silverni
MemberContent Type
Profiles
Forums
Events
Everything posted by silverni
-
Reference to an old thread: The browsing tends to become the Achilles' heel of Windows XP, which otherwise is still perfectly adequate and more productive than its successors. Fortunately, fairly up-to-date browsers are still available in WinXP, thanks to the contributions of some developers. For access to institutional sites there should be no problem for years to come (there are specific laws for accessibility), but access to sites that are "modernists" is problematic even today. For retrieve information from Twitter, Reddit, Facebook, and others, I use procedures atypical (I basically disable CSS and javascript), to interact I use the specific interfaces that these sites offer for old or limited browsers, e.g.: <https://old.reddit.com/> instead of <https://www.reddit.com/> In extreme cases (but I have never needed them), I have available some advanced solutions, which still allow me to have available all the data personal data that I access in WinXP: 1. From within XP start a Win7 virtual machine and use modern browsers that do not run on WinXP. 2. From within XP start an Android virtual machine and use Chrome or other known up-to-date browsers, or apps specific to the service you want to access. 3. Use as through an Android smartphone or tablet by controlling it from WinXP, e.g. via MyPhoneExplorer, and an updated browser or a dedicated app; the control from WinXP allows you to type from the PC keyboard all the information available in WinXP (passwords, etc.). 4.Use as through an NT6+ laptop system controlled by WinXP, and use modern browsers. 5. Exit WinXP and start Windows 10 (multiboot PC), and use modern browsers. Notes: a. From Windows 10 I access most of the programs and all the personal data I I use in WinXP. b. My Win10 installation is heavily customized, and the user interface looks a lot like WinXP. c. In Windows 10 I disabled Windows Update, the main source of system instability and control difficulties; it has been updated for about eight years, which should be enough to get a stable system. If the use of these "special systems" becomes frequent, it will be time to switch from WinXP to Win10 as the main operating system. Regards
-
There seems to be some confusion in some of the interventions in the thread. Drivers from W2k3 and Paragon GPT loader in WinXP allow access to GPT partitioning, but they have little to do with support for disks larger than 2TB, GPT can also be used on disks smaller than 2TB. For 3TB+ disk support, other factors are crucial, namely: BIOS, HD controller, drivers; for disks over USB, the primary variable is the USB box controller. For support for 3TB+ disks with WinXP there are a myriad of more or less proprietary solutions, but no universal solution; you must find and test the solution that best suits your hardware, and the quickest test is just to use CheckDisk from WinXP; if the disk contains data, you need to back it up or transfer it, before running the test. The support may change if you transfer the HD between the USB box and a controller internal to the PC. Regards
-
A real-time antimalware may be useful for novice users, but it makes little sense for users with a high level of mastery such as those who frequent this Windows XP section of the forum. After subjecting a system to on-demand scanning by multiple antimalware, online and offline, I can consider the system safe; rechecking every time I use components that have been in the system for many years and used countless times without problems is just a waste of time and computational resources. Since at least ten years I have been performing only periodic scans, and since the scans end regularly without reporting problems, gradually the period has automatically lengthened; and in any case, a possible infection would not create big problems and would be detected immediately. It is necessary instead carefully monitor new grafts, external elements entering into the system. To test new programs the procedures are well known to users of this forum: Virtual Machines, SandboxIE, other forms of sandboxes, etc. I typically test the installation of new programs under SandboxIE, and I use two scripts to derive a report of the changes that the installation would make to the system (new or changed files, changes to registry, etc.), reports that I archive along with the program. For incidentally, from this structural information I almost always build a portable instance of the program, which I keep off the system partition (20 GB, of which only 13.2 GB is occupied). If the program installs drivers in the system, SandboxIE is generally not usable and it is necessary to run the test in a virtual machine; even in this case I create and keep a report of the changes that the installation makes to the system. But today in reality the main source of infection is the Web, and the most dangerous vehicles are browsers; here the variables and defense mechanisms are virtually infinite, so I subscribe to the need posed by @UCyborg to create a new dedicated thread: Maybe we need a thread about surviving on the modern internet without an antivirus? Notes: 1. Similar considerations apply to Android, where the real usefulness of antimalware is even more doubtful, and many other defense tools exist. 2. I consider improper that in this technical forum are allowed expressions and positions of a decidedly racist nature, further confirmation of the well-known maxim that the first casualty of a war is truth (and common sense, I might add); but this too surely requires a dedicated thread. Greetings
- 910 replies
-
4
-
- Security
- Antimalware
-
(and 3 more)
Tagged with:
-
=== https://www.romexsoftware.com/bbs2/en-us/viewtopic.php?f=30&t=1135 support » Mon Feb 06, 2012 2:30 am - 2013-07-30 Update #002 System cannot resume from hibernation if Windows pagefile.sys is set to a virtual disk which uses Invisible Memory. [Issue cannot be fixed] Workaround: Do not set pagefile.sys to such virtual disk. Alternatively, disable hibernation. support » Wed Jul 25, 2012 8:11 am Even sometimes you may see that it works on hibernates and resumes, it does not mean that it always works. It is risky whether you use SCSI or DirctIO ramdisk. --------- To use Invisible Memory, Romex Software sell also PrimoCache Regards
-
XP/Vista-compatible clients for modern email services?
silverni replied to Mathwiz's topic in Windows XP
A clarification. An "app password" is a password chosen by the provider that is more robust than those normally chosen by customers; otherwise it functions identically to traditional passwords. One same "app password" can be used with multiple POP3 and IMAP clients, and in each client, for each remote account, multiple local accounts can be set up with different POP3 or IMAP access modes. The my main mail client is still Outlook 2003, and using MyPhoneExplorer I can synchronize with Andoid devices. Regards -
Other info Regards === https://pgl.yoyo.org/adservers/formats.php 230605 junkbuster - in internet junkbuster/privoxy format description: can be used as a starting point for the Internet Junkbuster Proxy, also usable with Privoxy http://www.junkbusters.com/ijb.html more info: https://pgl.yoyo.org/adservers/news.php#fourmore view: https://pgl.yoyo.org/adservers/serverlist.php?hostformat=junkbuster
-
My configuration is in first post. Regards
-
Other info Regards === https://www.privoxy.org/faq/misc.html 4.23. Should I continue to use a "HOSTS" file for ad-blocking? One time-tested technique to defeat common ads is to trick the local DNS system by giving a phony IP address for the ad generator in the local HOSTS file, typically using 127.0.0.1, aka localhost. This effectively blocks the ad. There is no reason to use this technique in conjunction with Privoxy. Privoxy does essentially the same thing, much more elegantly and with much more flexibility. A large HOSTS file may get in the way and seriously slow down your system. If you think your hosts list is neglected by Privoxy's configuration, consider adding your list to your user.action file: { +block } www.ad.example1.com ad.example2.com ads.galore.example.com etc.example.com === https://scripttiger.github.io/alts/ 230602 Additional Blacklist Support Below are assorted versions of Steven Black's unified hosts files reformatted for various other applications for additional support and are synced regularly. ::: Privoxy* To be used with a Privoxy action file. ::: * = Formats marked with an asterisk ("*") denote formats which take advantage of the higher flexibility afforded them and prune child sub-domains of parent domains already present on the list. For example, a domain assets.analytics.foo.com will be dropped from the list if either analytics.foo.com or foo.com are already present on the list. In the same example, analytics.foo.com would be dropped from the list if foo.com is already present on the list. However, if only assets.analytics.foo.com is present on the list, then both analytics.foo.com and foo.com will not be blocked. ::: Unified hosts = (adware + malware) FQDN | RFQDN | Adblock | dnsmasq | Unbound | RPZ | Privoxy | IPv4_IPv6 | Compressed | MCompressed ::: Privoxy https://scripttiger.github.io/alts/privoxy/blacklist.txt ::: Unified hosts = (adware + malware) Unified hosts + fakenews Unified hosts + gambling Unified hosts + porn Unified hosts + social Unified hosts + fakenews + gambling Unified hosts + fakenews + porn Unified hosts + fakenews + social Unified hosts + gambling + porn Unified hosts + gambling + social Unified hosts + porn + social Unified hosts + fakenews + gambling + porn Unified hosts + fakenews + gambling + social Unified hosts + fakenews + porn + social Unified hosts + gambling + porn + social Unified hosts + fakenews + gambling + porn + social
-
I came across the following pages that indicate the possibility of also using Privoxy as a filter to prevent malware, ads, etc. Many blacklists can be found on the Internet in HOSTS format, it seems easy to convert them into a format that can be used with Privoxy. Hereinafter I also point to a very curated source of blacklists in HOSTS format. By the way, I have not used real-time antimalware for at least five years. Regards ----------------------- https://github.com/ScriptTiger/Hosts-Conversions 230530 ScriptTiger / Hosts-Conversions Public Drag and drop a hosts file to convert it. ::: Privoxy: Converts a hosts file to Privoxy action file format to be used with a Privoxy action file, i.e. using something like {+block{Steven Black blacklist.}}. https://scripttiger.github.io/more/ 230530 Hosts-BL: Simple tool written in Go (=== exe NT6) to handle hosts file black lists that can remove comments, remove duplicates, compress to 9 domains per line, add IPv6 entries, as well as can convert black lists to multiple other black list formats compatible with other software. https://github.com/ScriptTiger/Hosts-BL 230530 ScriptTiger / Hosts-BL Public Usage: hosts-bl [options...] <source> <destination> -f <format> Destination format: ..., privoxy, ... https://github.com/StevenBlack/hosts Consolidating and extending hosts files from several well-curated sources. Optionally pick extensions for porn, social media, and other categories.
-
SMPlayer.22.7.0-qt5.6-Port.7z can use yt-dlp.exe by @nicolaasjan. The subdir \mpv\ contains MPV NT6, you can delete all the contents and copy yt-dlp.exe there. In the same subdir create yt-dlp.conf: --no-check-certificates #Suppress HTTPS certificate validation. MPV 10.2015 in WinXP can use yt-dlp.exe by @nicolaasjan renamed youtube-dl.exe <https://web.archive.org/web/20160610143950/https:/mpv.srsfckn.biz/> In the dir of MPV.exe I created a subdir \portable_config\, and in it I placed fonts.conf already in the package, and created mvp.conf: ytdl-format=720p/best ytdl-raw-options=no-check-certificates= ------------ youtube-dl.exe (yt-dlp.exe) when launched from MPV does not read its own configuration files (yt-dlp.conf), you can only pass parameters from MPV via ytdl-raw-options= SMPlayer.exe and MPV.exe can also be started by @roytam1 browsers with "Open With" or "mpv-youtube-dl-binding," as already indicated by others: ----------- IXOYE - 2023 January 13 I use "mpv-youtube-dl-binding" plug-in on NM28/S52: <https://web.archive.org/web/20160610143950/https:/mpv.srsfckn.biz/> <https://repo.hyperbola.info:50000/other/iceweasel-uxp/addons/mpv-youtube-dl-binding/watch_with_mpv-0.1.0-alpha.4-fx.xpi> nicolaasjan - 2023 Jan 13 In New Moon you can use the "Open With" extension to download videos or audio straight from the browsers right click menu: <https://ca-archive.us.to/storage/11/11097/open_with-6.8.6-fx+sm+tb.xpi> In my system VLC is less effective than SMPLayer and MPV for streaming Greetings
-
My Browser Builds (Part 4)
silverni replied to roytam1's topic in Browsers working on Older NT-Family OSes
I reported the bug to give way and time for the developers to fix it, but it is not a big deal to me. I have two versions of NM28 on disk, the one from February and the one from April, and I launch one or the other depending on the circumstances. By the way from WinXP I can boot a Win7 virtual machine, and in this one I can boot Palemoon, Firefox, and other NT6 browsers. Regards -
My Browser Builds (Part 4)
silverni replied to roytam1's topic in Browsers working on Older NT-Family OSes
The error does not occur in versions of the browsers until February, it only affects the latest versions of the browsers; it is a problem of the browsers, not of the site. Regards -
My Browser Builds (Part 4)
silverni replied to roytam1's topic in Browsers working on Older NT-Family OSes
error console screenshot 1.3MB , link from Onedrive: https://1drv.ms/u/s!AmvyhfGl8qmbgXddu90uCBgyvC5G?e=NuWXT8 Regards -
My Browser Builds (Part 4)
silverni replied to roytam1's topic in Browsers working on Older NT-Family OSes
-
My Browser Builds (Part 4)
silverni replied to roytam1's topic in Browsers working on Older NT-Family OSes
I need detailed instructions, I am not a web developer. I guess I need the report from the page that creates the error. From the "Toolkit Error Console" window, you can copy only one item at a time, do you need the whole page? Do I need to save the contents of the page in a file, and then attach it in a post? Or is it better to send the file as a personal message? Greetings -
My Browser Builds (Part 4)
silverni replied to roytam1's topic in Browsers working on Older NT-Family OSes
I tested Toolkit Error Console, What is F12 Browser Console? Regards -
After using Privoxy 3.0.20 for several months, I confirm that in my system it is much more efficient than ProxHTTPSProxy and BurpSuite 1.7.36, another SSL filter I have been using for some time. Meanwhile, @cmalex has compiled a build for WinXP of Privoxy 3.0.30, and it is running smoothly; so it will be quite easy to add TSL 1.3. Privoxy 3.0.40 is also available today. So far I have never needed to upgrade. Regards
-
My Browser Builds (Part 4)
silverni replied to roytam1's topic in Browsers working on Older NT-Family OSes
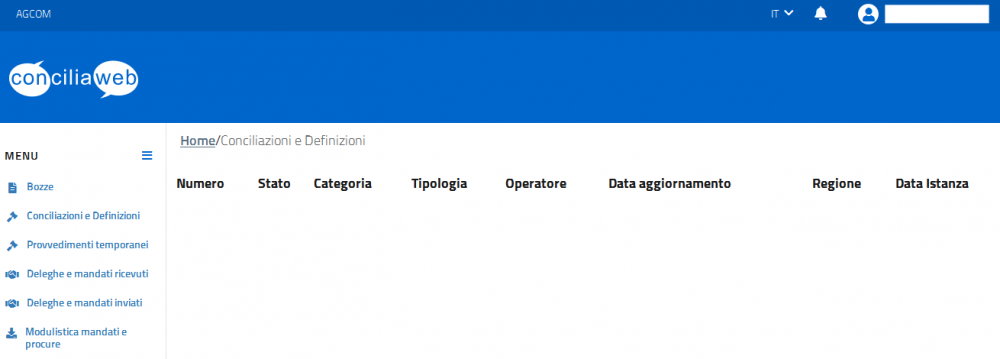
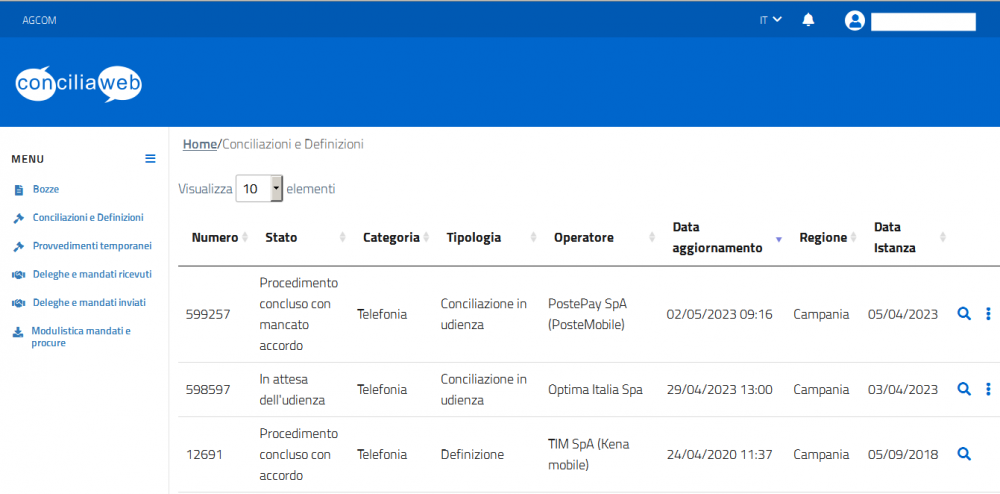
The following page is only accessible after login, so the bug is not easily reproducible. Source URL: https://conciliaweb.agcom.it Page reproduced by Firefox 52, and by the roytam1 programs from 20230211 The following image shows the same web page, but the list of practices is missing. The page is reproduced by Palemoon 32.1.1 from 20230417, and by the roytam1 20230415 programs tested: NM28, S52, S55, IceApe All Palefill versions tested are irrelevant: martok, roytam1, UCyborg 1.26.3 Regards -
My English is weak, sorry. For some time I have been using as SSL filter Privoxy 3.0.32 27/02/2021: https://www.privoxy.org/ https://www.privoxy.org/sf-download-mirror/win32/ Privoxy was born as a content filter, some years ago it has taken on the SSL filter function, then today: Privoxy = ProxhttpsProxy + Proxomitron Privoxy offers various advantages including a good updated documentation. At the moment I use Privoxy only as a SSL filter, with the configuration files that I report below. Privoxy 3.0.32 does not support TLS 1.3, supports various TLS 1.2, TLS 1.1, TLS 1.0, SSL 3 protocols; test: https://clienttest.ssllabs.com:8443/ssltest/ViewMYClient.html Privoxy 3.0.33 of 08/12/2021 does not work in my Winxp; I read that the compilation is simple (but today I can't do it), and that it can be linked with two cryptographic library, probably with the time Privoxy will also support TLS 1.3 ---- https://github.com/essandess/adblock2privoxy/issues/34 pdc1 May 15, 2021 I had to build my own privoxy, but it was very straightforward, the main thing to note is to include --with-openssl or --with-mbedtls when running configure to enable https-inspection. ----- My configuration With OPENSSL 1.0.2T I created the two files: privoxy.crt and privoxy.pem, during the creation I indicated the following data: Password: PrivoxyPassword Country Name (2 letter code):IT State or Province Name:Italia Locality Name:<MyCity> Organization Name: Privoxy Organizational Unit Name (eg, section): Privoxy Common Name: Privoxy Email Address: With Cert.MSC I imported the Privoxy.Crt file in the Windows certificates database: Certificates (Local Computet) > Authority of certifications reliable sources > Certificates > Right click > All activities > Import > Privoxy.crt I placed in the same subdir of Privoxy.exe the two files Privoxy.crt and Privoxy.pem I downaloaded cacert.pem updated and I placed it in the same subdir. In the same subdir I renamed the conf.txt file as config0.txt, and I copied my two configuration files config.txt and sv1.action At the moment in SV1.action I disabled the verification of the servers certificates, and I set an UserAgent suitable for my purposes. Greetings === config.txt #-- originali confdir . logdir . enable-remote-toggle 0 enable-remote-http-toggle 0 enforce-blocks 0 enable-proxy-authentication-forwarding 0 forwarded-connect-retries 0 accept-intercepted-requests 0 allow-cgi-request-crunching 0 split-large-forms 0 tolerate-pipelining 1 #--- modifiche mie listen-address 127.0.0.1:8079 enable-edit-actions 1 buffer-limit 40960 socket-timeout 30 #keep-alive-timeout 5 #connection-sharing 1 show-on-task-bar 0 activity-animation 0 close-button-minimizes 1 ca-directory . ca-cert-file privoxy.crt ca-key-file privoxy.pem trusted-cas-file cacert.pem certificate-directory R:\Temp\PrivoxyCerts ca-password PrivoxyPassword #actionsfile match-all.action #actionsfile default.action #actionsfile user.action actionsfile SV1.action #filterfile default.filter #filterfile user.filter #logfile privoxy.log #debug 1 #debug 1024 #debug 4096 #debug 8192 === SV1.action {+https-inspection} / # Match all URLs {+ignore-certificate-errors} / # Match all URLs {+hide-user-agent{Mozilla/5.0 (Windows NT 6.1; Trident/7.0; rv:11.0) like Gecko}} / # Match all URLs
-
Emulators and virtual machines, elixirs of eternal life for WinXP
silverni replied to silverni's topic in Windows XP
More than virtual machines, Android emulators seems interesting to me, for a long series of reasons. Recent developments in individual computing almost exclusively concern mobile devices; the Windows desktop environment has long been a mature product, recent developments are dictated exclusively by ambiguous and dangerous marketing strategies, oriented exclusively to organizations. For a single user with sufficient experience, recent versions of Windows NT6-10 are in fact a regression in terms of usability, but above all in terms of security (this aspect would require a dedicated post). The world of Android mobile devices, on the other hand, is in a phase of chaotic evolution, new solutions and applications are constantly being offered, almost all the most recent applications presented in the Windows desktop world have an Android version. Conversely, Android is still unstable and presents greater potential risks than WinXP. Reproducing an Android system in a stable and familiar environment like WinXP has many advantages, for example: - become familiar with the world of mobile devices and available apps - check the operation of the system and applications in more depth than is possible using an Android hardware device. Greetings -
Emulators and virtual machines, elixirs of eternal life for WinXP
silverni replied to silverni's topic in Windows XP
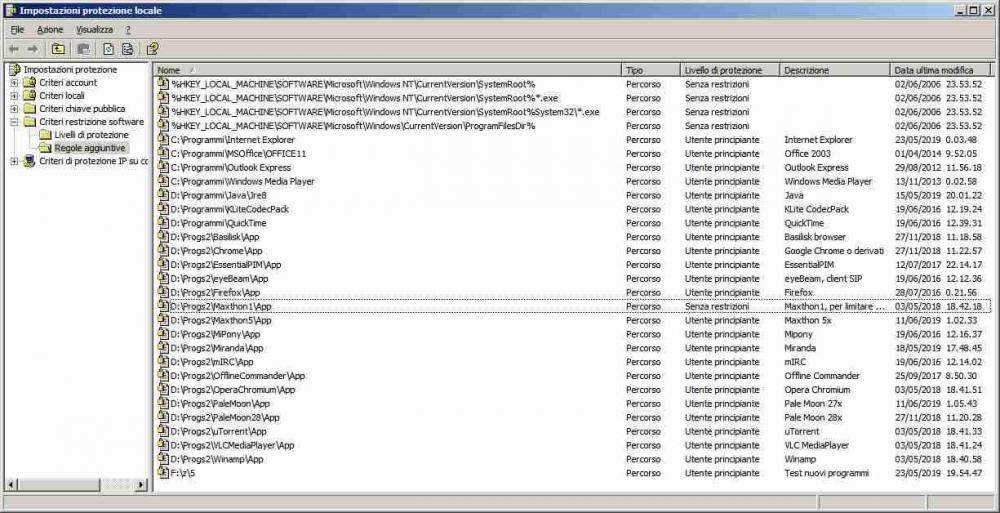
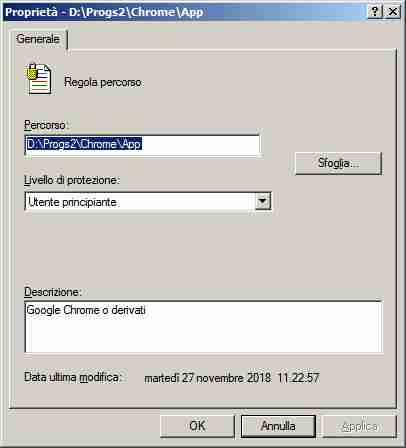
I currently do everything in WinXP. I created the mini-Win7 virtual machine for over a year, I started it only for testing and tuning, and the system was very solid. I'll probably need it sometime, and it's convenient to keep it ready. Certainly if I were to use the virtual machine over and over again it would be time to abandon WinXP, but for now I don't even see the need for it. The meaning of the thread is that the death of WinXP can be postponed indefinitely, in a future that is currently not predictable. I use VirtualBox 4.3.36 of 2016/01, the last officially supported and definitely working version in WinXP; for 5x the operation in WinXP should be verified, I did not find significant information on the Internet. As an operating system I only tested this mini-Win7, I don't expect I need more complete or modern systems. Among other things, the .vhd file can also be started autonomously from boot, as a secondary operating system for maintenance; and in reality this was the use envisaged by Wimb2, I believe the use as a virtual machine is my invention. I always try to use the minimum tool that allows me to achieve my goals. As a browser I almost always use NM27, the only one that supports the "Print pages to PDF" extension that I use a lot; more rarely I use portable NM28, or Firefox 52. I keep strictly away from sites that are too "trendy" or "experimental"; and in any case for the basic functions NM27 it is sufficient, for example I can download files and consult documentation on Github (and actually also works IExplorer6). As primary defense system I use secpol.msc, much more convenient than PSExec Sysinternals; settings can be changed on the fly and take effect immediately, no need to restart programs. I attach screenshot. Greetings -
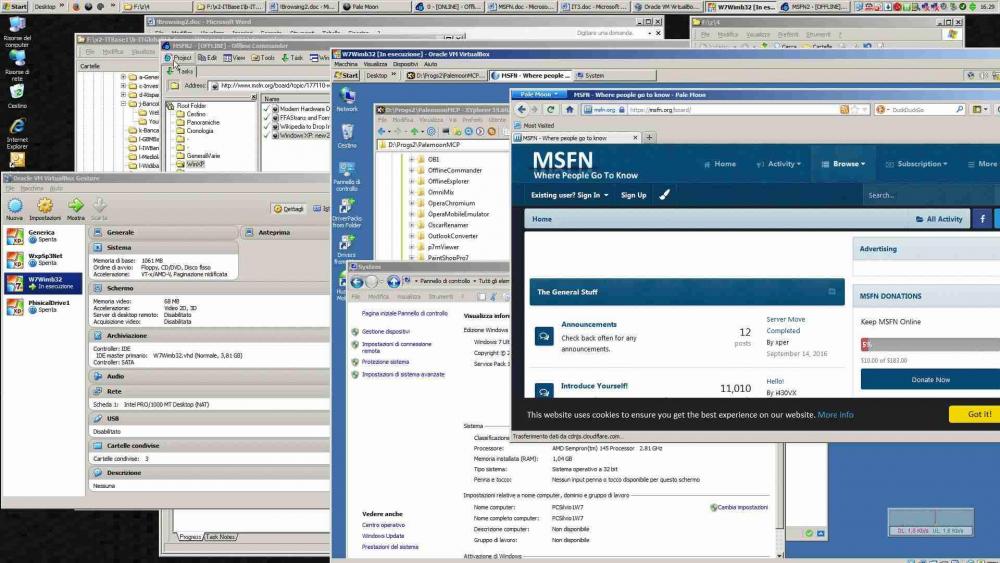
My English is elementary, I hope you can understand what I say; and for this reason I write very little in the forum. I report my experiences that I think are interesting for all WinXP users. In WinXP I start VirtualBox, and then a virtual machine and a 4GB .vhd file that contains a minimum Win7 Ultimate system; from within the virtual machine I launch for example Palemoon MPC and Firefox Quantum. The 4GB Win7 .vhd file was created using Wimb's instructions on the Reboot.pro and 911CD.net forums. I post a screenshot. An Android emulator can overcome other WinXP limitations (Whatsapp, Skype, App of the banks, ...); until now I have used a minimal Youwave system; soon I will test more powerful emulators compatible with WinXP; some references: Bluestacks and BlueStacks Tweaker https://www.bluestacks.com/ https://bstweaker.tk/ Nox App Player http://en.bignox.com/ MEMU https://www.memuplay.com/it/ Greetings
-
An ambiguous situation: - CertTrust.xml from Emet 5.2 is dated 15.03.04, and the rules expire on 16.08.01 - CertTrustUpd.xml by MicrosoftEasyFix51012.msi downloaded 16.01.15 is dated 15.09.02, however, the rules expire on 15.08.01 (that have already expired). Regards
-
EMET 4.1 updated pinned rules https://support.microsoft.com/en-us/kb/2961016#/en-us/kb/2961016 You can download MicrosoftEasyFix51012.msi, which is updated periodically; at 16.01.15 contains CertTrustUpd.xml updated to 15.09.02. It even works in WinXP. It requires Emet is in the default path, in WinXP is: "C:\Program Files\Emet 4.1\" I installed in C:\Program Files\Emet\, just create a temporary copy to "C:\ProgramFiles\Emet 4.1\", the patch does not modify files but only Windows registry. You can also start the program under Sandboxie, when it comes to the final screen close the program with sandboxie; in "%temp%\Fixit_51012\" are available both operational files: import.cmd and certTrustUpd.xml Regards ----- Italian version, my english is basic EMET aggionamenti periodici regole di convalida https://support.microsoft.com/en-us/kb/2961016#/en-us/kb/2961016 Si può prelevare MicrosoftEasyFix51012.msi, che viene aggiornato periodicamente; al 160115 la versione prelevata contiene CertTrustUpd.xml al 150902. Funziona anche in WinXP. Richiede che Emet sia presente nel percorso di default, in WinXP è: "C:\Programmi\Emet 4.1\" Io ho installato in C:\Programmi\Emet\, basta creare una copia temporanea in "C:\Programmi\Emet 4.1\", la patch non modifica i file ma solo i registri. Conviene anche avviare il programma sotto Sandboxie, quando arriva alla schermata finale chiudere la procedura con sandboxie; in "%Temp%\Fixit_51012\" sono disponibili i due file operativi: import.cmd e certTrustUpd.xml
-
Jaclaz, my english is basic, i'm non sure of automated translation. The suggested procedure can be useful for removing from the WinXP registers the POSReady hack, more conveniently than offline editing [HKEY_LOCAL_MACHINE\SYSTEM\WPA\PosReady] "Installed"=dword:00000001 ==> Edit to 0 1. Close all programs 2. Create a backup set of registry with ERUNT or Registry Backup 3. Start a registry editor, and load the SYSTEM hive from the backup set created in step 2 4. In the loaded hive, put the Installed DWORD value to 0 5. Unload the hive 6. Run the registry restore and restart WinXP Regards