Search the Community
Showing results for tags 'Security'.
-
Antimalware, firewall, and other security programs for Windows XP working in 2023 and hopefully beyond I hereby open a new thread on the topic of security programs for Windows XP. I have been thinking about that for a longer time, and then I decided to tackle this project. Windows XP is a very old operating system and a deeper knowledge of how to make it more secure is very important in my opinion. Therefore, I think it makes sense to get an overview of all the security programs still available for Windows XP. The thread "Which Antiviruses are Known for a Fact to be Working on XP SP3 as of 2019?", where I have previously written frequently about antivirus programs, has become rather bloated and confusing due to many informationless posts, is mainly focused on the topic of antivirus programs for Windows XP and has been completely unstructured from the very beginning. It is good to have such a thread full of different information for reference but there are many posts either outdated, incomplete or off-topic. Therefore, I have decided to start a completely different thread from scratch. I deliberately chose the term antimalware in the title of this topic. In these days, most so-called antivirus programs can not only identify computer viruses, but also trojans, worms, rootkits, exploits, spyware, and so on. Generally speaking: a virus is a malware, but a malware is not always a virus. Therefore, malware is a generic term for any malicious software, including viruses. For many years now, the so-called antivirus programs have actually been antimalware programs. In any case, this new topic here is about antimalware, firewall and other security programs for Windows XP. Under the term other security programs, I include among others security suites like internet security and total security, antivirus, antispyware, anti-rootkit, anti-exploit, online and offline scanner, ad blocker, protection layer, virtualization, security check and control programs and so on that make the use of Windows XP safer. And to avoid any misunderstanding, the main focus in this thread is on the concept of security. Those security programs that have been officially classified as insecure or not trustworthy are not the subject of consideration here, of course. Furthermore, many of these security programs can no longer be clearly classified in one of these categories due to their multifunctionality. I therefore define the following categories and their abbreviations: AM+ = Antimalware program with real-time protection AM- = Antimalware program without real-time protection SP = Specialized program (focused on one main antimalware function) IS = Internet Security TS = Total Security ON = Online scanner OF = Offline scanner AB = Ad blocker FW = Firewall VP = Virtualization program PL = Protection layer program SC = Security check program CP = Control program MF = Multifunctional program In addition, for the sake of simplicity, I define the following licence types and their abbreviations, reduced to the essentials: C = Commercial (any payment software including shareware) F = Free D = Donationware O = Open source In the second post of this thread, I will provide and maintain an alphabetical list of working antimalware, firewall, and other security programs for Windows XP which were each presented in a corresponding post here. This list has the following columns: Name, Version, Type, Date and Link. Name means the name of the program, Version means its last/latest version, Type means its license type, Date means its last/latest date of release or creation (in some cases, there is no date of release available anymore) and Link means the link to its corresponding post here in this thread. I will only include programs in this list that receive updates in some form, be it program updates, definition updates or database updates. With the exception, of course, that there are also programs that do not necessarily need such updates. In the third post of this thread, I will create and maintain an alphabetical list of programs that need to be tested for compatibility, features and support or whose installers have been lost and therefore could not be tested. In the fourth post of this thread, I will create an alphabetical list of programs that have recently been abandoned or should be avoided. Some of them should only be used for a while or be avoided due to security reasons. This project is very extensive and involves a lot of work. In-depth research in particular is very time-consuming, but necessary. So be patient, especially if the list of programs fills up slowly! As always: Good things come to those who wait. And just for clarification, I will not check all the programs myself to see if they can be installed properly and work, of course. Here, other members can make a perfect contribution with their knowledge or experiences already made. Furthermore, all the programs I have listed are not necessarily to be understood as recommendations. Basically, they are simply options that are still available for Windows XP. Because we all know that most manufacturers of security software have long since given up on Windows XP. If I personally consider a program to be good, I will express this in its relevant post. More about that here: Any discussions, questions or suggestions about security programs for Windows XP are explicitly welcome. But one thing must be very clear, everything should relate to this topic. Just for clarification, insulting, provocative or completely off-topic posts (especially about operating systems other than Windows XP) will not be tolerated. That means, please stay on topic! This thread is intended to be a well-structured source of information where readers can get ideas on how to make their old Windows XP a bit more secure. If you like this thread, or you find it interesting and helpful, I would appreciate any contribution, be it a comment, a like or an upvote. Thanks for your interest! Windows XP forever! Kind regards, AstroSkipper
- 1,225 replies
-
7
-
- Security
- Antimalware
-
(and 3 more)
Tagged with:
-
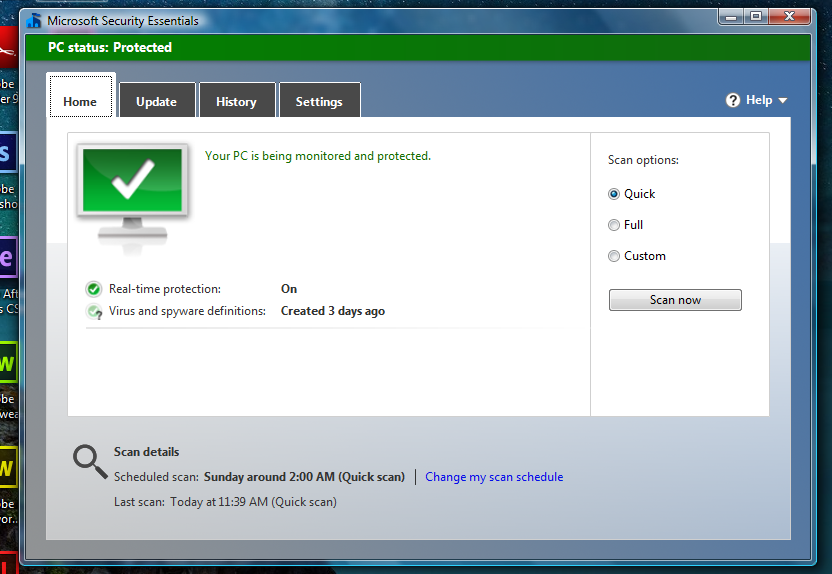
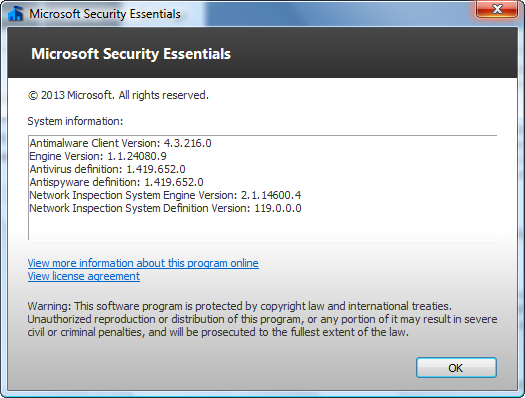
Full explanation (follow the explanation step by step to work with you correctly) First we will need some things including 1 - Microsoft Security Essentials whether you want the 2013 version or the latest (note I am working with the 2013 version and it works very well for me unlike the latest version there were some problems with the antivirus updates) Download links Microsoft Security Essentials x86 (2013 Release) Download Version - 32 Bit Microsoft Security Essentials x64 (2013 Release) Download Version - 64 Bit KB4474419 Update (x86) KB4474419 Update (x64) 2 - Windows update, which is KB4474419, which will be required to be able to work on the program First, you will download the KB4474419 update for the 32 or 64-bit system. Make sure what you have first Just click on the (Computer) icon and choose Properties to show you the information or from the control panel Then restart the device after updating the program Important note for those concerned - you can also get this update and some Windows Vista updates and other Microsoft products with Legacy Update Tool After installing the update, you must now start installing the program after installing it and opening it from the main interface, go to the (Update) tab, then update your antivirus and you will only wait a few minutes After that, congratulations, the program is ready to work with it
-
"Kyber (Quantum-Resistant Mechanism) in Chrome 124 Leads to Web Connection Problems" by Luke Jones "Impact on Connectivity and Responses The introduction of the Kyber768 quantum-resistant key agreement algorithm, intended for TLS 1.3 and QUIC connections, has inadvertently caused connectivity issues. System administrators have reported on Reddit and other platforms that web applications, firewalls, and servers are dropping connections following the ClientHello TLS handshake." "To address these connectivity problems, Google has provided a temporary workaround. Users experiencing issues can disable the TLS 1.3 hybridized Kyber support in Chrome by adjusting the browser's flags. Similarly, administrators have the option to disable the PostQuantumKeyAgreementEnabled policy." Source: https://winbuzzer.com/2024/05/02/google-chrome-124-launches-with-quantum-resistant-encryption-causes-connectivity-issues-xcxwbn/
-
Software support Firefox Nightly 2024-01-18+ if you turn on security.tls.enable_kyber in about:config. Available with TLSv1.3 including HTTP/3 (QUIC) This article is also available in Français, Deutsch and Español. https://blog.cloudflare.com/post-quantum-for-all/ Do any forum users use this Post-Quantum Key? It is possible to verify with 2 tests: https://browserleaks.com/tls You will see it under "Key Exchange" https://pq.cloudflareresearch.com/ You will see: "You are using X25519Kyber768Draft00 which is post-quantum secure"
- 5 replies
-
2
-
- Evil hAckErS
- Encryption
-
(and 3 more)
Tagged with:
-
what's the best antivirus that works with the extended kernel? ive been doing research into this recently and can't find anything that would work properly (or won't work at all) so my question is are there any antivirus known to work with the extended kernel if anyone could help with this it would be much appreciated. -legacyfan
- 25 replies
-
1
-
- compatibility
- anti-malware
-
(and 1 more)
Tagged with:
-
One of the most effective ways to keep your system secure and private while on the web is to implement a managed blacklist of sites you just won't allow your device(s) to visit. I have been developing a script that gathers data from various contributors around the web who have developed lists of badware web sites, and compiles the info into a blacklist of sites you REALLY DO NOT want to visit. The result is pressed into service by a very simple process: Adding blacklist entries into your hosts file. Windows uses the file %SystemRoot%\System32\drivers\etc\hosts. to allow you to pre-load your DNS cache. The intent is that if you have a server you'd like to name, but the name isn't provided by an online DNS service, you can name it in your hosts file. But what the hosts file can ALSO do is allow you to redirect name resolution to 0.0.0.0 for any number of sites that serve malware, ads, track you, or just deliver things you don't want to see. An attempt to access that named site just fails. Your computer never contacts it. If you put the right list into your hosts file, your system will automatically, and most importantly without noticeable ongoing overhead, just avoid visiting badware sites. That's it. It doesn't require decisions by you, and it doesn't cause extra software to run. And there's no cost; the information is freely available - and surprisingly well maintained. What you see in a practical sense is that your browsing experience becomes free from ads, you no longer see viruses and malware trying to come in, and your browsing experience even gets faster. No kidding. Let's say, for example, that a badware site is www.iservemalware.com... Maybe links to www.iservemalware.com are embedded in other people's web pages, in ad slots, for example, or in things you fear your kids might click on. Maybe it shows up as a link in an eMail. Or even worse, html that just opens the site as soon as you view the message. It'd be nice if something would just stop your computer from visiting such a bad site, right? One entry in the hosts file will do just that: 0.0.0.0 www.iservemalware.com Boom, your computer won't visit the online server for www.iservemalware.com again. Maybe you've already even added some of your own badware sites you've run across to your own hosts file. But wouldn't it be great if you could combine the web browsing experiences of other folks out there too? There are literally tens of thousands of bad web sites. Seriously. But that number is not infinite! I present to you, free of charge and with no strings attached, my HostsCompiler script: http://Noel.ProDigitalSoftware.com/files/HostsCompiler.zip It retrieves badware site data, processes it into a minimum size blacklist, and augments your existing hosts file. I've tested it on 64 bit Windows 7, 8.1, and 10, though it will probably also work on 32 bit systems and Vista and XP. To set it up: Unzip all the files into the same folder, open an elevated command prompt, CD into that folder, run HostsCompiler.bat by typing its name, it will prompt you to continue, and it will immediately go out and find lists of badware / malware / adware sites from online sources and add them to your hosts file. You'll be instantly protected against visiting nearly 50,000 known badware sites. You'll notice a positive difference in your browsing experience. Run it regularly - for example by scheduling it to run every day using the Windows Task Scheduler as I do - and you'll have a "set it and forget it" system that will keep itself up to date to block the latest servers showing up online with intent to turn you into a victim. For me the script literally runs to completion in 5 seconds. The online sources this script obtains the information from are the following at the time of this writing: http://winhelp2002.mvps.org http://malware-domains.com http://www.malwaredomainlist.com http://adaway.org http://someonewhocares.org http://pgl.yoyo.org http://www.quero.at I wish to acknowledge the fine people who publish the lists at the above sites for their contributions to enhanced online security, privacy, and browsing performance. The executables in my zip file are from the freely available GnuWin32 toolkit plus one I've written (SHOWTIME, a tiny command line executable for displaying the current time/date), and the script is editable and readable, with plenty of comments. It's designed to coexist with whatever else you do with your hosts file. If you have even the slightest worry over running this, I ENCOURAGE YOU to research the executables online and open HostsCompiler.bat in a text editor and learn how it works. Those of you wishing to schedule regular HostsCompiler runs will be interested in this excerpt from the script: :: Synopsis: :: :: HostsCompiler NoPrompt :: :: NoPrompt - (Optional) If specified, will avert the request for confirmation. :: :: :: Suggest scheduling this job with a command line similar to: :: :: HostsCompiler NoPrompt >>C:\Some\Path\HostsCompiler.log 2>&1 :: Be aware that this is batch script and that altering your hosts file is a bit geeky. It requires a little knowledge about how Windows works and the exercise of some care. Don't use this if you don't feel comfortable with manipulating files on your computer. Please let me know if you have any problems or suggestions about things that could be improved. I'd love to hear your experiences with this method of enhancing security. Mine have been good. After running this, if you find a site you'd like to visit no longer works, there are ways to determine what the host name is and whether it's being blocked by a hosts entry - e.g., choose F12 developer tools in Internet Explorer, go to the Network tab, enable tracing, navigate in your browser, and look for a Result of (Aborted) - and you need only comment out the entry in your hosts file to restore access. -Noel
-
The Department of Homeland Security has advised that PC owners uninstall Apple's QuickTime for Windows, after two vulnerabilities were discovered in its code. Because Apple is no longer updating the Windows version of the software, the DHS says "the only mitigation" is to remove the software entirely, or else risk "loss of confidentiality, integrity, or availability of data, as well as damage to system resources or business assets." More information: The Verge
-
I've been using Kerio Personal Firewall v2.1.5 (not the later Kerio's) all the way back to when it was called Tiny Firewall. I absolutely love it. I've tried many over the years and have come away disappointed after being spoiled by such a wonderful product. I'm looking for something similar to Kerio but perhaps a bit more hardened. Kerio has been EOL for ages. It must be as configurable as KPF. That it to say; it must alert me to each and every connection attempt, to define what program making the connection, what IP(s), port number, what type...UDP, TCP or ICMP and type of ICMP, incoming, outgoing or both directions, etc. Most of these must be definable in the firewall alert. It always can't be bloated. KPF is 3 files, totally 980 KB (not counting the help file). I might have asked this before and not looking for miracles just anything close and nothing bloated but I don't expect miracles like 980 KB. .
-
I know there is a place on this site where Windows Unofficial Updates are available (especially those for XP) Would someone please let me know that URL so I can bookmark it. I'd like to continue using XP and keep it updated, especially with the security patches) Thanks, tlcmd