Content Type
Profiles
Forums
Events
Posts posted by Dietmar
-
-
I make the same as yesterday: Just reserve 500 Bytes, adding space for a new .TXT
Dietmar
PS: No free space at all in .TEXT in original duser.dll
0 -
May be better to look for free space in .TEXT section in the original duser.dll ?
Dietmar
EDIT: I just look, in the .TEXT section is no free place.
0 -
First relocation in duser.dll works, but now asks me always for password,
I hit just enter and then I come to normal desktop.
May be, I put this duser.dll on fresh installed XP before last reboot, or any other idea?
Dietmar
0 -
Just now I make a try to have a duser.dll without any cmpxchg8b.
Dietmar
0 -
Is there a tool,
with which I can scan my whole XP SP3 installation for the opcode of "cmpxchg8b qword [ebp+0]" is "0F C7 4D 00"
Dietmar
Edit: I copy my whole MiniXP SP1 from 2007 on a complete with 00 everywhere filled USB stick.
Then I search the whole disk via this opcode with Winhex. It is found 12 +1 times, which means, that on the basic bootfiles,
only in ntoskrnl.exe and ntdll.dll cmpxchg8b qword [ebp+0] this code exists
Dietmar
EDIT: May be one time also in another file (+1), which I do not recognice until now.
Code 0F C7 4D 00 is in ntldr, but there not in a function, but in a data field?
0002D5F9 0F C7 4D 00
EDIT2: I use Notepad++ and search for ÇM . This gives the following list
ntdll.dll 5x
ntoskrnl.exe 7x (same for ntkrnlpa.exe but not used here for 1 cpu without any acpi).
duser.dll 2x
dpvoice.dll 2x
dpnsvr.exe 1x
dpnet.dll 5x
I think, it is a not so difficult task
Dietmar
0 -
All calls to such a relocated function use the new address, where I put it to.
This has the big advantage, that no extra jump at all has to be done,
keeps everything close as much as possible to the original.
Because I noticed, that XP wants to interpret 00 00 as opcode, now I always use 90 90 90..
Dietmar
0 -
Just now dirty ntoskrnl.exe with all functions in .DATA
 .
.
But here is last relocated function, works.
Now we have also NTDLL.DLL without any cmpxchg8b.
EDIT: But bad build ntoskrnl.exe works together with nice build NTDLL.DLL
 .
.
I just play Moorhuhn on that PC
Dietmar
NTDLL.DLL de for 486 cpu
53 55 8B E9 8B 1A 8B 4A 04 8B 54 24 0C 8B 02 8B 52 04 F0 0F B1 5D 00 75 F0 50 8B C2 F0 0F B1 4D 04 58 75 F5 5D 5B C2 04 00
.text:7C9C613C .text:7C9C613C ; =============== S U B R O U T I N E ======================================= .text:7C9C613C .text:7C9C613C .text:7C9C613C sub_7C9C613C proc near ; CODE XREF: sub_7C946DA9+105p .text:7C9C613C ; sub_7C94790B-6DDp ... .text:7C9C613C .text:7C9C613C arg_0 = dword ptr 4 .text:7C9C613C .text:7C9C613C push ebx .text:7C9C613D push ebp .text:7C9C613E mov ebp, ecx .text:7C9C6140 mov ebx, [edx] .text:7C9C6142 mov ecx, [edx+4] .text:7C9C6145 .text:7C9C6145 loc_7C9C6145: ; CODE XREF: sub_7C9C613C+17j .text:7C9C6145 mov edx, [esp+8+arg_0] .text:7C9C6149 mov eax, [edx] .text:7C9C614B mov edx, [edx+4] .text:7C9C614E lock cmpxchg [ebp+0], ebx .text:7C9C6153 jnz short loc_7C9C6145 .text:7C9C6155 .text:7C9C6155 loc_7C9C6155: ; CODE XREF: sub_7C9C613C+22j .text:7C9C6155 push eax .text:7C9C6156 mov eax, edx .text:7C9C6158 lock cmpxchg [ebp+4], ecx .text:7C9C615D pop eax .text:7C9C615E jnz short loc_7C9C6155 .text:7C9C6160 pop ebp .text:7C9C6161 pop ebx .text:7C9C6162 nop .text:7C9C6163 nop .text:7C9C6164 nop .text:7C9C6165 nop .text:7C9C6166 nop .text:7C9C6167 nop .text:7C9C6168 nop .text:7C9C6169 retn 4 .text:7C9C6169 sub_7C9C613C endp .text:7C9C6169 .text:7C9C6169 ; ---------------------------------------------------------------------------0 -
@pappyN4 Here a value 8 is returned, so C2 08 00
Dietmar
0 -
And next integrated, has no call at all, funny
 . Now, only one is left for to have also NTDLL.DLL without any cmpxchg8b
. Now, only one is left for to have also NTDLL.DLL without any cmpxchg8b
53 55 8B E9 8B DA 8B 55 04 8B 45 00 8B 4C 24 0C 89 01 8D 8A 00 00 01 00 03 4C 24 10 F0 0F B1 5D 00 75 F0 50 8B C2 F0 0F B1 4D 04 58 75 F5 5D 5B C2 08 000 -
And the next one integrated, works

53 55 8B E9 8B DA 8B 55 04 8B 45 00 89 03 8D 8A 01 00 01 00 F0 0F B1 5D 00 75 F1 50 8B C2 F0 0F B1 4D 04 58 75 F5 5D 5B C3
.text:7C9C609E .text:7C9C609E ; =============== S U B R O U T I N E ======================================= .text:7C9C609E .text:7C9C609E .text:7C9C609E sub_7C9C609E proc near ; CODE XREF: sub_7C920072+21p .text:7C9C609E ; RtlInterlockedPushEntrySList+Bp ... .text:7C9C609E push ebx .text:7C9C609F push ebp .text:7C9C60A0 mov ebp, ecx .text:7C9C60A2 mov ebx, edx .text:7C9C60A4 mov edx, [ebp+4] .text:7C9C60A7 mov eax, [ebp+0] .text:7C9C60AA .text:7C9C60AA loc_7C9C60AA: ; CODE XREF: sub_7C9C609E+19j .text:7C9C60AA mov [ebx], eax .text:7C9C60AC lea ecx, [edx+10001h] .text:7C9C60B2 lock cmpxchg [ebp+0], ebx .text:7C9C60B7 jnz short loc_7C9C60AA .text:7C9C60B9 .text:7C9C60B9 loc_7C9C60B9: ; CODE XREF: sub_7C9C609E+24j .text:7C9C60B9 push eax .text:7C9C60BA mov eax, edx .text:7C9C60BC lock cmpxchg [ebp+4], ecx .text:7C9C60C1 pop eax .text:7C9C60C2 jnz short loc_7C9C60B9 .text:7C9C60C4 pop ebp .text:7C9C60C5 pop ebx .text:7C9C60C6 nop .text:7C9C60C7 nop .text:7C9C60C8 nop .text:7C9C60C9 nop .text:7C9C60CA nop .text:7C9C60CB nop .text:7C9C60CC nop .text:7C9C60CD retn .text:7C9C60CD sub_7C9C609E endp .text:7C9C60CD .text:7C9C60CD ; ---------------------------------------------------------------------------1 -
I just integrate the Flush function in ntdll.dll, works

53 55 33 DB 8B E9 8B 55 04 8B 45 00 0B C0 74 17 8B CA 66 8B CB F0 0F B1 5D 00 75 F0 50 8B C2 F0 0F B1 4D 04 58 75 F5 5D 5B C3
.text:7C9C604F .text:7C9C604F ; =============== S U B R O U T I N E ======================================= .text:7C9C604F .text:7C9C604F .text:7C9C604F sub_7C9C604F proc near ; CODE XREF: RtlInterlockedFlushSList+8p .text:7C9C604F push ebx .text:7C9C6050 push ebp .text:7C9C6051 xor ebx, ebx .text:7C9C6053 mov ebp, ecx .text:7C9C6055 mov edx, [ebp+4] .text:7C9C6058 mov eax, [ebp+0] .text:7C9C605B .text:7C9C605B loc_7C9C605B: ; CODE XREF: sub_7C9C604F+1Aj .text:7C9C605B or eax, eax .text:7C9C605D jz short loc_7C9C6076 .text:7C9C605F mov ecx, edx .text:7C9C6061 mov cx, bx .text:7C9C6064 lock cmpxchg [ebp+0], ebx .text:7C9C6069 jnz short loc_7C9C605B .text:7C9C606B .text:7C9C606B loc_7C9C606B: ; CODE XREF: sub_7C9C604F+25j .text:7C9C606B push eax .text:7C9C606C mov eax, edx .text:7C9C606E lock cmpxchg [ebp+4], ecx .text:7C9C6073 pop eax .text:7C9C6074 jnz short loc_7C9C606B .text:7C9C6076 .text:7C9C6076 loc_7C9C6076: ; CODE XREF: sub_7C9C604F+Ej .text:7C9C6076 pop ebp .text:7C9C6077 pop ebx .text:7C9C6078 nop .text:7C9C6079 nop .text:7C9C607A nop .text:7C9C607B nop .text:7C9C607C nop .text:7C9C607D nop .text:7C9C607E retn .text:7C9C607E sub_7C9C604F endp .text:7C9C607E .text:7C9C607E ; ---------------------------------------------------------------------------0 -
@pappyN4 Yessssaaa


 I got it thanks to your help. The CRAZY function is ours^^..
I got it thanks to your help. The CRAZY function is ours^^..
Now, the Emulator is nearly perfect. I just delete Cli, Sti from it.
Now the Emulator of CMPXCHG8B is ready and can be used everywhere.
53 55 8B E9 8B 55 04 8B 45 00 0B C0 74 17 8D 4A FF 8B 18 F0 0F B1 5D 00 75 F0 50 8B C2 F0 0F B1 4D 04 58 75 F5 5D 5B C3
.text:7C9C6000 .text:7C9C6000 ; =============== S U B R O U T I N E ======================================= .text:7C9C6000 .text:7C9C6000 .text:7C9C6000 sub_7C9C6000 proc near ; CODE XREF: sub_7C9201D1+18p .text:7C9C6000 ; RtlInterlockedPopEntrySList+17p ... .text:7C9C6000 push ebx .text:7C9C6001 push ebp .text:7C9C6002 mov ebp, ecx .text:7C9C6004 mov edx, [ebp+4] .text:7C9C6007 mov eax, [ebp+0] .text:7C9C600A .text:7C9C600A loc_7C9C600A: ; CODE XREF: sub_7C9C6000+18j .text:7C9C600A or eax, eax .text:7C9C600C jz short loc_7C9C6025 .text:7C9C600E lea ecx, [edx-1] .text:7C9C6011 mov ebx, [eax] .text:7C9C6013 lock cmpxchg [ebp+0], ebx .text:7C9C6018 jnz short loc_7C9C600A .text:7C9C601A .text:7C9C601A loc_7C9C601A: ; CODE XREF: sub_7C9C6000+23j .text:7C9C601A push eax .text:7C9C601B mov eax, edx .text:7C9C601D lock cmpxchg [ebp+4], ecx .text:7C9C6022 pop eax .text:7C9C6023 jnz short loc_7C9C601A .text:7C9C6025 .text:7C9C6025 loc_7C9C6025: ; CODE XREF: sub_7C9C6000+Cj .text:7C9C6025 pop ebp .text:7C9C6026 pop ebx .text:7C9C6027 nop .text:7C9C6028 nop .text:7C9C6029 nop .text:7C9C602A nop .text:7C9C602B nop .text:7C9C602C nop .text:7C9C602D nop .text:7C9C602E nop .text:7C9C602F retn .text:7C9C602F sub_7C9C6000 endp .text:7C9C602F .text:7C9C602F ; ---------------------------------------------------------------------------0 -
But the Emulator for this crazy function, just now also with Cli, Sti is not good enough until now.
Here we have the log of Windbg
Dietmar
Break instruction exception - code 80000003 (first chance) nt!DbgBreakPoint: 804e3586 cc int 3 kd> g *** Unhandled exception 0xc0000096, hit in winlogon.exe: *** enter .exr 0006F964 for the exception record *** enter .cxr 0006F978 for the context *** then kb to get the faulting stack Break instruction exception - code 80000003 (first chance) NTDLL!`string'+0x12: 001b:7c91120e cc int 3 kd> .exr 0006F964 ExceptionAddress: 7c9c6002 (NTDLL!BaseStaticServerData <PERF> (NTDLL+0xb6002)) ExceptionCode: c0000096 ExceptionFlags: 00000000 NumberParameters: 0 kd> .cxr 0006F978 eax=7c95d8ec ebx=00000000 ecx=7c98c950 edx=00000000 esi=00000000 edi=00000000 eip=7c9c6002 esp=0006fc44 ebp=0006fc78 iopl=0 nv up ei pl zr na pe nc cs=001b ss=0023 ds=0023 es=0023 fs=003b gs=0000 efl=00010246 NTDLL!BaseStaticServerData <PERF> (NTDLL+0xb6002): 001b:7c9c6002 fa cli kd> kb *** Stack trace for last set context - .thread/.cxr resets it ChildEBP RetAddr Args to Child 0006fc78 7c943c6c 7c98c950 7c98b4a0 00000000 NTDLL!BaseStaticServerData <PERF> (NTDLL+0xb6002) 0006fc90 7c944676 7c885858 7c885854 00000000 NTDLL!_ValidateEH3RN+0x11e 0006fcb0 7c93dbde 7c885854 00000000 0006fce0 NTDLL!LdrpAccessResourceData+0x58 0006fcc0 7c82cbd2 7c885770 7c80b731 000725a4 NTDLL!RtlpGetAssemblyStorageMapRootLocation+0x1c8 WARNING: Frame IP not in any known module. Following frames may be wrong. 0006fd14 7c92b00a 7c91d04c 7c91e43f 00000000 0x7c82cbd2 0006fd18 7c91d04c 7c91e43f 00000000 00000001 NTDLL!LdrpInitializeProcess+0x136e 7c92b00a ffff9090 0000ffff f1580000 00007c94 NTDLL!RtlpCheckRelativeDrive+0x10a 7c92b012 f1580000 00007c94 f0f60000 f10c7c94 0xffff9090 7c92b016 00000000 f0f60000 f10c7c94 90907c94 0xf1580000 kd> !analyze -v Connected to Windows XP 2600 x86 compatible target at (Sat Apr 6 21:16:27.406 2024 (UTC + 2:00)), ptr64 FALSE Loading Kernel Symbols ............................................................... ................. Loading User Symbols ......................... Loading unloaded module list ...... ******************************************************************************* * * * Exception Analysis * * * ******************************************************************************* *** ERROR: Module load completed but symbols could not be loaded for winlogon.exe ************************************************************************* *** *** *** *** *** Either you specified an unqualified symbol, or your debugger *** *** doesn't have full symbol information. Unqualified symbol *** *** resolution is turned off by default. Please either specify a *** *** fully qualified symbol module!symbolname, or enable resolution *** *** of unqualified symbols by typing ".symopt- 100". Note that *** *** enabling unqualified symbol resolution with network symbol *** *** server shares in the symbol path may cause the debugger to *** *** appear to hang for long periods of time when an incorrect *** *** symbol name is typed or the network symbol server is down. *** *** *** *** For some commands to work properly, your symbol path *** *** must point to .pdb files that have full type information. *** *** *** *** Certain .pdb files (such as the public OS symbols) do not *** *** contain the required information. Contact the group that *** *** provided you with these symbols if you need this command to *** *** work. *** *** *** *** Type referenced: ULONG64 *** *** *** ************************************************************************* ************************************************************************* *** *** *** *** *** Either you specified an unqualified symbol, or your debugger *** *** doesn't have full symbol information. Unqualified symbol *** *** resolution is turned off by default. Please either specify a *** *** fully qualified symbol module!symbolname, or enable resolution *** *** of unqualified symbols by typing ".symopt- 100". Note that *** *** enabling unqualified symbol resolution with network symbol *** *** server shares in the symbol path may cause the debugger to *** *** appear to hang for long periods of time when an incorrect *** *** symbol name is typed or the network symbol server is down. *** *** *** *** For some commands to work properly, your symbol path *** *** must point to .pdb files that have full type information. *** *** *** *** Certain .pdb files (such as the public OS symbols) do not *** *** contain the required information. Contact the group that *** *** provided you with these symbols if you need this command to *** *** work. *** *** *** *** Type referenced: ULONG64 *** *** *** ************************************************************************* FAULTING_IP: ntdll!`string'+12 001b:7c91120e cc int 3 EXCEPTION_RECORD: 0006f964 -- (.exr 0x6f964) ExceptionAddress: 7c9c6002 (ntdll!BaseStaticServerData <PERF> (ntdll+0xb6002)) ExceptionCode: c0000096 ExceptionFlags: 00000000 NumberParameters: 0 CONTEXT: 0006f978 -- (.cxr 0x6f978;r) eax=7c95d8ec ebx=00000000 ecx=7c98c950 edx=00000000 esi=00000000 edi=00000000 eip=7c9c6002 esp=0006fc44 ebp=0006fc78 iopl=0 nv up ei pl zr na pe nc cs=001b ss=0023 ds=0023 es=0023 fs=003b gs=0000 efl=00010246 ntdll!BaseStaticServerData <PERF> (ntdll+0xb6002): 001b:7c9c6002 fa cli Last set context: eax=7c95d8ec ebx=00000000 ecx=7c98c950 edx=00000000 esi=00000000 edi=00000000 eip=7c9c6002 esp=0006fc44 ebp=0006fc78 iopl=0 nv up ei pl zr na pe nc cs=001b ss=0023 ds=0023 es=0023 fs=003b gs=0000 efl=00010246 ntdll!BaseStaticServerData <PERF> (ntdll+0xb6002): 001b:7c9c6002 fa cli Resetting default scope ERROR_CODE: (NTSTATUS) 0x80000003 - {AUSNAHME} Haltepunkt Im Quellprogramm wurde ein Haltepunkt erreicht. EXCEPTION_CODE: (HRESULT) 0x80000003 (2147483651) - Mindestens ein Argument ist ung ltig. EXCEPTION_PARAMETER1: 00000000 EXCEPTION_PARAMETER2: 7c975938 EXCEPTION_PARAMETER3: 00000028 NTGLOBALFLAG: 0 APPLICATION_VERIFIER_FLAGS: 0 APP: winlogon.exe ANALYSIS_VERSION: 6.3.9600.17237 (debuggers(dbg).140716-0327) x86fre DEFAULT_BUCKET_ID: STATUS_BREAKPOINT FAULTING_THREAD: 00000001 PRIMARY_PROBLEM_CLASS: STATUS_BREAKPOINT BUGCHECK_STR: APPLICATION_FAULT_STATUS_BREAKPOINT LAST_CONTROL_TRANSFER: from 7c943c6c to 7c9c6002 STACK_TEXT: 0006fc78 7c943c6c 7c98c950 7c98b4a0 00000000 ntdll!BaseStaticServerData <PERF> (ntdll+0xb6002) 0006fc90 7c944676 7c885858 7c885854 00000000 ntdll!_ValidateEH3RN+0x11e 0006fcb0 7c93dbde 7c885854 00000000 0006fce0 ntdll!LdrpAccessResourceData+0x58 0006fcc0 7c82cbd2 7c885770 7c80b731 000725a4 ntdll!RtlpGetAssemblyStorageMapRootLocation+0x1c8 0006fce0 7c82b26f 0006ff50 01031700 00000000 kernel32!BasepCreateDefaultTimerQueue+0x66 0006fce8 01031700 00000000 01030ed0 00000000 kernel32!SetTimerQueueTimer+0x19 WARNING: Stack unwind information not available. Following frames may be wrong. 0006ff50 0103e75e 01000000 00000000 000725a4 winlogon+0x31700 0006fff4 00000000 7ffdd000 000000c8 00000129 winlogon+0x3e75e FOLLOWUP_IP: winlogon+31700 001b:01031700 56 push esi SYMBOL_STACK_INDEX: 6 SYMBOL_NAME: winlogon+31700 FOLLOWUP_NAME: MachineOwner MODULE_NAME: winlogon IMAGE_NAME: winlogon.exe DEBUG_FLR_IMAGE_TIMESTAMP: 48027549 STACK_COMMAND: .cxr 0x6f978 ; kb FAILURE_BUCKET_ID: STATUS_BREAKPOINT_80000003_winlogon.exe!Unknown BUCKET_ID: APPLICATION_FAULT_STATUS_BREAKPOINT_winlogon+31700 ANALYSIS_SOURCE: KM FAILURE_ID_HASH_STRING: km:status_breakpoint_80000003_winlogon.exe!unknown FAILURE_ID_HASH: {f71cf305-2a12-4f5c-c480-6ae6676460a2} Followup: MachineOwner ---------
0 -
First I put the whole crazy function to this place and 90 90.. out her old place.
And voila, this relocation works, just until now with the original function
 ,
,
Dietmar
.text:7C9C6000 .text:7C9C6000 ; =============== S U B R O U T I N E ======================================= .text:7C9C6000 .text:7C9C6000 .text:7C9C6000 sub_7C9C6000 proc near ; CODE XREF: sub_7C9201D1+18p .text:7C9C6000 ; RtlInterlockedPopEntrySList+17p ... .text:7C9C6000 push ebx .text:7C9C6001 push ebp .text:7C9C6002 mov ebp, ecx .text:7C9C6004 mov edx, [ebp+4] .text:7C9C6007 mov eax, [ebp+0] .text:7C9C600A .text:7C9C600A loc_7C9C600A: ; CODE XREF: sub_7C9C6000+18j .text:7C9C600A or eax, eax .text:7C9C600C jz short loc_7C9C601A .text:7C9C600E lea ecx, [edx-1] .text:7C9C6011 mov ebx, [eax] .text:7C9C6013 lock cmpxchg8b qword ptr [ebp+0] .text:7C9C6018 jnz short loc_7C9C600A .text:7C9C601A .text:7C9C601A loc_7C9C601A: ; CODE XREF: sub_7C9C6000+Cj .text:7C9C601A pop ebp .text:7C9C601B pop ebx .text:7C9C601C nop .text:7C9C601D nop .text:7C9C601E nop .text:7C9C601F retn .text:7C9C601F sub_7C9C6000 endp .text:7C9C601F .text:7C9C601F ; ---------------------------------------------------------------------------1 -
I make a new try with your idea. Because in NTDLL.DLL appears 5 times cmpxchg8b,
I reserve 64 Byte for each of their modd. So, the 512 Byte are enough.
For to understand everything, I use in the beginning the original ntoskrnl.exe.
And I try to emulate first only one function in NTDLL.DLL, only the part of RtlInterlockedPopEntrySList with cmpxchg8b,
.text:7C912A8C sub_7C912A8C proc near.
This is the most crazy function, when this is done, the rest is easy
Dietmar
1 -
I found out, that this Emulation fails for the crazy function. When I add Cli and Sti, winlogon fails on Cli.
Everything with relocation works now for me.
Emulation of RtlInterlockedPopEntrySList crashes winlogon.exe, I can see the mouse pointer
Dietmar
EDIT: With ntdll!RtlpInterlockedFlushSList is all correct, it is here shown, because I changed places with ntdll!RtlInterlockedPopEntrySList , so Windbg shows wrong message.
*** An Access Violation occurred in winlogon.exe: The instruction at 00000000 tried to read from a NULL pointer *** enter .exr 0006F964 for the exception record *** enter .cxr 0006F980 for the context *** then kb to get the faulting stack Break instruction exception - code 80000003 (first chance) NTDLL!DbgBreakPoint: 001b:7c91120e cc int 3 kd> .exr 0006F964 ExceptionAddress: 00000000 ExceptionCode: c0000005 (Access violation) ExceptionFlags: 00000000 NumberParameters: 2 Parameter[0]: 00000000 Parameter[1]: 00000000 Attempt to read from address 00000000 kd> cxr 0006F980 Couldn't resolve error at 'xr 0006F980' kd> kb ChildEBP RetAddr Args to Child 0006f568 7c9752ae 00000000 7c885780 010304fd NTDLL!DbgBreakPoint 0006f5a8 7c9759c1 0006f870 7c9759c6 0006f828 NTDLL!RtlUnhandledExceptionFilter2+0x27b 0006f5b8 7c864031 0006f870 c0000005 00261e90 NTDLL!RtlUnhandledExceptionFilter+0x12 WARNING: Frame IP not in any known module. Following frames may be wrong. 0006f878 7c9132a8 0006f964 0006ffe4 0006f980 0x7c864031 0006f89c 7c91327a 0006f964 0006ffe4 0006f980 NTDLL!ExecuteHandler2+0x26 0006f94c 7c91e46a 00000000 0006f980 0006f964 NTDLL!ExecuteHandler+0x24 0006f94c 00000000 00000000 0006f980 0006f964 NTDLL!KiUserExceptionDispatcher+0xe 0006fc48 7c943c9f 7c98b4a0 00000000 00000000 0x0 7c98c950 00000000 00000000 00000000 00000000 NTDLL!RtlInterlockedPopEntrySList+0x1c kd> !analyze -v Connected to Windows XP 2600 x86 compatible target at (Sat Apr 6 17:06:47.531 2024 (UTC + 2:00)), ptr64 FALSE Loading Kernel Symbols ............................................................... ................. Loading User Symbols ......................... Loading unloaded module list ...... ******************************************************************************* * * * Exception Analysis * * * ******************************************************************************* *** ERROR: Module load completed but symbols could not be loaded for winlogon.exe ************************************************************************* *** *** *** *** *** Either you specified an unqualified symbol, or your debugger *** *** doesn't have full symbol information. Unqualified symbol *** *** resolution is turned off by default. Please either specify a *** *** fully qualified symbol module!symbolname, or enable resolution *** *** of unqualified symbols by typing ".symopt- 100". Note that *** *** enabling unqualified symbol resolution with network symbol *** *** server shares in the symbol path may cause the debugger to *** *** appear to hang for long periods of time when an incorrect *** *** symbol name is typed or the network symbol server is down. *** *** *** *** For some commands to work properly, your symbol path *** *** must point to .pdb files that have full type information. *** *** *** *** Certain .pdb files (such as the public OS symbols) do not *** *** contain the required information. Contact the group that *** *** provided you with these symbols if you need this command to *** *** work. *** *** *** *** Type referenced: ULONG64 *** *** *** ************************************************************************* ************************************************************************* *** *** *** *** *** Either you specified an unqualified symbol, or your debugger *** *** doesn't have full symbol information. Unqualified symbol *** *** resolution is turned off by default. Please either specify a *** *** fully qualified symbol module!symbolname, or enable resolution *** *** of unqualified symbols by typing ".symopt- 100". Note that *** *** enabling unqualified symbol resolution with network symbol *** *** server shares in the symbol path may cause the debugger to *** *** appear to hang for long periods of time when an incorrect *** *** symbol name is typed or the network symbol server is down. *** *** *** *** For some commands to work properly, your symbol path *** *** must point to .pdb files that have full type information. *** *** *** *** Certain .pdb files (such as the public OS symbols) do not *** *** contain the required information. Contact the group that *** *** provided you with these symbols if you need this command to *** *** work. *** *** *** *** Type referenced: ULONG64 *** *** *** ************************************************************************* FAULTING_IP: +368b8e80368b908 001b:00000000 ?? ??? EXCEPTION_RECORD: 0006f964 -- (.exr 0x6f964) .exr 0x6f964 ExceptionAddress: 00000000 ExceptionCode: c0000005 (Access violation) ExceptionFlags: 00000000 NumberParameters: 2 Parameter[0]: 00000000 Parameter[1]: 00000000 Attempt to read from address 00000000 CONTEXT: 0006f980 -- (.cxr 0x6f980;r) .cxr 0x6f980;r eax=00000000 ebx=0006fc78 ecx=7c98c950 edx=00000000 esi=00000000 edi=00000000 eip=00000000 esp=0006fc4c ebp=7c98c950 iopl=0 nv up ei pl zr na pe nc cs=001b ss=0023 ds=0023 es=0023 fs=003b gs=0000 efl=00010246 001b:00000000 ?? ??? Last set context: eax=00000000 ebx=0006fc78 ecx=7c98c950 edx=00000000 esi=00000000 edi=00000000 eip=00000000 esp=0006fc4c ebp=7c98c950 iopl=0 nv up ei pl zr na pe nc cs=001b ss=0023 ds=0023 es=0023 fs=003b gs=0000 efl=00010246 001b:00000000 ?? ??? .cxr Resetting default scope ERROR_CODE: (NTSTATUS) 0x80000003 - {AUSNAHME} Haltepunkt Im Quellprogramm wurde ein Haltepunkt erreicht. EXCEPTION_CODE: (HRESULT) 0x80000003 (2147483651) - Mindestens ein Argument ist ung ltig. EXCEPTION_PARAMETER1: 00000000 EXCEPTION_PARAMETER2: 7c975938 EXCEPTION_PARAMETER3: 00000028 NTGLOBALFLAG: 0 APPLICATION_VERIFIER_FLAGS: 0 CHKIMG_EXTENSION: !chkimg -lo 50 -d !ntdll !chkimg -lo 50 -d !ntdll 7c912a6e-7c912a6f 2 bytes - ntdll!RtlpInterlockedFlushSList+2 [ 33 db:8b e9 ] 7c912a71-7c912a9e 46 bytes - ntdll!RtlpInterlockedFlushSList+5 (+0x03) [ e9 8b 55 04 8b 45 00 0b:55 04 8b 45 00 0b c0 74 ] 7c912aa0-7c912aa4 5 bytes - ntdll!ExpInterlockedPopEntrySListEnd+1 (+0x2f) [ 0f c7 4d 00 75:90 90 90 90 90 ] 7c912aa6-7c912aaf 10 bytes - ntdll!ExpInterlockedPopEntrySListEnd+7 (+0x06) [ 5d 5b c3 8d 49 00 8f 04:90 90 90 90 90 90 90 90 ] 7c913420-7c913421 2 bytes - ntdll!$$VProc_ImageExportDirectory+20 (+0x97a) [ b4 48:fa 52 ] 7c913424-7c913425 2 bytes - ntdll!$$VProc_ImageExportDirectory+24 (+0x04) [ 40 5d:b4 48 ] 7c913e64-7c913e66 3 bytes - ntdll!$$VProc_ImageExportDirectory+a64 (+0xa40) [ b5 2e 06:6c ba 07 ] 7c916000-7c916011 18 bytes - ntdll!$$VProc_ImageExportDirectory+2c00 (+0x219c) [ 67 01 68 01 69 01 6a 01:00 00 ff ae 00 00 1b af ] 7c916013-7c9160a9 151 bytes - ntdll!$$VProc_ImageExportDirectory+2c13 (+0x13) [ 01 71 01 72 01 73 01 74:af 00 00 93 af 00 00 ad ] 7c9160ab-7c9160b0 6 bytes - ntdll!$$VProc_ImageExportDirectory+2cab (+0x98) [ 01 bc 01 bd 01 01:b2 00 00 c7 b2 00 ] 7c9160b2-7c9160bc 11 bytes - ntdll!$$VProc_ImageExportDirectory+2cb2 (+0x07) [ be 01 bf 01 c0 01 c1 01:d5 b2 00 00 f1 b2 00 00 ] 7c9160be-7c916137 122 bytes - ntdll!$$VProc_ImageExportDirectory+2cbe (+0x0c) [ c3 01 c4 01 c5 01 c6 01:1e b3 00 00 3a b3 00 00 ] 7c916139-7c91625c 292 bytes - ntdll!$$VProc_ImageExportDirectory+2d39 (+0x7b) [ 02 01 02 02 02 03 02 04:00 fd b5 00 00 15 b6 00 ] 7c91625e-7c9163c0 355 bytes - ntdll!$$VProc_ImageExportDirectory+2e5e (+0x125) [ 92 02 93 02 94 02 95 02:20 bb 00 00 3c bb 00 00 ] 7c9163c2-7c9163c5 4 bytes - ntdll!$$VProc_ImageExportDirectory+2fc2 (+0x164) [ 05 00 44 03:2c c2 00 00 ] 7c9163c7-7c916441 123 bytes - ntdll!$$VProc_ImageExportDirectory+2fc7 (+0x05) [ 03 45 03 46 03 47 03 48:c2 00 00 53 c2 00 00 68 ] 7c916443-7c91653f 253 bytes - ntdll!$$VProc_ImageExportDirectory+3043 (+0x7c) [ 03 82 03 83 03 84 03 85:c4 00 00 8b c4 00 00 97 ] 7c916541-7c91673f 511 bytes - ntdll!$$VProc_ImageExportDirectory+3141 (+0xfe) [ 04 01 04 02 04 03 04 04:00 5e c9 00 00 77 c9 00 ] 7c916741-7c916785 69 bytes - ntdll!$$VProc_ImageExportDirectory+3341 (+0x200) [ 05 01 05 02 05 03 05 04:00 be cd 00 00 c7 cd 00 ] 7c9201ea - ntdll!RtlpAllocateFromHeapLookaside+19 (+0x9aa9) [ 9e:7e ] 7c943c9b - ntdll!RtlInterlockedPopEntrySList+18 (+0x23ab1) [ ed:cd ] 7c95e8e2 - ntdll!RtlpLowFragHeapAlloc+436 (+0x1ac47) [ a6:86 ] 1988 errors : !ntdll (7c912a6e-7c95e8e2) APP: winlogon.exe ANALYSIS_VERSION: 6.3.9600.17237 (debuggers(dbg).140716-0327) x86fre READ_ADDRESS: 00000000 FOLLOWUP_IP: +368b8e80368b908 001b:00000000 ?? ??? FAILED_INSTRUCTION_ADDRESS: +368b8e80368b908 001b:00000000 ?? ??? FAULTING_THREAD: 00000001 ADDITIONAL_DEBUG_TEXT: Followup set based on attribute [Is_ChosenCrashFollowupThread] from Frame:[0] on thread:[PSEUDO_THREAD] LAST_CONTROL_TRANSFER: from 7c943c9f to 00000000 BUGCHECK_STR: APPLICATION_FAULT_MEMORY_CORRUPTION_LARGE PRIMARY_PROBLEM_CLASS: MEMORY_CORRUPTION_LARGE DEFAULT_BUCKET_ID: MEMORY_CORRUPTION_LARGE STACK_TEXT: 00000000 00000000 memory_corruption!ntdll+0x0 POSSIBLE_INVALID_CONTROL_TRANSFER: from 7c943c9a to 7c912a6c SYMBOL_STACK_INDEX: 0 SYMBOL_NAME: memory_corruption!ntdll FOLLOWUP_NAME: MachineOwner MODULE_NAME: memory_corruption DEBUG_FLR_IMAGE_TIMESTAMP: 0 STACK_COMMAND: ** Pseudo Context ** ; kb BUCKET_ID: CPU_CALL_ERROR IMAGE_NAME: memory_corruption FAILURE_BUCKET_ID: MEMORY_CORRUPTION_LARGE_80000003_memory_corruption!ntdll ANALYSIS_SOURCE: KM FAILURE_ID_HASH_STRING: km:memory_corruption_large_80000003_memory_corruption!ntdll FAILURE_ID_HASH: {2c85946d-85e8-c8a7-3c74-93e684cc96ed} Followup: MachineOwner --------- *** Possible invalid call from 7c943c9a ( ntdll!RtlInterlockedPopEntrySList+0x17 ) *** Expected target 7c912a6c ( ntdll!RtlpInterlockedFlushSList+0x0 )0 -
I dont know, how to do this. Because for example when I add "Cli" most of the function is "new"
Dietmar
For the pop function:
53 55 8B E9 8B 55 04 8B 45 00 0B C0 74 0C 8D 4A FF 8B 18 F0 0F C7 4D 00 75 F0 5D 5B C3 ==>
53 55 FA 8B E9 8B 55 04 8B 45 00 0B C0 74 18 8D 4A FF 8B 18 F0 0F B1 5D 00 75 F0 50 8B C2 F0 0F B1 4D 04 58 75 F5 FB 5D 5B C3
0 -
Can this be used, to put 32 Byte free space direct after EACH function of NTDLL.DLL with cmpxchg8b in it
Dietmar
0 -
0
-
I succeed to relocate this crazy function


 !!!!!!!!!!!!!!!!!!!!!!!!!!!!!!
!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!
First, I relocate to .DATA section the RtlInterlockedFlushSList function.
This works.
Then I zero out all the place where it has been before.
Then I delete the whole crazy function RtlInterlockedPopEntrySList at its original place.
This function RtlInterlockedPopEntrySList I relocate after this to the place, where before the Flush function stays.
There I copy and past with Winhex this crazy function, set all calls by hand to this place.
And voila, with this small setting (relocation) in front of the old crazy function,
now I have after her in .TEXT section enough place for modd

Dietmar
0 -
It seems, as if crazy XP reads
00 00 as the hexadecimal representation of the opcode for the instruction add byte ptr [eax], al
in .DATA section
Dietmar
0 -
Here is the relocated original(!) function from ntdll.dll
.data:7C98CA8C .data:7C98CA8C ; =============== S U B R O U T I N E ======================================= .data:7C98CA8C .data:7C98CA8C .data:7C98CA8C sub_7C98CA8C proc near ; CODE XREF: sub_7C9201D1+18p .data:7C98CA8C ; RtlInterlockedPopEntrySList+17p ... .data:7C98CA8C push ebx .data:7C98CA8D push ebp .data:7C98CA8E mov ebp, ecx .data:7C98CA90 mov edx, [ebp+4] .data:7C98CA93 mov eax, [ebp+0] .data:7C98CA96 .data:7C98CA96 loc_7C98CA96: ; CODE XREF: sub_7C98CA8C+18j .data:7C98CA96 or eax, eax .data:7C98CA98 jz short loc_7C98CAA6 .data:7C98CA9A lea ecx, [edx-1] .data:7C98CA9D mov ebx, [eax] .data:7C98CA9F lock cmpxchg8b qword ptr [ebp+0] .data:7C98CAA4 jnz short loc_7C98CA96 .data:7C98CAA6 .data:7C98CAA6 loc_7C98CAA6: ; CODE XREF: sub_7C98CA8C+Cj .data:7C98CAA6 pop ebp .data:7C98CAA7 pop ebx .data:7C98CAA8 nop .data:7C98CAA9 nop .data:7C98CAAA nop .data:7C98CAAB nop .data:7C98CAAC nop .data:7C98CAAD nop .data:7C98CAAE nop .data:7C98CAAF retn .data:7C98CAAF sub_7C98CA8C endp .data:7C98CAAF .data:7C98CAAF ; ---------------------------------------------------------------------------0 -
I put the function all by hand to another place in .DATA section.
Now I get this, @Mov AX, 0xDEAD can you help
Dietmar
*** An Access Violation occurred in winlogon.exe: The instruction at 7C98CAA8 tried to write to a NULL pointer *** enter .exr 0006F428 for the exception record *** enter .cxr 0006F444 for the context *** then kb to get the faulting stack Break instruction exception - code 80000003 (first chance) NTDLL!DbgBreakPoint: 001b:7c91120e cc int 3 kd> .exr 0006F428 ExceptionAddress: 7c98caa8 (NTDLL!RtlpUnloadEventTrace+0x000000a8) ExceptionCode: c0000005 (Access violation) ExceptionFlags: 00000000 NumberParameters: 2 Parameter[0]: 00000001 Parameter[1]: 00000000 Attempt to write to address 00000000 kd> .cxr 0006F444 eax=00000000 ebx=00000000 ecx=7c98c950 edx=00010000 esi=00000000 edi=00000000 eip=7c98caa8 esp=0006f710 ebp=0006f73c iopl=0 nv up ei pl zr na pe nc cs=001b ss=0023 ds=0023 es=0023 fs=003b gs=0000 efl=00010246 NTDLL!RtlpUnloadEventTrace+0xa8: 001b:7c98caa8 0000 add byte ptr [eax],al ds:0023:00000000=?? kd> kb *** Stack trace for last set context - .thread/.cxr resets it ChildEBP RetAddr Args to Child 0006f73c 7c943c6c 7c98c950 7c98c9a0 00000000 NTDLL!RtlpUnloadEventTrace+0xa8 0006f754 7c93d5cf 7c98c9a0 7c98c980 00000000 NTDLL!RtlpGetWaitEvent+0x12 0006f764 7c93d5a5 0009eda8 0009ed80 0006f79c NTDLL!RtlpStartWaitThread+0x18 0006f774 7c943308 0006f790 0009a7e0 0009ece8 NTDLL!RtlpFindWaitThread+0x2f 0006f79c 01029aec 0009ecf0 00000190 010298a1 NTDLL!RtlRegisterWait+0x16f WARNING: Frame IP not in any known module. Following frames may be wrong. 0006f81c 01029d91 00000001 01010d74 00000000 0x1029aec 0006fd14 7c92b00a 7c91d04c 7c91e43f 00000000 0x1029d91 0006ff50 0103e75e 01000000 00000000 00072364 NTDLL!_LdrpInitialize+0x246 0006fff4 00000000 7ffd5000 000000c8 000001f6 0x103e75e0 -
8 hours ago, pappyN4 said:
But first maybe try increase .TEXT size with a PE editor and put into .TEXT and see if that helps
How can I increase .TEXT size for a PE file
Dietmar
0



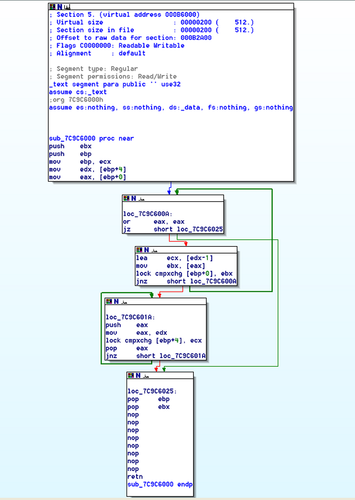
XP running on a 486 cpu
in Windows XP
Posted
@pappyN4
Just now I swap my system32 folder against that system32 folder from before last reboot (which I saved from the same installation),
but now with ntoskrnl.exe, ntdll.dll and modded duser.dll
Lets see,
Dietmar