Content Type
Profiles
Forums
Events
Posts posted by freakedenough
-
-
I am bad at searching in 5 Threads with 200 pages each. Did anyone try to get HVC decoded using Basilisk Serpent 52 on Vista?
Austrian Broadcasting Company uses DRM protected webstreams for live TV https://tvthek.orf.at/livestreams
I did find the thread about ESR52 and Adobe DRM plugin for H264. Its installed manually, but I dont think it matters here.
Cannot play media. No decoders for requested formats: video/mp4;codecs="hvc1", video/mp4;codecs="hev1.1.6.L93.B0", video/mp4;codecs="hvc1", video/mp4;codecs="hev1.1.6.L93.B0", application/vnd.apple.mpegURL, application/x-mpegURL, audio/mpegurl, audio/x-mpegurlWass there ever a 52ESR plugin for this?
0 -
did you add the tls 1.2 registry keys and verified they are visible and checked in internet options after a reboot?
https://www.windowspage.de/tipps/010303.html
https://www.retrospace.net/infoseiten/readm.php?id=98
this should automatically enable tls 1.2 in all apps using winhttp
keeping ie7 is impossible, 8 on xp and 9 on vista is required
1 -
it works again
 at least the sidebar gadget url. the one for origami is still dead.
1
at least the sidebar gadget url. the one for origami is still dead.
1 -
Its because the URL that is being called by the Gadget is dysfunctional since a few days:
http://weather.service.msn.com/data.aspx?src=vista&wealocations=FR:DE_Berlin&weadegreetype=C&culture=de-DEThe same applies to the Origami Experience 2.0 Weather Gadget, similar Domain:
http://weather.partners.msn.com/data.aspx?outputview=forecast&wealocations=wc:AUXX0025&src=UMPC&weadegreetype=C&culture=de-ATUnfortunately, one can only hope that MSN will fix it. Due to Microsoft's restriction to reroute Microsoft-owned Domains via HOSTS file, it will be hard (without involving a HTTP proxy) to redirect the Gadgets to a different Server which is able to return a XML payload which can be read by the Gadget. At least for the hardcoded Origami Now Gadget. The Sidebar one can be edited in HTML/JS.
I meanwhile switched to a 3rd party Gadget that is still maintained: https://00ff00.de/?page_id=658
2 -
Hi guys, does anybody know how to decrypt old Compaq SmartStart installation files?
Compaq used to encrypt several important files and implemented custom installers which asked for a Program License Diskette and an "Activation Key" on their COA which was bound to the SERIAL.TXT and corresponding LOK/DAT file on this Diskette, e.g. their OEM NT 3.1 disk. These disks also included drivers and OEM software which was and is relevant if you have such an old PC/Server.
Long story short, the COA is long gone, I have the disk but no key. Is there another way to decrypt the files?
0 -
someone over there https://forums.mydigitallife.net/threads/restore-windows-update-for-vista.82336/ made a WU patcher to enable its function again. you can get it from here https://1drv.ms/u/s!AubsH71V5bOkkmIPXEQi0fbX_45f?e=5KEwYg
i canconfirm that it works for me.
2 -
2020-10 – Monatliches Sicherheitsqualitätsrollup für Windows Server 2008 für x86-basierte Systeme (KB4580378)
2020-10 – Sicherheitsqualitätsupdate für Windows Server 2008 für x86-basierte Systeme (KB4580385)
2020-10-25 16:30:05:772 1192 f4c Shutdwn user declined update at shutdown 2020-10-25 16:30:05:772 1192 f4c AU AU initiates service shutdown 2020-10-25 16:30:05:772 1192 f4c AU ########### AU: Uninitializing Automatic Updates ########### 2020-10-25 16:30:05:803 1192 f4c Report CWERReporter finishing event handling. (00000000) 2020-10-25 16:30:05:803 1192 f4c Service ********* 2020-10-25 16:30:05:803 1192 f4c Service ** END ** Service: Service exit [Exit code = 0x240001] 2020-10-25 16:30:05:803 1192 f4c Service ************* 2020-10-25 16:33:40:387 3568 cc8 Misc =========== Logging initialized (build: 7.6.7600.256, tz: +0100) =========== 2020-10-25 16:33:40:388 3568 cc8 Misc = Process: C:\Windows\system32\wusa.exe 2020-10-25 16:33:40:388 3568 cc8 Misc = Module: C:\Windows\system32\wuapi.dll 2020-10-25 16:33:40:386 3568 cc8 COMAPI ----------- COMAPI: IUpdateServiceManager::AddScanPackageService ----------- 2020-10-25 16:33:40:388 3568 cc8 COMAPI - ServiceName = Eigenständiges Windows-Updateinstallationsprogramm 2020-10-25 16:33:40:388 3568 cc8 COMAPI - ScanFileLocation = C:\703105c0b590cd5475\wsusscan.cab 2020-10-25 16:33:40:413 1180 dc0 Misc =========== Logging initialized (build: 7.6.7600.256, tz: +0100) =========== 2020-10-25 16:33:40:413 1180 dc0 Misc = Process: C:\Windows\system32\svchost.exe 2020-10-25 16:33:40:413 1180 dc0 Misc = Module: c:\windows\system32\wuaueng.dll 2020-10-25 16:33:40:413 1180 dc0 Service ************* 2020-10-25 16:33:40:413 1180 dc0 Service ** START ** Service: Service startup 2020-10-25 16:33:40:413 1180 dc0 Service ********* 2020-10-25 16:33:40:431 1180 dc0 Agent * WU client version 7.6.7600.256 2020-10-25 16:33:40:431 1180 dc0 Agent * Base directory: C:\Windows\SoftwareDistribution 2020-10-25 16:33:40:432 1180 dc0 Agent * Access type: No proxy 2020-10-25 16:33:40:433 1180 dc0 Agent * Network state: Connected 2020-10-25 16:33:40:502 1180 66c Report CWERReporter::Init succeeded 2020-10-25 16:33:40:502 1180 66c Agent *********** Agent: Initializing Windows Update Agent *********** 2020-10-25 16:33:40:502 1180 66c Agent *********** Agent: Initializing global settings cache *********** 2020-10-25 16:33:40:502 1180 66c Agent * WSUS server: <NULL> 2020-10-25 16:33:40:502 1180 66c Agent * WSUS status server: <NULL> 2020-10-25 16:33:40:502 1180 66c Agent * Target group: (Unassigned Computers) 2020-10-25 16:33:40:502 1180 66c Agent * Windows Update access disabled: No 2020-10-25 16:33:40:502 1180 66c DnldMgr Download manager restoring 0 downloads 2020-10-25 16:33:40:509 1180 66c Misc Validating signature for C:\Windows\SoftwareDistribution\ScanFile\6da38975-319b-4369-bcb6-68cf05a1a9b3\Source.cab: 2020-10-25 16:33:40:562 1180 66c Misc Microsoft signed: Yes 2020-10-25 16:33:40:580 1180 66c DtaStor Default service for AU is {7971F918-A847-4430-9279-4A52D1EFE18D} 2020-10-25 16:33:40:582 3568 cc8 COMAPI - Added scan package service, ServiceID = {6DA38975-319B-4369-BCB6-68CF05A1A9B3} Third party service 2020-10-25 16:33:40:583 3568 cc8 COMAPI ------------- 2020-10-25 16:33:40:583 3568 cc8 COMAPI -- START -- COMAPI: Search [ClientId = wusa] 2020-10-25 16:33:40:583 3568 cc8 COMAPI --------- 2020-10-25 16:33:40:589 3568 cc8 COMAPI <<-- SUBMITTED -- COMAPI: Search [ClientId = wusa] 2020-10-25 16:33:40:721 1180 dc0 Report *********** Report: Initializing static reporting data *********** 2020-10-25 16:33:40:721 1180 dc0 Report * OS Version = 6.0.6003.2.0.65792 2020-10-25 16:33:40:721 1180 dc0 Report * OS Product Type = 0x00000001 2020-10-25 16:33:40:760 1180 dc0 Report * Computer Brand = Dell Inc. 2020-10-25 16:33:40:760 1180 dc0 Report * Computer Model = XPS M1330 2020-10-25 16:33:40:764 1180 dc0 Report * Bios Revision = A15 2020-10-25 16:33:40:764 1180 dc0 Report * Bios Name = Phoenix ROM BIOS PLUS Version 1.10 A15 2020-10-25 16:33:40:764 1180 dc0 Report * Bios Release Date = 2008-12-26T00:00:00 2020-10-25 16:33:40:764 1180 dc0 Report * Locale ID = 3079 2020-10-25 16:33:40:767 1180 3b0 Agent ************* 2020-10-25 16:33:40:767 1180 3b0 Agent ** START ** Agent: Finding updates [CallerId = wusa] 2020-10-25 16:33:40:767 1180 3b0 Agent ********* 2020-10-25 16:33:40:767 1180 3b0 Agent * Online = Yes; Ignore download priority = No 2020-10-25 16:33:40:767 1180 3b0 Agent * Criteria = "IsInstalled=0" 2020-10-25 16:33:40:767 1180 3b0 Agent * ServiceID = {6DA38975-319B-4369-BCB6-68CF05A1A9B3} Third party service 2020-10-25 16:33:40:767 1180 3b0 Agent * Search Scope = {Machine} 2020-10-25 16:33:40:990 1180 3b0 PT +++++++++++ PT: Synchronizing server updates +++++++++++ 2020-10-25 16:33:40:990 1180 3b0 PT + Offline serviceId = {6DA38975-319B-4369-BCB6-68CF05A1A9B3} 2020-10-25 16:33:40:990 1180 3b0 PT WARNING: Cached cookie has expired or new PID is available 2020-10-25 16:33:47:263 1180 3b0 PT +++++++++++ PT: Synchronizing extended update info +++++++++++ 2020-10-25 16:33:47:264 1180 3b0 PT + Offline serviceId = {6DA38975-319B-4369-BCB6-68CF05A1A9B3} 2020-10-25 16:33:47:396 1180 3b0 Agent * Added update {E38CA2E6-3086-4328-8037-282EB75BA2E0}.501 to search result 2020-10-25 16:33:47:396 1180 3b0 Agent * Found 1 updates and 58 categories in search; evaluated appl. rules of 127 out of 301 deployed entities 2020-10-25 16:33:47:399 1180 3b0 Agent ********* 2020-10-25 16:33:47:399 1180 3b0 Agent ** END ** Agent: Finding updates [CallerId = wusa] 2020-10-25 16:33:47:399 1180 3b0 Agent ************* 2020-10-25 16:33:47:401 3568 f04 COMAPI >>-- RESUMED -- COMAPI: Search [ClientId = wusa] 2020-10-25 16:33:47:406 1180 3b0 Report CWERReporter finishing event handling. (00000000) 2020-10-25 16:33:47:414 3568 f04 COMAPI - Updates found = 1 2020-10-25 16:33:47:415 3568 f04 COMAPI --------- 2020-10-25 16:33:47:415 3568 f04 COMAPI -- END -- COMAPI: Search [ClientId = wusa] 2020-10-25 16:33:47:415 3568 f04 COMAPI ------------- 2020-10-25 16:33:49:169 1180 66c DnldMgr *********** DnldMgr: Copy update to cache [UpdateId = {31CD24F7-1593-41FF-AD6F-4748C34C897E}.501] *********** 2020-10-25 16:33:49:235 1180 66c DnldMgr Asking handler to generate non-range requests. 2020-10-25 16:33:49:235 1180 66c Handler Generating request for CBS update 31CD24F7-1593-41FF-AD6F-4748C34C897E in sandbox C:\Windows\SoftwareDistribution\Download\8437763486ccfb1587bf58f999acfa8b_ctc 2020-10-25 16:33:49:236 1180 66c Handler Selecting self-contained because update does not have express payload. 2020-10-25 16:33:49:236 1180 66c Handler Selected payload type is ptSelfContained 2020-10-25 16:33:49:236 1180 66c Handler Detected download state is dsStart 2020-10-25 16:33:49:236 1180 66c Handler Adding Windows6.0-KB4580385-x86.cab (entire file) to request list. 2020-10-25 16:33:49:236 1180 66c Handler Request generation for CBS update complete with hr=0x0 and pfResetSandbox=0 2020-10-25 16:33:49:436 1180 66c Misc Validating signature for C:\Windows\SoftwareDistribution\Download\8437763486ccfb1587bf58f999acfa8b_ctc\Windows6.0-KB4580385-x86.cab: 2020-10-25 16:33:50:340 1180 66c Misc Microsoft signed: Yes 2020-10-25 16:33:50:341 1180 66c DnldMgr Asking handler to generate non-range requests. 2020-10-25 16:33:50:341 1180 66c Handler Generating request for CBS update 31CD24F7-1593-41FF-AD6F-4748C34C897E in sandbox C:\Windows\SoftwareDistribution\Download\8437763486ccfb1587bf58f999acfa8b_ctc 2020-10-25 16:33:50:341 1180 66c Handler Selecting self-contained because update does not have express payload. 2020-10-25 16:33:50:341 1180 66c Handler Selected payload type is ptSelfContained 2020-10-25 16:33:50:341 1180 66c Handler Detected download state is dsHavePackage 2020-10-25 16:33:50:341 1180 66c Handler Request generation for CBS update complete with hr=0x0 and pfResetSandbox=0 2020-10-25 16:33:50:363 3568 cc8 COMAPI ------------- 2020-10-25 16:33:50:363 3568 cc8 COMAPI -- START -- COMAPI: Install [ClientId = wusa] 2020-10-25 16:33:50:363 3568 cc8 COMAPI --------- 2020-10-25 16:33:50:363 3568 cc8 COMAPI - Allow source prompts: Yes; Forced: No; Force quiet: No 2020-10-25 16:33:50:363 3568 cc8 COMAPI - Updates in request: 1 2020-10-25 16:33:50:363 3568 cc8 COMAPI - ServiceID = {6DA38975-319B-4369-BCB6-68CF05A1A9B3} Third party service 2020-10-25 16:33:50:366 3568 cc8 COMAPI - Updates to install = 1 2020-10-25 16:33:50:366 1180 3d8 Agent ************* 2020-10-25 16:33:50:366 3568 cc8 COMAPI <<-- SUBMITTED -- COMAPI: Install [ClientId = wusa] 2020-10-25 16:33:50:366 1180 3d8 Agent ** START ** Agent: Installing updates [CallerId = wusa] 2020-10-25 16:33:50:366 1180 3d8 Agent ********* 2020-10-25 16:33:50:366 1180 3d8 Agent * Updates to install = 1 2020-10-25 16:33:50:370 1180 3d8 Agent * Title = Sicherheitsupdate für Windows (KB4580385) 2020-10-25 16:33:50:370 1180 3d8 Agent * UpdateId = {E38CA2E6-3086-4328-8037-282EB75BA2E0}.501 2020-10-25 16:33:50:370 1180 3d8 Agent * Bundles 1 updates: 2020-10-25 16:33:50:370 1180 3d8 Agent * {31CD24F7-1593-41FF-AD6F-4748C34C897E}.501 2020-10-25 16:33:50:559 1180 3d8 Handler Attempting to create remote handler process as DELL\Besitzer in session 1 2020-10-25 16:33:50:632 1180 3d8 DnldMgr Preparing update for install, updateId = {31CD24F7-1593-41FF-AD6F-4748C34C897E}.501. 2020-10-25 16:33:50:640 2396 b28 Misc =========== Logging initialized (build: 7.6.7600.256, tz: +0100) =========== 2020-10-25 16:33:50:640 2396 b28 Misc = Process: C:\Windows\system32\wuauclt.exe 2020-10-25 16:33:50:640 2396 b28 Misc = Module: C:\Windows\system32\wuaueng.dll 2020-10-25 16:33:50:639 2396 b28 Handler ::::::::::::: 2020-10-25 16:33:50:640 2396 b28 Handler :: START :: Handler: CBS Install 2020-10-25 16:33:50:640 2396 b28 Handler ::::::::: 2020-10-25 16:33:50:642 2396 b28 Handler Starting install of CBS update 31CD24F7-1593-41FF-AD6F-4748C34C897E 2020-10-25 16:33:50:800 2396 b28 Handler CBS package identity: Package_for_KB4580385~31bf3856ad364e35~x86~~6.0.1.10 2020-10-25 16:33:50:801 2396 b28 Handler Installing self-contained with source=C:\Windows\SoftwareDistribution\Download\8437763486ccfb1587bf58f999acfa8b\Windows6.0-KB4580385-x86.cab, workingdir=C:\Windows\SoftwareDistribution\Download\8437763486ccfb1587bf58f999acfa8b\inst 2020-10-25 16:34:25:483 1180 dc0 AU ########### AU: Initializing Automatic Updates ########### 2020-10-25 16:34:25:484 1180 dc0 AU # Approval type: Pre-download notify (User preference) 2020-10-25 16:34:25:484 1180 dc0 AU # Will interact with non-admins (Non-admins are elevated (User preference)) 2020-10-25 16:34:25:484 1180 dc0 AU # Will display featured software notifications (User preference) 2020-10-25 16:34:25:484 1180 dc0 AU Initializing featured updates 2020-10-25 16:34:25:484 1180 dc0 AU Found 0 cached featured updates 2020-10-25 16:34:25:485 1180 dc0 AU AU setting pending client directive to 'Unable To Detect' 2020-10-25 16:34:25:485 1180 dc0 AU AU finished delayed initialization 2020-10-25 16:34:25:485 1180 dc0 AU ############# 2020-10-25 16:34:25:485 1180 dc0 AU ## START ## AU: Search for updates 2020-10-25 16:34:25:485 1180 dc0 AU ######### 2020-10-25 16:34:25:487 1180 dc0 AU <<## SUBMITTED ## AU: Search for updates [CallId = {8DE9D592-19BD-4632-8800-518343E03C23}] 2020-10-25 16:34:25:487 1180 3b0 Agent ************* 2020-10-25 16:34:25:487 1180 3b0 Agent ** START ** Agent: Finding updates [CallerId = AutomaticUpdates] 2020-10-25 16:34:25:487 1180 3b0 Agent ********* 2020-10-25 16:34:25:488 1180 3b0 Agent * Online = No; Ignore download priority = No 2020-10-25 16:34:25:488 1180 3b0 Agent * Criteria = "IsInstalled=0 and DeploymentAction='Installation' or IsPresent=1 and DeploymentAction='Uninstallation' or IsInstalled=1 and DeploymentAction='Installation' and RebootRequired=1 or IsInstalled=0 and DeploymentAction='Uninstallation' and RebootRequired=1" 2020-10-25 16:34:25:488 1180 3b0 Agent * ServiceID = {7971F918-A847-4430-9279-4A52D1EFE18D} Third party service 2020-10-25 16:34:25:488 1180 3b0 Agent * Search Scope = {Machine} 2020-10-25 16:34:27:686 1180 3b0 Agent * Found 0 updates and 0 categories in search; evaluated appl. rules of 0 out of 0 deployed entities 2020-10-25 16:34:27:689 1180 3b0 Agent ********* 2020-10-25 16:34:27:689 1180 3b0 Agent ** END ** Agent: Finding updates [CallerId = AutomaticUpdates] 2020-10-25 16:34:27:689 1180 3b0 Agent ************* 2020-10-25 16:34:27:689 1180 3e4 AU >>## RESUMED ## AU: Search for updates [CallId = {8DE9D592-19BD-4632-8800-518343E03C23}] 2020-10-25 16:34:27:689 1180 3e4 AU # 0 updates detected 2020-10-25 16:34:27:689 1180 3e4 AU ######### 2020-10-25 16:34:27:689 1180 3e4 AU ## END ## AU: Search for updates [CallId = {8DE9D592-19BD-4632-8800-518343E03C23}] 2020-10-25 16:34:27:689 1180 3e4 AU ############# 2020-10-25 16:34:27:689 1180 3e4 AU No featured updates notifications to show 2020-10-25 16:34:30:485 1180 3b0 Report REPORT EVENT: {EAC1BB5C-F273-4077-A2DC-2929E53B9FD3} 2020-10-25 16:34:25:485+0100 1 202 102 {00000000-0000-0000-0000-000000000000} 0 0 AutomaticUpdates Success Content Install Reboot completed. 2020-10-25 16:34:30:486 1180 3b0 Report CWERReporter finishing event handling. (00000000) 2020-10-25 16:34:40:501 1180 dc0 AU Launched new AU client for directive 'Unable To Detect', session id = 0x1 2020-10-25 16:34:43:486 2396 ae8 Handler FATAL: CBS called Error with 0x80070490, 2020-10-25 16:34:44:074 2396 b28 Handler FATAL: Completed install of CBS update with type=0, requiresReboot=0, installerError=1, hr=0x80070490 2020-10-25 16:34:44:092 2396 b28 Handler ::::::::: 2020-10-25 16:34:44:092 2396 b28 Handler :: END :: Handler: CBS Install 2020-10-25 16:34:44:092 2396 b28 Handler ::::::::::::: 2020-10-25 16:34:44:096 1180 3d8 Agent ********* 2020-10-25 16:34:44:096 1180 3d8 Agent ** END ** Agent: Installing updates [CallerId = wusa] 2020-10-25 16:34:44:096 1180 3d8 Agent ************* 2020-10-25 16:34:44:096 1180 dc0 AU Triggering Offline detection (non-interactive) 2020-10-25 16:34:44:096 1180 dc0 AU ############# 2020-10-25 16:34:44:096 1180 dc0 AU ## START ## AU: Search for updates 2020-10-25 16:34:44:096 1180 dc0 AU ######### 2020-10-25 16:34:44:098 3568 cc4 COMAPI >>-- RESUMED -- COMAPI: Install [ClientId = wusa] 2020-10-25 16:34:44:098 3568 cc4 COMAPI - Install call complete (succeeded = 0, succeeded with errors = 0, failed = 1, unaccounted = 0) 2020-10-25 16:34:44:098 3568 cc4 COMAPI - Reboot required = No 2020-10-25 16:34:44:098 3568 cc4 COMAPI - WARNING: Exit code = 0x00000000; Call error code = 0x80240022 2020-10-25 16:34:44:098 3568 cc4 COMAPI --------- 2020-10-25 16:34:44:098 3568 cc4 COMAPI -- END -- COMAPI: Install [ClientId = wusa] 2020-10-25 16:34:44:098 1180 dc0 AU <<## SUBMITTED ## AU: Search for updates [CallId = {847AF9C6-E777-4F25-A2D1-DE10A9FE16BF}] 2020-10-25 16:34:44:098 3568 cc4 COMAPI ------------- 2020-10-25 16:34:44:099 1180 3b0 Agent ************* 2020-10-25 16:34:44:099 1180 3b0 Agent ** START ** Agent: Finding updates [CallerId = AutomaticUpdates] 2020-10-25 16:34:44:099 1180 3b0 Agent ********* 2020-10-25 16:34:44:099 1180 3b0 Agent * Online = No; Ignore download priority = No 2020-10-25 16:34:44:099 1180 3b0 Agent * Criteria = "IsInstalled=0 and DeploymentAction='Installation' or IsPresent=1 and DeploymentAction='Uninstallation' or IsInstalled=1 and DeploymentAction='Installation' and RebootRequired=1 or IsInstalled=0 and DeploymentAction='Uninstallation' and RebootRequired=1" 2020-10-25 16:34:44:099 1180 3b0 Agent * ServiceID = {7971F918-A847-4430-9279-4A52D1EFE18D} Third party service 2020-10-25 16:34:44:099 1180 3b0 Agent * Search Scope = {Machine} 2020-10-25 16:34:44:719 1180 3b0 Agent * Found 0 updates and 0 categories in search; evaluated appl. rules of 0 out of 0 deployed entities 2020-10-25 16:34:44:722 1180 3b0 Agent ********* 2020-10-25 16:34:44:722 1180 3b0 Agent ** END ** Agent: Finding updates [CallerId = AutomaticUpdates] 2020-10-25 16:34:44:722 1180 3b0 Agent ************* 2020-10-25 16:34:44:723 1180 3e4 AU >>## RESUMED ## AU: Search for updates [CallId = {847AF9C6-E777-4F25-A2D1-DE10A9FE16BF}] 2020-10-25 16:34:44:723 1180 3e4 AU # 0 updates detected 2020-10-25 16:34:44:723 1180 3e4 AU ######### 2020-10-25 16:34:44:723 1180 3e4 AU ## END ## AU: Search for updates [CallId = {847AF9C6-E777-4F25-A2D1-DE10A9FE16BF}] 2020-10-25 16:34:44:723 1180 3e4 AU ############# 2020-10-25 16:34:44:723 1180 3e4 AU No featured updates notifications to show 2020-10-25 16:34:49:098 1180 3b0 Report REPORT EVENT: {F026D04C-83C1-4CFA-BB51-FC1FE8E32D3C} 2020-10-25 16:34:44:093+0100 1 182 101 {E38CA2E6-3086-4328-8037-282EB75BA2E0} 501 80070490 wusa Failure Content Install Installation Failure: Windows failed to install the following update with error 0x80070490: Sicherheitsupdate für Windows (KB4580385). 2020-10-25 16:34:49:105 1180 3b0 Report WARNING: CWERReporter::HandleEvents - Failed to queue WER report with 0x800700a1 2020-10-25 16:34:49:105 1180 3b0 Report CWERReporter finishing event handling. (800700a1)
both fail with error 0x80070490, any idea?
0 -
Quote
2020-08 Servicing Stack Update für Windows Server 2008 für x86-basierte Systeme(KB4572374).msu
2020-08 Sicherheits- und Qualitätsrollup für .NET Framework 2.0, 3.0 unter Windows Server 2008 SP2 (KB4569766).msu
2020-08 Sicherheitsupdate für .NET Framework 2.0, 3.0 unter Windows Server 2008SP2 (KB4569735).msu
2020-08 – Monatliches Sicherheitsqualitätsrollup für Windows Server 2008 für x86-basierte Systeme (KB4571730).msu
2020-08 – Sicherheitsqualitätsupdate für Windows Server 2008 für x86-basierte Systeme (KB4571746).msu
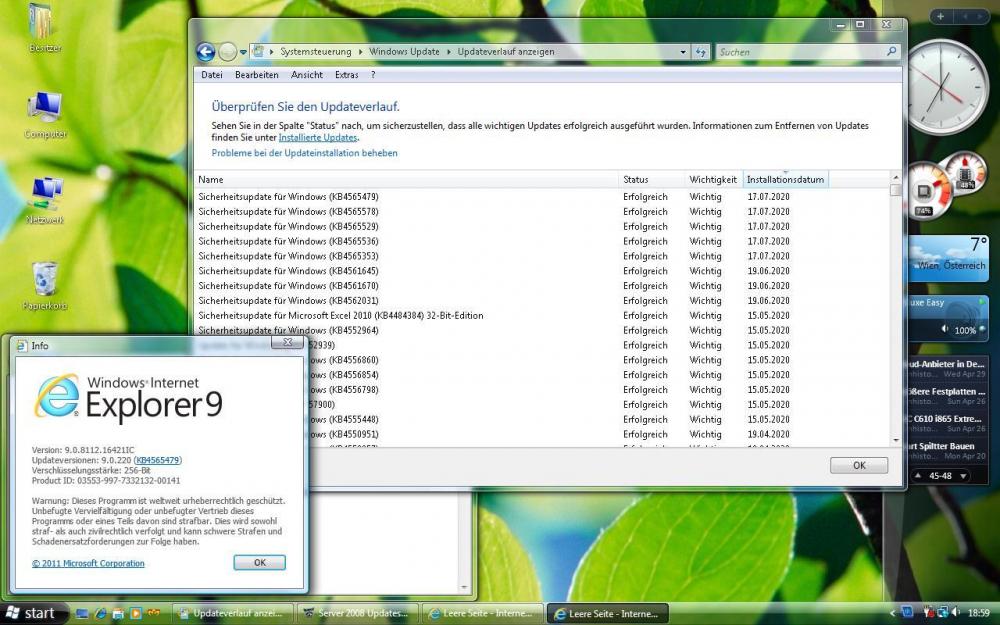
2020-08 Kumulatives Sicherheitsupdate für Internet Explorer 9 für Windows Server 2008 für x86-basierte System (KB4571687).msuaugust 2020 updates work too.
0 -
The DWM flickering/crashes is/are by the way gone since the June updates.
0 -
I cannot confirm, IE9 update worked on my x86 installation.
Since no one posted the June and July update list yet, here we go:
Quote2020-06 Servicing Stack Update für Windows Server 2008 für x86-basierte Systeme (KB4562031)
2020-06 – Monatliches Sicherheitsqualitätsrollup für Windows Server 2008 für x86-basierte Systeme (KB4561670)
2020-06 – Sicherheitsqualitätsupdate für Windows Server 2008 für x86-basierte Systeme (KB4561645)
2020-06 Kumulatives Sicherheitsupdate für Internet Explorer 9 für Windows Server 2008 für x86-basierte System (KB4561603)
2020-07 Servicing Stack Update für Windows Server 2008 für x86-basierte Systeme (KB4565353).msu
2020-07 Kumulatives Sicherheitsupdate für Internet Explorer 9 für Windows Server 2008 für x86-basierte System (KB4565479).msu
2020-07 – Monatliches Sicherheitsqualitätsrollup für Windows Server 2008 für x86-basierte Systeme (KB4565536).msu
2020-07 – Sicherheitsqualitätsupdate für Windows Server 2008 für x86-basierte Systeme (KB4565529).msu2 -
Here we go,
May 2020 Update list:
KB4556854 -- 2020-05 Security Only Quality Update for Windows Server 2008
KB4556860 -- 2020-05 Security Monthly Quality Rollup for Windows Server 2008
KB4555448 -- 2020-05 Servicing Stack Update for Windows Server 2008
KB4556798 -- 2020-05 Cumulative Security Update for Internet Explorer 9 for Windows Server 2008 for x64-based systems (KB4556798)Non-security related updates
KB4557900 -- 2020-05 Update for Windows 8.1, Windows Server 2012 R2, Windows Embedded 8 Standard, Windows Server 2012, Windows 7, Windows Server 2008 R2, and Windows Server 2008 - Morocco Summer time update.NET
KB4552919 -- 2020-05 Security and Quality Rollup for .NET Framework 4.6, 4.6.1, 4.6.2, 4.7, 4.7.1, 4.7.2 for Windows Embedded Standard 7, Windows 7, Windows Server 2008 R2, and Windows Server 2008
KB4552920 -- 2020-05 Security and Quality Rollup for .NET Framework 4.5.2 for Windows Embedded Standard 7, Windows 7, Windows Server 2008 R2, and Windows Server 2008
KB4552939 -- 2020-05 Security and Quality Rollup for .NET Framework 2.0, 3.0 for Windows Server 2008
KB4552951 -- 2020-05 Security Only Update for .NET Framework 4.6 for Windows Embedded Standard 7, Windows 7, Windows Server 2008 R2, and Windows Server 2008
KB4552952 -- 2020-05 Security Only Update for .NET Framework 4.5.2 for Windows Embedded Standard 7, Windows 7, Windows Server 2008 R2, and Windows Server 2008
KB4552964 -- 2020-05 Security Only Update for .NET Framework 2.0, 3.0 for Windows Server 2008
KB4556402 -- 2020-05 Security and Quality Rollup for .NET Framework 2.0, 3.0, 4.5.2, 4.6 for Windows Server 2008
KB4556406 -- 2020-05 Security Only Update for .NET Framework 2.0, 3.0, 4.5.2, 4.6 for Windows Server 2008
1 -
April 2020 Updates:
KB4550951 -- Security Monthly Quality Rollup for Windows Server 2008 https://www.catalog.update.microsoft.com/Search.aspx?q=KB4550951
KB4550957 -- Security Only Quality Update for Windows Server 2008 https://www.catalog.update.microsoft.com/Search.aspx?q=KB4550957
KB4550737 -- Servicing Stack Update for Windows Server 2008 https://www.catalog.update.microsoft.com/Search.aspx?q=KB4550737
KB4550905 -- Cumulative security update for Internet Explorer: April 14, 2020 https://www.catalog.update.microsoft.com/Search.aspx?q=KB4550905
2 -
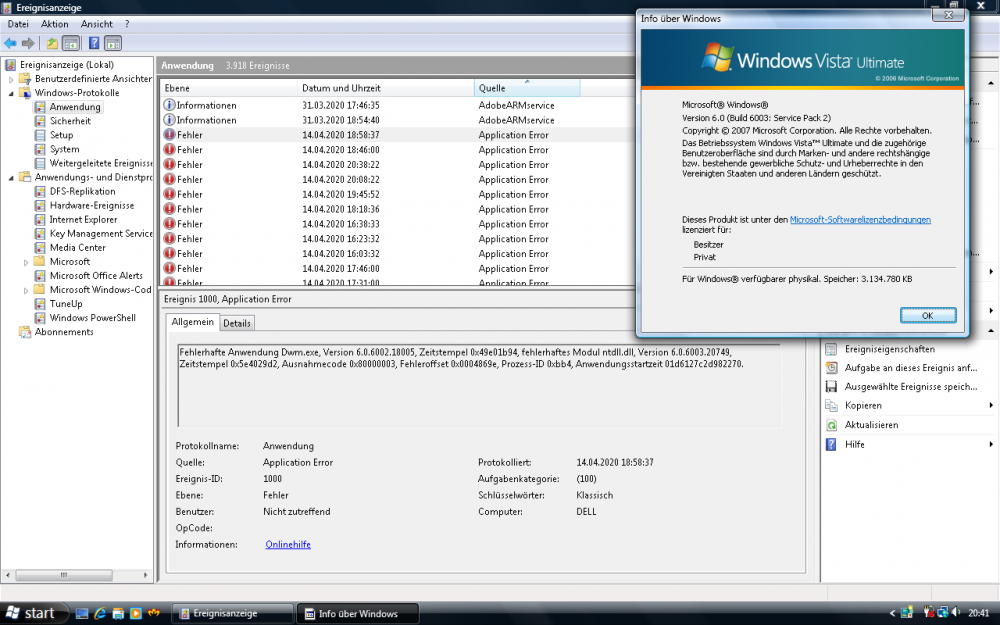
Hey guys, I followed your thread with high interest and installed the update pack from mega.nz link plus the monthly updates till 2020-03 (see down below), but I am getting a DWM crash every 20 minutes, even if its just idle-ing.
Any idea? I tried several Intel GMA 965 drivers, they don't cause it.
2020-01 Servicing Stack Update für Windows Server 2008 für x86-basierte Systeme (KB4536953).msu 2020-01 Monatliches Sicherheitsqualitätsrollup für Windows Server 2008 für x86-basierte Systeme (KB4534303).msu 2020-01 Sicherheitsqualitätsupdate für Windows Server 2008 für x86-basierte Systeme (KB4534312).msu 2020-02 Cumulative Security Update for Internet Explorer 9 for Windows Server 2008 for x86-based systems (KB4537767).msu 2020-02 Servicing Stack Update für Windows Server 2008 für x86-basierte Systeme (KB4537830).msu 2020-02 Monatliches Sicherheitsqualitätsrollup für Windows Server 2008 für x86-basierte Systeme (KB4537810).msu 2020-02 Sicherheitsqualitätsupdate für Windows Server 2008 für x86-basierte Systeme (KB4537822).msu 2020-03 Kumulatives Sicherheitsupdate für Internet Explorer 9 für Windows Server 2008 für x86-basierte System (KB4540671).msu 2020-03 Servicing Stack Update für Windows Server 2008 für x86-basierte Systeme (KB4550736).msu 2020-03 Monatliches Sicherheitsqualitätsrollup für Windows Server 2008 für x86-basierte Systeme (KB4541506).msu 2020-03 Sicherheitsqualitätsupdate für Windows Server 2008 für x86-basierte Systeme (KB4541504).msueventvwr.msc shows:
Fehlerhafte Anwendung Dwm.exe, Version 6.0.6002.18005, Zeitstempel 0x49e01b94, fehlerhaftes Modul ntdll.dll, Version 6.0.6003.20749, Zeitstempel 0x5e4029d2, Ausnahmecode 0x80000003, Fehleroffset 0x0004869e, Prozess-ID 0xbb4, Anwendungsstartzeit 01d6127c2d982270.
translates to:
Disfunctional application Dwm.exe, Version 6.0.6002.18005, timestamp 0x49e01b94, incorrectly working module ntdll.dll, Version 6.0.6003.20749, timestamp 0x5e4029d2, exception code 0x80000003, error offset 0x0004869e, process id 0xbb4, application start timestamp 01d6127c2d982270.
0 -
i read the following text at http://www.vorck.com/hfslip.html
"SETUPAPI.DLL
This is optional, you do not have to have it. If you are an "HFSLIP Expert," you might want it. Here is how to edit SETUPAPI.DLL to shut off setup file checking to allow you to edit system files such as LAYOUT.INF. Svajunas points out that "for Xp (SP1, SP2) and W2k3 (SP1), search for sequence 55 8B EC 8B 45 2C and replace with 33 C0 C2 30 00 2C. This should work and for future Xp and W2k3 versions.""
now i've edited my setupapi.dll with xvi32 and changed "55 8B EC 8B 45 2C" to "33 C0 C2 30 00 2C"
but now the windows logo test fails all the time, cause its damaged? dunno why..
does anybody know how to fix that?
(sorry for my bad english, i'm from austria)
0


Server 2008 Updates on Windows Vista
in Windows Vista
Posted · Edited by freakedenough
I recently installed Vista SP2 and patched it up to the EOL state using WSUS Offline. From there, I patched it to receive SHA2 Windows Server 2008 updates. However, the system is 32-bit, and Windows Update tends to excessively use memory and CPU when searching for updates. Ultimately, I encounter error 0x8007000E ("out of memory") when svchost.exe (Windows Update service) reaches around 2.5GB of memory consumption. WUMT and a WSUS Proxy is of no help. Has anyone found a solution for this? I know there was a hotfix for Windows 7 (KB3050265), but I couldn't find any for Vista/2008.
In the meantime, I built a script that installs all MSUs in the same folder one after another, restarting the Windows Update service in between to prevent the endless "searching for updates" bug. However, I'm sure I've missed many MSUs and possibly installed superseded updates as well. The file naming scheme I'm using is "yyyy-mm KBxxxxxxx.msu", which makes the script to install older updates first.
@echo off cls echo. echo Installing updates from "%~dp0" echo. for /r "%~dp0" %%m in (*.msu) do ( set msupath=%%m set msufile=%%~nm call :wusa ) echo. echo Done! Please check %log% for results. echo. pause goto :eof :wusa echo %msufile% start /wait "%SystemRoot%\System32\wusa.exe" "%msupath%" /quiet /norestart echo Restarting Windows Update Service... net stop wuauserv net start wuauserv