aphelion
MemberContent Type
Profiles
Forums
Events
Everything posted by aphelion
-
I was referring to them all as a group. They are all addressed the same way as the same types of behaviors are audited on a per-occurence basis. That applies to Adobe, Stardock, IE and SmartScreen. All of MS products that are inherently insecure by design cna be disabled through group policy as I understand is the best practice I've not had any issues follwowing that approach. Flash player should be sandboxed in an out of process context and java not installed if at all possible, otherwise would also need to be sandboxed as its own is not sufficient. I assumed you were asking about the problems they caused because you were having those issues. If that not correct I'm not sure how I can help as there's othing to fix. In any case dont want to clutter up the thread with things unrelated to aeroglass more than already have, so happy to answer any questions over PM or in another thread to sort out those concerns. I do find there is a big benefit to performance and stability when they are addressed so more than happy to help
-
There is a bullet point list near my first post that summarizes that. If you have trouble finding it i can go back in an hour or 2 and PM you the link Edit: This may be helpful if the list seems unfamiliar: http://en.wikipedia.org/wiki/Computer_security. The Security by Design section is good background reading for the topics that were covered. If it is not a relevant concern of course you can skip it
-
Practically every security product on the market has some implementation of intrusion prevention spefically to address the issues you mention. I suggest Comodo's although it's a bit agressive sometimes If you can't see a distinction between reporting an issue and not liking a product, the nI can understand why calling someone "Mr. Big Brain" could make sense Good luck clearing up those infections. The clean endpoint tool can be helpful in cases where they are all present but I would start from scratch and practice good security from the beginning.
-
No absolutely not. This was a theoretical discussion that got out of hand. SO WHAT ARE YOU SAYING ? & WHAT IS THE POINT OF ALL THIS THAN ? Very funny but I'll play along. Formus are for discussion and this was a discussion. What's your experience with forums?
-
No absolutely not. This was a theoretical discussion that got out of hand.
-
I'll do the same also. And I see where the expectation of communicating privately came from. Personal preference aside, I was also under the impression, apparently mistakenly, that public disclosure wouldn't be surprising or offensive as that's been by far the norm for 6 months dating back to around 2.5 years. But I forget things are different elsewhere and I realize iI assumed. so for what it's worth I didnt mean to offend by posting publicly. Intent is singular, resolution, and thats been what I've seen in the past. In this case there is no immediate risk of an exploit and not a line of code was posted so that there wouldn't be the risk of one. The context was the focus in the debug example but thats far too long ago to be of any use clarifying now. As I don't really look anywhere outside the US and it's always up the author what is decided, I didn't realize the opposite of what the intention was would happen. If really only 1 line of procexp was looked at there is definitely more there, but I may be misreading an exaggeration literally. In any case it seems I will be up after all and i'm sure I won't be able to keep my curiosity for more than a few hours. Im sure its highly unlikely but in case anything exists that i can clarify I am am happy to do that either public or private with the email you have
-
Ok, i just read about 3 words there about me bashing Glass. I think you really think that's true. So that fits in well with the reason I came back, which was the donation I made a joke about. If you're still not sure, just ask anyone. They will confirm it's a joke. That's how they're written here. But of course I know that won't be enough, so I sent another donation. I don't know any other way to communicate that any more clearly in a way that seems to speak louder than any other. I hope when things are calm you will have a chance to review with perspective what I actually wrote.
-
Your post explains what I meant above. Normally, in software development, when some security vulnerability appears, it is reported to developers in a private way so nobody cannot abuse it. It is described what happens, the potential risk and possible solution. But what is shown here? He only spams the forum with many unuseful messages with the goal "look, look everybody how Aero Glass is unsecure, look how it is dangerous", then he does not forget mention that debug window is annoying and that it can be simply removed and that the biggest vulnerability is in the nagging message popup. And he finishes with request to refund. So that's why I'm saying he's trolling only... Can any moderator clean this discussion so it is readable for regular users only? If someone really wants to report any security bug he can use PM with possible solution and not only cry how he is clever and how Aero Glass is bad. Are you reading the same forum? Debug window I mentioned is annoying, thats your gripe? Maybe I was unclear in some way. My concern is singular: security. And the effects of DWMHook on it. Why does it insert the DWM group (skip the isolation lesson) into so many privileges? Why is lsass constantly asking to get permission from user land? Any answers to the real questions? And no, I would never message you personally because I actually read the thread and saw how you responded before. If you prefer to be PM'ed, I think you have a long way to go How about all the ones you skipped.... Why is it a process thta launches with the highest permissions possible left entirely unprotected in a user folder? How is that different than a text file on the desktop, in terms of security? Why are there no permissions set to prevent even basic exploitation left wide open by this dll? Are you even aware of ingtegrity level and trust levels? I dont mean to insut, but the way it's approached in the DLL is duplicating existing OS functionaity of integrity in an inherently flawed way. Now I'm speaking from the point of view of viewing through a debugger all the security holes, which is what I've always been talking about. The only secure thing I see (barely, sorry) is the crypotgraphy around the key. At the cost of everything else.So many questions, so few answers. I think that clears things up enough for me. Sorry guys, I tried. He'll fix them eventually.
-
And here we are, because your answer is what I was exactly expecting. Maybe you should look how process isolation and interactive services works. DWM process is a service with very limited privileges and it runs in its own session thus it cannot interact with user desktop in any way. However, the operating system, since Windows Vista, provides a feature so non-interactive services can send a message to the interactive desktop. And this is handled by CSRSS.EXE process. Very simple, it's no taking over the security policy, elevating some privileges nor hooking any system process. It is official WinAPI feature by calling MessageBox function. I don't comment whether this way is secure or not, I just say that it is handled completely by official OS function and if there is anything unsecure with it, then it is bug in the OS itself and not something which I do. Glad we have a response, hope it keeps coming. Especially these good ones. Here's the problem. You said hook again. Never once have I said it hooked csrss.exe. I did say many things that you entirely skipped over, and had a 1 run on paragraph response about something you have in your mind that's entirely made up. You don't see that? Also, thanks for the primer, I'll try to remember all that. If you really think that was necessary, maybe skip the stuff that seems too easy. I am happy to jump in anytime. Of course I'd bring up things you didn't mention like the protect lock. Which may be a self defense mechanism although I've not seen that by the WIndows team before. But as you said, possible. Fact remains that the lock is there when DWMGlass is running and not there when it's not running. That's a problem whether directly or indirectly caused by DWMGlass. I'm not going to waste any more typing on this but I will create those screenshots if you can't replicate. It seems to be a strange coincidence to lock read access to the process being used... to... deliver the donation message. I find it difficult to reconcile, but it's not that important. There is a big deal, though, and that's the first one on my list. And the one right above your post. Look at that for a second while I put together some pictures to help so I can go to sleep. Also, can I get more space?
-
To your point on the purpose of public forums, agreed. Consider though, if I just PM it, do you think it will get fixed? Maybe? That's why it's posted here, for visibility. It may not make sense yet, as i haven't covered it in detail and that will take some time. But it certainly should have been making sense for quite a while to the target audience. I don't see any more name calling coming my way, which is a nice thing. Just saying. Edit: typos
-
I am getting there... the pots I just made should explain somewhat but probably not enough. LUA is Limited User Account and having the security process asking for system access from that account is a behavior that should never happen, since it's the master after all. Except when its compromised... but I am trying to not say anything too inflammatory because we saw the reaction earlier and I want to give all the information first, since the explanations are all online also. But I will cover everything eventually, or at least I intend to. Sorry for not being more thorough. It is 10 am and I havent slept yet as you can see the posts have gone back quite a while
-
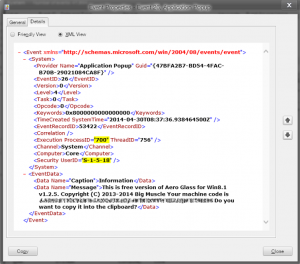
Still here. Sorry. slept for 30-45 min apparently. I will finish this post, and then have to come back. It's pretty clear even just from the screenshots... Let's just look at the biggest thing right now, as mentioned before that's that's lsass.exe, the authority for all security on your computer. What should definitely not be happening, and only happens when DWMGlass is running, is trying to pull Tcb privilege constantly as a regular user. Out of disk space for screenshots. Great. External host. Looks giant so if its the same on your end, sorry about that. Somehow doubting I'll get more space to provide the screenshots I'm obligated to.... Anyway, Tcb means "Acting as Part of the Operating system": DWMGlass disabled = no sensitive privilege requests denied, because everything it's asking to do is within the scope of what it's supposed to be doing and the OS lets it through without issue DWN Glass disabled = already described but will go over with screen in a second with screens. Basically, Tcb in user land... the OS obviously does not belong in the LUA context so that will be how it wraps up and leave the door open for counterpoint and explanation. Maybe So I will brb with that and in the meantime ,as I said I would not judge or jump to conclusions, the door is wide open Mr. Big, would love to hear your take on this behavior you're entirely unaware of Also can I get more space? Thanks
-
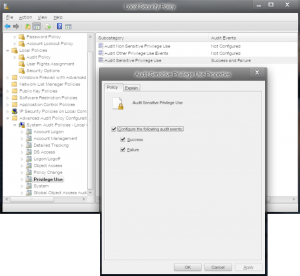
Yes, I want a proof to all of this, because neither one of these happens in my tool. Ok. Given that 2 of the points I posted are suddenly missing, I'm assuming you are admitting they are not "Wrong" as you repeated over and over. Thank you for taking a more sensible approach. I am also glad you picked some, so I am not wasting time on things that are not going to be productive. However I'm not sure where the "Yes" and "all of this" came from. If you scroll up to check you will see I what I said is that I will have to take screenshots. There was no "all of this" to say "yes" to because you fully well know that's hundreds of screenshots. Obviously I'm not going to make a hundred screenshots for you because your "tool" (feel free to be more specific) isn't showing something.. Maybe that was your hope. If so I am sorry to disappoint, but I will do what I said and provide screenshots to prove the points that are still on your list. That will be on a rolling basis until you change your mind about your tools or whatever else you think of until then. I expect not to receive any response once each is proven but certainly if there is any discrepancy you'd like to resolve, that's pretty much the point. I wish that there was even a chance of that but I'm not holding my breath. So with that said, here is the first that I said I would take, which is on your list as well. For context: You are wrong. No, I'm not. And here's your proof: PID of system level (nagware delivery mechanism Process Explorer correlating PID to csrss.exe I can't imagine that you might try to say that the role of csrss.exe, a process critical to system operation which "terminating will result in system failure", is being hijacked here in some other way than I described, but since there's lots of time until I wake up I'm sure you'll think of something to pick at. Whatever that is, keep in mind that the as more is posted the picture only gets clearer and I will come back to refute every single point where you said I was wrong until it's clear you're full of it. I resent having to make a picture book with links for you. But it seems that's the only way you will admit it's not that I "saw something somewhere" and "don't understand it" while you don't know anything about it "because neither one of these happens in your tools". Except the ones that disappeared from the list without explanation of course. Let me know when you've seen enough to give up the pretense completely, instead of just one or 2 points at a time, so I can stop wasting my time. I hope it will lead to a fix, but still there is not even an indication of that. If I can stay awake long enough I will give you a glimpse into what I saw and where with the actual tools used. I hope there's some recognition as that should resolve any doubt you still have even after this, given we're already halfway through the list. Based on your code there should be, but based on your responses here it seems the opposite. Before that, though, I think it's important to let people see some of those things happening on their own machines. Rather than picking at 1 thing and then another, this should give a good look into some of the more egregious security holes created by restructuring system wide security. And that's all I will do, no explanation and no assumption. I'm sure there's a very good explanation 1. Setting up Auditing for "sensitive privilege use" (Windows term, not mine) [ 500k limit per post, continuing in the next post... ]
-
Sure, you are right. But your posts contain several things which show that you don't understand it at all and you only saw something somewhere and making some own speculation from it. And if you end it with "can I get refund", it only proofs that you are trying to troll instead of making technical discussion. And it's not worth of normal answer.No, thats sarcasm. We are from different countries so i can understand there is likely a gap in the intonation there. I "heard" this... is that some way of trying to discourage me from posting proof or the oppsite? I'm not sure if you think denill without any counterpoint is just going to be fine and dandy when anyone can replicate the steps. Hey guys, run secpol. Now run it without dwmhook. Notice the difference. Thats it. Its all right there. It just goes too far not to notice. YOu aid you anted screenshots. Fine. I will head to my desktop and take some. I will start with csrss act ing asa your nagware delivery system. I dont suspect that to satisfy you, or that anything will. Frankly I dont need 3 euros no more than I need this fixed. My system is patched and if you want to screw over everybody else that is your choice. I have nothing to gain and only more time to lose. That I 'm doing this is not trolling, it's time and apparently most important to you, given the joke you chose to focus on instead of the proof i posted, money.
-
Don't worry, nothing need to be quoted by you, I don't need to delete anything. It was you who edited your post several times - you first post contained that you are going to provide some proof for your speculation. So you are free to do it.Okay, so you don't see the above. What part is most useful for you to see? I can't understand the mindset and to provide dozens of screenshots....is a waste of time that I will do even without apparent effect....but if you have something that you feel is truly wrong and would like demonstrated in detail that would be a better way to focus. Its all true so just pick anything and consider a walkthrough ready in a few hours (it 5am here in nyc...so that means tomorrow)
-
You are wrong. You are wrong. You are wrong. You are wrong. You are wrong. You are wrong. I'm correcting you, because you are completely wrong and you posts has no sense. Quoting before the deletion. Edit: Actually not even going to be sarcastic since I think the response is enough to speak for itself. Please fix it. Thats all. "Nothing to fix" will just lead to more of this except i will have to take screenshots for the others. You are wrong. Not at medium integrity?C:\AeroGlass>chml DWMGlass.dllChml v1.53 -- View and change Windows file/folder integrity levelsby Mark Minasi (c) 2006-2009 www.minasi.com email:help@minasi.comThe file DWMGlass.dll has no integrity label.Windows treats unlabeled objects like this:File DWMGlass.dll's integrity level: mediumInheritance flags: No inheritance flagsIntegrity policies: No read up: disabled No execute up: disabled No write up: enabledNot the same as a txt file saved to the desktop? C:\Users\Rod\Desktop>chml dxdiag.txtChml v1.53 -- View and change Windows file/folder integrity levelsby Mark Minasi (c) 2006-2009 www.minasi.com email:help@minasi.comThe file dxdiag.txt has no integrity label.Windows treats unlabeled objects like this:File dxdiag.txt's integrity level: mediumInheritance flags: No inheritance flagsIntegrity policies: No read up: disabled No execute up: disabled No write up: enabledNot left unlocked you say? C:\AeroGlass>handle DWMGlass.dllHandle v3.51Copyright (C) 1997-2013 Mark RussinovichSysinternals - www.sysinternals.comNo matching handles found.Not left wide open? C:\AeroGlass>ren DWMGlass.dll BMversion.dll & echo arbitrary code > DWMGlass.dll & type DWMGlass.dllarbitrary codeDo you really think the original dll is going to run at the next startup? Obviously anything can replace echo so no need to say "that wont execute" I can understand being defensive but repeating 4 times isnt going to plead to any different facts. Lets not get to screenhots of process explorer or secpol showing the rest. Obviously enough time wasted already so why not just do the right thing I don't understand, but its your choice
-
That's the DLL talking, not the OS. It's so the protect flag can be set on csrss.exe to prevent tampering with the nag. You can keep the nag intact and still run whenever you want like say, logon where it actually makes sense. The only difference is that lsass already loaded at logon, and no way is about ot hand over the primary token privilege. Command line works fine too. Either with schtasks or third party tools like nircmd, psexec to run as system. Those are just some options, all within eula. Of course glass still works fine then because all that effort has nothing to do with glass, or hooking dwm. I don't know the purpose, but can see the result same as anyone in is practically every aspect of security overhauled to protect the nag box instead of the user Some security can be restored but it's a little tedious since at least 3 tools are needed. icacls for permissions and integrity, secpol to restore privilege access, and schtasks so they cant be changed back. still within eula btw, and glass still working. i did the secpol manually since its a gui but it can be automated. not a big deal though since gui also means the defaults are shown. just look under the warnings, past the explanations of why it's dangerous to make changes, then under caution heading for the really bad ones. thats where they are
-
Actually I see the dacl now, you defintely know how big a security hole this is, so then its more of why create a vector wide enough to compromise a system so easily accessible in user space? There' that and then messagew for the annoying debug window. Easily removed without modifying , hooking, etc whatever you put in your eula i didnt touch. just a taskkill on the hidden conhost generated. You dont see that?
-
So... nice job on the blur. Looks great. Heres what I see. And I checked many times, but correct me if any is wrong: - Hooks lsass..exe (Local Security Authority Process) so it can take over the security policy of the entire system - Uses that to allow DWM group to assign privieged security tokens that only exist for the purpose of the OS itself to use - Hooks DWM and elevates privilege using the new tokens to bypass all security so it can hook csrss.exe - Sets the protect flag on csrss.exe so nothing else can touch it (seems like good security until we circle back round) - Uses this core system process in a highly restricted security context for the only purpose of showing a nag dialog box, which could be shown anywhere but then it could be closed with the X instead of the No button - Leaves DWMGlass.dll in a medium integrity (regular user account, not running under elevation/as adminisrator) zone - So all I need to do to take over a system is replace tihs file, that's not protected in any way by permissions, integrity level, or any sort of security whatsoever No need to even get someone to run anything as admin. No need for an exe file. Just a hkcu reg add, change up DWMGlass.dll a bit, since its not even locked during user logon (seriously?), and I can do pretty much whatever with anyone who has this cool blur thing installed. Is that about right? Thats not including all the user level security proceses compromised, no point mentioning given kernel security is the same as a text file on the desktop Edit: All that is hardly trivial so I figur eyou know what you're doing, but just in case - trust level 8000 - system integrity - sign the code (!) - lock the dll Can I get a refund? Cause all this still happens when my key is in
-
Aero Glass Cofigurator For Windows 8.1
aphelion replied to MrGRiM's topic in Aero Glass For Windows 8+
You didn't specify so I assumed a workaround would be helpful. Either you can copy the file there or if you want it to be a little cleaner, select this text: mklink /j C:\AeroGlass P:\AeroGlass Ctrl+C Start Hold Shift+Ctrl, hit V then hit Enter -
Aero Glass Cofigurator For Windows 8.1
aphelion replied to MrGRiM's topic in Aero Glass For Windows 8+
Grim I really like your stuff and everything you do for the community. It's your work that got a lot of us including me into tweaking. That being said this tool really screwed a lot of tsuff up for me, with Aero only though. The very first day I started getting the out of range popups on dwm had to click ignore every time Aero launched. I figured it would just go away or I'd ignore it or whatever. Day and a half in, I'm at a dead black screen after clicking Apply. Alright, stuff happens, reboot, go into it and see what might have done it. All settings are gone it seems. I change the blue compositing mode and suddenly the solid color from before Aero is back. ****. No problem, reboot. It's still there. Tweak some settings, try again, reboot, edit registry. Nope. Still there. time to reinstall... without the tool :-( -
I've only seen it happen under different security contexts, like different accounts, or when using the elevated token, or running a process as system with something like psexec or nircmd. Assuming that's the case for you just navigate to O-N-E under that security context (i.e. in the same window you see the ribbon) and set all the preferences again. They should stick then.
-
So much for that theory. I saw it happen outside a sandbox today (and other sandboxed apps didn't replicate that behavior) so it has to be something about the way the windows are being created. I took a cap at 3x mag: I guess the reason the caption title was made into Metro style DirectWrite is because it's maybe the only part of the interface the developer usually doesn't get involved in. Somewhere down the road maybe they are hoping to bring desktop apps into Metro.
-
Hi, I have a potential feature suggestion with a possible way to do it. I'm using a theme with a gradient for the title bar (Executive) but I restored the text so I could see the titles. I noticed in some cases the background color behind them did not render so I wanted to request that as a feature. It seems like that option would fit right in with O-N-E, and many themes are using blank fonts to go around it right now so it would help a lot of people. I will explain to the best of my understanding how to replicate the result but first here is a screenshot... [ Screenshot showing no caption background ] (foreground center "Araxis Merge" window) The reason that window does not have a solid background color is because Comodo Defense+ is blocking access to, I believe, the COM interface required for DirectWrite. It could be blocking access to Direct2D entirely but I'm not sure how to do the tracing to figure that out. The window in this case is double sandboxed by Comodo and Sandboxie, but this effect only happens when Comodo is running. Sandboxie doesn't deny whatever access the DWM needs to put the solid background color, but Comodo does. I realized it was DirectWrite when I used Actual Window Manager to mirror that part of the desktop at 2x magnification. The other title bars show up blurry in the mirror so they must be in 3D space, and the one without the background color appears pixelated (e.g. nearest neighbor resampling) like the rest of the window. I think the transparent title bg may be possible by tracing the interface and blocking it. I have Process Explorer but I'm not sure what to look for to figure out which interface is being blocked but I'm happy to give it a shot if anyone can point me in the right direction. If you want to duplicate it yourself you can use this link to get Comodo, then just run any program as sandboxed using the right click menu: http://www.comodo.com/home/internet-security/free-internet-security.php The component of CIS that does the blocking is the Virtual Kiosk which creates a fully virtualized session, sandboxed using both its HIPS-based security and native Win8.1 virtualization (which other apps use on purpose, like Dropbox). That's about as far as I've been able to figure out.