
mixit
-
Posts
222 -
Joined
-
Days Won
10 -
Donations
0.00 USD
Content Type
Profiles
Forums
Events
Posts posted by mixit
-
-
57 minutes ago, roytam1 said:
yeah, MSO update of Office2003 seems fine, but not compatibility pack update.
MSO.DLL (12.0.6807.5000) in KB4092465 links to bcrypt.dll which is not exist in XP.
MSO.DLL (11.0.8453.0) in KB4462154 seems working fine.
Unless people are seeing issues, in this case the delay-load linkage to brcypt.dll.as such shouldn't be a problem, even in the original Office 2007 Compatibility Pack SP3 (KB2526297) MSO.DLL (12.0.6607.1000) has it. I thought the same thing you did at first, but going back and checking earlier versions seems reassuring.
1 -
On 2/7/2019 at 1:44 AM, capmo said:
Hi wyxchari, the link you posted above is no longer available. Could you please be kind enough to re-upload this file? I can't find the PTB version anywhere in the internet (besides Google, I've also tried the Wayback Machine and torrent sites). Muchas gracias!
Just look in the Brazilian folder instead of Portuguese. (Incidentally, this post was the very next one after the one you quoted
 )
1
)
1 -
3 hours ago, zipandlips said:
How to fix a problem with a sudden stop of the broadcast in youtube in all Palemoon assemblies from 27 to 28? You watch, watch the stream and somewhere after 30 minutes the video stops and freezes! You have to restart the stream and everything is restored!
You shouldn't need to restart the stream, just hitting the left arrow key and then the right arrow key should do it - this jumps you 5 seconds back and then 5 seconds forward to where you were before (in case some other page element has focus, you may need to click on the video first). It's still an annoyance, but much less disruptive this way.
 I pretty much do it on autopilot at this point, after years of practice courtesy of Mozilla.
I pretty much do it on autopilot at this point, after years of practice courtesy of Mozilla. 
This works at most other video sites as well. since most players bind these keys similarly.
1 -
@Dave-H
I'm still getting the 2017 version here. MS caches seem to be a crapshoot in terms of getting the latest certificate updates (for example I'm also still not getting the latest update @heinoganda notified us about). Not the first time this has happened, either. I wouldn't even be surprised if the version you downloaded manually just now was different than the one WU gets when it tries.I don't know about "exactly", but functionally, yes, for our purposes they should be the same. The automatic updater wouldn't know about your manual updates as the mechanism it uses is different (.sst vs .stl), and thus also its versioning. I don't think there's any checking being done against individual certificates being present or not.
0 -
1 hour ago, Dave-H said:
Thanks, yes I was aware of the option to disable the function, although it probably hadn't been specifically mentioned in the thread.
I was hoping to fix the problem though of course, rather than just working around it by disabling the function!
If it proves to be a function that fundamentally no longer works on XP, I will switch it off of course, but I haven't quite yet given up on finding a fix!
I guess I'm not sure why you think you still need this active if you're doing your updates separately anyway? You're already "working around" this functionality as is.
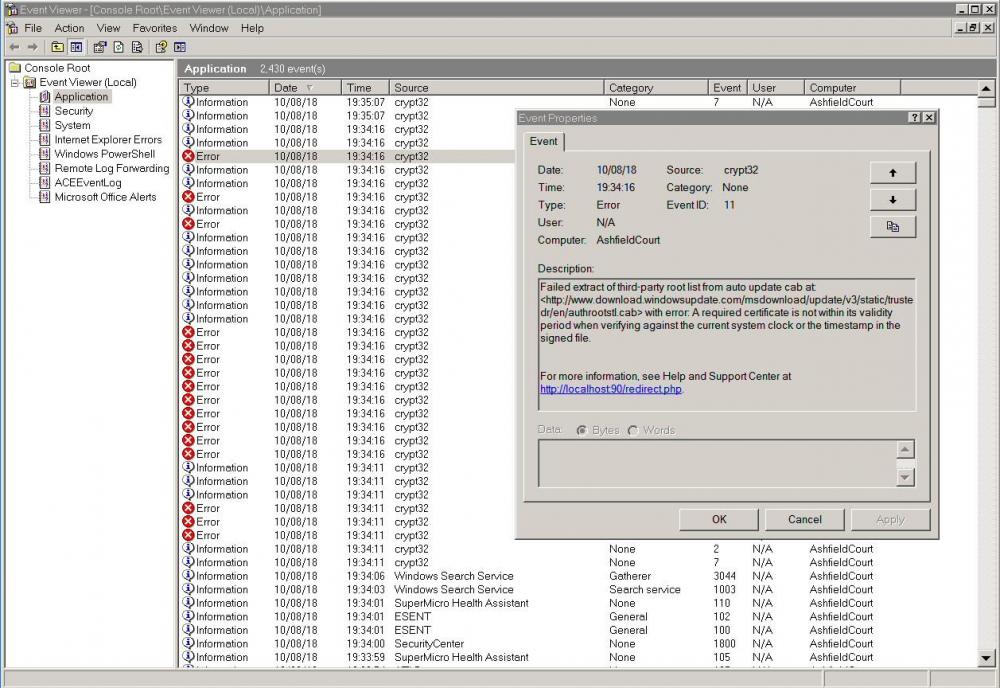
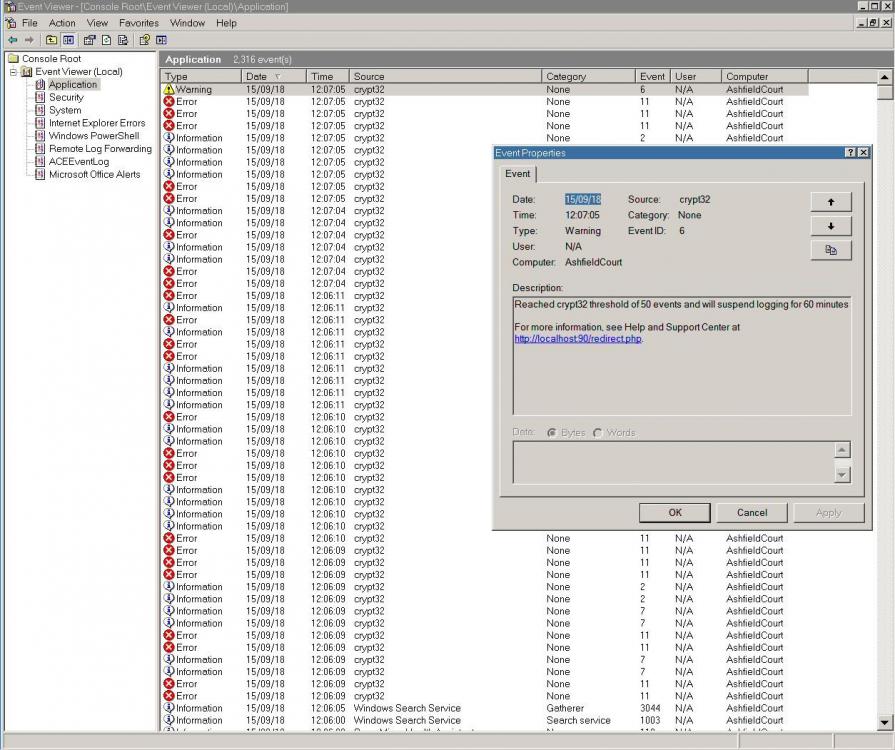
I think it was you who pointed out earlier in the thread that the current authroot.stl dates from 2017/9/22. Viewing its signature shows that the Microsoft Certificate Trust List Publisher certificate it's signed by was valid from 2017/1/25 to 2018/4/13. I'd venture a guess that this is when your errors started (can't tell by this thread as MSFN forum issues seem to have wiped out some of the posts). Until Microsoft updates this list, I believe you're always going to have the problem with the Event 11 certificate validity errors against your system clock:On 8/11/2018 at 3:18 AM, Dave-H said:0 -
On 9/15/2018 at 2:43 PM, Dave-H said:
@Dave-H
Since you seem to be getting Event 11 errors for crypt32, maybe you have the automatic Update Root Certificates component still active in your XP installation? It would seem quite odd for you to be getting lots of errors about not being able to extract certificates from a WU cab unless something was trying to update them. Given that you're updating manually (or via @heinoganda 's tool) anyway, you should probably turn it off even if that won't resolve the errors issue.- In Control Panel, run Add or Remove Programs.
- Click Add/Remove Windows Components in the left-hand column.
- Scroll all the way down to Update Root Certificates, clear the check box, click Next, and then complete the Windows Components Wizard.
Pardon me if this is old news to you. I tried checking back in this thread to see if this component was mentioned in connection with your problem and didn't find anything.
0 -
1 hour ago, muzungu said:
Since I'm using xp /pos updates with fat32 (working so well), I think I'm not concerned with th KB4056615 update (NTFS stuff)
In theory, yes - although you could potentially end up missing fixes for permissions not related to the file system (the registry, services, whatever else - can't say I'm an expert).
1 hour ago, muzungu said:Many said ALL intel cpus for 20 years except Atom (and some few others) are affected. Others said that core 2 duo are not affected. Intel offered microcode patch for linux, and in the list, there is core 2 duo. So... I'm confused. Core 2 duo : Affected or not?
@Destro will tell you in no uncertain terms that you're not affected if you have an FSB processor (those ex-KGB guys know how to protect their stuff;
 j/k, it means "front-side bus") - and indeed, Intel hasn't confirmed these CPUs are affected; then again, some proof-of-concept tests floating around appear to work on C2D (assuming the tests are implemented correctly). So, confusion continues...
j/k, it means "front-side bus") - and indeed, Intel hasn't confirmed these CPUs are affected; then again, some proof-of-concept tests floating around appear to work on C2D (assuming the tests are implemented correctly). So, confusion continues...  That microcode list, though, doesn't mean C2D is getting any updates at this point - it's cumulative and includes historical updates as well.
0
That microcode list, though, doesn't mean C2D is getting any updates at this point - it's cumulative and includes historical updates as well.
0 -
Well, It's certainly possible that the big guns don't always cover everything, I just figure they'd generally get more input because of how many users they have. I think you'd get the same result if you added the Mining Blocker rules to ABP. It's slow enough as is even without using another blocker on top of it (had to move to uBO myself for better speed, even though I prefer ABP's interface).
0 -
@wyxchari You are correct, domains and especially script file names can always be changed. And since Mining Blocker simply blocks the following sites:
'*://coinhive.com/lib*','*://coin-hive.com/lib*','*://cnhv.co/lib*','*://coinhive.com/captcha*','*://coin-hive.com/captcha*','*://cnhv.co/captcha*','*://*/miner.pr0gramm.com/*','*://miner.pr0gramm.com/*','*://*/coin-have.com/*','*://coin-have.com/*','*://*/hashforcash.us/*','*://hashforcash.us/*','*://*/hashforcash.com/*','*://hashforcash.com/*','*://*/coinerra.com/*','*://coinerra.com/*','*://*/pr0gramm.com/*','*://pr0gramm.com/*','*://minecrunch.co/web/*','*://mine-crunch.co/web/*','*://jsecoin.com/server*','*://*.jsecoin.com/server*','*://*.35.190.24.124.com/server*','*://load.jsecoin.com/*','*://*.load.jsecoin.com/*','*://server.jsecoin.com/*','*://*.server.jsecoin.com/*','*://static.reasedoper.pw/*','*://mataharirama.xyz/*','*://listat.biz/*','*://crypto-loot.com/lib*','*://cryptoloot.com/lib*','*://gus.host/*','*://*/gus.host/*','*://xbasfbno.info/*','*://*/xbasfbno.info/*','*://azvjudwr.info/*','*://*/azvjudwr.info/*','*://jyhfuqoh.info/*','*://*/jyhfuqoh.info/*','*://jroqvbvw.info/*','*://*/jroqvbvw.info/*','*://projectpoi.com/*','*://*/projectpoi.com/*','*://kdowqlpt.info/*','*://*/kdowqlpt.info/*','*://ppoi.org/*','*://*/ppoi.org/*','*://inwemo.com/*','*://*/inwemo.com/*','*://lmodr.biz/*','*://mine-my-traffic.com/*','*://minemytraffic.com/*','*://coinblind.com/lib/*','*://coinnebula.com/lib/*','*://coinlab.biz/*','*://deepc.cc/*','*://*/coinlab.biz/*','*://gridcash.net/*','*://*/gridcash.net/*','*://socketminer.com/*','*://*/socketminer.com/*','*://ad-miner.com/*','*://*/ad-miner.com/*','*://cloudcoins.co/*','*://*/cloudcoins.co/*','*://webmine.cz/*','*://*/webmine.cz/*','*://hashunited.com/*','*://*/hashunited.com/*','*://mineralt.io/*','*://*/mineralt.io/*','*://authedmine.com/*','*://*/authedmine.com/*','*://easyhash.io/*','*://*/easyhash.io/*','*://webminepool.com/*','*://*/webminepool.com/*','*://monerise.com/*','*://*/monerise.com/*','*://coinpirate.cf/*','*://*/coinpirate.cf/*','*://crypto-webminer.com/*','*://*/crypto-webminer.com/*','*://webmine.pro/*','*://*/webmine.pro/*','*://*/monad.network/*','*://monerominer.rocks/scripts/*','*://cdn.cloudcoins.co/javascript/*','*://minero.pw/miner.min.js*'
and any script URLs containing any of the following strings:
'CoinHive','Coin-Hive','jsecoin','mataharirama','minecrunch','coin-have','hashforcash','coinerra','reasedoper','minemytraffic','lmodr','cryptoloot','crypto-loot','listat','monero.worker','scrypt.worker','scrypt.asm','neoscrypt.asm','gus.host','xbasfbno','azvjudwr','jyhfuqoh','miner.pr0gramm','jroqvbvw','projectpoi','kdowqlpt','ppoi','minemytraffic','inwemo','minero','coinblind','coinnebula','coinlab','cloudcoins','deepc','monerominer','gridcash','monad','ad-miner','socketminer','cloudcoins','webmine','mineralt','authedmine','hashunited','webminepool','monerise','coinpirate','crypto-webminer','c-hive','cryptonight'
and any scripts containing:
'miner','CoinHive','Coin-Hive','Coin-Have','hashforcash','coinerra','jsecoin','mataharirama','minecrunch','reasedoper','minemytraffic','cryptoloot','crypto-loot','inwemo','minero','CoinBlind','coinnebula','minemytraffic','cryptonight','coinlab','cloudcoins','monerominer','deepMiner','gridcash','monad','ad-miner','socketminer','cloudcoins','webmine','mineralt','authedmine','webminepool','monerise','coinpirate','crypto-webminer','c-hive','CRLT.Anonymous','hashunited'
It would seem pretty easy to bypass it by renaming (also easy to get something useful blocked because of false positives).
Since Mining Blocker has only 7,898 installs versus 13,424,117 for Adblock Plus and 5,111,703 for uBlock Origin, I'd rather rely on blocker extensions with massive user base, because their blocklists are likely to be up to date more quickly.
 Also, with Mining Blocker you currently have to update the extension itself just to get an updated blocklist.
Also, with Mining Blocker you currently have to update the extension itself just to get an updated blocklist.  The only "feature" Mining Blocker has is that upon installation it attempts to stop any mining scripts already running - useful if for some reason you don't like to restart the browser.
The only "feature" Mining Blocker has is that upon installation it attempts to stop any mining scripts already running - useful if for some reason you don't like to restart the browser. 
(I looked at Mining Blocker because I was curious what interesting tricks they might use to detect mining scripts, not to be contrary with you.
 Based on these results, I'm afraid most of the "specialized" anti-mining extensions would similarly turn out to be not terribly useful subsets of full-blown adblocker functionality.)
0
Based on these results, I'm afraid most of the "specialized" anti-mining extensions would similarly turn out to be not terribly useful subsets of full-blown adblocker functionality.)
0 -
My observations
 :
:
- Your browser version doesn't really matter, all you need to get "You're protected" is somehow blocking coinhive.com and coin-hive.com.
- This can be done in any browser by running a regular adblocker like uBlock Origin, etc., I don't see much need for specialized addons.
- While raising awareness is commendable in itself, the cryptojackingtest.com site seems to be more about advertising Opera (specifically its built-in adblocker) than serious testing for cryptojacking protection. In my opinion, actually mining cryptocurrency on the site (instead of just checking if it could be done) is a pretty questionable move, even if they claim to donate the proceeds.
-
Edit: If Opera were the ones behind this site, I don't see why they'd register this domain anonymously - this is starting to look like a clever ruse to use people to mine a bit under the guise of an awareness campaign.Apparently the site is referenced in Opera's official blog so it should be legit. It's still weird that they'd use a domain privacy service instead of registering the domain with their official contact information.
1 -
@ThomasW
Without knowing the exact details of what has been changed in the browser, it's hard to say with 100% certainty that these fixes won't slow anything down. However, it seems very unlikely based on the overview given by Mozilla. Don't let the common word "time" confuse you, reducing the precision of time sources should in no way affect site loading times; and it's hard to imagine any legitimate scripts used by social media sites needing microsecond precision for anything, so they should be unaffected as well.As @Bersaglio said, don't worry about it (least of all on XP, which hasn't received slowdown-causing OS-level mitigations). Besides, ESR means no feature changes, so even in the very unlikely case of there being slowdowns, you can always go back to the previous point release without the risk of messing up your profile.
 1
1 -
(Apologies for the slew of quotes, I wanted to get the full context.)
5 hours ago, amberghaji said:here the list, 2371 CPUs affected.
5 hours ago, SD73 said:That is a pretty complete list. Where did you find it? I thought I was home free with my FSB processor, but it is on the list.
5 hours ago, amberghaji said:I find it here: https://downloadcenter.intel.com/download/27431/Linux-Processor-Microcode-Data-File
Microcodes updates released for Linux and maybe soon for Windows. All listed CPUs will receive microcodes but not all will be patched for Meltdown/spectre flaw. please read notes included in intel download.
4 hours ago, amberghaji said:According with this only the more recent CPUs will be patched for the flaws. check the list:
https://www.bleepingcomputer.com/news/security/intel-releases-linux-cpu-microcodes-to-fix-meltdown-and-spectre-bugs/#commentsSince 2013?
https://en.wikipedia.org/wiki/Intel_CoreIt sure would be nice to have a list like that for Meltdown/Spectre, but unfortunately the fact that a CPU is on this list doesn't mean that it's vulnerable to them, just that it has had a microcode update released for it. If you scroll down the downloadcenter.intel.com page and look at Other Versions on the left-hand side, you'll see that there have been many previous microcode releases dating from years before anyone knew about these vulnerabilities, It's a cumulative release and the list you posted simply reflects that, most of the updates included in it are from years ago. As you correctly stated in the end, only the more recent CPUs will be patched for these particular vulnerabilities.
EDIT: Just to be clear, I'm not getting on your case or anything.
 I myself also misunderstood at first what the list actually meant, because I was first directed to it from a site that flat out claimed this was a list specifically for Meltdown/Spectre...
1
I myself also misunderstood at first what the list actually meant, because I was first directed to it from a site that flat out claimed this was a list specifically for Meltdown/Spectre...
1 -
27 minutes ago, glnz said:
Second, - about the Meltdown+Spectre patches KB4056615 and KB4056941: do I even need them?
They are not Meltdown+Spectre patches - as things stand right now, those won't be coming to XP-based OSes at all. KB4056615 has seen some pretty serious issues that have been reported here (they don't happen to all installations - I personally have encountered no problems so far) , I haven't noticed any reports about problems with KB4056941 specifically.
EDIT: Unrelated, but important for Office 2000/XP/2003 users:
0 -
With the latest patches out this Tuesday, Microsoft has completely removed Equation Editor from all still supported Office versions, so it's a very good idea to also remove it from older Office versions ASAP. See the updated opening post for details.
0 -
39 minutes ago, Dave-H said:
So what exactly was it for then?

Surely you don't release an out of sequence update to fundamental system files which haven't been updated for ten years, like ntfs.sys, unless there's a very critical reason for doing so!
"An elevation of privilege vulnerability exists in the way that the Windows Kernel API enforces permissions." (marked as Important, but Exploitation Less Likely). Doesn't sound very Meltdownish to me. For whatever reason, they decided to release a whole bunch of Windows OS patches early. Take a look at the Server 2008 updates for instance, clearly things like Microsoft Color Management information disclosure vulnerability aren't related to Meltdown.
0 -
Time to stop worrying and love the bomb...? From Microsoft's official guidance Protect your Windows devices against Spectre and Meltdown (expand "My operating system (OS) is not listed. When can I expect a fix to be released?") (emphases in the quote added by me):
QuoteWe will not be issuing updates for Windows Vista or Windows XP-based systems including WES 2009 and POSReady 2009.
Although Windows Vista and Windows XP-based systems are affected products, Microsoft is not issuing an update for them because the comprehensive architectural changes required would jeopardize system stability and cause application compatibility problems. We recommend that security-conscious customers upgrade to a newer supported operating system to keep pace with the changing security threat landscape and benefit from the more robust protections that newer operating systems provide.
I think this should also settle the confusion some people seem to have over whether KB4056615 was supposed to be a Meltdown fix: it wasn't.
0 -
1 hour ago, Destro said:
I see a lot of people freaking out for zero reason. It irritates me so I am trying to educate.
I know what you mean, but until Intel can be bothered to make a definitive itemized list of all processors these problems apply to, 99.9% of the people are going to think Core 2 Duos are included in this, because people aren't going know that "2nd generation Intel® Core™ processors" are supposed to be the same i3/5/7 processors that were already mentioned before (that is, unless Intel has now started reinterpreting the meanings of their own jargon). They just see the word "Core" and assume that they're probably affected, especially with all the vague claims being circulated in the media about all x64 processors being affected, etc.
0 -
-
1 hour ago, Sampei.Nihira said:
SpecuCheck (link was in the post you quoted
 ).
Quote
).
QuoteIf you see the text:
Your system either does not have the appropriate patch, or it may not support the information class required
This indicates that your system is not currently patched to mitigate against these vulnerabilities.
0 -
3 hours ago, MaterSystem said:
I used TortoiseGit to access the Git Chromium repository and incidentally Kaspersky warned me of the security risk in the file:
...\src\third_party\WebKit\LayoutTests\images\resources\crbug702934.png
Exploit.Win32.CVE-2013-2977.a
- This is a deliberately tweaked test image for a bug in Chromium's PNGImageDecoder, that doesn't mean it's malicious.
- Even if it were malicious, CVE-2013-2977 applies to IBM Notes which you're unlikely to have installed.
- In other words, don't worry about it.
1 -
While I was was being cautious about suggesting /overwriteoem above, I think that if you guys have been applying POSReady updates so far without these kinds of "OEM driver" issues, it should be pretty safe to use it in this case. There have been a number of kernel updates already, so if all of those got applied on your systems without problems, it's rather unlikely that your current kernel files could still be OEM versions of some sort, so forcing the overwrite shouldn't be a problem. (I'd be more cautious if this were the first kernel update you've ever applied.)
I'd still feel more comfortable if I knew what actually causes this strange issue to begin with - my personal policy is not to suggest things to people unless I can be sufficiently certain they won't cause problems, and in this case the situation is somewhat vague.
0 -
Check C:\WINDOWS\KB4056615.log. If it contains messages like
c:\windows\system32\ntoskrnl.exe is in the list of oem drivers...skipping copy! c:\windows\system32\ntkrnlpa.exe is in the list of oem drivers...skipping copy!
you can try running the KB .exe file with the /overwriteoem switch.
This could have unwanted consequences, so only try it if you have everything backed up and feel confident you are capable of recovering your system if there are problems!
I've never used this switch on a physical installation (because I've never had this issue occur), only for kernel updates in the VirtualBox VM I use for POSReady updates testing before applying them on my actual PC. While I haven't seen any problems resulting in the VM, that doesn't necessarily mean this is always safe. So, please don't take this as the recommended course of action, just something you can try if you're feeling adventurous.
0 -
At this point it appears that KB4056615, despite being a kernel update, does not address the Meltdown/Spectre issue. At least neither the official Speculation Control Validation PowerShell script from Microsoft nor Alex Ionescu's SpecuCheck seem to think that it does anything to fix the problem. (To run the PS script on XP, refer to Wolferajd_fur's tip in the Q&A section. For the compiled SpecuCheck executable, you'll have to doctor the minimum OS version in the PE header.) Edit: Of course there's a possibility that these tools themselves don't work properly on XP, but I'd think the syptoms for that would look a bit different.
I looked at the Windows 7 Meltdown/Spectre patch (KB4056897), and it updates a huge number of major system components and drivers, not just the kernel and the NTFS driver. It seems we'll have to wait a bit longer to get a fix for XP.
0 -
10 hours ago, greenhillmaniac said:
Can anybody find the PT-PT version of the exFAT update for XP, KB955704, mentioned in this thread a few pages ago? I'm trying to build a repository of all updates for the NT5.x line of Oses in my native language, and I just can't find a working link for it... Here's the best I could find, from archive.org:
Go to Onepiece XP Post-SP3 AIO Update Pack FINAL at RyanVM. At the bottom of the first post, there is a list of mirrors. Most of the mirrors don't seem to have the original Microsoft issued updates used to build the pack, but currently the Mega.nz mirror (it's the goo.gl link right of the Dropbox one) does have them under the UpdatePack/Portuguese folder. You can probably get the other PTG updates you're still missing from there as well. (I'm not posting a direct link here because such repositories tend to be pretty volatile and I think it's more useful to know where to get the most current links.)
2



Instagram videos not working in Firefox 52 ESR?
in Browsers working on Older NT-Family OSes
Posted · Edited by mixit
You guys give up too easily, is this the infamous XP lair of fanatics or not!?
Fortunately there is (for time being, anyway) a pretty simple fix for this "video problem". (I use quotes because it has nothing to do with video as such.) You don't need to switch or recompile browsers either - at least not right now over this particular issue.
Apparently ESR 52.9 handles CSS flex layout a bit differently, so with the current Instagram code the video and its surroundding elements kindly get the height of 0 pixels... This can be fixed by modifying a surrounding <div> container to use block display instead of flex.
If you use uBlock Origin, you can add the following rule to your My filters:
(Just make sure Filterlists > Parse and enforce cosmetic filters is checked and that Settings > Default behavior > Disable cosmetic filtering is not checked or is overridden per-site for instagram.com.)
The same can presumably be done with other styling/tweaking extensions, only the syntax may be a little different. I don't use anything else, so can't give you the specifics.
If you don't use any such extensions and don't want to install them, you can just add the following CSS snippet to your userContent.css file (it's located in the chrome subdirectory under your Firefox profile folder. Edit: as @Dave-H pointed out, the file may not exist yet, in which case just create a new text file, put this stuff in it, and rename the file to userContent.css.)
(In this case you'll have to restart the browser for this to take effect, only refreshing the page won't make a difference.)
BTW, aside from div.ZyFrc[role="dialog"] , simply using div.ZyFrc or div[role="dialog"] also works. I'm just using the more specific condition to hopefully avoid accidentally breaking something else on Instagram (I'm not a frequent visitor there, so I wouldn't know). The mangled class name ZyFrc is pretty likely to change when they rebuild they code, and using the role-based version without a class name may survive that. Or it may not - as we know web devs need to constantly tweak their stuff, even when it's not broken... So this may need to be revisited.
Edit: Forgot to give kudos to @Mathwiz for narrowing down the problem and linking to this change list with hints to flex layout being the problem.
Edit 2: I tested this style fix on ESR 52.9.0, but I'd be surprised if 52.9.1 would be any different in this regard.
-----------------------
In other news, if you're spoofing a more current version of Firefox on all sites with ESR 52.9, apparently you'll have to drop your spoofed version below 57 on instagram starting today, because they seem to have switched over to Quantum-specific code for newer versions and basically nothing works anymore. (If you're using the default 52.9 user agent, you shouldn't need to make any changes because of this - at least it seems to work for me.) It could mean, though, that they'll be dropping support for anything pre-Quantum sooner rather than later, which may also affect the various Pale Moon derivatives, depending on how up-to-date their CSS and JS support is.