
DiGGiTY
Content Type
Profiles
Forums
Events
Posts posted by DiGGiTY
-
-
It looks like you don't have all of the DNS records to support Active Directory. To solve this, go to the server and run ipconfig /registerdns.
0 -
What you're looking for is this:
User Key: [HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\
Explorer]
System Key: [HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Policies\
Explorer]
Value Name: NoRecentDocsNetHood
Data Type: REG_DWORD (DWORD Value)
Value Data: (0 = track shares, 1 = disable tracking)
0 -
You OC memory in the BIOS... Before soing this, Google your memory and overclocking.... You should work with some settings that have already been tested.
0 -
The copy command syntax is wrong. The /-Y command comes right after copy, not after the source and destination.
0 -
Another thing you may not think of all the time... Install your support tools and resource kits before applying any service packs or updates. There are always updates to the resource kit in services packs.
0 -
I'd suggest getting the books that Mark Minasi publishes. He is the well-known author of the 'Mastering' series. You'll find that the majority of professionals use his books because they are the most complete references for Windows Server products.
If you are interested in more technical nuances and obscure details, be sure to check out Microsoft's 'Notes from the Field' series. There's lots of good stuff there.
0 -
FYI: This may not be the case here, but when Xp is installed, logic ascertains which hardware abstraction layer to install. There are different HAL's for APM versus APIC motherboards.
0 -
Microsoft released a tool named BootVis that optimizes your startup time... It is not available for download at Microsoft any longer, but if you do a Google for 'download bootvis' you should be able to find it.
It works... I've used it a lot over the last few years.
0 -
It is an installation with no GUI interface and no user interaction
0 -
These are the top two boards for the AMD 939:
Dfi LanParty - better for overclocking
MSI k8n-Neo
0 -
A big no
0 -
There are plenty of wireless keyboards out there with mouse functions on the touch pad. You have to understand that deploying a full blown Media Center in your living room is cutting edge (viz. expensive).
Give it time. High end displays, video cards, and sound boards all exist today, but they will be less expensive in the future. This is how it always is with newer technology.
0 -
Are you planning on overclocking?
0 -
Halo 2
Splinter Cell-Chaos Theory
Brothers in Arms
Jade Empire
Knights of the Old Republic II
0 -
Symantec AntiVirus Corporate Edition 9.0 (most companies use this)
0 -
Here's another interesting point: Initially the large antivirus companies were adament in respect to keeping antivirus and antispyware products separate--they weren't intersted in handling spyware.
Presently, Symantec and McAfee (the big 2) have released their first versions of antivirus integrated with antispyware removal. Prior to that these companies only detected spyware.
Gartner group recommends that businesses use a stop-gap solution presently to handle spyware. Gartner says that your long-term solution will be offered by antivirus vendors.
0 -
This will do what you want...
The Windows 2003 Resource Kit has a hidden .dll file called Acctinfo.dll. After registering the .dll with the following command, it will add a new property page, called Additional Account Info, to the user properties page in Active Directory Users and Computers (or ADUC for short).
Here's the original link:
http://www.petri.co.il/view_additional_use...ion_in_aduc.htm
0 -
wait... straighten me out on this again. Is the Web Server you are connecting out in the DMZ or is it internal?
0 -
If you run DCPromo on a server that is already a DC, isn't the only option you get to choose is to demote the DC to a Member Server?
Yes, you are correct. You first have to demote the domain controller with dcpromo.
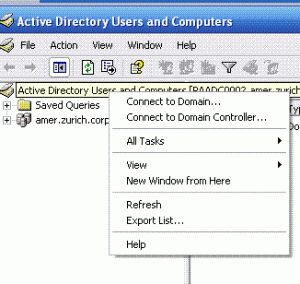
Also, you mentioned that you wanted to view two domains in AD Users & Computers... In case you weren't aware, you can connect to different Domains from that console:
0 -
Welcome softcd.... Enjoy!
0 -
Go ahead and use that API. There are several ways to accomplish this task. I think doing it programmatically will be best.
0 -
Using code to perform the function might be easier... Here's a decent snippet.
'RegObj must be installed to run this script.
'http://msdn.microsoft.com/vbasic/downloads/addins/default.asp
'Author.Mike Ford.08.26.03
Dim rserver
const objKey = "\HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon\"
const name = "DefaultUserName"
strComputer = Inputbox("Remote Computer?")
If strComputer = "" Then
WScript.Quit
End If
Set fso = WScript.CreateObject("RegObj.Registry")
Set connect = fso.RemoteRegistry(strComputer)
Set username = connect.RegKeyFromString(objKey).Values(name)
wscript.echo "The Last Logged on User was: " & username
0 -
Sysinternals has a command line tool that can return the locally logged on user (and more info as well). You can use this to create a text dumpfile and parse it to pull out the relevent data:
PsLoggedOn
You can determine who is using resources on your local computer with the "net" command ("net session"), however, there is no built-in way to determine who is using the resources of a remote computer. In addition, NT comes with no tools to see who is logged onto a computer, either locally or remotely. PsLoggedOn is an applet that displays both the locally logged on users and users logged on via resources for either the local computer, or a remote one. If you specify a user name instead of a computer, PsLoggedOn searches the computers in the network neighborhood and tells you if the user is currently logged on.
PsLoggedOn's definition of a locally logged on user is one that has their profile loaded into the Registry, so PsLoggedOn determines who is logged on by scanning the keys under the HKEY_USERS key. For each key that has a name that is a user SID (security Identifier), PsLoggedOn looks up the corresponding user name and displays it. To determine who is logged onto a computer via resource shares, PsLoggedOn uses the NetSessionEnum API. Note that PsLoggedOn will show you as logged on via resource share to remote computers that you query because a logon is required for PsLoggedOn to access the Registry of a remote system.
Installation
Copy PsLoggedOn onto your executable path and type "psloggedon".
PsLoggedOn works on NT 4.0, Windows 2000 and Windows XP.
Usage
usage: psloggedon [-?] [-l] [-x] [\\computername | username]
-l
Shows only local logons instead of both local and network resource logons.
-x
Don't show logon times.
\\computername
Specifies the name of the computer for which to list logon information.
username
If you specify a user name PsLoggedOn searches the network for computers to which that user is loggedon. This is useful if you want to ensure that a particular user is not logged on when you are about to change their user profile configuration.
0 -
My guess is that its stored in the registry... I think you'll be on your own figuring this one out.
Just create a scheduled scan and then jump into the registry a poke around in the Symantec key.
0

Firefoxes google
in Software Hangout
Posted
You can do this from inside the Tabbrowser Preferences extension. Just download it, configure, and enjoy