taos
MemberContent Type
Profiles
Forums
Events
Everything posted by taos
-
Most of my machines are still running XP; but I now have two machines running win7, along with Roytam's Firefox-derived, XP-capable, 32bit browsers. I sooo enjoy being able to customize For New Moon 27 (Tycho) and New Moon 28 (UXP) you can see add-ons here: http://addons.palemoon.org/extensions/ For Serpent (UXP) you can see add-ons here: https://addons.basilisk-browser.org/extensions/ For me, these are now the best 'Firefox' versions... lol http://rtfreesoft.blogspot.com/
-
+1 This is a good way to test a scanner, and see if you like the program. The fully functioning download is free, but the output (jpg, tif, pdf) has watermarks. After purchasing, subsequent output is free of watermarks
-
My Browser Builds (Part 1)
taos replied to roytam1's topic in Browsers working on Older NT-Family OSes
Matt & Roytam, glad to see things are being worked out. You two are separated by thousands of miles, different cultures, and different languages. But you share in having great technical gifts, independent personalities, and a desire to enjoy your craft. Please keep your dialog going + 1 -
My Browser Builds (Part 1)
taos replied to roytam1's topic in Browsers working on Older NT-Family OSes
I run NM 27 and basilisk 55 on multiple machines. But I tweak the preferences and addons on a single machine, and then copy the profiles over to the other machines. I'm thinking about using the built-in password manager: Remember Passwords / Auto Fill In / Master Password I'm wondering if that will play nice and copy to the other machines, or if I'm going to run into problems. Any thoughts ? -
My Browser Builds (Part 1)
taos replied to roytam1's topic in Browsers working on Older NT-Family OSes
You are disrespectful and rude. Period. -
My Browser Builds (Part 1)
taos replied to roytam1's topic in Browsers working on Older NT-Family OSes
You can also bookmark this: http://rtfreesoft.blogspot.com/ That should work for you -
My Browser Builds (Part 1)
taos replied to roytam1's topic in Browsers working on Older NT-Family OSes
Thank you Mathwiz -
My Browser Builds (Part 1)
taos replied to roytam1's topic in Browsers working on Older NT-Family OSes
-
Yup ! This corporate modus operandi is terrible. And we must guard against updates from other corporations, too. Such as... here 'Back in 2016, printing giant HP sent a deceitful, malicious update to millions of OfficeJet and OfficeJet Pro printers that disguised itself as a "security update." Users who trusted HP and applied the update discovered to their chagrin that the update didn't improve their printers' security: rather, the updated printers had acquired the ability to reject cheaper ink, forcing the printer owners to throw away their third-party and refilled ink cartridges and buy new ones. Now, Epson has followed suit: in late 2016 or early 2017, Epson started sending deceptive updates to many of its printers. Just like HP, Epson disguised these updates as routine software improvements, when really they were poison pills, designed to downgrade printers so they could only work with Epson's expensive ink systems.'
-
erpdude8, thanks for your update on the updates
-
Thank you Radish . That's good info, and just the type that's needed to keep our updates to a minimum.
-
My Browser Builds (Part 1)
taos replied to roytam1's topic in Browsers working on Older NT-Family OSes
Thank you very much VistaLover. Some great info there. Perhaps it should be pinned. -
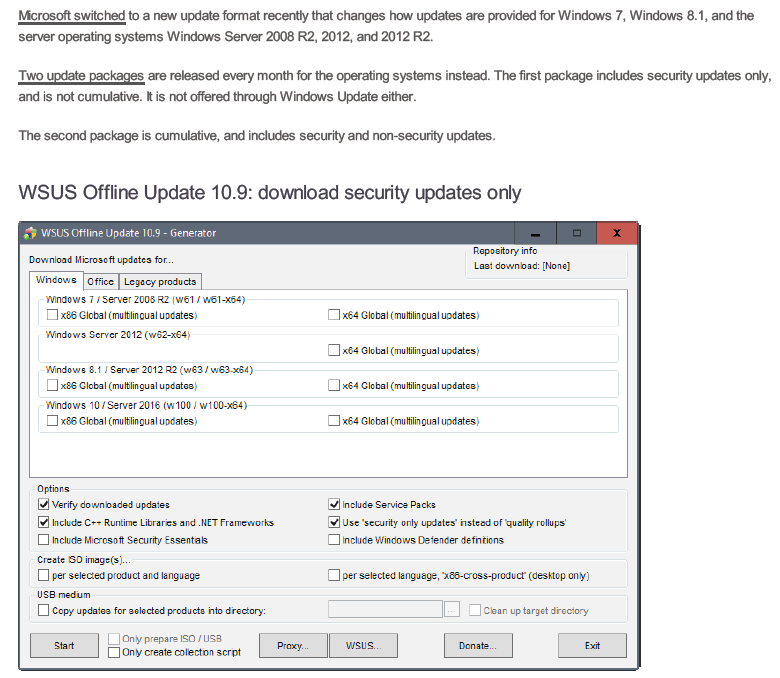
I've come across another freeware updater called WSUS Offline Update. http://download.wsusoffline.net/ Since version 10, it added the ability to download only security updates. Looks like it can also create an iso: But... a couple of people on their forum have said that MS has introduced unwanted updates by masquerading them as security updates.
-
Another vote for 'don't bother' Thanks, that makes sense.
-
a kindred spirit Yes, the advice has been good here. * * * * * * * * It took almost 3 hours to install the 2 update packages onto my test setup. 170 updates. Blind trust was necessary. All I see is the update label (security, hotfix, etc). I'm not given any meaningful information about them. I suppose I could look up each one individually and, perhaps, uninstall individually
-
Continuing with my test setup…. From the simplix blog site, I downloaded patch 18.6.15, ran it, and then ran the new 18.6.15 updater it created. I began with 178 updates (from simplix 17.12.15). The 18.6.15 updater scanned the system and determined I needed 7 new updates. After the install and restarts the new total was 170 updates. 3 of the 7 new updates didn't show up in the list. And 12 previous updates are now missing from the list. Is that normal behavior of simplix update process ? * * * * * Also downloaded InSpectre, release #8. Do I now look for Intel download for Ivy Bridge processor ?
-
Thank you Tripredacus. So you install Windows 7 SP1 and disable auto updates. I like that method, too :) I noticed that my Win7pro-sp1 disks can include varying amounts of additional updates: * Undated generic, ebay DVD contains two additional updates, kb976902 & kb2534111 * 2010-nov. Dell DVD contains one additional update, kb976902 * 2011-dec. Lenovo DVD contains kb976902, IE 9, and 42 more updates
-
Thank you for the simplix link alacran. I gave the simplix updater a test run on a spare disk. After I installed the OS, I went to installed updates, and there were only two listed. I then ran the simplix updater (17.12.15), which added 178 updates (it also removed one of my existing updates). The update process lasted almost two hours. It restarted itself 3 times, as it only seems to process 80 updates max per session. I'll see how it goes... Thanks again
-
I’ve been thinking about this for a few days. I’m doing fresh installs of win7pro-sp1 on three machines and have been wondering if I should bother with any updates. To begin with, I don’t use other MS products like Office, Defender, and Security Essentials, etc. Nor do I plan to upgrade to a newer OS. I also don't use Internet explorer. What I had in mind was only updates for OS security The lack of user-control and transparency with the MS update process really annoys me. From reading at the RyanVM & MDL sites, it seems that, in order to gain control over the update process, one must waste a good amount of valuable time identifying good and bad updates, and downloading 3rd party tools. So far I’ve been lucky with the many XPpro-sp3 setups (without further updates) that I’ve done for friends & family. In 12 years I’ve only had to reinstall OS on one machine. And that’s because the user was baited and clicked on some bad stuff. Looking at the wider picture I think what worries me more than hackers is MS. They’re the menace. They’re the ones who are actively taking away user control, actively trying to change BIOS to not accept legacy products, actively outdating existing hardware via updates, actively trying to upgrade OS to an unwanted product. It seems this is the sort of cat and mouse ‘game’ that one gets into when joining the MS update ‘game’ * * * * * * * * * * * * * EDIT ... Here's some of the proposals that have emerged in this thread: > Operate with only SP1, unless your software requires something more. > Stay current only with security updates, via WSUS offline update. > Load all updates through Dec 2017, via Simplex or WSUS offline update. > Minimalist approach, just 5 updates: KB3177467 KB3071756 KB3033929 KB4474419 KB4490628 > Install 2 essential patches to read future updates with new SHA-2 code signing, which will be implemented on August 13th, 2019 SHA-2 code signing support update for Windows Server 2008 R2 and Windows 7: March 12, 2019 KB4474419 Servicing stack update for Windows 7 SP1 and Windows Server 2008 R2 SP1: March 12, 2019 KB4490628 Thanks Radish
-
My Browser Builds (Part 1)
taos replied to roytam1's topic in Browsers working on Older NT-Family OSes
Very good. Thank you! -
My Browser Builds (Part 1)
taos replied to roytam1's topic in Browsers working on Older NT-Family OSes
Off-topic: Just discovered my 2-month old account got deleted in the midst of that server debacle. I'm re-registered and starting from scratch Is updating to the latest build as simple as emptying the folder content (in program files) and then inserting the content from the above (unzipped) folder? Also, are all the necessary 32bit LAV dlls included in the new builds, or do I have to re-install those?