Content Type
Profiles
Forums
Events
Everything posted by FranceBB
-

Last version of VLC that works with KernelEx?
FranceBB replied to bob_smith's topic in Windows 9x/ME
Well, without KernelEx, VLC 0.8.6 is the last supported version, while for the K-Lite Codec Pack (LAV Filters + MPC-HC) the last supported version is 2.69 which includes MPC-HC version 6.4.8.7 -
Yes, apologies, I see how they can be counterintuitive without an explanation. The download page I showed is where the roytam1 publishes the builds of his browsers, which are forked version of common browsers. As a straight on replacement for Firefox, you can go with Basilisk (Serpent) from the list of builds, which is exactly an XP compatible Firefox fork by roytam, nothing more, nothing less. Other browsers like Palemoon are XP compatible forks of other Palemoon which in turn was a Firefox fork. I personally use the company oriented x86 non public builds of Chromium 108 ESR (yes, on XP, not-so-recently upgraded from Chromium 92 ESR) which I'm very lucky to receive on a regular basis, but whenever I need to browse the web with something else I use Palemoon (which ain't great, but it gets the job done unless you wanna stream some DRM protected content). Some other friend of mine use Basilisk (Serpent) which is alright. To put this into context, Chromium 108 ESR vs Palemoon 28 (roytam1):
-
That's weird. Windows properties should also show 16GB. Are you actually using One Core API or some other patch? This is a screenshot from December 2020, during the pandemic, when I upgraded to 64 GB of RAM: Which browser are you using? Are you using the builds from here? http://rtfreesoft.blogspot.com/search/label/browser Welcome to adulthood. And I'll tell you a secret: it will just get worse once you'll get to the point of having a job and going to the office every single day with as little as two weeks vacation per year that you won't really enjoy as you're an engineer so they'll be calling you for literally any little thing that happens to any of the systems you either made/coded or that you manage.
-
@AstroSkipper yep and as they said although the three 0 day vulnerabilities were then patched by Microsoft too, if a new 0 day vulnerability comes out they will try to patch it and I'm pretty damn sure that Microsoft won't release a patch this time around given that support ended in summer 2019. Besides, as they said, they also address vulnerabilities in other software which wouldn't necessarily be possible to update while retaining XP compatibility. This is an example of the patches that have been actively applied to my system as I opened some programs or did some other things that required them: As you can see, it kept me safe from known CVE in Java, WinRAR and RDP. There are other patches there which have never been applied, but still, it's nice to have and although I'm using the Pro version you can safely use the free version too which is a very valid alternative. Well, although a home user won't probably be exposed to some of them, we gotta keep in mind that Windows XP derived OS are still widespread everywhere mostly 'cause they were tied to hardware in embedded systems and also 'cause they were running software that would otherwise be incompatible with newer version of Windows. As result, it's not really uncommon for companies to still have Windows XP / Windows Embedded or Windows Server machines still up and running, either on bare metal or on VMs. In a business context those can be very valid points.
-
This is actually true, so I'm gonna try to change the trend a bit here with what we know. Essentially, there are threats out there and they can definitely affect XP. Unfortunately, Windows XP doesn't receive updates any longer and the threats out there can either come from a third party program installed or from a known vulnerability. Let's start with the latter. One of the most common examples is with SMB shares. Unfortunately, Windows XP is limited to SMBv1, as we all know, and given that this is still supported by modern version of Windows (including Windows Server in companies) as a fallback, this is generally targeted by threat actors as a way to breach a system. As result, SMB has had lots of CVE in the past and luckily they've been patched, not for the "good heart of Microsoft towards XP users", but rather 'cause they were affecting Windows Server as well, which is why Microsoft is still pushing and pushing for administrators to disable them and I feel like one day they'll just stop allowing people to enable SMBv1 altogether and force the use of SMBv3. The second most common target is, of course, RDP. Now, the RDP implementation inside XP is quite old to say the least and not only it doesn't support features like the new codecs and high frame rate (like H.264 4:4:4 encoding) etc but it also has known open CVE that will never be patched by Microsoft. Those, of course, can (and will) be exploited by threat actors. Another security vulnerability comes from the very limited support by Windows XP in terms of encryption ciphers. As we all know, XP does support kerberos and XP Professional workstations can be added to a domain and talk to a domain controller. During the handshake XP will expose the list of the ciphers it supports and the server will "agree" on one, but the problem here is that XP only supports DES CBC and RC4 HMAC, both of which are not only outdated but have very well known security vulnerabilities. In other words, it doesn't support AES and by forcing DES or RC4 the communication with the ticket granting server and the domain controller along with the other machines connected to the network isn't really safe and threat actors can exploit those to pretend to be the user in the domain. Last but not least, there are known vulnerabilities coming from the use of old programs and one of the main focus is on browsers. As you guys are probably aware, pretty much everything is based on Chromium and therefore this is the most attacked browser. As result, there are lots of 0 day vulnerabilities and CVE open that are generally quickly patched by the community, however, given that XP doesn't receive official updates, we're left with the risk of using browsers with known security vulnerabilities. If we add this to the fact that older, backported, version of Chromium like M92 and M108 also run with the sandbox disabled (as it was never ported by anyone), this leads to the perfect recipe to a good disaster. This, of course, isn't limited to Chromium, but it also involves other programs, for instance, there are known vulnerabilities for Adobe Acrobat Reader XI, there are known vulnerabilities for the last version of Java running on XP and so on and so forth. This leads us to the question: what can you do to mitigate this? To which, the answer is: be careful on what you do and keep an eye on the processes running. Personally, on top of that, I like to rely on two main things: 1) Avast 2) 0Patch The benefit of both have been vastly discussed on other topics, so I won't extend those any further, but just to recap very quickly, Avast is not just an antivirus but it plays the role of a firewall and a sandbox as well among other things, while 0patch can be used to address known vulnerabilities as a remedy for the lack of security updates. Last but not least, to the question "is the Windows XP user base actually 0?" the answer is: "it depends on how that statistic is counted/interpreted". I think that for the overwhelming majority of the people in this forum the answer would be: "Do you have XP installed and do you use it regularly?" -> Yes "Is XP your only system?" -> No
-
Yep, I use Total Commander myself for the same reason: renaming lots of files. It's very handy and I've been using it for years and years. On XP in particular, I also use it to transfer large files from a network storage to another 'cause it gives the speed and detailed info on how much data has been transferred. On modern Windows this is included in the transfer window, but on XP without Total Commander I would only have the simple progress bar filling up from left to right, which offers no info whatsoever.
-
Yes, it is still working, the problem isn't IrfanView per se but rather the plugins. Unfortunately, while the program still supports XP, some of its plugins were either made to leverage on native Windows API to decode some formats that simply don't exist in XP or they were compiled in a non XP compatible way. Luckily, I've encountered only a few isolated cases so far, but still... Same here, but only since early 2000 with Windows98SE. I didn't even know it existed before.
-

Universal VESA/VBE Video Display Driver for Win9x
FranceBB replied to Kdoasar's topic in Windows 9x/ME
Yep. Speaking of the latest driver, I also had a quite insightful discussion with the dev about a patch I was totally unaware of: https://github.com/JHRobotics/vmdisp9x/issues/2 -
What do you guys use to come to MSFN? (Or rather, do you come to MSFN with 98 at all?) I mean, Retrozilla isn't really usable nowadays.
-

Universal VESA/VBE Video Display Driver for Win9x
FranceBB replied to Kdoasar's topic in Windows 9x/ME
For those who don't get automatic notifications (you should really enable them on GitHub to receive emails): the author published a new version. I've just installed it. Works like a charm. -
Well, I really don't know whether it counts or not, but the BBC wrote an article 7 days ago about the increasing number of accidental phone calls to the police now that Android has released a new feature in which if you press the power button 5 times it will send an emergency alert to your emergency contacts and will also call the police for you. https://www.bbc.com/news/technology-65962942 The article has a picture at the very beginning which depicts a police station with operators monitoring incoming calls and on the computer you can clearly see the Windows XP start button with the classic Luna theme: Of course, although the article was released as little as 7 days ago, we don't know whether the picture used is a stock photo or if it's a recent one and they're still using XP to run legacy stable software, this is why I said "I don't know if it counts" at the very beginning.
-
Old story. Besides, it wasn't the antivirus, but a "product" called "Avast Secure Browser" which is a chromium fork and as such it doesn't work on XP. That, of course, used to track everything and give data to third party for analysis as long as you opted in to share your info, however Avast wasn't aware that the third party was also reselling the data instead of using it for research and to make transactions safer (yes, in theory it was born as a browser on which you were supposed to make transactions like logging in to your bank account or use credit cards / debit cards on etc so that it was totally sandboxed etc etc etc). When the story came out, Avast dropped the contract with the third party. Since you're concerned about the antivirus itself, that program only shares data about the threats you find if you choose to send them up for analysis. It also shares a very limited amount of data, which can be increased if you opt in to the optional data sharing, but it's gonna be limited to how many threats you face every month, what your subscription is like and what OS you are running on what hardware etc so that they have some statistics that can be useful to make a better antivirus. For instance, think about polymorphic viruses. They're viruses whose code changes frequently so that - in theory - they will be able to do some damage before they're included in the virus definitions and detected. Avast of course has heuristics, so it might see that although a program isn't in the virus definition, such a program isn't signed and is behaving in a peculiar way, perhaps by accessing resources etc. It's a point based system and if the score adds up to a certain threshold, Avast detects it and blocks the program, thus asking you confirmation. Although this might lead to some false positives, it can also detect polymorphic viruses and, once you catch one of those viruses which is temporarily blocked, you can send it in for analysis and they will immediately add it to the virus signature database which every user will receive through the streaming updates immediately. All this is, again, if you "opt in", with the word "opt in" being the keyword here. Exactly. I remember talking about this a while ago, thank you for confirming.
- 910 replies
-
4
-
- Security
- Antimalware
-
(and 3 more)
Tagged with:
-
More like: "this exploit is also developed in Russia" LMAO Jokes aside, thanks for the info, but I don't really feel like using anything Russian made on my machine and I think it's the same for pretty much everyone here...
- 910 replies
-
4
-
- Security
- Antimalware
-
(and 3 more)
Tagged with:
-
If you're worried about an NSA backdoor, it doesn't have one, don't worry. Besides, the XP version won't be updated anyway (aside from getting the virus definition updates), so we're safe even though now the company is no longer the one it used to be...
- 910 replies
-
2
-
- Security
- Antimalware
-
(and 3 more)
Tagged with:
-
NNEDI3 through Avisynth. Works like a charm on XP, even the latest version.
-

Universal VESA/VBE Video Display Driver for Win9x
FranceBB replied to Kdoasar's topic in Windows 9x/ME
Thank you so much for this! It took me a while to make it work 'cause it was crashing at first, but then I realized that it was the VRAM size fault. If you exceed 64MB, the driver will lead to a blue screen (128MB) or a Guru Meditation crash (256MB), however, as long as you stick to 64MB, it will work like a charm in FULL HD 1920x1080 RGB32: This is the very first time that I see Windows98SE running in FULL HD... There's so much space... I'm not used to it xD For everyone running on a VM, this driver is definitely a must have, way better than the old SciTech driver and compared to the bear windows ones, it allows you to set 16:9 resolutions instead of being limited to 4:3 ones only. -
Too much specialized hardware for far too many years. XP is here to stay as long as the hardware they're controlling keeps going. Unfortunately, the sad reality is that those XP systems and their relative embedded variants will, inevitably, be replaced one day 'cause the hardware they're attached to (like fuel pumps, elevators, airplane docking etc) will die one day, however, given the very long expected lifespan of those systems and the cost it would have to replace them before they break down, I guess they're gonna stay here for a long time (and we will still be able to celebrate them, here in the Spotters Club. ).
-
Exactly. Luckily we're on an old version that won't get any changes anyway. I just hope they won't kill it. Ah and by the way, the merger has only been approved by the European regulator few days ago, so they were still effectively two separate companies. Anyway, it saddens me a bit to see avast end up in the hands of Symantec (which is actually broadcom). So now we have Piriform (Speccy, CCleaner etc), Norton, Symantec, Avira, AVG and Avast all under one single company, Gen Digital. P.s I saw the whole discussion about Kaspersky, but to be fair, the last thing I wanna do in this historical period is install a Russian antivirus on my computer. I mean... it's probably ok, but these days you never know...
-
I have, it definitely works on Fritzbox routers but I assume it works on other providers too.
-
Well, we can speculate a bit. Avast 4.8 was the latest compatible version for Windows98SE and was released in 2008. The definition updates went on 'till 2017, so this gives us 9 years of definition updates. Avast 18.8 was the latest compatible version for Windows XP and was released in 2018. Should it follow the same pattern as 98SE, we should get definition updates 'till 2027 at least. Yeah it's been tough for a number of reasons one of which was COVID. I was one of the people you heard about on TV that was hospitalized after taking the first dose of Oxford Astra Zeneca. The 2nd dose went fine (still Oxford Astra Zeneca) after taking stuff to avoid blood clots and the 3rd one (Pfizer Booster) also was fine. Then in December 2021 I caught COVID, had a miserable time despite being triple jabbed, spent Christmas and New Year alone etc. I don't wanna talk too much about all this, but yeah, pretty tough time...
-
Stupid question, but is it actually out of sync? I mean in the bottom right corner, if you check the date and time, is it the correct day, month, year and time? You can even set XP to sync the time with: time.google.com which, by the way, is a Stratum 1 source connected to a real Stratum 0 Atomic Clock.
-
There are some providers that are still using PPTP and L2TP like FastestVPN (not the fastest, unlike the name suggests, but still). Otherwise, you can use different protocols, for instance OpenVPN works just fine on XP, you just have to install the client (or rather an older version of the client). Alternatively, you can go for a different protocol like IPSec Xauth PSK by installing the Shrew Soft VPN Client which still runs on XP. As to the browsers, aside from Roytam's constantly updated forks, I'm currently using some special Long Term Support XP Compatible Chromium builds that my company receives as part of a special support, so I'm currently on Chromium 92, however it does have some pretty bad CVE, so I'm trying to use it as little as possible until the next update comes up. Lastly, when it comes to updates, the best thing you can do is to install 0Patch and call it a day as they will at least provide some level of protection against vulnerabilities that Microsoft didn't bother to patch after July 2019.
-
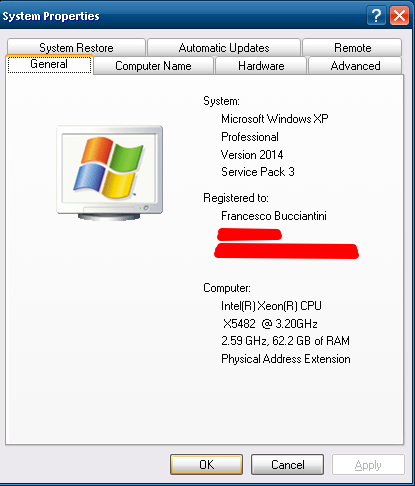
Hi there guys, long time no see. I'm still here and yep I'm still using XP, although with some compromises, but after all, aren't we all living with compromises? Anyway, I found an old installation of XP from several years ago (it was a notebook I used to use at university and then I gave to my grandma when I didn't need it any longer). She mostly uses it to transfer pictures from her compact camera to an HDD, closely following the steps I told her years ago and that she wrote down meticulously on a piece of paper. Anyway, I need to retrieve a value my system stored long long time ago, in 2009. Unfortunately I don't remember the value any longer, however I'm the admin of the PC and I can access the registry, the only "bad" thing about this is that the value is in 256bit BINARY_REG and not in plain text ASCII. I saw that you guys have already done this for a guy in the Windows98SE section, so is there a way to do the same on XP? The value is: de406b9e19e531dbe6beba290e765c8a28bd9553694c930cac3f857fdbdd5ad7