Content Type
Profiles
Forums
Events
Everything posted by lmacri
-
Thanks to everyone for their browser suggestions. As superliew noted <above>, Mozilla has given Firefox ESR v115.x (the legacy version for Win 7 and 8.1) another last-minute reprieve and decided to extend support for this browser until March 2026 (see the official Firefox ESR release calendar at https://whattrainisitnow.com/release/?version=esr) so I'll be recommending my acquaintance stay with Firefox ESR v115.x, assuming uBlock Origin and other popular browser extensions continue to work with the FF v115.x branch for the next 6 months. Unfortunately, I haven’t seen any similar announcements about an extension for Mozilla’s Thunderbird ESR v115.x mail client for Win 7 and 8.1. AFAIK Thunderbird ESR v115.18.0 (rel. 24-Dec-2024) is still the final release for Thunderbird ESR 115. --------------- Dell Inspiron 15 5584 * 64-bit Win 10 Pro v22H2 build 19045.6218 * Firefox v142.0.1 * Microsoft Defender v4.18.25070.5-1.1.25070.4 * Malwarebytes Premium v5.3.8.212-140.0.5364 * Macrium Reflect Free v8.0.7783 * MS Outlook 2019
-
Can anyone suggest a secure browser and email client for an acquaintance who has a "plain vanilla" 64-bit Windows 8.1 machine? I am aware that Mozilla is ending support for the legacy FF ESR v115.x browser for Win 7 / Win 8.x in Sep 2025 and that FF ESR v115.27.0 (rel. 19-Aug-2025) will be the last FF browser released by Mozilla for these older OSs. I recommended they try r3dfox (a fork of modern Firefox) or Supermium (a fork of modern Chrome) but would appreciate knowing if someone has another suggestion for a supported browser that still runs on a Win 8.1 OS. I also recommended Thunderbird ESR for an email client, but I have no idea if Mozilla as made any similar announcements about dropping support for Thunderbird in the near future for Win 7 / Win 8.x OSs, or if there are other email clients that still support Win 8.1. ----------- Dell Inspiron 15 5584 * 64-bit Win 10 Pro v22H2 build 19045.6218 * Firefox v142.0.1 * Microsoft Defender v4.18.25070.5-1.1.25070.4 * Malwarebytes Premium v5.3.6.205-138.0.5346 * Macrium Reflect Free v8.0.7783 * MS Outlook 2019
-

Last versions of software for Windows Vista and Windows Server 2008
lmacri replied to WinClient5270's topic in Windows Vista
Hi WinClient5270: Just an FYI that Malwarebytes announced today that Malwarebytes v3.5.1 (the legacy edition for Win XP and Vista) has officially reached end-of-life. This EOL is effective immediately and there will be no further malware definition updates released for this legacy product. See employee jtodd234’s 08-Aug-2024 post in anon74’s Malwarebytes 3.5.1 not updating definitions… again in the Malwarebytes forum for more information.- 1,239 replies
-
- Server 2008
- software
-
(and 1 more)
Tagged with:
-

Last versions of software for Windows Vista and Windows Server 2008
lmacri replied to WinClient5270's topic in Windows Vista
Just a reminder that today (22-May-2024) is supposed to be the official EOL for all legacy Norton Security v22.15.x products for Win XP and Vista. I checked the Norton Security | Norton Internet Security | Norton AntiVirus board today and didn't see any new topics about this EOL, but if Norton follows through and stops pushing out malware definition updates it could be a week or so before v22.15.x users start seeing pop-up warnings in their system tray about out-of-date protection files.- 1,239 replies
-
- Server 2008
- software
-
(and 1 more)
Tagged with:
-

Last versions of software for Windows Vista and Windows Server 2008
lmacri replied to WinClient5270's topic in Windows Vista
NortonLifeLock has announced that they will stop supporting Norton Security v22.15.x products on Vista and other older OSs that do not support SHA-2 code signing as of 22-May-2024. See employee Gayathri_R's 01-Mar-2024 announcement End-of-Life announcement for Norton security software on Windows XP, Windows Vista, and Windows 7 (SP0) for more information. Note that Win 7 SP0 is Win 7 without Service Pack 1. NortonLifeLock threatened to end support for Norton Security v22.15.x a few years ago and reversed their decision after customers complained but I think they intend to stick to the 22-May-2024 end-of-life date this time.- 1,239 replies
-
2
-
- Server 2008
- software
-
(and 1 more)
Tagged with:
-

Windows Vista Update Repository (until April 2017+)
lmacri replied to greenhillmaniac's topic in Windows Vista
Hi trancer03: The GitHub home page for Dism++ at https://github.com/Chuyu-Team/Dism-Multi-language is currently offering v10.1.1002.2 (rel. 26-Mar-2023). I can't tell you if that new version posted yesterday still runs correctly on Vista machines but you might find some helpful hints in SIW2's 02-Dec-2021 instructions <here> in the VistaForums for using the previous v10.1.1002.1 of this tool. SIW2 suggested that you only apply ~ 30 updates at one time with Dism++, re-boot, apply the next 30 updates, and proceed this way until all available updates have been installed. -
Could someone confirm that the legacy Avast v18.8 antivirus products for Win XP and Vista (available for download from the July 2018 Avast announcement End of Support for Windows XP/Vista) are still getting regular virus definition updates? WinClient5270 recently updated their original post in Last Versions of Software for Windows Vista and Windows Server 2008 (most of the the antivirus programs listed there are also compatible with Win XP SP3) that would indicate that legacy Avast / AVG v18.8 products are still receiving virus definition updates, but I came across a recent post <here> in the AskWoody forum from a Win XP SP3 user who believes that their Avast Free Antivirus v18.8 is no longer working and is looking for a replacement. I believe they'd prefer to stay with Avast Free Antivirus if a clean reinstall would fix their problem, but I don't want to suggest this if virus definition updates for this legacy product have stopped.
-

Last versions of software for Windows Vista and Windows Server 2008
lmacri replied to WinClient5270's topic in Windows Vista
Hi AndrewSM36: Does Webroot Secure Anywhere v9.0.31.84 require any modification to a "plain vanilla" Vista SP2 OS patched to end of support on 11-Apr-2017 (i.e., does it run on OS Build 6.0.6002.x)? Your 25-Mar-2022 post in Best Windows Vista Anti-Virus regarding v9.0.29.62 states "i installed the sha2 updates, but i havent installed the extended kernel", so I'm guessing you installed the Windows Server 2008 updates KB4493730 (April 2019 Service Stack Update) and KB4474419 (Sept 2019 SHA-2 Code Signing Support) at some point in the past and currently have OS Build 6.0.6003.x.- 1,239 replies
-
- Server 2008
- software
-
(and 1 more)
Tagged with:
-

Forum registration with Hotmail account?
lmacri replied to ShaggyMoose's topic in Site & Forum Issues
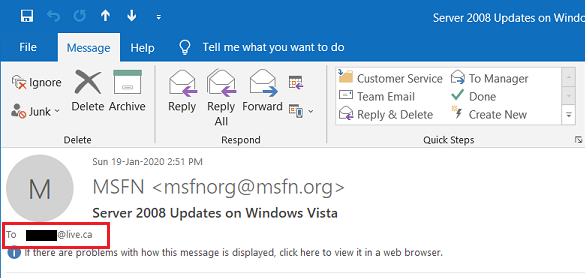
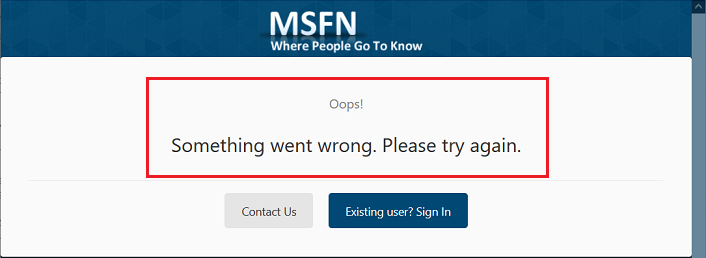
Hi Tripredacus: That can't be correct, because the image below shows an old notification email I received on 19-Jan-2020 that was automatically sent to my @live.ca email address. As I stated <above>, my email notifications from MSFN to this @live.ca email address stopped in Sep 2020 and there was nothing I could do to get them re-started (e.g., unsubscribing and then re-subscribing to threads I wanted to follow didn't work) so I had to change the email address in my MSFN account settings to an alternate email address provided by my ISP to get my email notifications working again. Now I can't change back to this @live.ca email address because the validation email to confirm this is a legitimate email address never arrives. I've checked everywhere I can think, including my Blocked Senders list on Outlook.com, and can't find any reason why emails sent by MSFN to this @live.ca address would be blocked on my end. EDIT: If I resend my confirmation email the message is "Oops! Something went wrong, Please try again". Doesn't that imply that the problem is on your end? -------------- 64-bit Win 10 Pro v21H2 build 19044.1889 * Firefox v104.0.0 * Microsoft Defender v4.18.2205.7-1.1.19500.2 * Malwarebytes Premium v4.5.13.208-1.0.1740 * Macrium Reflect Free v8.0.6867 * MS Outlook 2019 v2207 (Build 15427.20210) Dell Inspiron 15 5584, Intel i5-8265U CPU, 8 GB RAM, 256 GB Toshiba KBG40ZNS256G NVMe SSD, Intel UHD Graphics 620 -

Forum registration with Hotmail account?
lmacri replied to ShaggyMoose's topic in Site & Forum Issues
I am currently using the email address provided by my ISP in my MSFN account and would like to change it to the free email address provided by Microsoft (@live.ca) but I can't because the validation email to confirm my new email address never arrives in my MS Outlook 2019 inbox. I waited for about 20 min and tried re-sending the validation email but got an error stating "Oops! Something went wrong, Please try again". I have confirmed that the validation e-mails do not go my Junk Email folder, that msfn@msfn.org is in my Safe Senders list, and that no email address or domain associated with MSFN is in my Blocked Senders list. In order to sign into this forum again I had to change my email address back to the address provided by my ISP, and the validation email arrived as expected. I don't know if it's relevant, but when I originally registered on MSFN back in Feb 2019 I used that same Microsoft Outlook email address (@live.ca). In Sep 2020 I stopped receiving e-mail notifications when new replies were posted in topics that I was subscribed to, and changing my email address in my MSFN account settings to the alternate email address provided by my ISP got my email notifications working again. I first tried changing back to my free Microsoft Outlook email address in Mar 2021 but had the same problem described above where the validation email sent to that @live.ca email account never arrived. As of now I'm not sure if MSFN does not allow the use of any Microsoft (Hotmail/Outlook/Live) email address, or if I'm having problems because I tried to switch back to an @live.ca email address I had used previously to register on the MSFN forum (e.g., my Microsoft email address is on a list of previously used emails that are banned to prevent anyone from creating more than one MSFN account with the same email address). -------------- 64-bit Win 10 Pro v21H2 build 19044.1889 * Firefox v103.0.2 * Microsoft Defender v4.18.2205.7-1.1.19500.2 * Malwarebytes Premium v4.5.13.208-1.0.1740 * Macrium Reflect Free v8.0.6867 * MS Outlook 2019 v2207 (Build 15427.20210) Dell Inspiron 15 5584, Intel i5-8265U CPU, 8 GB RAM, 256 GB Toshiba KBG40ZNS256G NVMe SSD, Intel UHD Graphics 620 -
Hi coderun / D.Draker: Before this August 2019 thread is locked, just note that greenhillmaniac's 08-Aug-2020 post in their thread Windows Vista Update Repository (until April 2017+) has a link to their MEGA.nz repository of 32-bit and 64-bit Vista updates, and the link to that repository was still working when I checked today. Also see SIW2's 02-Dec-2021 instructions in post # 3186 of Vista ISO Download in the VistaForums for instructions for using the Dism++ utility to patch 32-bit and 64-bit Vista SP2 installations back to end of support (11-Apr-2017). I believe that Dism++ utility is still working even though Microsoft deactivated their Windows Update servers for Win XP and Vista on 03-Aug-2020. The last time I checked in December 2021 users performing a clean reinstall of Vista were still able to re-activate their license using the slui.exe 4 method in Step 2 / Option 2 of Brink's tutorial How to Activate Vista Normally and by Phone Activation in the VistaForums. D.Draker: Since you specifically mention Kaby Lake I'd suggest reading Will Vista Work on Kaby Lake? and Compatible Hardware with Windows Vista. I'm not certain but I recall reading that Vista will not run correctly on machines with 7th gen Kaby Lake processors.
-

Certifacte Trust Provider error installing updates
lmacri replied to mikey8811's topic in Windows Vista
Hi Boss: Thanks for letting us know that updating your trust certificates seems to have fixed you CAPI2 errors. There are multiple reasons why a .msu standalone installer will display that generic message - see the section titled "The update is not applicable to your computer" in the MS support article Windows Update Troubleshooting. The most common reasons are that the update is already installed (e.g., like your KB4015461), the update is no longer required because it was superseded (replaced) by a newer update that is already installed on your system, or you tried to install an update that doesn't match the architecture of your OS (e.g., you tried to run a 32-bit/x86 installer on a computer with a 64-bit OS). In most cases this message just means that the update isn't required for your system. -

Certifacte Trust Provider error installing updates
lmacri replied to mikey8811's topic in Windows Vista
Hi Boss: Try a slight variation of greenhillmaniac's suggestion <here>. Download the MicrosoftRootCertificateAuthority2011.cer file from http://go.microsoft.com/fwlink/?linkid=747875&clcid=0x409 and save it to the root C:\ directory of your computer (i.e., so the location is C:\MicrosoftRootCertificateAuthority2011.cer). Then open an elevated command prompt with Administrator rights (search for "Command Prompt" from the search box next to the Start button and choose Run as Administrator), and enter the command certutil -addstore "Root" "C:\MicrosoftRootCertificateAuthority2011.cer" (include the quotes) to apply the required trust certificate. Does KB4014984 (Security and Quality Rollup for NET. Framework 2.0, 3.0, 4.5.2, 4.6 on Windows Vista SP2 and Server 2008 SP2: April 11, 2017) install correctly after that trust certificate is applied? -
Hi winvispixp: You might be interested in reading ITMA's 14-Jan-2021 thread Security Software for Windows Vista? in the Norton forum. That thread offers suggestions for a few security programs with real-time protection that still receive regular virus definition updates and are compatible with Win XP and Vista, including the legacy Norton Security v22.15.x, the legacy Malwarebytes Premium v3.5.1, the legacy Avast/AVG Antivirus Free v18.8, the legacy Kaspersky v18.0/v19.0 (Free and paid products, v18.0 for older CPUs that do not support SSE2; v19.0 for Pentium III or newer CPUs that support SSE2), and Panda Security's current line of Panda Dome products. I don't believe the legacy Norton products or current Panda Dome products have been mentioned in this thread yet. As noted <here> in ITMA's thread, ESET is currently supporting Win XP and Vista, but that support will likely end on 15-Apr-2021 when their SHA-1 code signing certificates expire. Also note that when ITMA's thread started on 14-Jan-2021 Norton was originally planning to end support for Win XP and Vista on 28-Feb-2021, but the company reversed that decision (see Norton employee Gayathri_R's 08-Mar-2020 announcement Maintenance Mode for Windows XP, Windows Vista, and Windows 7 SP0 for Norton Security Software) and continues to support these older operating systems. I used Norton Security Deluxe v22.15.x for several years on my "plain vanilla" Vista SP2 machine (patched to Vista SP2 end of support, no Win Server 2008 updates or extended kernel) and was very happy with the protection it offered, but I switched to Malwarebytes Premium v3.5.1 a few years ago after I purchased a Win 10 laptop. Malwarebytes Premium v3.5.1 is a good choice for my Vista SP2 machine because I only use it on occasion as a test machine so it's rarely connected to the internet these days, and because I had a spare perpetual / lifetime license for Malwarebytes Premium (not available for purchase since 2014) that does not require me to pay an annual subscription. ---------- 32-bit Vista Home Premium SP2 * Firefox ESR v52.9.0 * Malwarebytes Premium v3.5.1-1.0.365 HP Pavilion dv6835ca, Intel Core2Duo T5550 @ 1.83 GHz CPU, 3 GB RAM, Western Digital Scorpio WD2500BEVS 256 GB SATA HD, NVIDIA GeForce 8400M GS
-

Last versions of software for Windows Vista and Windows Server 2008
lmacri replied to WinClient5270's topic in Windows Vista
Just an FYI that NortonLifeLock has reversed its decision and is planning to continue delivering SDS (virus) definitions and other protection updates to the legacy version of Norton Security v22.15.x for Win XP and Vista beyond 28-Feb-2021. See NortonLifeLock employee Gayathri_R's announcement today (08-Mar-2021) at Maintenance Mode for Windows XP, Windows Vista, and Windows 7 SP0 for Norton Security Software, which states in part: ---------- 32-bit Vista Home Premium SP2 * Firefox ESR v52.9.0 * Malwarebytes Premium v3.5.1-1.0.365 HP Pavilion dv6835ca, Intel Core2Duo T5550 @ 1.83 GHz, 3 GB RAM, NVIDIA GeForce 8400M GS- 1,239 replies
-
1
-
- Server 2008
- software
-
(and 1 more)
Tagged with:
-

Last versions of software for Windows Vista and Windows Server 2008
lmacri replied to WinClient5270's topic in Windows Vista
Hi Osman Kovan: Are you able to purchase songs and/or download previous purchases from the iTunes Store if you sign in to iTunes v12.1.3.6 with two-factor authentication? Candy Crush Saga is a free app in Apple's App Store so I'm wondering you can actually purchase a song from the iTunes Store and download it to your Vista SP2 computer when you log in to the iTunes Store with 2FA. ---------------- 32-bit Vista Home Premium SP2 * Firefox ESR v52.9.0 * Malwarebytes Premium v3.5.1-1.0.365 HP Pavilion dv6835ca, Intel Core2Duo T5550 @ 1.83 GHz, 256 GB WD SATA HDD, 3 GB RAM, NVIDIA GeForce 8400M GS- 1,239 replies
-
1
-
- Server 2008
- software
-
(and 1 more)
Tagged with:
-
Hi Boss: I suspect your 800B0109 is related to a known issue with KB4014984 (Security and Quality Rollup for NET. Framework 2.0, 3.0, 4.5.2, 4.6 on Windows Vista SP2 and Server 2008 SP2: April 11, 2017) that started around March 2020. The workaround below is posted in m#l's thread Updates not working, it has been searching for updates for hours in the MS Answers forum. Once the MicrosoftRootCertificateAuthority2011.cer file is applied you can download the .msu standalone installer from the Microsoft Update Catalog at https://www.catalog.update.microsoft.com/Search.aspx?q=vista KB4014984 (use the x86 installer for 32-bit Vista), save it to your desktop, and double-click to run the installer. The 24-Jun-2020 Microsoft support article Windows Update SHA-1 Based Endpoints Discontinued for Older Windows Devices that Vistapocalypse mentioned <above> notes that error 80244019 (The device cannot connect to Windows Update) is one of the expected errors Win XP and Vista users will see if they try to run Windows Updates after 03-Aug-2020. There's nothing you can do to fix this error and, as Vistapocalypse noted, adding Dalai's 4 or 5 "speed up" patches will no longer fix Windows Update. See the section titled ***** IMPORTANT NOTICE as of August 3, 2020 ***** in m#l's thread Updates not working, it has been searching for updates for hours in the MS Answers forum for further details. ---------- 32-bit Vista Home Premium SP2 * Firefox ESR v52.9.0 * Malwarebytes Premium v3.5.1-1.0.365 HP Pavilion dv6835ca, Intel Core2Duo T5550 @ 1.83 GHz, 3 GB RAM, NVIDIA GeForce 8400M GS
-
Hi terryindorset: I don't want to sound like a broken record, but if you haven't confirmed your Vista SP2 OS is patched to end of extended support (see my 23-Jul-2020 post <here>) then you should do so as soon as possible. User erpster4 reminded me today in the VistaForums thread Problem After Installing Updates Agent 7.6.7600.256 that as of 03-August-2020, Windows Update will stop working on older operating systems like Win XP SP3 and Vista SP2 that do not support Secure Hash Algorithm 2 (SHA-2) code signing and will likely throw a "Windows Could Not Search For New Updates" error 8024402C if you try to check for available updates after this date. If you applied all the required Vista service packs (SP1 and/or SP2) during your clean reinstall but did not patch Vista SP2 (including any installed MS .NET Frameworks, Internet Explorer 9, and other programs that normally receive updates via Windows Update) to the end of extended support on 11-Apr-2017 by following the instructions on on page 1 of m#l's thread Updates not working, it has been searching for updates for hours then this machine could encounter ongoing problems with poor system performance, server connection errors, etc. even though you've added TLS 1.2 support. ---------- 32-bit Vista Home Premium SP2 * Firefox ESR v52.9.0 * Malwarebytes Premium v3.5.1-1.0.365 HP Pavilion dv6835ca, Intel Core2Duo T5550 @ 1.83 GHz, 3 GB RAM, NVIDIA GeForce 8400M GS
-
Further to the 24-Jun-2020 Microsoft support article Windows Update SHA-1 Based Endpoints Discontinued for Older Windows Devices, could someone tell me which updates would have to be applied to a Vista SP2 OS to add SHA-2 code signing support? After reading the section in that support article titled How to Update Windows Devices to SHA-2 I'm guessing that adding the Windows Server 2008 SP2 updates KB4474419: SHA-2 code signing support update and KB4493730: WU Service Stack Updates are required but I'd just like to confirm. Also, would adding these Windows Server 2008 SP2 updates change the build of a Vista SP2 machine from 6.0.6002.x (Build 2) to 6.0.6003.x (Build 3) as discussed in the MS support article Build Number Changing to 6003 in Windows Server 2008. If a Vista SP2 user performs a clean reinstall of their OS after July 2020, does this mean that they will have to add SHA-2 support by manually applying these Windows Server 2008 SP2 updates first, and then apply the 4 or 5 required "speed up" patches recommended on page 1 of page 1 of m#l's thread Updates not working, it has been searching for updates for hours in the MS Answers forum before Windows Update will work correctly and patch their Vista SP2 system back to end of extended support (11-Apr-2017)? ---------- 32-bit Vista Home Premium SP2 * Firefox ESR v52.9.0 * Malwarebytes Premium v3.5.1-1.0.365 HP Pavilion dv6835ca, Intel Core2Duo T5550 @ 1.83 GHz, 3 GB RAM, NVIDIA GeForce 8400M GS
-
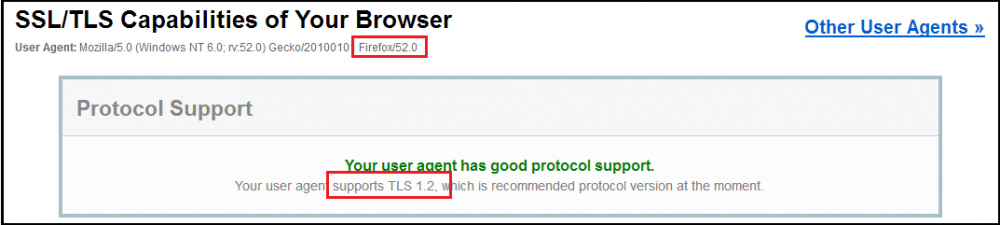
Hi jaclaz: Your assumptions about TLS 1.2 and Firefox ESR v52.9.0 (rel. 26-Jun-2018) are not what I observe on my own Vista SP2 machine. My Vista SP2 is patched to end of extended support on 11-Apr-2017 [i.e., I have not installed any Windows Server 2008 updates released after April 2017 like the KB4054565 (CredSSP remote code execution vulnerability in Windows Server 2008, Windows Embedded POSReady 2009, and Windows Embedded Standard 2009: March 13, 2018) recommended in John Haller's instructions <here>] and the image I posted <above> on 23-Jul-2020 shows my Firefox ESR browser supports TLS 1.2. As noted in that post, TLS 1.2 support has been enabled in Firefox since FF 27 was released in 2014 (i.e, security.tls.version.max was automatically set to a value of 3) as stated in the FF 27 release notes <here> and and far as I know, Vista SP2 users who use Firefox ESR v52.9.0 as their default browser should not have to make any changes in their advanced browser settings at about:config or install any OS patches released after end of support on 11-Apr-2017 to connect to secure https web sites that require the TLS 1.2 protocol. I believe John Haller's instructions allow Vista SP2 users to enable TLS 1.1 and TLS 1.2 support in their Internet Explorer 9. ---------- 32-bit Vista Home Premium SP2 * Firefox ESR v52.9.0 * Malwarebytes Premium v3.5.1-1.0.365 HP Pavilion dv6835ca, Intel Core2Duo T5550 @ 1.83 GHz, 3 GB RAM, NVIDIA GeForce 8400M GS
-
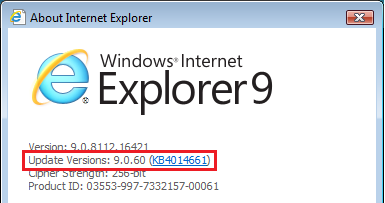
Hi terrryindorset: Further to my 23-Jul-2020 post <above>, what happens when you run a manual Windows Update (Step # 2) and is your IE9 browser Update Versions 9.0.60 / KB4014661 (Step # 3)? The image you posted in your VistaForums thread <here> appears to show that the last Vista security updates installed on 30-Jan-2018 have KB numbers like KB2535512 and KB2544893 which were actually released back in 2011, and indicates Windows Update isn't working correctly and still needs to be fixed so it can install your final six years of security updates to patch you back to end of support on 11-Apr-2017. I'd still suggest you follow the instructions on page 1 of m#l's thread Updates not working, it has been searching for updates for hours in the MS Answers forum and just confirm you have all the required "speed up" patches [e.g., KB3205638 (rel. 13-Dec-2016); KB4012583 (rel. 14-Mar-2017); KB4015380 (rel. 11-Apr-2017), etc.] and that you're fully patched to end of support before you add TLS 1.2 support to your IE9 browser. I also checked the system requirements <here> for Flight1's Instant Scenery 3 (IS3) for your MS Flight Simulator 2004 and it says "Windows 10 (may not install on other operating systems)". Did the tech support people at Flight1 specifically say that IS3 would run correctly on a Vista SP2 OS as long as you had an Internet Explorer browser that supports TLS 1.2, or would a Firefox ESR v52.9.0 browser with built-in TLS 1.2 support still meet their system requirements? Perhaps a downgrade to Instant Scenery 2 (IS2), which is compatible with XP/Vista/WIn 7, would solve your problem. ---------- 32-bit Vista Home Premium SP2 * Firefox ESR v52.9.0 * Malwarebytes Premium v3.5.1-1.0.365 HP Pavilion dv6835ca, Intel Core2Duo T5550 @ 1.83 GHz, 3 GB RAM, NVIDIA GeForce 8400M GS
-
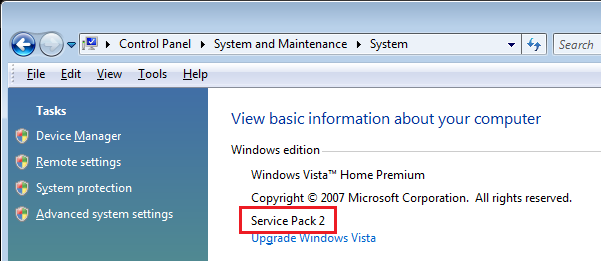
Hi terryindorset: Follow these steps to confirm your Vista SP2 OS is fully patched to end of extended support (11-Apr-2017): Go to Control Panel | System Information | System and confirm you have Service Pack 2 installed as shown below (as noted in FAQ How to Fix Vista SP2 "Checking for Updates..." Hangs and Slow Windows Updates, users performing a clean reinstall of the OS will not see the Windows Update hangs until after Service Pack 2 is applied). Run a manual Windows Update (Control Panel | System and Maintenance | Windows Update | Check for Updates). If you are patched to end of support (11-Apr-2017) Windows Update should run to completion in less than 5 or 10 minutes and report no updates are available. Launch your IE9 browser and go to Help | About Internet Explorer. If you are patched to end of support (11-Apr-2017) you should see that IE9 has Update Versions 9.0.60 / KB4014661 (Cumulative Security Update for Internet Explorer 9: April 11, 2017) as shown below. As jaclaz noted, if you are not patched to end of support and your background Windows Updates are hanging on "Checking for updates..." then standalone .msu installers will also get stuck and fail to run to completion until you fix your Windows Update problem. ---------- 32-bit Vista Home Premium SP2 * Firefox ESR v52.9.0 * Malwarebytes Premium v3.5.1-1.0.365 HP Pavilion dv6835ca, Intel Core2Duo T5550 @ 1.83 GHz, 3 GB RAM, NVIDIA GeForce 8400M GS
-
Hi terryindorset: Further to my previous post, are you the user TerryWallace who created the VistaForums thread Enable TLS 1.2 today? If so, the additional information you posted there about your OS reinstall and hanging updates sounds like you're affected by the problem described in the FAQ How to Fix Vista SP2 "Checking for Updates..." Hangs and Slow Windows Updates that's pinned at the top of the Windows Update board of that forum. That FAQ includes a link to instructions on page 1 of m#l's thread Updates not working, it has been searching for updates for hours in the MS Answers Vista board that should get your OS patched to the end of extended support (11-Apr-2017). ---------- 32-bit Vista Home Premium SP2 * Firefox ESR v52.9.0 * Malwarebytes Premium v3.5.1-1.0.365 HP Pavilion dv6835ca, Intel Core2Duo T5550 @ 1.83 GHz, 3 GB RAM, NVIDIA GeForce 8400M GS
-
Hi terryindorset: The SSL / TLS protocols your browser supports is specific to the browser you use and is not determined by the operating system. If you follow VistaLover's instructions you will add TLS 1.1 and TLS 1.2 support to your IE9 browser but it would not affect the protocols your Firefox browser supports. I believe Firefox has supported TLS 1.2 by default since Feb 2014 when Firefox 27 was released. If you use Firefox ESR v52.9.0 (the legacy version for Win XP/Vista available at https://archive.mozilla.org/pub/firefox/releases/52.9.0esr/win32/) then you should see something similar to the image below when you browse to the Qualys SSL Labs test page at https://www.ssllabs.com/ssltest/viewMyClient.html with your Firefox browser. I added TLS 1.3 support to my Firefox ESR v52.9.0 browser by changing security.tls.version.max to a value of 4 in the advanced browser settings. See Martin Brinkmann's June 2017 ghacks.net article How to Enable TLS 1.3 Support in Firefox and Chrome for instructions. ---------- 32-bit Vista Home Premium SP2 * Firefox ESR v52.9.0 * Malwarebytes Premium v3.5.1-1.0.365 HP Pavilion dv6835ca, Intel Core2Duo T5550 @ 1.83 GHz, 3 GB RAM, NVIDIA GeForce 8400M GS
-

Certifacte Trust Provider error installing updates
lmacri replied to mikey8811's topic in Windows Vista
Thank you for confirming. And just an FYI that I know of several Vista SP2 users performing a clean reinstall of their OS who have reported that your suggestion <here> to apply the MicrosoftRootCertificateAuthority2011.cer certificate file fixed the error 800B0109 ("A certificate chain processed, but terminated in a root certificate which is not trusted by the trust provider") that Windows Update now throws when it tries to install KB4014984 (Security and Quality Rollup for NET. Framework 2.0, 3.0, 4.5.2, 4.6 on Windows Vista SP2 and Server 2008 SP2: April 11, 2017). I decided to add a footnote to my instructions in the MS Answers thread Updates not working, it has been searching for updates for hours (where I post as user Great White North) in April 2020 and alert users to your solution since this problem installing KB4014984 has become so common.