Content Type
Profiles
Forums
Events
Posts posted by alacran
-
-
20 hours ago, RanCorX2 said:
or you can look in fridge before going shopping and make a list of what you need? some tech is just not needed unless you are rich and lazy or both.
It seems only useful for people that puts everything in fridge, including toilet paper.
0 -
@Roffen
Right click on desktop, select Personalise, find themes and look carefully on top right and there is an option for add icons on desktop. I think location may change depending on Pro, Home or update version (as all does on 10).
0 -
9 hours ago, Radish said:
Event filter with query "SELECT * FROM __InstanceModificationEvent WITHIN 60 WHERE TargetInstance ISA "Win32_Processor" AND TargetInstance.LoadPercentage > 99" could not be reactivated in namespace "//./root/CIMV2" because of error 0x80041003. Events cannot be delivered through this filter until the problem is corrected.
There was a fix from MS for this: MicrosoftFixit50688.msi not easily available anymore, But I found it here.
2 -
On 8/7/2018 at 4:22 PM, Xack said:
There's a few news articles going around that suggest Intel is launching the H310C chipset, which will be backward compatible with Windows 7 due to it still being popular in China. I wonder if it will be fully compatible or will it still need to add USB3 drivers and wufuc for updates.
Useful link with more info: https://www.anandtech.com/show/13201/intel-preps-h310-revision-with-win7-coffee-lake-support
alacran
2 -
Let me suggest you to include on your collection of tools BootIce (available on x86 & x64) Link http://www.ipauly.com/
QuoteBOOTICE is a startup-related maintenance gadget for installing, repairing, backing up and restoring disk (mirror) MBR or partition PBR; editing Windows boot configuration file BCD; managing UEFI boot entry; VHD/VHDX file management. In addition, it also has the functions of disk sector editing, disk filling, partition management, disk partitioning and formatting, and GRUB4DOS menu editing.
On MBR partitioned disks, Grub4dos and BootIcel is what I have always used for creating my multiboot environments. About grub4dos I prefer 046a (this do not require contiguos file to direct boot [not from RAM] an ISO from internal or USB drives) last version: http://dl.grub4dos.chenall.net/grub4dos-0.4.6a-2018-07-01.7z (516 Kb). In fact I have booted from my WinPE ISO files even having 4 fragments.
Congratulations you have a very nice thread here and very well explained for beginners, keep the good work.
Your friend
alacran
0 -
For Backup/Restore and also install new MBR to hard disks you may use BootIce, there is a 32 and a 64 bits version. Totally portable (runs on WinPE x86 and x64). Also can be used in Commandline.
1 -
11 hours ago, jaclaz said:
This link worked fine for me.
About:
QuoteYou may open MSFN at any Android device (mobile phone or tablet) and click on that link to download the file into the device downloads folder. After that you may connect the device to your computer and extract the downloaded file to be used under Windows.
I already downloaded it from Jaclaz link, no need to use an Android device, anyway thanks for your suggestion.
0 -
9 hours ago, jaclaz said:
Thanks Jaclaz for attaching the file, by the way using the resolved link in your last post (http://ericksystem.weebly.com/uploads/1/1/0/3/11039286/repair_this_1.0.zip ) also can't find the server.
0 -
I always got a message Server ericksystem.weebly.com not found on Firefox 61.01 and also on Internet Explorer 11, I'm on Win7 x64. Could you please upload it to an alternative free storage site?
I already disabled Avast AV and firewall (Firewall App Blocker 1.6) and retry but same thing. This may be caused for something else blocking that address on my side.
Thanks in advance.
0 -
On 5/18/2010 at 5:33 PM, cannie said:
- "Repair this", to remove the hidden file "System Volume Information" as explained at paragraph 8.9.
Just to inform this link is not working.
0 -
11 hours ago, taos said:
Thank you for the simplix link alacran.
I gave the simplix updater a test run on a spare disk.
After I installed the OS, I went to installed updates, and there were only two listed.
I then ran the simplix updater (17.12.15), which added 178 updates (it also removed one of my existing updates).
The update process lasted almost two hours. It restarted itself 3 times, as it only seems to process 80 updates max per session.
I'll see how it goes... Thanks again
You may integrate the Update Pack to your selected install image index or all if you want (it takes long time for all indexes) on your ISO in a single run, see: http://forum.oszone.net/post-2609527-2478.html (Use Google translate to read it in your own language).
Download Link: http://files.simplix.ks.ua/boss911/UP7Integrator.7z
This way you only apply the pack once and not every install, but you may also apply the more recent pack on line after installing your December/2017 updated ISO if you want, and it will only apply the required updates (not the 178 updates), taking only a few minutes to run it. And control Spectre and Meltdown mitigations patchs using InSpectre: https://www.grc.com/inspectre.htm
alacran
2 -
You may download and install Simplix UpdatePack7R2 v17.12.15(x86/x64) from Dec/15th/2017. This pack do not contain telemetry updates and this Dec. update do not contain any updates related to Meltdown and Spectre yet (they started on Jan. 2018) , so no performance impact.
Previous links may require register on that forum, for your convenience I copied here for you the download link.
Download Link: https://update7.simplix.info/UpdatePack7R2-17.12.15.exe
1 -
That may be the cause of lost info, thanks for your answer, I didn't see that post from June 7 before, sorry for the inconvenience.
0 -
I think there is something wrong on topic:
As you can see it shows page 114 as last page and last post from Jan 29th 2018, but I'm totally sure there are more pages and posts after this.
Maybe the topic is too long now for forum software, Could a moderator check and fix this please?
Thanks in advance
alacran
0 -
On 6/21/2018 at 3:41 AM, Stefan43 said:
I use the latest version of Firefox (Quantum) on Windows 7 x86 and it works fine. Maybe you like it when you try it, it's quite fast.
Yes, the x64 version has been working very fine for me on 7 x64, I assume x86 version will be fine too as Stefan43 said.
Link for last version (x86 & x64) for all OS's and languages: https://www.mozilla.org/en-US/firefox/all/
0 -
Quote
Malware takes screenshots of users' desktops, and has been operating silently for six years
Researchers have uncovered a sophisticated rootkit-based adware, mainly prevalent on Windows 10 devices, that has been operating covertly for six years.
Dubbed Zacinlo, this rare strain of malware typically operates by silently rendering webpages in the background in hidden windows to simulate clicks and keyboard interactions, or can replace ads naturally loaded in an open web browser with its own ads to collect revenue.
The malware, subject to an extensive investigation by security company Bitdefender, is armed with a sophisticated array of features to ensure it remains undetected, and even quashes any 'competition', featuring an adware cleanup routine to remove any potential rivals in the adware space.
It can also uninstall or delete services based on instructions it receives from the command and control infrastructure, to which it routinely sends information about its environment, including what form of anti-malware services may be installed, and which applications are running on startup.
One of its most concerning features involves a significant invasion of privacy, with Zacinlo able to take screen captures of a user's desktop and send them to its command and control centre for analysis.
More info on Source: http://www.itpro.co.uk/adware/31333/zacinlo-malware-threatens-windows-10-pcs-security
0 -
AFAIK MS is not activating XP installs (on line or by phone) anymore. I just read about this a few days ago but can't find that link.
Anyway googling I found this other link for you, more info on it, source: http://www.digitalfaq.com/forum/video-capture/7879-windows-xp-longer.html
QuoteMicrosoft has taken down their activation servers for WinXP. This is bad news, because without activating, an XP install becomes unusable after 30 days. I hear a lot of people rely on this OS for making reliable analog capture machines (this includes my new build, which is how I just discovered this is a problem). What this would mean is we could only use an install for 30 days, and then get locked out and be forced to create a total reinstall.
alacran
0 -
First make a backup of current system, then try running it from your actual OS and during install select update keeping your documents and programs. If you didn't remove all required in order to run the install this way it should work, but it may not remove some components if you are looking for a lighter install.
0 -
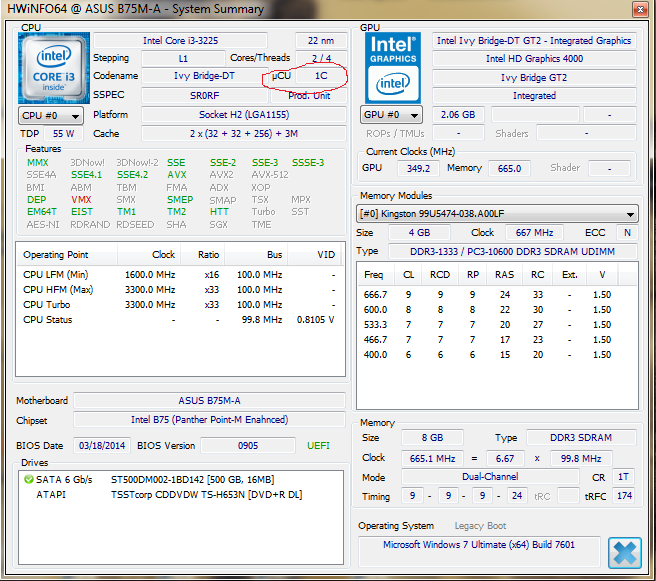
From an info I got on MDL only the CPU's on following list got a Microcode Update on Linux Processor Microcode Data File Version: 20180108 (Latest) Date: 1/8/2018 (absolutely necessary to make Windows patch to work).
QuoteCPUID=306C3 Rev=23 2017/11/20 CRC=16535FE4 Off=0 Size=5C00 Plat=1,4,5
CPUID=306D4 Rev=28 2017/11/17 CRC=734956F1 Off=0 Size=4800 Plat=6,7
CPUID=306E4 Rev=42A 2017/12/01 CRC=9B215C1F Off=0 Size=3C00 Plat=0,2,3,5,6,7
CPUID=306F2 Rev=3B 2017/11/17 CRC=B4A4C42D Off=0 Size=8400 Plat=0,1,2,3,5,6
CPUID=306F4 Rev=10 2017/11/17 CRC=40551AAB Off=0 Size=4400 Plat=7
CPUID=40651 Rev=21 2017/11/20 CRC=2B637CE4 Off=0 Size=5800 Plat=1,4,5,6
CPUID=40661 Rev=18 2017/11/20 CRC=A2AC454C Off=0 Size=6400 Plat=1,4,5
CPUID=40671 Rev=1B 2017/11/17 CRC=4763E424 Off=0 Size=3400 Plat=1,5
CPUID=406E3 Rev=C2 2017/11/16 CRC=C6C6F699 Off=0 Size=18400 Plat=6,7
CPUID=50654 Rev=200003C 2017/12/08 CRC=A4059069 Off=0 Size=6C00 Plat=0,1,2,4,5,7
CPUID=50662 Rev=14 2017/12/16 CRC=9161527A Off=0 Size=7C00 Plat=4
CPUID=50663 Rev=7000011 2017/12/16 CRC=B17C1102 Off=0 Size=5800 Plat=4
CPUID=506E3 Rev=C2 2017/11/16 CRC=328B43AF Off=0 Size=18400 Plat=1,2,4,5
CPUID=706A1 Rev=22 2017/12/26 CRC=CA264967 Off=0 Size=12000 Plat=0
CPUID=806E9 Rev=80 2018/01/04 CRC=6961A256 Off=0 Size=18000 Plat=6,7
CPUID=806EA Rev=80 2018/01/04 CRC=F6263DAE Off=0 Size=18000 Plat=6,7
CPUID=906E9 Rev=80 2018/01/04 CRC=6AA1DE93 Off=0 Size=18000 Plat=1,3,5
CPUID=906EA Rev=80 2018/01/04 CRC=84CABC68 Off=0 Size=17C00 Plat=1,5
CPUID=906EB Rev=80 2018/01/04 CRC=D24EDB7F Off=0 Size=18000 Plat=1So it seems if your CPU is not in that list you are out of luck and they decided not to update your CPU Microcode.
1 -
As we can see in following pictures VMware CPU Microcode Update Driver really works updating the Microcode.
Before applying VMware CPU Microcode Update Driver:

After applying VMware CPU Microcode Update Driver:

But Intel has not updated it to fix this vulnerabilities on recent version for my i3 3225, as SpecuCheck reported:

alacran
0 -
Quote
This Fling is a Windows driver that can be used to update the microcode on a computer system’s central processor(s) (“CPU”). This type of update is most commonly performed by a system’s firmware (“BIOS”). However, if a newer BIOS cannot be obtained from a system vendor then this driver can be a potential substitute.
VMware CPU Microcode Update Driver: https://labs.vmware.com/flings/vmware-cpu-microcode-update-driver
Linux Processor Microcode Data File Version: 20180108 (Latest) Date: 1/8/2018: https://downloadcenter.intel.com/download/27431/Linux-Processor-Microcode-Data-File?v=t
I am on a i3 3225 Win7x64 PC, followed instruction on page https://labs.vmware.com/flings/vmware-cpu-microcode-update-driver#instructions and was able to confirm on "Event Viewer" "Successfully updated microcode on one or more CPUs".
Unfortunatelly after running SpecuCheck I got this:
QuoteMicrosoft Windows [Versión 6.1.7601]
Copyright (c) 2009 Microsoft Corporation. Reservados todos los derechos.C:\>SpecuCheck.exe
SpecuCheck v1.0.5 -- Copyright(c) 2018 Alex Ionescu
https://ionescu007.github.io/SpecuCheck/ -- @aionescu
-------------------------------------------------------Mitigations for CVE-2017-5754 [rogue data cache load]
-------------------------------------------------------
[-] Kernel VA Shadowing Enabled: yes
├───> with User Pages Marked Global: yes
└───> with PCID Flushing Optimization (INVPCID): noMitigations for CVE-2017-5715 [branch target injection]
-------------------------------------------------------
[-] Branch Prediction Mitigations Enabled: no
├───> Disabled due to System Policy (Registry): no
└───> Disabled due to Lack of Microcode Update: yes
[-] CPU Microcode Supports SPEC_CTRL MSR (048h): no
└───> Windows will use IBRS (01h): no
└───> Windows will use STIPB (02h): no
[-] CPU Microcode Supports PRED_CMD MSR (049h): no
└───> Windows will use IBPB (01h): noC:\>
NOTE: Wasn't able to run PowerShell script on my win7x64 so that's why I ran SpecuCheck. Of course KB4056897 was installed on my system before doing all this.
VMware program did work (as I confirmed), but in file "microcode-20180108.tgz" Intel Microcode Data File for my i3 3225 was not patched for this vulnerabilities. So this means Intel is launching this file "microcode-20180108.tgz" to public and not all Microcode Data have been updated to fix this vulnerabilities and no mention to this on download page.
INTEL HAS LOST ALL CREDIBILITY FOR ME.
Somebody with a newer Processor should check this in order to verify if Intel has fixed this on recent Processors.
alacran
1 -
On 4/1/2018 at 2:58 PM, Homes32 said:
That's the plan. wimgapi for mount/unmount and wimlib for everything else. If wimlib ever supports mount/unmount on windows then we can look at moving everything over. Only time will tell.
I think that using wimlib-imagex we can just extract the complete image (or part of it) to a folder, a VHD or an empty partition, then add all required files, folders and make registry changes, latter capture it again with wimlib-imagex (or inject to source when partial extraction was done), this way there is no need to mount/unmount wich takes a very long time, this is in few words the way MistyPE project works.
alacran
1 -
Now that Win10 forced update is over most of aegis script is not required anymore. There is a very good script from abbodi1406 on MDL to disable Telemetry on Win7.
You need to run it as administrator after installing updates, and then reboot your OS again. This needs to be done always after new updates are installed.
Attached for your convenience as you need to sign on MDL to view this topic. I hope abbodi1406 do not mind for this, He is also a member of this forum and I hope he can come to this thread and comment a little more about this.
source: https://forums.mydigitallife.net/threads/disable-remove-telemetry-and-tracking-service.68131/
alacran
0 -
@ Joveler
About this:
QuoteLauncher now detects installed .Net Framework's version and warn user to install lastest framework, but launcher itself requires .Net Framework.
I lowered the target to 4.6.2 temporary (since Launcher.exe used that version before), but I am willing to lower more if it is necessary.
You can refer to this article to determine adequate version.I respect your decition, but since you ask for comments I suggest lower the NET warn to 4.0 wich I think is more comon since having version from XP to all new sistems it makes sence to me (I always had it installed since XP times).
alacran
0




Official - Windows 10 Worst Crap Ever!
in Windows 10
Posted
That sounds very logical as one is crap and the other for cleaning crap.