
riso
Content Type
Profiles
Forums
Events
Posts posted by riso
-
-
Look for the log file which say:
Hacker attached to system and the date and time, then look for the entry of:
Hacker detached from system and the date and time.
Obviously if someone where to enter the guys machine they would probably have enough nohow of how to clear any evidence of their being there.
Yeah, that was the point I was trying to make by raising doubts. You won't know for sure you were hacked, when you were hacked, how you were hacked; unless the hacker left a trace just to let you know you weren't smart enough to secure your system.
The question for the original poster is: How do you know you were hacked? What clues led you to think you were hacked?
We are offering him advice without knowing the details.
Yep. you are very right.
0 -
To solve lettering problems, you might want to actually try Letter Assigner, it does have a DOS version:
http://www.v72735.f2s.com/LetAssig/
do read the docs.
Some reference here:
http://www.msfn.org/board/index.php?showtopic=85729
jaclaz
Be carefull though because any programs which point to locations on the current drive letter may misfunction should that letter change.
0 -
From the information we were supplied, I can see no reason why the task would be performed by anyone other than an administrator and there shouldn't even be a need to use a script to deploy the command.In addition to that line of code you could add the following, which is part of a script i created to to run programs as an admin:However I'm sure your addition may be useful to those capable of breaking down your code for other tasks.
<Edit>
BTW, the 'wildcard' asterisk at the end of my line of code was a requirement!
</Edit>
It was snippet of code and not the full runas code. The snippet would allow him to enter the old information and the information to be replaced with and then click ok. Then when he clicks ok, the information he entered would be placed after the run code for the file and then the file would run with the information he entered.
I hope this makes sence? But basically, this code "should" work, but may need a little "tweaking" in places.
0 -
A Patron is a long-time, respected MSFN member who has contributed significantly to the community.
Ah ok, thanks for clearing that up.
What about Kidd0. I know he caused no end of issues with Ddos attacks on various tech communities in 2003. What was his problem?
0 -
Can you post a screenshot of the error you are getting please?
Also, what media are the files on? (CD, DVD, External Drive Caddy?)
This can all contribute to the issue you are experiencing
0 -
Where are these logs located?
I'm interested to find out.
start => run (or command prompt) eventvwr.msc
Look for the log file which say:
Hacker attached to system and the date and time, then look for the entry of:
Hacker detached from system and the date and time.
Obviously if someone where to enter the guys machine they would probably have enough nohow of how to clear any evidence of their being there.
0 -
All you need is a simple search and replace utility. Although this can be done using scripting, there are already some fantastic tools out there for this type of task. My suggestion would be to use rpl.exe.
Download the zip binary package, place the exe from the bin directory somewhere within your %path%. Within your console navigate to C: and run the following line of code:
Location=Inputbox("Please type the location of the file you wish to run below, then press OK.", "Runas")
If IsEmpty(Location) Then
Wscript.Quit
End If
Confirm=MsgBox("You entered the following location:" & vbCrLf & vbCrLf & Location & vbCrLf & vbCrLf & "Click ok to make the changes.", vbOkCancel+vbInformation, "Runas")
If Confirm=vbOk Then
Dim oShell
set oShell= Wscript.CreateObject("WScript.Shell")
oShell.Run "rpl -R -q -x .txt DAMREM004202 DAMREM004203 " & Location
Wscript.Quit
Else Confirm=vbCancel
Wscript.Quit
End IfThis should work, but may need to be played around with a little as i didnt have time to check it thoroughly.
0 -
I want to change the colour, background of Flash screen which is shown untill Welcome Screen get loaded.
It is in skyblue colour by default.
Whilst logged in as your account or the admin account, load tweak UI (search google for it, its from MS.
In Tweak UI, go to log in and select to copy all options currently set for the current user, so that would be background, theme etc.
Note, that through this you can also set the machine to auto login, which can be a security risk and is not recommended.
0 -
WOW! Gosh comes back and then GreenMachine shows up and throws him a bone.
What next?
Maybe the one known as kidd0 will return.

But GreenMachine is absolutely right. MSFN has become less interesting (post-wise) over the last few months, IMO. What used to take me about an hour to go through usually only takes me a few minutes. There are too many new threads being created that in which questions have already been answered in previous ones. Maybe a new project will do this forum some good (not that the current ones aren't exciting or useful).

What is a patron?
Kidd0 seems to ahve caused all kinds of trouble in 2003. What was that kids issue?
0 -
Nice to see such friendly staff on here! Quite refreshing

Ain't it true. All steadfast and voluntary.
Welcome to MSFN riso!
DL
Yep. I think i will like it here
 .
.How fast is this community growing? I mean on average how often do new users join?
0 -
To be honest with you, im not 100% sure. However, by my understanding, in XP you can do this reasonably safely and in Vista you can adjust your partitions completely, however in 95 -98 etc, i do not believe you can do this without 3rd party software, which even then can cause the partition to be unstable.
My advise would be to ensure you have a good backup of everything before attempting this, even if you where using xp or Vista.
0 -
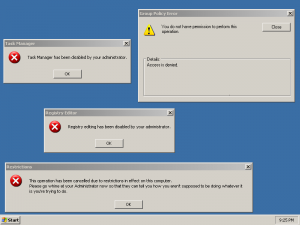
I just don't understand you people who run as admin just to boost your ego. It's dumb. If you have a good reason, fine, but just to make yourself feel good? I voted user, because that's what I'm logged into right now. But it's my computer, and I have an Administrator account, I just only use it when I need it. I tend to use the Runas... a lot, and also in command prompt, using
runas /user:Administrator "someprogram.exe".
I don't totally trust myself, because I like to mess around with things. Also, I don't want to get viruses and such, which are easier to install if you're an Admin. I have used System once or twice, but tend to avoid it like the plague, since I know that whatever I do there is permanent and very dangerous. I tell everyone not to run as an Admin on a regular basis, it's just not safe. But my limited account is really in between, thanks to my group policies. So I guess another answer should have been "somewhere in between".
 But anyone else who wants to use my computer, they get stuck using the account i called Public. It's very very locked down. Hah, can't change the password, can't use run or cmd.exe or regedit or control panel, can't change the display settings, very very locked up and drives some people crazy
But anyone else who wants to use my computer, they get stuck using the account i called Public. It's very very locked down. Hah, can't change the password, can't use run or cmd.exe or regedit or control panel, can't change the display settings, very very locked up and drives some people crazy  . Hee hee. They get lots of ego-deflating "You aren't privileged" dialogs, and "This action prohibited by your system administrator. Go whine at them now please." dialogs, too.
. Hee hee. They get lots of ego-deflating "You aren't privileged" dialogs, and "This action prohibited by your system administrator. Go whine at them now please." dialogs, too. I use a seperate account, but am in the admin group. Although you are right, you can run as.
There is also a script online that you can drag the file you want to run as an admin to and it will run that file. The only problem being that you have the admin password showing in plain text format, unless you encode the script, which is easily reversiable.
0 -
First thing is to learn not to use the term "hacked" to loosely.
The other day i "hacked" someones network, just to see if i could do it. However this was not really hacking. The wireless network had no security so i was free to connect and use their network connection for free. Then i browsed the computers connected to the network and saw 2 machines, one MAC and one PC. The PC was named the owners name (so i now have his name).
The guy was sharing out his music and documents, so i could easily browse to his documents etc and if i had been malicious, could have deletted everything.
It also gave me the chance to see pictures of him, his family and private arrangments for when he was going away (so i now know he lives in the area. If i spot him i could follow to see where he lives, and then later when i know he is away because of what i have seen on his machine i could break in, knowing he wont be back for a good long while.
He didnt have a password on the admin account so i had access to what i wanted.
Because i was just doing it to see what i could do and not to be malicious i simply left a message in a place i know he would see saying he has been hacked and should secure his network.
Sine then he has secured it with WEP encryption, which is better than no encryption.
However, to be secure as possible at a cheapest way try the following:
If using wireless use WPA2 and make the passcode something that no one could even guess. Make sure your not broadcasting your SSID and enable MAC connections so only machines with the MAC address' you say, can join the network.
Make sure you have a good firewall. A hardware firewall is better than any software firewall, but as that is not usually an option try some firewall software. Anything other than the standard Windows firewall is good. Zonealarm is usually the standard for most home users.
Make sure you have spyware software installed. I prefer spybot.
Make sure you have antivirus installed, a good free one is Avast!
Some people like to run multipul antivirus and spyware programs, but this will seriously impact your system performance.
Other than that, just use your initiative. Dont exept files from people you dont know or dont trust etc. Common sense things really.
0 -
Hi, since Microsoft has removed the Apple Talk protocol I would need a replacement.
I found a commercial version where the demo didn't even work with OS X 10.4.9
Is there a free version of Apple Talk available for Windows XP ?
I have searched but cant find any free ones. I found one that looks like its ok, but its a demo that only works for 180 minutes before you need to reboot.
0 -
Of course mate, welcome to the board!

Cheers mate.
Nice to see such friendly staff on here! Quite refreshing
 0
0 -
Sorry everyone. Just seen the "Im New Here" forum. Great start huh!

Any chance someone could move this for me please?
Cheers.
0 -
Hey everyone. Im new to the forums and though i should introduce myself.
My name is Rich, however as that has been taken i have created an account under my Slovak name of Riso.
I hope to stick around the forums for a while and hopefully watch it as it grows over time as well as hopefully bring some extra knowledge to the place and help people out whilst here.
Anyway, thats it for me in a nutshell.
Where are a majority of you guys from?
0

q05h q011y
in General Discussion
Posted
http://www.dreamincode.net/forums/lofivers....php/t7192.html
Your site is mentioned there too. His real name was Kenny Pollock. I think the lads at Neowin traced him and got all the info they could on him, including his mothers name, his address, his picture etc.
I just dont know what was up with him, why and how did he do these things?