Content Type
Profiles
Forums
Events
Posts posted by Dietmar
-
-
I just integrate the Flush function in ntdll.dll, works

53 55 33 DB 8B E9 8B 55 04 8B 45 00 0B C0 74 17 8B CA 66 8B CB F0 0F B1 5D 00 75 F0 50 8B C2 F0 0F B1 4D 04 58 75 F5 5D 5B C3
.text:7C9C604F .text:7C9C604F ; =============== S U B R O U T I N E ======================================= .text:7C9C604F .text:7C9C604F .text:7C9C604F sub_7C9C604F proc near ; CODE XREF: RtlInterlockedFlushSList+8p .text:7C9C604F push ebx .text:7C9C6050 push ebp .text:7C9C6051 xor ebx, ebx .text:7C9C6053 mov ebp, ecx .text:7C9C6055 mov edx, [ebp+4] .text:7C9C6058 mov eax, [ebp+0] .text:7C9C605B .text:7C9C605B loc_7C9C605B: ; CODE XREF: sub_7C9C604F+1Aj .text:7C9C605B or eax, eax .text:7C9C605D jz short loc_7C9C6076 .text:7C9C605F mov ecx, edx .text:7C9C6061 mov cx, bx .text:7C9C6064 lock cmpxchg [ebp+0], ebx .text:7C9C6069 jnz short loc_7C9C605B .text:7C9C606B .text:7C9C606B loc_7C9C606B: ; CODE XREF: sub_7C9C604F+25j .text:7C9C606B push eax .text:7C9C606C mov eax, edx .text:7C9C606E lock cmpxchg [ebp+4], ecx .text:7C9C6073 pop eax .text:7C9C6074 jnz short loc_7C9C606B .text:7C9C6076 .text:7C9C6076 loc_7C9C6076: ; CODE XREF: sub_7C9C604F+Ej .text:7C9C6076 pop ebp .text:7C9C6077 pop ebx .text:7C9C6078 nop .text:7C9C6079 nop .text:7C9C607A nop .text:7C9C607B nop .text:7C9C607C nop .text:7C9C607D nop .text:7C9C607E retn .text:7C9C607E sub_7C9C604F endp .text:7C9C607E .text:7C9C607E ; ---------------------------------------------------------------------------0 -
@pappyN4 Yessssaaa


 I got it thanks to your help. The CRAZY function is ours^^..
I got it thanks to your help. The CRAZY function is ours^^..
Now, the Emulator is nearly perfect. I just delete Cli, Sti from it.
Now the Emulator of CMPXCHG8B is ready and can be used everywhere.
53 55 8B E9 8B 55 04 8B 45 00 0B C0 74 17 8D 4A FF 8B 18 F0 0F B1 5D 00 75 F0 50 8B C2 F0 0F B1 4D 04 58 75 F5 5D 5B C3
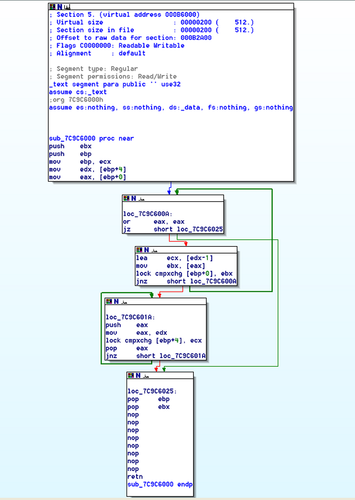
.text:7C9C6000 .text:7C9C6000 ; =============== S U B R O U T I N E ======================================= .text:7C9C6000 .text:7C9C6000 .text:7C9C6000 sub_7C9C6000 proc near ; CODE XREF: sub_7C9201D1+18p .text:7C9C6000 ; RtlInterlockedPopEntrySList+17p ... .text:7C9C6000 push ebx .text:7C9C6001 push ebp .text:7C9C6002 mov ebp, ecx .text:7C9C6004 mov edx, [ebp+4] .text:7C9C6007 mov eax, [ebp+0] .text:7C9C600A .text:7C9C600A loc_7C9C600A: ; CODE XREF: sub_7C9C6000+18j .text:7C9C600A or eax, eax .text:7C9C600C jz short loc_7C9C6025 .text:7C9C600E lea ecx, [edx-1] .text:7C9C6011 mov ebx, [eax] .text:7C9C6013 lock cmpxchg [ebp+0], ebx .text:7C9C6018 jnz short loc_7C9C600A .text:7C9C601A .text:7C9C601A loc_7C9C601A: ; CODE XREF: sub_7C9C6000+23j .text:7C9C601A push eax .text:7C9C601B mov eax, edx .text:7C9C601D lock cmpxchg [ebp+4], ecx .text:7C9C6022 pop eax .text:7C9C6023 jnz short loc_7C9C601A .text:7C9C6025 .text:7C9C6025 loc_7C9C6025: ; CODE XREF: sub_7C9C6000+Cj .text:7C9C6025 pop ebp .text:7C9C6026 pop ebx .text:7C9C6027 nop .text:7C9C6028 nop .text:7C9C6029 nop .text:7C9C602A nop .text:7C9C602B nop .text:7C9C602C nop .text:7C9C602D nop .text:7C9C602E nop .text:7C9C602F retn .text:7C9C602F sub_7C9C6000 endp .text:7C9C602F .text:7C9C602F ; ---------------------------------------------------------------------------0 -
But the Emulator for this crazy function, just now also with Cli, Sti is not good enough until now.
Here we have the log of Windbg
Dietmar
Break instruction exception - code 80000003 (first chance) nt!DbgBreakPoint: 804e3586 cc int 3 kd> g *** Unhandled exception 0xc0000096, hit in winlogon.exe: *** enter .exr 0006F964 for the exception record *** enter .cxr 0006F978 for the context *** then kb to get the faulting stack Break instruction exception - code 80000003 (first chance) NTDLL!`string'+0x12: 001b:7c91120e cc int 3 kd> .exr 0006F964 ExceptionAddress: 7c9c6002 (NTDLL!BaseStaticServerData <PERF> (NTDLL+0xb6002)) ExceptionCode: c0000096 ExceptionFlags: 00000000 NumberParameters: 0 kd> .cxr 0006F978 eax=7c95d8ec ebx=00000000 ecx=7c98c950 edx=00000000 esi=00000000 edi=00000000 eip=7c9c6002 esp=0006fc44 ebp=0006fc78 iopl=0 nv up ei pl zr na pe nc cs=001b ss=0023 ds=0023 es=0023 fs=003b gs=0000 efl=00010246 NTDLL!BaseStaticServerData <PERF> (NTDLL+0xb6002): 001b:7c9c6002 fa cli kd> kb *** Stack trace for last set context - .thread/.cxr resets it ChildEBP RetAddr Args to Child 0006fc78 7c943c6c 7c98c950 7c98b4a0 00000000 NTDLL!BaseStaticServerData <PERF> (NTDLL+0xb6002) 0006fc90 7c944676 7c885858 7c885854 00000000 NTDLL!_ValidateEH3RN+0x11e 0006fcb0 7c93dbde 7c885854 00000000 0006fce0 NTDLL!LdrpAccessResourceData+0x58 0006fcc0 7c82cbd2 7c885770 7c80b731 000725a4 NTDLL!RtlpGetAssemblyStorageMapRootLocation+0x1c8 WARNING: Frame IP not in any known module. Following frames may be wrong. 0006fd14 7c92b00a 7c91d04c 7c91e43f 00000000 0x7c82cbd2 0006fd18 7c91d04c 7c91e43f 00000000 00000001 NTDLL!LdrpInitializeProcess+0x136e 7c92b00a ffff9090 0000ffff f1580000 00007c94 NTDLL!RtlpCheckRelativeDrive+0x10a 7c92b012 f1580000 00007c94 f0f60000 f10c7c94 0xffff9090 7c92b016 00000000 f0f60000 f10c7c94 90907c94 0xf1580000 kd> !analyze -v Connected to Windows XP 2600 x86 compatible target at (Sat Apr 6 21:16:27.406 2024 (UTC + 2:00)), ptr64 FALSE Loading Kernel Symbols ............................................................... ................. Loading User Symbols ......................... Loading unloaded module list ...... ******************************************************************************* * * * Exception Analysis * * * ******************************************************************************* *** ERROR: Module load completed but symbols could not be loaded for winlogon.exe ************************************************************************* *** *** *** *** *** Either you specified an unqualified symbol, or your debugger *** *** doesn't have full symbol information. Unqualified symbol *** *** resolution is turned off by default. Please either specify a *** *** fully qualified symbol module!symbolname, or enable resolution *** *** of unqualified symbols by typing ".symopt- 100". Note that *** *** enabling unqualified symbol resolution with network symbol *** *** server shares in the symbol path may cause the debugger to *** *** appear to hang for long periods of time when an incorrect *** *** symbol name is typed or the network symbol server is down. *** *** *** *** For some commands to work properly, your symbol path *** *** must point to .pdb files that have full type information. *** *** *** *** Certain .pdb files (such as the public OS symbols) do not *** *** contain the required information. Contact the group that *** *** provided you with these symbols if you need this command to *** *** work. *** *** *** *** Type referenced: ULONG64 *** *** *** ************************************************************************* ************************************************************************* *** *** *** *** *** Either you specified an unqualified symbol, or your debugger *** *** doesn't have full symbol information. Unqualified symbol *** *** resolution is turned off by default. Please either specify a *** *** fully qualified symbol module!symbolname, or enable resolution *** *** of unqualified symbols by typing ".symopt- 100". Note that *** *** enabling unqualified symbol resolution with network symbol *** *** server shares in the symbol path may cause the debugger to *** *** appear to hang for long periods of time when an incorrect *** *** symbol name is typed or the network symbol server is down. *** *** *** *** For some commands to work properly, your symbol path *** *** must point to .pdb files that have full type information. *** *** *** *** Certain .pdb files (such as the public OS symbols) do not *** *** contain the required information. Contact the group that *** *** provided you with these symbols if you need this command to *** *** work. *** *** *** *** Type referenced: ULONG64 *** *** *** ************************************************************************* FAULTING_IP: ntdll!`string'+12 001b:7c91120e cc int 3 EXCEPTION_RECORD: 0006f964 -- (.exr 0x6f964) ExceptionAddress: 7c9c6002 (ntdll!BaseStaticServerData <PERF> (ntdll+0xb6002)) ExceptionCode: c0000096 ExceptionFlags: 00000000 NumberParameters: 0 CONTEXT: 0006f978 -- (.cxr 0x6f978;r) eax=7c95d8ec ebx=00000000 ecx=7c98c950 edx=00000000 esi=00000000 edi=00000000 eip=7c9c6002 esp=0006fc44 ebp=0006fc78 iopl=0 nv up ei pl zr na pe nc cs=001b ss=0023 ds=0023 es=0023 fs=003b gs=0000 efl=00010246 ntdll!BaseStaticServerData <PERF> (ntdll+0xb6002): 001b:7c9c6002 fa cli Last set context: eax=7c95d8ec ebx=00000000 ecx=7c98c950 edx=00000000 esi=00000000 edi=00000000 eip=7c9c6002 esp=0006fc44 ebp=0006fc78 iopl=0 nv up ei pl zr na pe nc cs=001b ss=0023 ds=0023 es=0023 fs=003b gs=0000 efl=00010246 ntdll!BaseStaticServerData <PERF> (ntdll+0xb6002): 001b:7c9c6002 fa cli Resetting default scope ERROR_CODE: (NTSTATUS) 0x80000003 - {AUSNAHME} Haltepunkt Im Quellprogramm wurde ein Haltepunkt erreicht. EXCEPTION_CODE: (HRESULT) 0x80000003 (2147483651) - Mindestens ein Argument ist ung ltig. EXCEPTION_PARAMETER1: 00000000 EXCEPTION_PARAMETER2: 7c975938 EXCEPTION_PARAMETER3: 00000028 NTGLOBALFLAG: 0 APPLICATION_VERIFIER_FLAGS: 0 APP: winlogon.exe ANALYSIS_VERSION: 6.3.9600.17237 (debuggers(dbg).140716-0327) x86fre DEFAULT_BUCKET_ID: STATUS_BREAKPOINT FAULTING_THREAD: 00000001 PRIMARY_PROBLEM_CLASS: STATUS_BREAKPOINT BUGCHECK_STR: APPLICATION_FAULT_STATUS_BREAKPOINT LAST_CONTROL_TRANSFER: from 7c943c6c to 7c9c6002 STACK_TEXT: 0006fc78 7c943c6c 7c98c950 7c98b4a0 00000000 ntdll!BaseStaticServerData <PERF> (ntdll+0xb6002) 0006fc90 7c944676 7c885858 7c885854 00000000 ntdll!_ValidateEH3RN+0x11e 0006fcb0 7c93dbde 7c885854 00000000 0006fce0 ntdll!LdrpAccessResourceData+0x58 0006fcc0 7c82cbd2 7c885770 7c80b731 000725a4 ntdll!RtlpGetAssemblyStorageMapRootLocation+0x1c8 0006fce0 7c82b26f 0006ff50 01031700 00000000 kernel32!BasepCreateDefaultTimerQueue+0x66 0006fce8 01031700 00000000 01030ed0 00000000 kernel32!SetTimerQueueTimer+0x19 WARNING: Stack unwind information not available. Following frames may be wrong. 0006ff50 0103e75e 01000000 00000000 000725a4 winlogon+0x31700 0006fff4 00000000 7ffdd000 000000c8 00000129 winlogon+0x3e75e FOLLOWUP_IP: winlogon+31700 001b:01031700 56 push esi SYMBOL_STACK_INDEX: 6 SYMBOL_NAME: winlogon+31700 FOLLOWUP_NAME: MachineOwner MODULE_NAME: winlogon IMAGE_NAME: winlogon.exe DEBUG_FLR_IMAGE_TIMESTAMP: 48027549 STACK_COMMAND: .cxr 0x6f978 ; kb FAILURE_BUCKET_ID: STATUS_BREAKPOINT_80000003_winlogon.exe!Unknown BUCKET_ID: APPLICATION_FAULT_STATUS_BREAKPOINT_winlogon+31700 ANALYSIS_SOURCE: KM FAILURE_ID_HASH_STRING: km:status_breakpoint_80000003_winlogon.exe!unknown FAILURE_ID_HASH: {f71cf305-2a12-4f5c-c480-6ae6676460a2} Followup: MachineOwner ---------
0 -
First I put the whole crazy function to this place and 90 90.. out her old place.
And voila, this relocation works, just until now with the original function
 ,
,
Dietmar
.text:7C9C6000 .text:7C9C6000 ; =============== S U B R O U T I N E ======================================= .text:7C9C6000 .text:7C9C6000 .text:7C9C6000 sub_7C9C6000 proc near ; CODE XREF: sub_7C9201D1+18p .text:7C9C6000 ; RtlInterlockedPopEntrySList+17p ... .text:7C9C6000 push ebx .text:7C9C6001 push ebp .text:7C9C6002 mov ebp, ecx .text:7C9C6004 mov edx, [ebp+4] .text:7C9C6007 mov eax, [ebp+0] .text:7C9C600A .text:7C9C600A loc_7C9C600A: ; CODE XREF: sub_7C9C6000+18j .text:7C9C600A or eax, eax .text:7C9C600C jz short loc_7C9C601A .text:7C9C600E lea ecx, [edx-1] .text:7C9C6011 mov ebx, [eax] .text:7C9C6013 lock cmpxchg8b qword ptr [ebp+0] .text:7C9C6018 jnz short loc_7C9C600A .text:7C9C601A .text:7C9C601A loc_7C9C601A: ; CODE XREF: sub_7C9C6000+Cj .text:7C9C601A pop ebp .text:7C9C601B pop ebx .text:7C9C601C nop .text:7C9C601D nop .text:7C9C601E nop .text:7C9C601F retn .text:7C9C601F sub_7C9C6000 endp .text:7C9C601F .text:7C9C601F ; ---------------------------------------------------------------------------1 -
I make a new try with your idea. Because in NTDLL.DLL appears 5 times cmpxchg8b,
I reserve 64 Byte for each of their modd. So, the 512 Byte are enough.
For to understand everything, I use in the beginning the original ntoskrnl.exe.
And I try to emulate first only one function in NTDLL.DLL, only the part of RtlInterlockedPopEntrySList with cmpxchg8b,
.text:7C912A8C sub_7C912A8C proc near.
This is the most crazy function, when this is done, the rest is easy
Dietmar
1 -
I found out, that this Emulation fails for the crazy function. When I add Cli and Sti, winlogon fails on Cli.
Everything with relocation works now for me.
Emulation of RtlInterlockedPopEntrySList crashes winlogon.exe, I can see the mouse pointer
Dietmar
EDIT: With ntdll!RtlpInterlockedFlushSList is all correct, it is here shown, because I changed places with ntdll!RtlInterlockedPopEntrySList , so Windbg shows wrong message.
*** An Access Violation occurred in winlogon.exe: The instruction at 00000000 tried to read from a NULL pointer *** enter .exr 0006F964 for the exception record *** enter .cxr 0006F980 for the context *** then kb to get the faulting stack Break instruction exception - code 80000003 (first chance) NTDLL!DbgBreakPoint: 001b:7c91120e cc int 3 kd> .exr 0006F964 ExceptionAddress: 00000000 ExceptionCode: c0000005 (Access violation) ExceptionFlags: 00000000 NumberParameters: 2 Parameter[0]: 00000000 Parameter[1]: 00000000 Attempt to read from address 00000000 kd> cxr 0006F980 Couldn't resolve error at 'xr 0006F980' kd> kb ChildEBP RetAddr Args to Child 0006f568 7c9752ae 00000000 7c885780 010304fd NTDLL!DbgBreakPoint 0006f5a8 7c9759c1 0006f870 7c9759c6 0006f828 NTDLL!RtlUnhandledExceptionFilter2+0x27b 0006f5b8 7c864031 0006f870 c0000005 00261e90 NTDLL!RtlUnhandledExceptionFilter+0x12 WARNING: Frame IP not in any known module. Following frames may be wrong. 0006f878 7c9132a8 0006f964 0006ffe4 0006f980 0x7c864031 0006f89c 7c91327a 0006f964 0006ffe4 0006f980 NTDLL!ExecuteHandler2+0x26 0006f94c 7c91e46a 00000000 0006f980 0006f964 NTDLL!ExecuteHandler+0x24 0006f94c 00000000 00000000 0006f980 0006f964 NTDLL!KiUserExceptionDispatcher+0xe 0006fc48 7c943c9f 7c98b4a0 00000000 00000000 0x0 7c98c950 00000000 00000000 00000000 00000000 NTDLL!RtlInterlockedPopEntrySList+0x1c kd> !analyze -v Connected to Windows XP 2600 x86 compatible target at (Sat Apr 6 17:06:47.531 2024 (UTC + 2:00)), ptr64 FALSE Loading Kernel Symbols ............................................................... ................. Loading User Symbols ......................... Loading unloaded module list ...... ******************************************************************************* * * * Exception Analysis * * * ******************************************************************************* *** ERROR: Module load completed but symbols could not be loaded for winlogon.exe ************************************************************************* *** *** *** *** *** Either you specified an unqualified symbol, or your debugger *** *** doesn't have full symbol information. Unqualified symbol *** *** resolution is turned off by default. Please either specify a *** *** fully qualified symbol module!symbolname, or enable resolution *** *** of unqualified symbols by typing ".symopt- 100". Note that *** *** enabling unqualified symbol resolution with network symbol *** *** server shares in the symbol path may cause the debugger to *** *** appear to hang for long periods of time when an incorrect *** *** symbol name is typed or the network symbol server is down. *** *** *** *** For some commands to work properly, your symbol path *** *** must point to .pdb files that have full type information. *** *** *** *** Certain .pdb files (such as the public OS symbols) do not *** *** contain the required information. Contact the group that *** *** provided you with these symbols if you need this command to *** *** work. *** *** *** *** Type referenced: ULONG64 *** *** *** ************************************************************************* ************************************************************************* *** *** *** *** *** Either you specified an unqualified symbol, or your debugger *** *** doesn't have full symbol information. Unqualified symbol *** *** resolution is turned off by default. Please either specify a *** *** fully qualified symbol module!symbolname, or enable resolution *** *** of unqualified symbols by typing ".symopt- 100". Note that *** *** enabling unqualified symbol resolution with network symbol *** *** server shares in the symbol path may cause the debugger to *** *** appear to hang for long periods of time when an incorrect *** *** symbol name is typed or the network symbol server is down. *** *** *** *** For some commands to work properly, your symbol path *** *** must point to .pdb files that have full type information. *** *** *** *** Certain .pdb files (such as the public OS symbols) do not *** *** contain the required information. Contact the group that *** *** provided you with these symbols if you need this command to *** *** work. *** *** *** *** Type referenced: ULONG64 *** *** *** ************************************************************************* FAULTING_IP: +368b8e80368b908 001b:00000000 ?? ??? EXCEPTION_RECORD: 0006f964 -- (.exr 0x6f964) .exr 0x6f964 ExceptionAddress: 00000000 ExceptionCode: c0000005 (Access violation) ExceptionFlags: 00000000 NumberParameters: 2 Parameter[0]: 00000000 Parameter[1]: 00000000 Attempt to read from address 00000000 CONTEXT: 0006f980 -- (.cxr 0x6f980;r) .cxr 0x6f980;r eax=00000000 ebx=0006fc78 ecx=7c98c950 edx=00000000 esi=00000000 edi=00000000 eip=00000000 esp=0006fc4c ebp=7c98c950 iopl=0 nv up ei pl zr na pe nc cs=001b ss=0023 ds=0023 es=0023 fs=003b gs=0000 efl=00010246 001b:00000000 ?? ??? Last set context: eax=00000000 ebx=0006fc78 ecx=7c98c950 edx=00000000 esi=00000000 edi=00000000 eip=00000000 esp=0006fc4c ebp=7c98c950 iopl=0 nv up ei pl zr na pe nc cs=001b ss=0023 ds=0023 es=0023 fs=003b gs=0000 efl=00010246 001b:00000000 ?? ??? .cxr Resetting default scope ERROR_CODE: (NTSTATUS) 0x80000003 - {AUSNAHME} Haltepunkt Im Quellprogramm wurde ein Haltepunkt erreicht. EXCEPTION_CODE: (HRESULT) 0x80000003 (2147483651) - Mindestens ein Argument ist ung ltig. EXCEPTION_PARAMETER1: 00000000 EXCEPTION_PARAMETER2: 7c975938 EXCEPTION_PARAMETER3: 00000028 NTGLOBALFLAG: 0 APPLICATION_VERIFIER_FLAGS: 0 CHKIMG_EXTENSION: !chkimg -lo 50 -d !ntdll !chkimg -lo 50 -d !ntdll 7c912a6e-7c912a6f 2 bytes - ntdll!RtlpInterlockedFlushSList+2 [ 33 db:8b e9 ] 7c912a71-7c912a9e 46 bytes - ntdll!RtlpInterlockedFlushSList+5 (+0x03) [ e9 8b 55 04 8b 45 00 0b:55 04 8b 45 00 0b c0 74 ] 7c912aa0-7c912aa4 5 bytes - ntdll!ExpInterlockedPopEntrySListEnd+1 (+0x2f) [ 0f c7 4d 00 75:90 90 90 90 90 ] 7c912aa6-7c912aaf 10 bytes - ntdll!ExpInterlockedPopEntrySListEnd+7 (+0x06) [ 5d 5b c3 8d 49 00 8f 04:90 90 90 90 90 90 90 90 ] 7c913420-7c913421 2 bytes - ntdll!$$VProc_ImageExportDirectory+20 (+0x97a) [ b4 48:fa 52 ] 7c913424-7c913425 2 bytes - ntdll!$$VProc_ImageExportDirectory+24 (+0x04) [ 40 5d:b4 48 ] 7c913e64-7c913e66 3 bytes - ntdll!$$VProc_ImageExportDirectory+a64 (+0xa40) [ b5 2e 06:6c ba 07 ] 7c916000-7c916011 18 bytes - ntdll!$$VProc_ImageExportDirectory+2c00 (+0x219c) [ 67 01 68 01 69 01 6a 01:00 00 ff ae 00 00 1b af ] 7c916013-7c9160a9 151 bytes - ntdll!$$VProc_ImageExportDirectory+2c13 (+0x13) [ 01 71 01 72 01 73 01 74:af 00 00 93 af 00 00 ad ] 7c9160ab-7c9160b0 6 bytes - ntdll!$$VProc_ImageExportDirectory+2cab (+0x98) [ 01 bc 01 bd 01 01:b2 00 00 c7 b2 00 ] 7c9160b2-7c9160bc 11 bytes - ntdll!$$VProc_ImageExportDirectory+2cb2 (+0x07) [ be 01 bf 01 c0 01 c1 01:d5 b2 00 00 f1 b2 00 00 ] 7c9160be-7c916137 122 bytes - ntdll!$$VProc_ImageExportDirectory+2cbe (+0x0c) [ c3 01 c4 01 c5 01 c6 01:1e b3 00 00 3a b3 00 00 ] 7c916139-7c91625c 292 bytes - ntdll!$$VProc_ImageExportDirectory+2d39 (+0x7b) [ 02 01 02 02 02 03 02 04:00 fd b5 00 00 15 b6 00 ] 7c91625e-7c9163c0 355 bytes - ntdll!$$VProc_ImageExportDirectory+2e5e (+0x125) [ 92 02 93 02 94 02 95 02:20 bb 00 00 3c bb 00 00 ] 7c9163c2-7c9163c5 4 bytes - ntdll!$$VProc_ImageExportDirectory+2fc2 (+0x164) [ 05 00 44 03:2c c2 00 00 ] 7c9163c7-7c916441 123 bytes - ntdll!$$VProc_ImageExportDirectory+2fc7 (+0x05) [ 03 45 03 46 03 47 03 48:c2 00 00 53 c2 00 00 68 ] 7c916443-7c91653f 253 bytes - ntdll!$$VProc_ImageExportDirectory+3043 (+0x7c) [ 03 82 03 83 03 84 03 85:c4 00 00 8b c4 00 00 97 ] 7c916541-7c91673f 511 bytes - ntdll!$$VProc_ImageExportDirectory+3141 (+0xfe) [ 04 01 04 02 04 03 04 04:00 5e c9 00 00 77 c9 00 ] 7c916741-7c916785 69 bytes - ntdll!$$VProc_ImageExportDirectory+3341 (+0x200) [ 05 01 05 02 05 03 05 04:00 be cd 00 00 c7 cd 00 ] 7c9201ea - ntdll!RtlpAllocateFromHeapLookaside+19 (+0x9aa9) [ 9e:7e ] 7c943c9b - ntdll!RtlInterlockedPopEntrySList+18 (+0x23ab1) [ ed:cd ] 7c95e8e2 - ntdll!RtlpLowFragHeapAlloc+436 (+0x1ac47) [ a6:86 ] 1988 errors : !ntdll (7c912a6e-7c95e8e2) APP: winlogon.exe ANALYSIS_VERSION: 6.3.9600.17237 (debuggers(dbg).140716-0327) x86fre READ_ADDRESS: 00000000 FOLLOWUP_IP: +368b8e80368b908 001b:00000000 ?? ??? FAILED_INSTRUCTION_ADDRESS: +368b8e80368b908 001b:00000000 ?? ??? FAULTING_THREAD: 00000001 ADDITIONAL_DEBUG_TEXT: Followup set based on attribute [Is_ChosenCrashFollowupThread] from Frame:[0] on thread:[PSEUDO_THREAD] LAST_CONTROL_TRANSFER: from 7c943c9f to 00000000 BUGCHECK_STR: APPLICATION_FAULT_MEMORY_CORRUPTION_LARGE PRIMARY_PROBLEM_CLASS: MEMORY_CORRUPTION_LARGE DEFAULT_BUCKET_ID: MEMORY_CORRUPTION_LARGE STACK_TEXT: 00000000 00000000 memory_corruption!ntdll+0x0 POSSIBLE_INVALID_CONTROL_TRANSFER: from 7c943c9a to 7c912a6c SYMBOL_STACK_INDEX: 0 SYMBOL_NAME: memory_corruption!ntdll FOLLOWUP_NAME: MachineOwner MODULE_NAME: memory_corruption DEBUG_FLR_IMAGE_TIMESTAMP: 0 STACK_COMMAND: ** Pseudo Context ** ; kb BUCKET_ID: CPU_CALL_ERROR IMAGE_NAME: memory_corruption FAILURE_BUCKET_ID: MEMORY_CORRUPTION_LARGE_80000003_memory_corruption!ntdll ANALYSIS_SOURCE: KM FAILURE_ID_HASH_STRING: km:memory_corruption_large_80000003_memory_corruption!ntdll FAILURE_ID_HASH: {2c85946d-85e8-c8a7-3c74-93e684cc96ed} Followup: MachineOwner --------- *** Possible invalid call from 7c943c9a ( ntdll!RtlInterlockedPopEntrySList+0x17 ) *** Expected target 7c912a6c ( ntdll!RtlpInterlockedFlushSList+0x0 )0 -
I dont know, how to do this. Because for example when I add "Cli" most of the function is "new"
Dietmar
For the pop function:
53 55 8B E9 8B 55 04 8B 45 00 0B C0 74 0C 8D 4A FF 8B 18 F0 0F C7 4D 00 75 F0 5D 5B C3 ==>
53 55 FA 8B E9 8B 55 04 8B 45 00 0B C0 74 18 8D 4A FF 8B 18 F0 0F B1 5D 00 75 F0 50 8B C2 F0 0F B1 4D 04 58 75 F5 FB 5D 5B C3
0 -
Can this be used, to put 32 Byte free space direct after EACH function of NTDLL.DLL with cmpxchg8b in it
Dietmar
0 -
0
-
I succeed to relocate this crazy function


 !!!!!!!!!!!!!!!!!!!!!!!!!!!!!!
!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!
First, I relocate to .DATA section the RtlInterlockedFlushSList function.
This works.
Then I zero out all the place where it has been before.
Then I delete the whole crazy function RtlInterlockedPopEntrySList at its original place.
This function RtlInterlockedPopEntrySList I relocate after this to the place, where before the Flush function stays.
There I copy and past with Winhex this crazy function, set all calls by hand to this place.
And voila, with this small setting (relocation) in front of the old crazy function,
now I have after her in .TEXT section enough place for modd

Dietmar
0 -
It seems, as if crazy XP reads
00 00 as the hexadecimal representation of the opcode for the instruction add byte ptr [eax], al
in .DATA section
Dietmar
0 -
Here is the relocated original(!) function from ntdll.dll
.data:7C98CA8C .data:7C98CA8C ; =============== S U B R O U T I N E ======================================= .data:7C98CA8C .data:7C98CA8C .data:7C98CA8C sub_7C98CA8C proc near ; CODE XREF: sub_7C9201D1+18p .data:7C98CA8C ; RtlInterlockedPopEntrySList+17p ... .data:7C98CA8C push ebx .data:7C98CA8D push ebp .data:7C98CA8E mov ebp, ecx .data:7C98CA90 mov edx, [ebp+4] .data:7C98CA93 mov eax, [ebp+0] .data:7C98CA96 .data:7C98CA96 loc_7C98CA96: ; CODE XREF: sub_7C98CA8C+18j .data:7C98CA96 or eax, eax .data:7C98CA98 jz short loc_7C98CAA6 .data:7C98CA9A lea ecx, [edx-1] .data:7C98CA9D mov ebx, [eax] .data:7C98CA9F lock cmpxchg8b qword ptr [ebp+0] .data:7C98CAA4 jnz short loc_7C98CA96 .data:7C98CAA6 .data:7C98CAA6 loc_7C98CAA6: ; CODE XREF: sub_7C98CA8C+Cj .data:7C98CAA6 pop ebp .data:7C98CAA7 pop ebx .data:7C98CAA8 nop .data:7C98CAA9 nop .data:7C98CAAA nop .data:7C98CAAB nop .data:7C98CAAC nop .data:7C98CAAD nop .data:7C98CAAE nop .data:7C98CAAF retn .data:7C98CAAF sub_7C98CA8C endp .data:7C98CAAF .data:7C98CAAF ; ---------------------------------------------------------------------------0 -
I put the function all by hand to another place in .DATA section.
Now I get this, @Mov AX, 0xDEAD can you help
Dietmar
*** An Access Violation occurred in winlogon.exe: The instruction at 7C98CAA8 tried to write to a NULL pointer *** enter .exr 0006F428 for the exception record *** enter .cxr 0006F444 for the context *** then kb to get the faulting stack Break instruction exception - code 80000003 (first chance) NTDLL!DbgBreakPoint: 001b:7c91120e cc int 3 kd> .exr 0006F428 ExceptionAddress: 7c98caa8 (NTDLL!RtlpUnloadEventTrace+0x000000a8) ExceptionCode: c0000005 (Access violation) ExceptionFlags: 00000000 NumberParameters: 2 Parameter[0]: 00000001 Parameter[1]: 00000000 Attempt to write to address 00000000 kd> .cxr 0006F444 eax=00000000 ebx=00000000 ecx=7c98c950 edx=00010000 esi=00000000 edi=00000000 eip=7c98caa8 esp=0006f710 ebp=0006f73c iopl=0 nv up ei pl zr na pe nc cs=001b ss=0023 ds=0023 es=0023 fs=003b gs=0000 efl=00010246 NTDLL!RtlpUnloadEventTrace+0xa8: 001b:7c98caa8 0000 add byte ptr [eax],al ds:0023:00000000=?? kd> kb *** Stack trace for last set context - .thread/.cxr resets it ChildEBP RetAddr Args to Child 0006f73c 7c943c6c 7c98c950 7c98c9a0 00000000 NTDLL!RtlpUnloadEventTrace+0xa8 0006f754 7c93d5cf 7c98c9a0 7c98c980 00000000 NTDLL!RtlpGetWaitEvent+0x12 0006f764 7c93d5a5 0009eda8 0009ed80 0006f79c NTDLL!RtlpStartWaitThread+0x18 0006f774 7c943308 0006f790 0009a7e0 0009ece8 NTDLL!RtlpFindWaitThread+0x2f 0006f79c 01029aec 0009ecf0 00000190 010298a1 NTDLL!RtlRegisterWait+0x16f WARNING: Frame IP not in any known module. Following frames may be wrong. 0006f81c 01029d91 00000001 01010d74 00000000 0x1029aec 0006fd14 7c92b00a 7c91d04c 7c91e43f 00000000 0x1029d91 0006ff50 0103e75e 01000000 00000000 00072364 NTDLL!_LdrpInitialize+0x246 0006fff4 00000000 7ffd5000 000000c8 000001f6 0x103e75e0 -
8 hours ago, pappyN4 said:
But first maybe try increase .TEXT size with a PE editor and put into .TEXT and see if that helps
How can I increase .TEXT size for a PE file
Dietmar
0 -
With all the other functions it was no problem to use .DATA space. Only not for this crazy function.
The problem is, that there is no free place in .TEXT or I just do not find
Dietmar
0 -
I do not find a place in ntdll.dll, where I can relocate this (original) function.
I check all, the relocation is done correct.
Always I get this Bsod from above after relocation, even it is the identic function, just on other place.
With all the other functions, relocation was no problem.
Even no problem after relocation of RtlInterlockedFlushSList in ntdll.dll itself.
But RtlInterlockedPopEntrySList is crazy. Bsod stays the same, when I replace to the original ntoskrnl.exe.
Dietmar
This is the original function before relocation. At this original place, it works.
.text:7C912A8C .text:7C912A8C ; =============== S U B R O U T I N E ======================================= .text:7C912A8C .text:7C912A8C .text:7C912A8C sub_7C912A8C proc near ; CODE XREF: sub_7C9201D1+18p .text:7C912A8C ; RtlInterlockedPopEntrySList+17p ... .text:7C912A8C push ebx .text:7C912A8D push ebp .text:7C912A8E mov ebp, ecx .text:7C912A90 mov edx, [ebp+4] .text:7C912A93 mov eax, [ebp+0] .text:7C912A96 .text:7C912A96 loc_7C912A96: ; CODE XREF: sub_7C912A8C+18j .text:7C912A96 or eax, eax .text:7C912A98 jz short loc_7C912AA6 .text:7C912A9A lea ecx, [edx-1] .text:7C912A9D mov ebx, [eax] .text:7C912A9F lock cmpxchg8b qword ptr [ebp+0] .text:7C912AA4 jnz short loc_7C912A96 .text:7C912AA6 .text:7C912AA6 loc_7C912AA6: ; CODE XREF: sub_7C912A8C+Cj .text:7C912AA6 pop ebp .text:7C912AA7 pop ebx .text:7C912AA8 retn .text:7C912AA8 sub_7C912A8C endp .text:7C912AA8 .text:7C912AA8 ; ---------------------------------------------------------------------------0 -
1 hour ago, roytam1 said:
2000 RTM's ntdll.dll has same thing, maybe there is another way in 2000 to not using them?
EDIT: yes, it checks processor features in shared data first, it processor has no CX8 support, kernel will just skip this part.
Does it jump to those functions and return at once or how is this skip done,
thanks a lot
Dietmar
0 -
I notice, that with CLi and Sti I get the same error message of violating memory with my Emulator as with the original relocated code. The instruction at 7C98BAAC tried to write to an invalid address, 00007C98.
7C98BAAC is the entry point of my relocated function.
But this here is for the original, but relocated code with cmpxchg8b, for RtlInterlockedPopEntrySList.
The problem seems to be, that in ntdll.dll you cant choose any free place. But I have no idea, if another free place in ntdll.dll would work.
THE EMULATOR SEEMS TO WORK!
Relocations works in ntdll.dll for the function RtlInterlockedFlushSList with Emulator
Relocation works not in ntdll.dll, even not with original code! RtlInterlockedPopEntrySList
*** An Access Violation occurred in winlogon.exe: The instruction at 7C98BAAC tried to write to an invalid address, 00007C98 Access violation - code c0000005 (!!! second chance !!!) win32k!_GetDCEx+0x2a: bf803ea8 8b4004 mov eax,dword ptr [eax+4] kd> g Access violation - code c0000005 (!!! second chance !!!) win32k!_GetDCEx+0x2a: bf803ea8 8b4004 mov eax,dword ptr [eax+4] kd> !analyze Connected to Windows XP 2600 x86 compatible target at (Fri Apr 5 16:04:39.000 2024 (UTC + 2:00)), ptr64 FALSE Loading Kernel Symbols ............................................................... ................. Loading User Symbols ........................ Loading unloaded module list ...... ******************************************************************************* * * * Bugcheck Analysis * * * ******************************************************************************* Use !analyze -v to get detailed debugging information. BugCheck 0, {0, 0, 0, 0} Probably caused by : win32k.sys ( win32k!_GetDCEx+2a ) Followup: MachineOwner --------- kd> !analyze -v ******************************************************************************* * * * Bugcheck Analysis * * * ******************************************************************************* Unknown bugcheck code (0) Unknown bugcheck description Arguments: Arg1: 00000000 Arg2: 00000000 Arg3: 00000000 Arg4: 00000000 Debugging Details: ------------------ PROCESS_NAME: drwtsn32.exe FAULTING_IP: win32k!_GetDCEx+2a bf803ea8 8b4004 mov eax,dword ptr [eax+4] ERROR_CODE: (NTSTATUS) 0xc0000005 - Die Anweisung "0x%08lx" verweist auf Speicher bei "0x%08lx". Die Daten wurden wegen eines E/A-Fehlers in "0x%081x" nicht in den Arbeitsspeicher bertragen. EXCEPTION_CODE: (NTSTATUS) 0xc0000005 - Die Anweisung "0x%08lx" verweist auf Speicher bei "0x%08lx". Die Daten wurden wegen eines E/A-Fehlers in "0x%081x" nicht in den Arbeitsspeicher bertragen. EXCEPTION_PARAMETER1: 00000000 EXCEPTION_PARAMETER2: 00000004 READ_ADDRESS: 00000004 FOLLOWUP_IP: win32k!_GetDCEx+2a bf803ea8 8b4004 mov eax,dword ptr [eax+4] BUGCHECK_STR: ACCESS_VIOLATION DEFAULT_BUCKET_ID: NULL_CLASS_PTR_DEREFERENCE ANALYSIS_VERSION: 6.3.9600.17237 (debuggers(dbg).140716-0327) x86fre LAST_CONTROL_TRANSFER: from bf8037b5 to bf803ea8 STACK_TEXT: f7555d34 bf8037b5 00000000 00000000 00010001 win32k!_GetDCEx+0x2a f7555d48 bf8037e5 00000000 0007f9a4 f7555d64 win32k!_GetWindowDC+0x14 f7555d58 804de7ec 00000000 0007f9b8 7c91e4f4 win32k!NtUserGetWindowDC+0x27 f7555d58 7c91e4f4 00000000 0007f9b8 7c91e4f4 nt!KiFastCallEntry+0xf8 0007f994 7e36902d 5b10c013 00000000 5b0f0000 ntdll!KiFastSystemCallRet 0007f9b8 5b10bdab 00000000 0007f9d0 5b10bd74 USER32!NtUserGetWindowDC+0xc 0007f9c4 5b10bd74 5b0f0000 0007f9f0 5b0f166e UxTheme!ProcessStartUp+0x2d 0007f9d0 5b0f166e 5b0f0000 00000001 0007fd30 UxTheme!DllMain+0x30 0007f9f0 7c91118a 5b0f0000 00000001 0007fd30 UxTheme!_DllMainCRTStartup+0x52 0007fa10 7c92c4da 5b0f1626 5b0f0000 00000001 ntdll!LdrpCallInitRoutine+0x14 0007fb18 7c931194 0007fd30 7ffdd000 7ffde000 ntdll!LdrpRunInitializeRoutines+0x344 0007fc94 7c93108f 0007fd30 7c910000 0007fce0 ntdll!LdrpInitializeProcess+0x1131 0007fd1c 7c91e437 0007fd30 7c910000 00000000 ntdll!_LdrpInitialize+0x183 00000000 00000000 00000000 00000000 00000000 ntdll!KiUserApcDispatcher+0x7 STACK_COMMAND: kb SYMBOL_STACK_INDEX: 0 SYMBOL_NAME: win32k!_GetDCEx+2a FOLLOWUP_NAME: MachineOwner MODULE_NAME: win32k IMAGE_NAME: win32k.sys DEBUG_FLR_IMAGE_TIMESTAMP: 48025f2a IMAGE_VERSION: 5.1.2600.5512 FAILURE_BUCKET_ID: ACCESS_VIOLATION_win32k!_GetDCEx+2a BUCKET_ID: ACCESS_VIOLATION_win32k!_GetDCEx+2a ANALYSIS_SOURCE: KM FAILURE_ID_HASH_STRING: km:access_violation_win32k!_getdcex+2a FAILURE_ID_HASH: {ab1bddfb-8c7a-d233-cca1-748f5fec6a1d} Followup: MachineOwner ---------0 -
This I forget to clean out, but the function already dont use this place any longer.
But I have another BIG problem in NTDLL.DLL.
There seems real atomic necessary in the function . It is much sharper than in notskrnl.exe. lock cmpxchg8b qword ptr [ebp+0]
I think, with my simulator it is impossible to reach, because not real atomic. Only a try with lock bts may help,
but this complete different to my attempt. I also update my Emulator but real atomic I cant reach with this,
see second code
Dietmar
.text:7C912A8C .text:7C912A8C ; =============== S U B R O U T I N E ======================================= .text:7C912A8C .text:7C912A8C .text:7C912A8C sub_7C912A8C proc near ; CODE XREF: sub_7C9201D1+18p .text:7C912A8C ; RtlInterlockedPopEntrySList+17p ... .text:7C912A8C push ebx .text:7C912A8D push ebp .text:7C912A8E mov ebp, ecx .text:7C912A90 mov edx, [ebp+4] .text:7C912A93 mov eax, [ebp+0] .text:7C912A96 .text:7C912A96 loc_7C912A96: ; CODE XREF: sub_7C912A8C+18j .text:7C912A96 or eax, eax .text:7C912A98 jz short loc_7C912AA6 .text:7C912A9A lea ecx, [edx-1] .text:7C912A9D mov ebx, [eax] .text:7C912A9F lock cmpxchg8b qword ptr [ebp+0] .text:7C912AA4 jnz short loc_7C912A96 .text:7C912AA6 .text:7C912AA6 loc_7C912AA6: ; CODE XREF: sub_7C912A8C+Cj .text:7C912AA6 pop ebp .text:7C912AA7 pop ebx .text:7C912AA8 retn .text:7C912AA8 sub_7C912A8C endp .text:7C912AA8 .text:7C912AA8 ; ---------------------------------------------------------------------------Second code with my updated Emulator
.data:7C98BAAC ; Exported entry 657. RtlInterlockedPopEntrySList .data:7C98BAAC .data:7C98BAAC ; =============== S U B R O U T I N E ======================================= .data:7C98BAAC .data:7C98BAAC .data:7C98BAAC ; PSINGLE_LIST_ENTRY __stdcall RtlInterlockedPopEntrySList(PSLIST_HEADER ListHead) .data:7C98BAAC public RtlInterlockedPopEntrySList .data:7C98BAAC RtlInterlockedPopEntrySList proc near ; CODE XREF: sub_7C9201D1+18p .data:7C98BAAC ; sub_7C943C83+17p ... .data:7C98BAAC push ebx .data:7C98BAAD push ebp .data:7C98BAAE mov ebp, ecx .data:7C98BAB0 mov edx, [ebp+4] .data:7C98BAB3 mov eax, [ebp+0] .data:7C98BAB6 .data:7C98BAB6 loc_7C98BAB6: ; CODE XREF: RtlInterlockedPopEntrySList+18j .data:7C98BAB6 or eax, eax .data:7C98BAB8 jz short loc_7C98BAD1 .data:7C98BABA lea ecx, [edx-1] .data:7C98BABD mov ebx, [eax] .data:7C98BABF lock cmpxchg [ebp+0], ebx .data:7C98BAC4 jnz short loc_7C98BAB6 .data:7C98BAC6 .data:7C98BAC6 loc_7C98BAC6: ; CODE XREF: RtlInterlockedPopEntrySList+23j .data:7C98BAC6 push eax .data:7C98BAC7 mov eax, edx .data:7C98BAC9 lock cmpxchg [ebp+4], ecx .data:7C98BACE pop eax .data:7C98BACF jnz short loc_7C98BAC6 .data:7C98BAD1 .data:7C98BAD1 loc_7C98BAD1: ; CODE XREF: RtlInterlockedPopEntrySList+Cj .data:7C98BAD1 pop ebp .data:7C98BAD2 pop ebx .data:7C98BAD3 retn .data:7C98BAD3 RtlInterlockedPopEntrySList endp .data:7C98BAD3 .data:7C98BAD3 ; ---------------------------------------------------------------------------0 -
@jumper Yes, of course but works. The trick is the "lock" in front of it
Dietmar
PS: I just change the first funktion with success in ntdll.dll
0 -
Voila,
here is working ntoskrnl.exe XP SP3
5.1.2600.5512 (xpsp.080413-2111) for "Standard PC" without any CMPXCHG8B in it.
It is stable. Now fun starts

Dietmar
0 -
Just 4. function successful integrated in ntoskrnl.exe
Dietmar
0 -
Here is 3. integrated function, works
 .
.
Now, most work is already done for XP SP3 on 486 compi
Dietmar
Here is ntoskrnl.exe with 3 new functions, all without any CMPXCHG8B.
Interesting, boottime goes down as much as possible. Now less than 7 sec to full desktop.
53 55 8B E9 8B DA 8B 55 04 8B 45 00 89 03 8D 8A 01 00 01 00 F0 0F B1 5D 00 50 8B C2 F0 0F B1 4D 04 58 5D 5B C3
.data:00476332 ; =============== S U B R O U T I N E ======================================= .data:00476332 .data:00476332 .data:00476332 public InterlockedPushEntrySList .data:00476332 InterlockedPushEntrySList proc near ; CODE XREF: sub_40DE72+F2p .data:00476332 ; sub_4114DB+9Ep ... .data:00476332 push ebx .data:00476333 push ebp .data:00476334 mov ebp, ecx .data:00476336 mov ebx, edx .data:00476338 mov edx, [ebp+4] .data:0047633B mov eax, [ebp+0] .data:0047633E mov [ebx], eax .data:00476340 lea ecx, [edx+10001h] .data:00476346 lock cmpxchg [ebp+0], ebx .data:0047634B push eax .data:0047634C mov eax, edx .data:0047634E lock cmpxchg [ebp+4], ecx .data:00476353 pop eax .data:00476354 pop ebp .data:00476355 pop ebx .data:00476356 retn .data:00476356 InterlockedPushEntrySList endp .data:00476356 .data:00476356 ; ---------------------------------------------------------------------------0 -
I delete in both functions the rescue of the flags and also the cli for disabling interrupts.
And voila, now no Bsod at all!!! I use my new Emulator, which is close as much as possible to the original.
XP Sp3 on 486 cpu is now only a small step away, may be tomorrow

Dietmar
Here it is the working ntoskrnl.exe
EDIT: I see, that the functions in ntdll.dll are the same as in ntoskrnl.exe for to be emulated.
0



XP running on a 486 cpu
in Windows XP
Posted
And the next one integrated, works
53 55 8B E9 8B DA 8B 55 04 8B 45 00 89 03 8D 8A 01 00 01 00 F0 0F B1 5D 00 75 F1 50 8B C2 F0 0F B1 4D 04 58 75 F5 5D 5B C3
.text:7C9C609E .text:7C9C609E ; =============== S U B R O U T I N E ======================================= .text:7C9C609E .text:7C9C609E .text:7C9C609E sub_7C9C609E proc near ; CODE XREF: sub_7C920072+21p .text:7C9C609E ; RtlInterlockedPushEntrySList+Bp ... .text:7C9C609E push ebx .text:7C9C609F push ebp .text:7C9C60A0 mov ebp, ecx .text:7C9C60A2 mov ebx, edx .text:7C9C60A4 mov edx, [ebp+4] .text:7C9C60A7 mov eax, [ebp+0] .text:7C9C60AA .text:7C9C60AA loc_7C9C60AA: ; CODE XREF: sub_7C9C609E+19j .text:7C9C60AA mov [ebx], eax .text:7C9C60AC lea ecx, [edx+10001h] .text:7C9C60B2 lock cmpxchg [ebp+0], ebx .text:7C9C60B7 jnz short loc_7C9C60AA .text:7C9C60B9 .text:7C9C60B9 loc_7C9C60B9: ; CODE XREF: sub_7C9C609E+24j .text:7C9C60B9 push eax .text:7C9C60BA mov eax, edx .text:7C9C60BC lock cmpxchg [ebp+4], ecx .text:7C9C60C1 pop eax .text:7C9C60C2 jnz short loc_7C9C60B9 .text:7C9C60C4 pop ebp .text:7C9C60C5 pop ebx .text:7C9C60C6 nop .text:7C9C60C7 nop .text:7C9C60C8 nop .text:7C9C60C9 nop .text:7C9C60CA nop .text:7C9C60CB nop .text:7C9C60CC nop .text:7C9C60CD retn .text:7C9C60CD sub_7C9C609E endp .text:7C9C60CD .text:7C9C60CD ; ---------------------------------------------------------------------------