Content Type
Profiles
Forums
Events
Everything posted by JorgeA
-
On the security/privacy front: Police keep quiet about cell-tracking technology Worried about the government? Internet giants also dip their hands in the cookie jar The news is not ALL bad, though: --JorgeA
-
That's amazing!! You're right, it makes sense to conclude from this news that they must have tons of unsold inventory. It also suggests what their view is of the kinds of people who are the target market for Surface devices (i.e., unlikely to ever find this out, except for articles in the press). --JorgeA
-

Scan Android phone on Windows PC?
JorgeA replied to JorgeA's topic in Malware Prevention and Security
Thanks a bunch, jaclaz. I installed the F-Droid app manager, then used it to install the Ghost Commander, and then I used that to install Eset Mobile Security. Much appreciated! --JorgeA -

Scan Android phone on Windows PC?
JorgeA replied to JorgeA's topic in Malware Prevention and Security
Update: I'm facing what we could call a recursive (or question-begging) issue. The information for installing the ESET security app outside the Google store suggests using a file manager to browse to the APK and then tapping to Install. OK, I can understand that. But, if using a file manager is the way to install an app without the Google store, then how do you install the file manager itself without the Google store? By definition, before that's installed there is not yet a file manager that you can use to browse to the file manager app in order to install it. I have checked all the file manager apps available on that F-Droid site, and none of them give any instructions as to how to install their apps. The method must be so simple to do that it requires no explanation. But, as an Android noob, I don't know what that method might be. I suppose I could start downloading and tapping and see what happens, but I prefer to first understand the process, lest I screw things up on the phone. --JorgeA -
Very good!! Paul elaborates on his change of mind in Windows Weekly 349: [emphasis added] --JorgeA
-

Scan Android phone on Windows PC?
JorgeA replied to JorgeA's topic in Malware Prevention and Security
Thanks very much, jaclaz Step 4 of the first link that you kindly provided requires me to Obviously, I'd rather install a file browser without signing up for the Google store. The F-Droid repository that you also linked to, seems to have a couple of file browsers listed. The most promising-looking one I've seen so far is Ghost Commander. But I'd still be curious to know the answer to the question that I did ask. --JorgeA -
I've been using my first smartphone for a few months now, and as my use of it increases I feel an increasing need to protect it with some kind of antivirus/antimalware solution. At the same time, I would prefer not to register for the Google Store (or whatever they call it), as I have zero confidence that Google will not continue to track me and monitor my travels around the Web, no matter whether I've "signed out" of their store. Thus, the following occurred to me: Linux to Windows; how about Windows to Linux? We already have Linux-based live CDs that are used to virus-scan Windows PCs, so could it work in the other direction: might it be possible to scan an Android (Linux) phone from a Windows PC? Linux to Linux? Barring that, how about connecting the Android phone to the computer, then booting up an antivirus Linux live CD and scanning the phone with it? I do know about sideloading Android apps outside of the Google store, but AFAICT you need first to install a file explorer app in order to do that, which requires a visit to the Google store (thus defeating the purpose). What I'd like to focus on here is whether it's possible to scan an Android phone for malware with a Linux or Windows AV application. Any thoughts? is this a silly/crazy idea? --JorgeA
-
Paul Thurrott takes the clearest step yet toward advocating for the REAL Windows: In Windows, Veritas --JorgeA
-
Hey Tony, If it was CP/M, it must have been a different OS than the one I had for the Sanyo. Huh, just occurred to me that maybe lawyers got involved at some point to sort things out between DOS Plus and DS-DOS PLUS. Amstrad. That's another blast from the past! My second computer was a PC6400 model. It came with MS-DOS (I forget which version) and (on a separate diskette) the GEM GUI, which was outside the Microsoft universe. Looking it up, it must have come with a version of CP/M. Oh yeah, that too was from Digital Research. I remember thinking at the time, "What do I need this gwee thing for?? It's just something to get in-between me and my files." @jaclaz: Nice research work! The first link is that same company. --JorgeA EDIT: typo
-
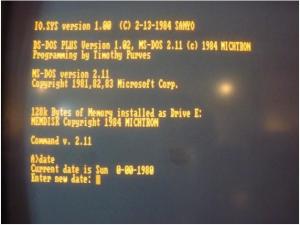
Here's a screenshot of my Sanyo MBC-550 booting up: Ah, the ol' girl still works. Click on the image for a clearer view. --JorgeA
-
The entire article can be read here: http://phys.org/news/2014-03-wpa2-wireless.html#jCp Not quite as easy breaking into a WEP system, but it appears that it isn't all that hard for a determined party to breach. Wouldn't want to point any fingers, but I think we can all think of several alphabet agencies of various governments that would fall into that category. Didn't mean to ruin everyone's weekend. bpalone Thanks for the heads-up. The following excerpt states very well what I have believed every since I started thinking about wired vs. wireless networking: Not that a wired connection is totally secure -- just that it's more secure than a wireless one. --JorgeA
-
To me, the nub of the issue is this: Microsoft: Going through your 'private' emails is like searching 'ourselves' Sorry, but it is NOT searching "yourselves" when it's somebody else's e-mail. Sure, the e-mail may be stored in your servers, but you have rented or lent out the servers for other people to place information on them, therefore you have no property right in that information. If you want to reclaim your server drives, then close out everybody's accounts and stick the drives where they may fit best. Oh,and if you want to pull out the cr*p about the TOS allowing you to do this -- yes by all means proclaim it far and wide. Put it prominently in every TV and Web ad for your e-mail service, that you're allowed to go through people's stuff at your sole discretion. Do this for a couple of years, and then let's see how many users you're left with at the end. --JorgeA
-
Speaking of Y2K: I have a special version of DOS called DS-DOS Plus, published in 1984 by a long-forgotten company called MichTron. This OS, based on MS-DOS 2.11, enabled the Sanyo MBC computer (some may remember it as the "silver fox") to read from and write to quad-density, 10-sector (800K) floppy disks. If you slide one of these OS disks into the drive, start up the machine, and type in today's 21st-century date, it will accept it without blinking and if you type "date" at the command prompt it will give you the right day of the week. That was back in 1983. These guys looked further ahead than BillG and his crack team of programmers. --JorgeA
-
A funny and fitting description of this move by Microsoft (source): --JorgeA
-
More about Microsoft's attempts to control what you may put on your computer, and to make you install (Win8) programs through their Windows Store -- From Windows Weekly #347: Mary Jo says that a project to deal with this problem had been taken down, but it seems to be (back?) up at https://bootybay.codeplex.com/. --JorgeA
-
Another reason to block tracking in one's browser: A Close Look at the NSA’s Most Powerful Internet Attack Tool Useful background material on this topic: Our Government Has Weaponized the Internet. Here’s How They Did It What can be done about it? --JorgeA
-
Excellent. If I may quote it here: Reply: --JorgeA
-
Again my emphasis. Almost sounds like JorgeA is going to be practicing his Penguin waddle. [...] You may be right. About that second alternative, I would definitely not be happy about being able to keep the Desktop but having to receive Windows Updates only through the Windows Store. --JorgeA
-
Now, I question if the article was well researched, as it sticks to my feeble mind that something has been said around here about the embedded being supported for a few more years. That being said here is another quote: Just found it interesting and thought I would point it out. Could this be what you're thinking of? --JorgeA
-
A follow-up on the story about the Windows leaker who got busted after Microsoft went through his Hotmail: Microsoft caught up in fresh privacy storm My reaction: to the blogger, that's what can happen when you keep your e-mail files in the cloud. Anybody who might have any interest in reading the whole article, I suggest you do it soon as FT articles seem to go behind a paywall fairly quickly. --JorgeA
-
Wow. That is very cool and very scary. Soon we'll have to start living and traveling underground. --JorgeA
-
That's exactly who I thought it might be. He seemed to suddenly disappear, for no apparent reason, around that time. Looks like these guys' gossip interest ran way ahead of their security mindfulness: Sheesh, if you're going to be engaging in this cloak-and-dagger stuff, you need to be a little more cautious than that. --JorgeA
-
Cybersecurity (not): Without proper security measures, smart homes are just begging to be targets Bet the NSA's counting on that. The infrastructure for 1984 is going up all around us and we are eager participants in its construction. All it will take is a sufficiently determined party in charge for whom the ends justify the means. --JorgeA
-
Cyberprivacy (not): NSA surveillance program reaches ‘into the past’ to retrieve, replay phone calls Speaking of the cloud: [emphasis added] Too bad they're not putting the stuff on SkyDrive. --JorgeA
-
That is at the same time unbelievable and so typical. ---JorgeA