Content Type
Profiles
Forums
Events
Posts posted by D.Draker
-
-
16 hours ago, ED_Sln said:
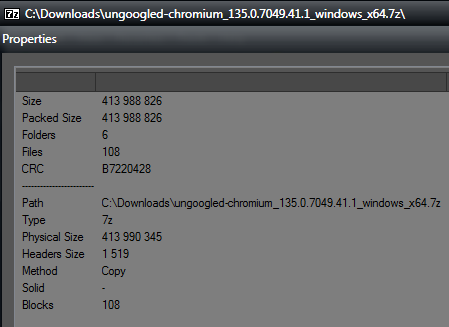
It looks like e3kskskskoy7wqk just unpacked chrome.7z from the installer, and there it is packed without compression. If I compress in 7zip (with ultra compression) the unpacked Chrome-bin folder, I got an archive size of only 101 MB for the 64 bit version of the browser.
He just used "Copy" method for the compression, it's of course bigger than "Ultra", the compression in this method is almost none. Why use 7z then? Makes no sense. Windows Zip would be a better and more logical choice in this case.
4 -
22 hours ago, NotHereToPlayGames said:
A compressed DLL would also make the program unusable on systems with disabled page files (not uncommon),
Wait, whaaaaat? How so? Elaborate pls.
4 -
11 hours ago, mjd79 said:
It seems that yes, chrome.dll is already 270mb....
Yeah, but 7z should *allegedly* compress the files, no?
And it looks like it simply fails.
5 -
13 hours ago, cc333 said:
That's strange. I've never had any trouble with sound on XP. All cards I've tried function as they should, and I could set 44.1kHz (or any other supported sample rate) easily. Of course, I've often used USB or Firewire (IEEE1394) audio interfaces with ASIO support for top sound quality, and they usually include decent drivers; in my experience, I've found that virtually all of the so-called "HD" sound systems built into most XP-era motherboards have stupidly bloated and half-broken drivers and often are hideously noisy and cheap sounding regardless of driver or Windows version (if anything, newer Windows versions with newer drivers sound worse as the already mediocre support the bad drivers have deteriorates further).
Perhaps your drivers weren't fully compatible or something was wrong with your sound card?
c
I used the drivers that came with the Xonar CD (which contained both Xp and Vista), but obviously not 11, hence I don't know and can't make judgements about 11.
At that time, I had just D1, but later upgraded to the more advanced Xonar D2, The sound on Vista was fantastic, on XP and 7, very similar to what we were listening in the 80's terrible cassette walkmans. or similar to the garbage mp3.
On Vista, I always choose 192Khz, of course not 44, and 44 is more like for partially deaf people, the ones who have nothing to lose in the terms of quality anyways.
I served in the artillery, my hearing is damaged, and even I hear the clear difference in favour of Vista.
3 -
@mjd79, the new 135 is 400mb in size, is this normal?
3 -
22 hours ago, mjd79 said:
also kernel33.dll in the files, which is the original kernel last modified by win32ss in December, 2022
So the last (real) kernel release was in 2022, I knew something fishy was going on, thanks for the warning!
5 -
Found it! This driver worked for that member, I don't remember, probably, and most likely I gave it.
3 -
22 hours ago, mjd79 said:
shell32.dll
Also, shell32.dll, is not needed at all? SHGetPropertyStoreForWindow replace with SHGetStockIconInfo, should be all. I wrote about it before.
Basically, all others can be replaced too, but in kernel32 you would have to re-implement the function which gets the info about your locale (or extensions won't work).
I could care less because I use the one and only English GB. But other languages, including the US dialect will fail to load, and you will see empty strings.
4 -
21 hours ago, mjd79 said:
ntdll.dll
Fantastic result, I had trust in you, I wrote earlier.
ntdll.dll, Why it's needed at all? NTDLL NtOpenKeyEx needs to replaced with just NtOpenKey, should be all, no?!
4 -
On 4/7/2025 at 2:08 AM, ED_Sln said:
No, he hasn't updated the Vista version.
Thank you! Do you know how to turn off the highlighting of inactive tabs when I hover over them?
3 -
On 4/7/2025 at 5:04 AM, Mark-XP said:
Thank you @D.Draker, neither driver worked unfortunately. The only ,advice' regarding that error ["I/O process stopped because of end of a thread" (in german: E/A Vorgang wegen Threadendes abgebrochen)] on the web was: new installation of XP. And that's not practical for me, because of 2 other OS's ,behind' XP, on several backup ssd's.
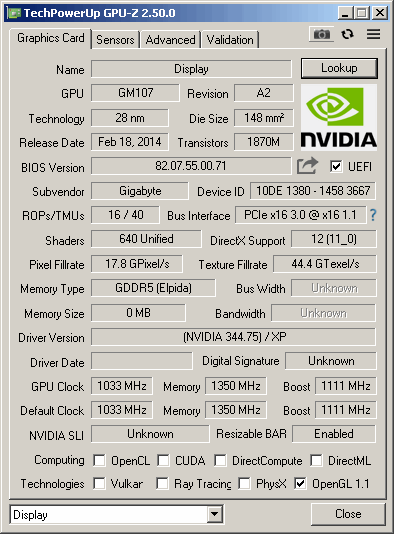
See below the GPU-Z info after the latest unsuccessful driver installation on XP/32 (SP3): There are problems regarding Bus Width, Memory Size an Bandwidh:
Mark, but this screenshot is from 344, not 347 I gave you earlier, I remembered, we had a user@UCyborg with an identical card, and it had no problems with XP.
I'll try to find the driver that worked for that user. Hold on.
4 -
On 4/3/2025 at 9:23 PM, Karla Sleutel said:
So far, no matter how many browsers I tried, only CatsXP has them partially disabled, it just sends empty strings, just like in @Dixel's hack, but the API works, Possibly Brave, too. @NotHereToPlayGames, you mentioned you use brave 134, could you check? Thanks
Brave
3 -
On 4/3/2025 at 3:09 PM, swaglord69 said:
I think my windows 8.1 pc died anyways sadly, so this might just be it for that system anyways. it just powers up but nothing more, keyboard isnt even doing stuff already. I will probably let it rest for a few weeks and then try again
Make a dedicated topic to help you diagnose the trouble.
3 -
@Mark-XP, did my 347 driver suggestion help? Need further assistance?
4 -
Blaukovitch inserts a unique identifier to its ported Chrome. What for? What Russia structures Blaukovitch really works for?
Blaukovitch had removed the standard X-Client-Data filed on HTML response header form and changed to F**KYOUGOOGLE
X-Client-Data, what it is.
https://gigazine.net/gsc_news/en/20200205-google-chrome-x-client-data/
More info on the matter.
"When a browser wishes to fetch a web page from a server, it sends an HTTP request for that page, a request that contains a set of headers, which are key-value pairs separated by colons. These headers describe data relevant to the request. For example, sending the header accept: text/html tells the browser what media types it will accept.
For years, since 2012 at least, Chrome has sent a header called X-client-data, formerly known as X-chrome-variations"
https://www.theregister.com/2020/02/05/google_chrome_id_numbers/
3 -
On 4/4/2025 at 7:06 PM, D.Draker said:
Before, you wrote you don't use CAPSLOCK, I already asked you. What changed? You parrot D.Draker?
Client Hints have more to do with tracking than "content based on device", content based on device works perfectly fine by using the standard UA.
To prove my point even further, a standard Android or iOS phone already includes the precise model in its UA. What else do they need!?!??!
Mozilla/5.0 (Linux; Android 13; SAMSUNG SM-A536B) AppleWebKit/537.36 (KHTML, like Gecko) SamsungBrowser/21.0 Chrome/110.0.5481.154 Mobile Safari/537.3
https://deviceatlas.com/blog/samsung-phones-user-agent-strings-list
Mozilla/5.0 (iPhone; CPU iPhone OS 15_1_1 like Mac OS X) AppleWebKit/605.1.15 (KHTML, like Gecko) Version/15.1 Mobile/15E148 Safari/605.1 NAVER(inapp; search; 1000; 11.8.10; 12PROMAX)
https://whatmyuseragent.com/platforms/ios/ios/15
3 -
-
A very good idea, but what to do with XP sound quality, which will still remain awful, cheaply sounding resampled 48Khz, very similar to mp3 128kb?
No matter how many pro grade sound cards I tried, all was terrible until NT6.0, and then got downhill with the release of Windows 7, going further donm with 8 and 10.
How's the sound in 11? My cards have no drivers for 11.
2 -
11 hours ago, D.Draker said:
In NTDLL NtOpenKeyEx needs to replaced with just NtOpenKey, it's even safer this way, why would they need the extended variant!?!
If it fails, don't give up, try NtCreateKey.
https://learn.microsoft.com/en-us/windows-hardware/drivers/ddi/wdm/nf-wdm-zwcreatekey
2 -
On 12/17/2024 at 8:19 AM, Nikolas said:
Thanks for the advice! I’ll try it out.
You're very welcome! Let us know the result, what finally worked for you. Thanks.
0 -
For lower OS in SHELL32
SHGetPropertyStoreForWindow replace with SHGetStockIconInfo
3 -
In NTDLL NtOpenKeyEx needs to replaced with just NtOpenKey, it's even safer this way, why would they need the extended variant!?!
3 -
10 hours ago, mjd79 said:
@D.Draker, I already know what break ungoogled Chromium 135 Chinese stundent on 7 SP0.
My trust in you has no bounds, I had no doubts you would find.
1 -
11 hours ago, mjd79 said:
Unfortunately, as you probably already saw in the relevant topic, it will not support Vista. I checked the version for 7 SP1 on 7 SP0 out of curiosity, the browser takes a suspiciously long time to start and I get a STATUS_BREAKPOINT error on every tab. I, unfortunately, do not have the skills or a sufficiently powerful computer to be able to compile his browser with the design that helped him maintain Vista compatibility, but perhaps there is a suitable person on the forum.
On 7 SP0 it is probably possible to solve this problem, I checked much older compilations of the Chinese student, and its run without this problem.
Yes, I saw, but with the already ported version 136 we could do just fine for about two years, as you see, Thorium and Supermium only started to completely fail after two years from the initial version 111 (which in my humble opinion they are based on). My PC also sucks by the modern day standards, its CPU is very similar to the severely outdated CPU used by NotHereToPlayGames.
2




The actual reason Windows 11 failed
in Windows 11
Posted · Edited by D.Draker
Thanks.
No, I have lots and lots of different hardware. Windows 7 sound is the worst, sandy, Win 8 is soooo soft, like Sony HiFi audio (if you remember the late 70s-80s, of course, you'll understand). XP isn't far away from 7, a bit punchier, but also over-bassy and flat (poor surround), like they smash you straight in the face. But if you listen to CDs with their 16bit primitivism and over-loaded, highly compressed to the "brick wall" audio, which totally suck in the first place, probably you won't notice.
Edit:
Read about loudness wars, and even if a CD is properly mastered, 16bit is still not enough. It's 60s tech.