.3, too. Anyway, it was your suggestion! Cheers, AstroSkipper1 point
-
Update notification! My article "ProxHTTPSProxy or HTTPSProxy in Windows XP for future use" in the first post of this thread has been extended by a new section about TLS and their cipher suites. It will be updated and enhanced continously by everything about my program packages in the next weeks. A lot will be rewritten due to the existence of the brand new TLS 1.3 proxy. A further, new section will be added, too. So, stay tuned! If you are interested in, then have a look from time to time here. Cheers, AstroSkipper1 point
-
This thread is about different proxies to establish secure connections to servers or, more generally, to the internet. You often read about TLS and cipher suites here. Therefore, I have written a short article on these "termini technici" for those who do not know exactly what is meant by them. The TLS protocols and their cipher suites If you research the term TLS on the internet, you will get a lot of information, sometimes very simply presented, sometimes very technical, more for IT experts. With this small article, which can be seen more as a summary, I try to provide a little more transparency in this stuff. Transport Layer Security, abbreviated TLS, is a protocol for the authentication and encryption of Internet connections. For this purpose, TLS is inserted as its own layer between TCP and the protocols of the application layer. Here is a linked graphic to make it more clear: The individual tasks include authentication, certification, key exchange, integrity assurance and encryption. The main tasks are to guarantee the authenticity of the contacted remote stations, in most cases a server, by means of a certificate and to encrypt the connection between the remote stations. Here is a second linked graphic to demonstrate the actions and reactions in the communication between a client and a server: The used protocol defines the basic communication for the connection and is as crucial for a secure connection as the encryption protocol itself. Due to a series of vulnerabilities, the SSL2 and SSL3 protocols must be considered a security vulnerability and should be avoided at all costs. The successor to SSL3, TLS 1.0 should also be avoided, as the protocol offers a method to downgrade an established TLS 1.0 connection to SSL3. Thus, the connection is again vulnerable to the vulnerabilities that affect SSL3. Unfortunately, its successor TLS 1.1 is also no longer up to date and should be rather avoided nowadays. For a long time, the TLS 1.2 protocol was considered secure and therefore recommended. It offers a number of improvements that should ensure the security of connections again. In general, each new SSL or TLS version has brought additional features and options, making configuration a little more confusing, implementation more error-prone and handling more tedious. Overall, the use of TLS has become more insecure. With TLS 1.3, this should change, at best. Or, this was and is the actual goal, at least. For this reason, every single function of TLS has been tested for its security benefits and risks. In the process of development and in regard to the present knowledge, some parts were removed that no longer offer security and some of which are now also considered insecure. At the same time, security was improved with new procedures. Furthermore, measures for performance optimisation and preventive hardening measures for future attacks were taken into account. TLS 1.3 breaks backwards compatibility for the first time, which unfortunately causes some problems in practice. Connections with TLS 1.3 can be interrupted either because the connection is not accepted en route or due to a defective web server. Anyway, the protocols TLS 1.2 and, above all, TLS 1.3 are recommended as secure protocols nowadays. Here is a list of typical protocols and their cipher suites used by the TLS 1.3 proxy of my current program package ProxHTTPSProxy's PopMenu TLS 1.3 3V3 as an example. It's a screenshot taken from the website https://browserleaks.com/ssl: In the screenshot above, you can see many so called cipher suites belonging to specific TLS protocols. A cipher suite is a standardised collection of cryptographic procedures (algorithms) for encryption. In the Transport Layer Security (TLS) protocol, the cipher suite specifies which algorithms are to be used to establish a secure data connection. A cipher suite is generally displayed as a long string of seemingly random information, but each segment of that string contains essential information. Generally, this data string is made up of several key components: The used protocol, in most cases TLS. The key exchange algorithm dictates the manner by which symmetric keys will be exchanged such as RSA, DH, DHE, ECDH, ECDHE. The authentication algorithm dictates how server authentication and (if needed) client authentication will be carried out such as RSA, DSA, ECDSA. The bulk encryption algorithm dictates which symmetric key algorithm will be used to encrypt the actual data such as AES, 3DES, CAMELLIA. The Message Authentication Code (MAC) algorithm dictates the method the connection will use to carry out data integrity checks such as SHA, SHA256, MD5. In some cases, there is an Elliptic Curve Cryptography (ECC) which is an encryption technique that provides public-key encryption similar to RSA. While the security strength of RSA is based on very large prime numbers, ECC uses the mathematical theory of elliptic curves and achieves the same security level with much smaller keys. Here are three linked graphics to illustrate this with examples: This article will also be part of my main article in the first post of this thread as soon as possible so that everyone is well informed about the technical background and the purpose of TLS and their cipher suites which are important for our proxies. Greetings from Germany, AstroSkipper.1 point
-
Hello @Taiga-chan! Glad to hear you got my program package working! Have fun with it! You're welcome! And, many thanks! Greetings from Germany, AstroSkipper1 point
-
Update notification! Both versions of my Root Certificate and Revoked Certificate Updater have been updated and are now of 08/23/2022. You can find them in section Downloads -> Latest Downloads -> Downloads related to Root Certificate Updates in the first post of this thread. Cheers, AstroSkipper1 point
-
No, I am not angry at all. But, as you know, I mean what I write, i.e., I would like to read comments with your personal experiences and ideas. I don't like rephrasing, repeating and comments without own content. To show you what I mean I rewrote your statement. Here is your comment in a more personal way of wording providing own opinions and experiences: It's just an example.1 point
-
Thank you @mina7601! But basically, it is not necessary to rephrase my statements, and frankly, I don't like that at all. My statements are meant as they were formulated by me. If you want to comment on them, I would like to read your own opinion and not what I have already said or maybe, didn't want to say, either. Provide your own experiences and thoughts! That would be much more interesting and valuable! IMHO, self-created content that contains personal and unique statements without constantly repeating those of others should be the goal of a poster, actually. The human mind, no matter what age, is capable of creating and formulating its own. Finding the right and individual path in life and also here in this forum always means forming your own opinion, standing by it and expressing it to others. I hope this helps you a bit! Cheers, AstroSkipper1 point
-
Very good! It's all fine with my program package. We had here a beta test, and all my self-created executables are definitely clean. Any alarm notfication from security programs is a false positive.1 point
-
Update notification! The Root Certificates have been updated and are now from 23-08-2022. Here is a screenshot: My self-created, offline Root Certificate Updaters will be updated as soon as possible. Cheers, AstroSkipper1 point
-
The computer has to work and do its job. If not, you have to solve it! But please, do not talk about it! It's boring. Ever experienced this?1 point
-
Same here in Germany. Mina is the first name of a female. But in Egypt, it is vice versa! Right! Or, you can also use the TLS 1.3 proxy locally. The TLS 1.3 proxy and thus also my program package makes it possible to establish connections to servers or generally to the Internet via the TLS 1.3 protocol (and all other TLS protocols which was already done with previous releases) in Windows XP even independently of browsers, which was not possible before. You can test my program package with the old Firefox ESR 52.9.0. Here is a link, you still have to choose your language: https://ftp.mozilla.org/pub/firefox/releases/52.9.0esr/win32/ And, in any case, with the Internet Explorer 8, too. Some email programs and others also need such a proxy nowadays. All information about these proxies can be found in my article "ProxHTTPSProxy and HTTPSProxy in Windows XP for future use" in the first post of this thread. This article will be updated when time is available. My program package ProxHTTPSProxy's PopMenu TLS 1.3 3V3 is fully documented inside its archive.1 point
-
And, just to be clear, I am not a Bavarian!1 point
-
Thanks for the quick reply , both versions (32 and 64bit) won't launch . They are just giving different errors , x64 bit shows : SHAssocEnumHandlersForProtocolByApplication not found in shell32.dll And no , I'm not trying the latest versions . It's Opera 60 and earlier. Edit : maybe the patched files are old , but I don't know where to find their newer versions...1 point
-
Hello , sadly it didn't work with Opera , I did all aforementioned steps , rebooted , yet it still wants TryAcquireSRWLockExclusive. I even tried older versions , like 60 . I'm using extended files dated July 2020, from the known youtube video.1 point