Leaderboard
Popular Content
Showing content with the highest reputation on 09/26/2020 in all areas
-
Yes, I did implement it. And it should be one of the few stable functions, as it doesn't call outdated ntdll functions that others do (banking on ntext x86 to fix that though!). Though you don't have to replace your main kernel32.dll in this case. The addition of a string to the registry and a .local file in the Windows Defender folder along with my kernel32 should suffice.3 points
-
New build of Serpent/UXP for XP! Test binary: Win32 https://o.rths.ml/basilisk/basilisk52-g4.6.win32-git-20200926-ef27fbe-uxp-e0bda2246-xpmod.7z Win64 https://o.rths.ml/basilisk/basilisk52-g4.6.win64-git-20200926-ef27fbe-uxp-e0bda2246-xpmod.7z source code that is comparable to my current working tree is available here: https://github.com/roytam1/UXP/commits/custom IA32 Win32 https://o.rths.ml/basilisk/basilisk52-g4.6.win32-git-20200926-ef27fbe-uxp-e0bda2246-xpmod-ia32.7z source code that is comparable to my current working tree is available here: https://github.com/roytam1/UXP/commits/ia32 NM28XP build: Win32 https://o.rths.ml/palemoon/palemoon-28.10.2a1.win32-git-20200926-9f56811e0-uxp-e0bda2246-xpmod.7z Win64 https://o.rths.ml/palemoon/palemoon-28.10.2a1.win64-git-20200926-9f56811e0-uxp-e0bda2246-xpmod.7z Official UXP changes since my last build: - Isse #1224 - revert change to unbust debug builds. (5ad0a15f6) - [no issue] Fix whitespace (no code change) (04ccc4b12) - [SVG] Only fire the SVG onload when scripting is enabled and allowed (4d999e03a) - [dom/media] Use an atomic for mInputDeviceID to avoid potential race (aecdb2830) - [webaudio] Keep track of whether the HRTF database has already been loaded. (f5e5b5c32) - Issue #1655: Update MediaQueryList to the current draft spec. (388b9c802) - Output webidl filenames as they are processed, for real this time. (c14e7d70f) - Issue #1656 - Part 1: Nuke most vim config lines in the tree. (a680bdc63) - Issue #1656 - Part 2: Unmangle some unfortunate UTF-8 victims. (7572f3718) - Issue #1656 - Part 2b: Unmangle one more lost little UTF-8 victim. (5d97621bb) - Issue #1656 - Part 3: Nuke more vim config lines in the tree. (528b88d70) - Issue #1656 - Part 4: Tackle *.idl, *.css, *.ipdlh, *.webidl, *.cc (18ea98f7a) - Issue #1656 - Part 4: Manual cleanup (7523b9ea0) - Issue #1656 - Part 6: Clean up the build files (d5a2c45aa) - Issue #1656 - Part 7: Nuke vim config lines in JS (0c3bd2b10) - Issue #1656 - Part 8: Devtools and misc. (4a42352e6) - Issue #1656 - Part 9: Single-line-comment style. (6b9f2095a) - Issue #1656 - Part 10: Manual cleanup. (e0bda2246) Official Basilisk changes since my last build: - [downloads] Stop using referrers as sources (ef27fbe) Official Pale-Moon changes since my last build: - Back-end branch pointer update (unstable 2020-09-18) (b4943fc3c) - Issue #1744 - Add pref to ask for master password on application start. (04cd94da7) - [no issue] Whitespace fixes. No code change. (19f9cd83c) - [downloads] Stop using referrers as sources. (9f56811e0)3 points
-
2 points
-
2 points
-
That hack is essentially the same we used on XP: by keeping Engine Version 1.1.15800.1, we were able to continue updating up to the *.vdm v. 1.293.2807.0... then the next *.vdm files required a newer engine version and game over it was. But, from that period just before game over, @heinoganda had cobbled up an automated updater that download the the new definitions, replaced the engine by the last one working and put all files in their proper place, therefore helping more people to keep their MSE up-to-date up to game over, and I bet he sure might be able to modify that tool for the Vista community to enjoy the last leg of their MSE/WD more confortably. In case he doesn't ping this theread soon, do send him a PM. I'm sure he'll be delighted to be of help. Ceterum censeo Decimum delendum esse!2 points
-
@dencorso: You probably missed reading ... and the 3 following posts (exchange between me and @Vistapocalypse ), especially this: Historical progression of facts: 1. WD/MSE on Vista stopped being update-able directly from Windows Update (or via their integrated [manually] "Check for Updates" feature [which also evokes WU]) in the start of July 2019, when Microsoft changed the WU delivery infra to employ only SHA-2 endpoints (the SHA-1 ones were still on-line at the time...) 2. WD/MSE users on Vista had to turn to manually fetching files (for 32-bit OSes) mpas-fe.exe/mpam-fe.exe and running those to get the definitions of their M$ antispyware/antimalware "solution" up-to-date; these standalone files (links of which can be found on http://www.microsoft.com/en-us/wdsi/defenderupdates ) were, at the time, still dual-signed (i.e. both SHA-1+SHA-2 code signatures), so running them and installing updated defs was working.... 3. Towards the middle of October 2019, M$ stopped dual-signing those files (as well as their "ingredient" files), updated versions came as only SHA-2 signed; while running an SHA-2 only signed file is not necessarily a problem on Vista SP2 patched fully until its EOS (April 2017), it is in this case because the security app/OS has to verify the integrity of both the engine and updated definitions, before installing/integrating them... Without SHA-2 support in the OS, definitions for both WD/MSE would stay at their last dual-signed version and become stale in a few days... For posterity, the last dual-signed version of the off-line updaters was v1.303.1946.0, sharing the same mpengine.dll v1.1.16400.2 ... 4. To overcome [3], Vista SP2 users had to manually download and apply some KBs, targeting Vista's Server counterpart, WS2008, which bring SHA-2 support to the Vista OS; with that implemented, mpas-fe.exe/mpam-fe.exe [SHA-2 only] could properly update off-line their respective M$ security apps... NB: While the finer details were not very clear then, installing those SHA-2 enabling M$ updates on Vista has the following shortcomings: 4.1. Vista's Windows Update Agent (wuaueng.dll) is not being updated to its SHA-2 compatible version (M$ made it sure, via checks, that only the supported WS2008 SKUs got that privileged treatment, not poor EoS'ed Vista , despite them both sharing NT 6.0) , so connection to the new SHA-2 only Windows Update endpoints was/is not feasible; hence, WD/MSE could not connect to WU and be updated, again, via that route (as in the era before July 2019) ... 4.2. Vista's build number is changed to 6.0.6003 (SP2 = 6.0.6002) and that fact by itself made the WU SHA-1 endpoints give it the cold shoulder (this is OT in this discussion, but if available dual-signed Vista updates were not installed prior to the migration to SHA-2 support, these would no longer be offered via WU[SHA-1] 5. On the first week of August 2020, M$, as announced, shut down permanently their WU SHA-1 endpoints, cutting off completely Vista SP2 (with/without SHA-2 enabled support) and, I'm sure you know already, WinXP This had, of course, no bearing on either WD/MSE on Vista, but is at least related to this thread's title... 6. Closing in on recent times, v1.321.xxxx.0 was/is the last Vista compatible series of offline security updates (i.e. files mpas-fe.exe for WD & mpam-fe.exe for MSE); that series introduced engine file (common for both installers) mpengine.dll v1.1.17300.4; the last version in that series was 1.321.2290.0, released on Aug 28th 2020: Next series of off-line installers,1.323.xxxx.0, introduced new engine version 1.1.17300.5, but that one is no longer compatible with Vista/NT6.0: So Vista SP2 (with SHA-2 support installed) users of either WD/MSE can't manually update their definitions past v1.321.2290.0 (close to a month stale as it is...) M$ continue to advertise on their "Security Intelligence" () portal that they offer off-line updaters for "Windows Defender in Windows 7 and Windows Vista", and in fact I have sent them feedback informing them of the current predicament Vista users find themselves in, but they have yet to respond to my report... BTW, next series v1.325.xxxx.0 is closing in... PS1: There have been reservations expressed by members here, notably @Vistapocalypse, about the efficacy of running Vista's native WD or a considerably old, nag-free, version of MSE on Vista, and probably with good justification ... But this is NOT the gist of this post; so please refrain from such remarks here... PS2: As of this writing, I have employed a "hack" to keep updating my WD with defs past Aug 28th, which essentially boils down to keep using the last compatible engine, v1.1.17300.4, with definitions (files *.vdm) prepared for the non-compatible engine 1.1.17300.5; for now, it seems to just work; but the two engine versions are close enough/similar; I bet when a future engine version is released, say 1.1.19xxx.0, the new definition files it will come with won't be backwards compatible with v1.1.17300.4 - it'll then be GAME OVER! PS3: I haven't yet jumped into @win32's Extended Kernel, especially since I'm on a physical machine (so not on a VM I can experiment with), but also because I am on 32-bit, which presents special challenges towards the ExtKernel goal... If @win32 has already implemented TryAcquireSRWLockExclusive in his kernel32.dll wrapper, then that would be the ultimate solution for Vista users wanting to keep their WD/MSE installation updated with current definitions/engine! PS4: A new project has come to light (first mentioned here by @burd ) that restores WU[SHA-2] support to Vista SP2 past last August's breakage; the legality of that project is still unclear; also unclear is whether WU connection is being restored to either WD/MSE, so that the apps could (again) download updated definitions directly from WU (Vista Extended Kernel would be required for successful installation...). I guess that's it!2 points
-
New NewMoon 27 Build! 32bit https://o.rths.ml/palemoon/palemoon-27.9.7.win32-git-20200926-a291744c7-xpmod.7z 32bit SSE https://o.rths.ml/palemoon/palemoon-27.9.7.win32-git-20200926-a291744c7-xpmod-sse.7z 32bit noSSE https://o.rths.ml/palemoon/palemoon-27.9.7.win32-git-20200926-a291744c7-xpmod-ia32.7z 64bit https://o.rths.ml/palemoon/palemoon-27.9.7.win64-git-20200926-a291744c7-xpmod.7z source repo: https://github.com/roytam1/palemoon27 repo changes since my last build: - import changes from `dev' branch of rmottola/Arctic-Fox, and fix --enable-shared-js: - Bug 1164338 - Move styles markers to be generated in DoProcessRestyles rather than when the Flush_Style queue is flushed. r=smaug,heycam (b8f62d25a) - pointer style (c8d305ae5) - Bug 1150783 - Use a special JitFrame to record when LazyLink stubs are on the stack. r=h4writer (999a5d8dd) - Bug 1050500: Add SpiderMonkey API for reporting JavaScript entry points. r=shu (86b990918) - Bug 1050500 followup: Annotate js.cpp "Exit()" method as "override". rs=ehsan (023d67749) - Bug 1050500 - Add callee information to Javascript timeline markers. r=smaug (a5c078bc0) - Bug 1050500 - add fields to ProfileTimelineStackFrame; r=smaug (7852af842) - Bug 944164 - Move a bunch of file-related stuff onto an os.file object, creating aliases from the old names, r=jorendorff (a746506c0) - Bug 1167860 - Make sure unboxed expandos are traced during minor GCs if the original unboxed object is converted to a native, r=terrence. (40552cef4) - Bug 1168667 - Immediately convert unboxed objects to natives in PreventExtensions, and convert unboxed arrays as well as unboxed plain objects when required, r=jandem. (34e1c1267) - Bug 1172150 - Remove bogus assert. (r=bz) (1138519fa) - Bug 1165794 - Correctly handle getter/setters like methods everywhere. r=efaust (69a5cef61) - Bug 1164778 - Make |super.prop| work inside heavyweight arrow functions. (r=shu) (2eaffe30d) - Bug 1168750 - SharedStubs: (part2) Rename registers used by baseline stubs for use with shared stubs, r=jandem (db8080b41) - pointer style (ae0ef8c24) - fix spaces (0b5a0f55d) - Bug 1168864 - Use mayResolve hook for addprop stubs. r=bhackett (14f89c938) - Bug 1166678 - Optimize Array.prototype.slice in Ion, r=jandem. (978215128) - Bug 1169611 - Rewrite IonBuilder::getPropTryConstant to not require a singleton result. r=bhackett (22c6137ea) - Bug 1169611 part 2 - Unbox getprop/getelem inputs based on Baseline feedback. r=bhackett (dd3d50088) - Bug 1148009; [webvr] Move gfx vr code to gfx/vr; r=jrmuizel (d3e0a12c7) - Bug 1148009; [webvr] Split out gfxVROculus from gfxVR, refactor VRHMDManager; r=jrmuizel (393030b10) - Bug 1148009; [webvr] Add Quaternion class to Moz2D; r=jrmuizel (85165c87c) - Bug 1144674; Implement HAL support for ROTATION_VECTOR and GAME_ROTATION_VECTOR sensors; r=snorp (482211f00) - Bug 1148009; Add support for Cardboard (and other rotation-sensor based VR) in Firefox for Android; r=jrmuizel (d3f78e657) - Bug 1157835: Remove the MSVC_ENABLE_PGO flag from the build system. r=glandium (a5cc2bb8f) - Bug 1170534 - Remove Visual Event Tracer. r=dougt (720c1bbc3) - Bug 1169967 - Add a forward declare for MIRGenerator. r=nbp (81c6d0492) - Bug 1154435 - [nsDumpUtil] Refine nsDumpUtils::OpenTempFile to make this function more flexible. r=dhylands (ca1e07244) - Bug 1154435 - [nsGZFileWriter] Add one more mode for writing a GZFile (Create/Append). r=froydnj (d0cc62270) - Bug 1165456 - Start converting name-resolution code to act upon kinds, not arities. r=shu (1162554f4) - fix let (3ad7122ea) - Bug 1165456 - Handle a bunch of simple known-arity kinds, by kind, when resolving nested function names. r=shu (82da03c43) - Bug 1165456 - Perform name resolution on more nodes by kind, not arity. r=shu (214062efa) - Bug 1165456 - Perform name resolution on additional nodes by kind. r=shu (c13147c9e) - Bug 1165456 - More name-resolution conversion for arrays and (tagged) template literals. r=shu (f0cd596e8) - Bug 1165456 - Extra bits of name-resolution conversion. r=shu (51d1045d7) - Bug 1165456 - Final bits of name-resolution by kind. r=shu (57fca554e) - Bug 1165456 - Remove dead code performing name resolution by arity. r=shu (b03db072a) - pointer style (ab86d2ca7) - Bug 1149510 - Initialize the MachineState with safe-bad pointers. r=jandem (7d35b51c9) - Bug 1149510 - Don't try to read the result object when doing in-place debug mode bailout in a for-of loop. (r=jandem) (40c1e23a7) - Bug 1156115 - Apply Bug 1135629 changes to the non-ion jit. r=nbp (332a21041) - pointer style (fab908ba9) - Bug 1155468 - Fix Register::GetName typedef issue with clang. r=jandem (5c7758d85) - Bug 1176633 - Add more Operand constructors to the none backend. r=nbp (1557fe119) - Bug 1160672 - Part 1/2 - Import VIXL 1.5-1.6. r=jbramley (c84218fec) - Bug 1160672 - Part 2/2 - Add Mozilla VIXL modifications. r=dougc (1fd1c7443) - Bug 1160672 - Follow-up - Add missing </p> tag. no_r=me (f783f0793) - Bug 1160672 - Follow-up - Comment out unlanded header on a CLOSED TREE. no_r=me (f65a68eed) - Bug 1166037 - Import ARM64 Baseline changes. r=djvj (5ddb53015) - Bug 1166527 - Import ARM64 Architecture and Assembler. r=nbp (999380926) - Bug 1077014 - MacroAssembler API. r=h4writer (78f470fa5) - Bug 1077014 - ARM assembler support for for-effect atomics. r=mjrosenb (a78d1f786) - Bug 1077014 - MacroAssembler API, for MIPS. r=rankov (d22cb063c) - Bug 1077014 - optimize atomics for effect. r=h4writer (5a0bf089c) - Bug 1170758 - Make non-debug GraphSpewer constructor explicit. r=nbp (2b7c1a90b) - Bug 1176631 - Predeclare TempAllocator for non-ion platforms. r=nbp (73cd914a7) (a291744c7)2 points
-
All ~1810 functions in Vista's ntdll are exported from ntext and then forwarded to ntdll. Then I added a large code section to house RtlQueryPerformanceCounter and future functions. Only applications that call RtlQueryPerformanceCounter need to use this wrapper ATM. You can go into CFF Explorer -> Import Directory and change the entry for ntdll.dll under the "Module Name" column to ntext.dll. That can also be done with a hex editor, as the only likely reference to ntdll in the application would be in the import/delay load import tables. I just decided to compile it with the SSE2 switch. the best that VC++ offers (though it may not do much for a wrapper DLL, admittedly). Since most Windows 7+ applications probably need SSE2 to begin with, I don't see much harm in this decision.2 points
-
I compiled the NTEXT wrappers. SSE2 required. Note: the linkout.pl script makes an assumption that VC++ adds an extra underscore to functions that start with one. That is not true with VC++ 9, so such functions had one too many underscore for me. Though VC++ 6-8 may be different... The wrappers can be imported in place of ntdll.dll. New releases of kernel32.dll will refer to ntext instead of ntdll. The x64 ntext.dll has a modified RtlQueryPerformanceCounter, and it works good with Firefox 80. But there is a significant issue with the function in its unmodified form; it appears that any call to ntdll functions causes a "privileged instruction" error. So instead of calling the export-forwarded ZwQueryPerformanceCounter, I placed it directly in my dll as a subroutine and that fixed it. The x86 wrapper will need a little extra work since x86 ntdll is much farther behind W7 than the x64 ones.2 points
-
@max-h this installs 7.6.7600.256 for XP and Vista http://download.windowsupdate.com/windowsupdate/redist/standalone/7.6.7600.320/WindowsUpdateAgent-7.6-x64.exe http://download.windowsupdate.com/windowsupdate/redist/standalone/7.6.7600.320/WindowsUpdateAgent-7.6-x86.exe2 points
-
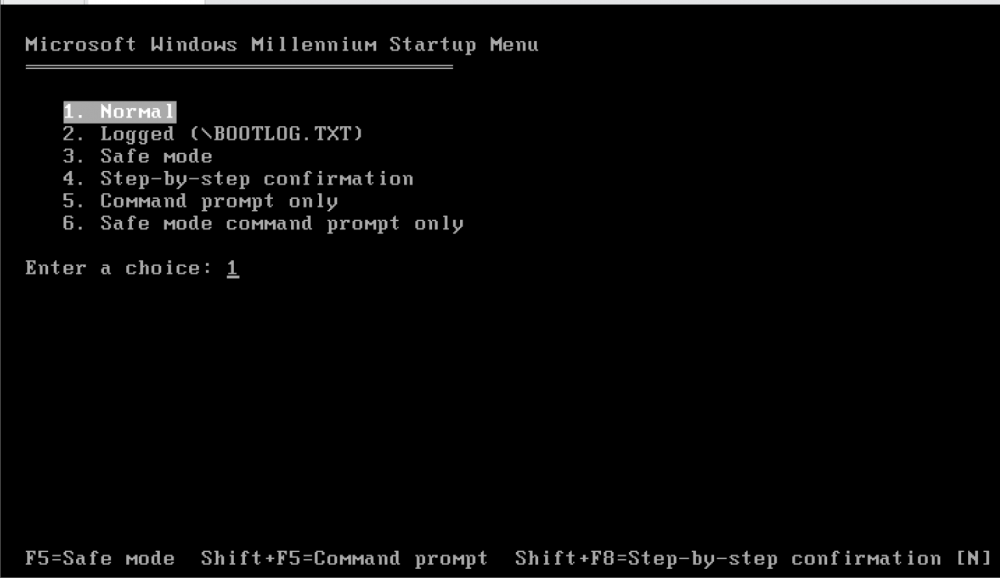
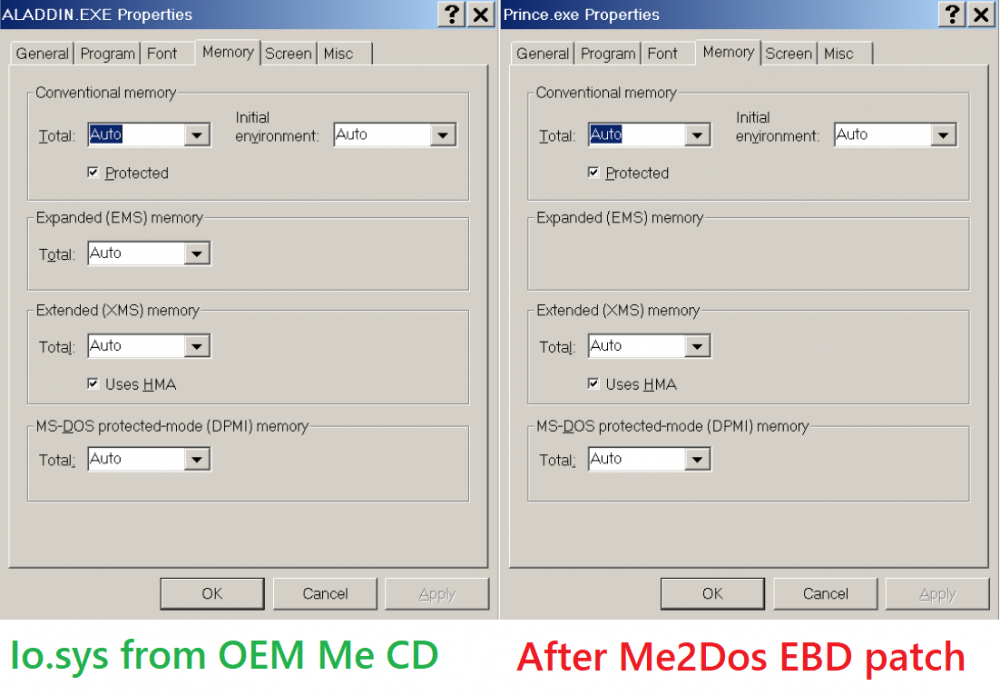
So I hope you guys know about some of the interesting things about Windows Me, at MSFN in fact, I found all this info in bits and pieces scattered over many threads so I am posting it in a single post. Also, there are many people here who already know it or are much smarter so ignore, I am only posting it for those still playing with this ancient OS in a VM or real old hardware. Hope it's not a problem: 1. Only the OEM version of Windows Me has hibernation support, retail doesn't. Also, OEM Windows Me CD is bootable. 2. It is common knowledge that Windows Me was patched to restore MS-DOS real mode. Io.sys, Command.com and Regenv.exe can be patched so it processes Config.sys and Autoexec.bat. That is old news. But this way of patching has a downside - you lose the nice white Windows Me boot logo (logo.sys that's inside Io.sys) because it takes the Io.sys/Winboot file from the EBD (Emergency Boot Disk). But instead what I recently learned (sure seasoned members and experts know it already) is after using the Me2Dos patch to modify Io.sys, command.com and regenv.exe or patching it yourself with a hex editor, if you take the Io.sys from Windows Me's Bootable CD (after it boots to DOS for Setup) or from the OEM Preinstallation Kit (OPK) that's there in tools\nettools\fac -> DTA files (which are actually CAB files on the CD) and overwrite the one in C:\ drive's root with this one, then this OEM Io.sys does have the nice boot screen and you can still boot to DOS if you want due to the patched Command.com and Regenv.exe. In fact you get the full set of startup options like 95/98 except "Previous version of MS-DOS". So, after you have patched Windows Me with the famous Me2DOS patch to boot like 95/98, you can replace Io.sys with the non-patched Io.sys from Me OPK or Bootable Me ISO, and you get the best of both worlds - boot screen as well as boot to DOS/startup files no longer ignored. 3. Another advantage of Io.sys from OEM CD vs EBD patch is Expanded Memory is available in Windows Me for DOS programs. 4. Finally, you need to make a few changes to startup files after the Me2Dos patch and replacing Io.sys from OEM CD, so that "Command prompt only" option works like 95/98 and also you don't get boot errors at startup when booting Windows Me with the "Normal" option. I'll explain why you need to modify files again after the Me2Dos patch. With this unpatched Io.sys from OEM CD Boot image/OPK, it always loads Windows Me even if you choose the "Command prompt only" option. This is because the Command interpreter line in startup files lacks the /P (permanent) switch. You just need to add the /P switch to config.sys. After you install the Me2Dos patch, it modifies Config.sys to add this line: shell=c:\command.com e:32768. Just modify it as stated below so you don't get a "File creation error" when booting. Like this: shell=c:\command.com c: /p /e:32768 (Note the correct use of /p switch in Config.sys is to list dir where command interpreter resides before it so you must add: c: before /p) Also this Io.sys will automatically load Ifshlp.sys so you can comment out the line in config.sys added by Me2Dos patch by a semicolon and lastly remove the line from Autoexec.bat: C:\WINDOWS\win.com as with the non-patched Io.sys from Bootable OEM CD, it will load Windows Me anyway when "Normal" startup is used. So you get all options working exactly like Windows 95/98: Normal, Logged, Safe Mode, Step-by-Step Confirmation, Command Prompt only (which does process your Config.sys and Autoexec.bat but boots to DOS only) and Safe mode command prompt only which bypasses them. 5. Another fun thing I recently learned is with the ORIGINAL Io.sys that Windows Me officially installs (not the patched one from Me2Dos/EBD patch and not the one from OEM Me CD), Windows Me does not actually need Win.com to boot! It is there only for compatibility but Win.com then loads vmm32.vxd which is the main file that switches from real-mode to protected mode. So you can do fun trick (not that there is any use of it): - Rename C:\Windows\Win.com to WinMe.com so Windows doesn't find it automatically - Rename C:\Windows\system\vmm32.vxd to vmm32.com. - Take Command.com from tools\nettools\fac -> DTA files and rename it to C:\Windows\system\vmm32.vxd Now when your PC boots with original unpatched Io.sys, it will only load Command.com Also you can directly load Windows Me by running: C:\Windows\system\vmm32.com. Or create a batch file in C:\ called Win.bat which points to C:\Windows\system\vmm32.com. That way it loads command.com. If you type, Win, it loads Windows Me. Note that I find this trick (#5) useless as original Io.sys bypasses startup files so there is no advantage of booting to DOS. Also if you use any different Io.sys, then vmm32.com will fail to load Windows Me directly. Let me know what you guys think. I think having access to MS-DOS almost like Windows 98 is awesome. The only thing that is still missing is Restart to MS-DOS Mode option but you can always dual boot between some version of DOS and Windows Me/DOS if you don't like "Command Prompt only" (Windows Me DOS 8.0).1 point
-
Get rvkroots.exe (Google), extract updroots.exe from it and put it in some folder. Get Curl: https://rwijnsma.home.xs4all.nl/files/curl/curl-7.69.1-mbedtls-zlib-win32-static-xpmod-sse.7z and unpack in the same folder. Then you just run the following batch file: ----------------------------------------------------------------------------------------------------------------------------------------- curl -O http://www.download.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authroots.sst curl -O http://www.download.windowsupdate.com/msdownload/update/v3/static/trustedr/en/delroots.sst curl -O http://www.download.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcert.sst curl -O http://www.download.windowsupdate.com/msdownload/update/v3/static/trustedr/en/roots.sst curl -O http://www.download.windowsupdate.com/msdownload/update/v3/static/trustedr/en/updroots.sst updroots authroots.sst updroots updroots.sst updroots -l roots.sst updroots -d delroots.sst updroots -l -u disallowedcert.sst cls ----------------------------------------------------------------------------------------------------------------------------------------- Done, takes 20 seconds to update, no complicated nonsense like they do in the XP forum.1 point
-
uB0-legacy now targets at least a Mozilla 45 compatible platform, so it remains compatible with FxESR 45, UXP-based browsers (NM28, Serpent 52.9.0), as well as Serpent 55.0/Moebius, but compatibility with Tycho-based browsers (NM27) is, sadly, lost... The very last stable version that is compatible with NM27 is 1.16.4.21 : https://github.com/gorhill/uBlock-for-firefox-legacy/releases/tag/firefox-legacy-1.16.4.21 I prefer myself uB0 to the AdBlock Plus family of content blockers (not least because the latter consume far more RAM), but it is true that v1.16.4.21 will remain onwards in an unmaintained state, while, OTOH, several useful filter lists now target recent versions of content blockers and, as such, employ more recent code formats/syntax that, unfortunately, the combination of NM27+uB0-1.16.4.21 can't cope with any more... So expect, over time, uB0-1.16.4.21 to become less efficient in its designated blocking tasks... I don't use myself NM27 quite often, but when I do (and for the specific sites I visit with it), uB0-1.16.4.21 serves me well for the time being...1 point
-
It's perfectly usable. To use it, just do something like this: The next kernel32 update will call ntext instead of ntdll as well.1 point
-
It seems that the native downloads popup page is also broken. Downward arrow in the toolbar (showing "Display the progress..." after mouse hover) does not respond to the mouse click to open current or previous downloads. In addition, menu item "Downloads Ctr+J" shows empty downloads page in the opened Library.1 point
-
1 point
-
NM28XP 32 bit 26/9 latest release breaks this add-on. https://addons.palemoon.org/addon/downloads-window/ downloads still work but the separate download window remains empty.1 point
-
Starting last August, the WSUSscsn2.cab file is being signed by M$ ONLY with a SHA-2 code-signature, high chances are it won't work with WUMT under XP ; it certainly chokes here under Vista SP2:1 point
-
I use Macrium Reflect Free for all my backup / cloning purposes on my work and at home. It's free for both comercial and personal users. Give it a try.1 point
-
You need extended Core , XP usb drivers and MTP Driver from google. @win32 if Microsoft open source it, it will be a boon to reactos. I believe they should as it is hard to put genie back into bottle once it is out.1 point
-
Thanks for the info, @Dave-H Someone over at Microsoft must have (temporarily, I bet... ) turned back on the SHA-1 endpoints for Microsoft/Windows Update, perhaps solely for the sake of delivering these last few Office 2010 updates on XP/Vista users ... I can also confirm that WU[SHA-1] is currently (Sept 26th 2020, ca. 01:35 UTC) back on Vista SP2 32-bit: Since I have installed SHA-2 support last October, I am currently on Vista build 6.0.6003; hence, I get offered nothing by MU/WU (but, OTOH, I don't think I have anything missing as far as Vista SP2 up-to-EoS [April 2017] updates are concerned... ) ...1 point
-
Believe it or not, I've just been offered two updates for Office 2010 through Automatic Updates, with a yellow shield in the system tray, after weeks of it repeatedly saying in the Event Log that it can't connect! I immediately went to the Microsoft Update website, and it successfully scanned for them and installed them, so it's not quite dead yet!1 point
-
Thank you. You know, I couldn't for the life of me make sense of replies like "The update is not applicable to your computer". https://answers.microsoft.com/en-us/windows/forum/all/windows-7-update-error-80244019/c220c4eb-115a-4703-b580-70b36f2c2b0e An answer in perfect accordance to article 4569557 was given, but no success??? So I tried to break Windows Update by removing KB4474419. Nothing happened. Ran Windows Update on a fresh virtual installation of Windows 7 SP1 - found updates without making any preparations... I know that both updates become indispensable going further, but Microsoft's claim of "Will be impacted" regarding Windows 7 SP1 is just plain incorrect. Windows 7 SP1 has experienced no change at all by the 2020 SHA-1 endpoint discontinuation. Also note that it just makes no sense advising to fix Windows 7 RTM and SP1 the same way. https://support.microsoft.com/en-us/help/4569557/windows-update-sha-1-based-endpoints-discontinued Regards, VZ1 point
-
Cool! Glad you found those changes useful. I've been using that script with the tweaks I made since and it's been hum-de-dum. I owe it to you though for putting the foundation together! Great installer!1 point
-
Hi I've adapted the "open with-6.8.6" add-on. get it from the Seamonkey add-on site to work with iceape-UXP . It is an add-on that allows you to open another browser or video player to view youtube videos externally to iceape-uxp. This allows you to open the videos on any other video hosting websites referenced in the "youtube.dl..." list. with mpv for xp . VLC also opens in iceape-UPX for youtube only with "open with 6.8.6", so you can avoid commercial ads and some youtube restrictions (age, etc.). I remind you of the instruction manual thread... https://msfn.org/board/topic/180462-my-browser-builds-part-2/?do=findComment&comment=1178761 open_with-6.8.6-iceape+tb.xpi1 point
-
Not at all. In full contrast to Microsoft's announcement at help article 4569557, Windows 7 SP1 remains unaffected whatsoever by the August 2020 discontinuation of SHA-1 based endpoints. Regards, VZ1 point
-
Microsoft cut a few days (or hours) ago I don't know precisely, the self-update of windows update agent. This means that WUMT will display "class not registered" until we manually update the agent. It's really the end this time. Fortunately, I found version 7.4.7600.226 as standalone package : https://support.microsoft.com/en-us/help/946928/information-for-network-administrators-about-how-to-obtain-the-latest As indicated, there is no standalone package for version 7.6.7600.256 but 7.4 works well.1 point
-
Well, as RainyShadow already mentioned, after 11 pages it's a bit late to suddenly convert a general topic into a very restricted one: From "old browsers" to: - only Firefox and Chrome - only on XP - AND only their LATEST version for XP that's neglecting "XP" again, and "latest version".... .1 point
-
But why? Did you thought these 11 pages were written to support only you? You should've said so in the OP...1 point
-
With all due respect, probably because the older software still performs perfectly and is licensed for life, while an upgrade would require a new and expensive license just for show purposes, since it adds nothing really needed. Do you think people are made of money? Moreover, you yourself told he's gotten his clinic renovated... for normal human beings, there's only so much money (more so in times of covid-19, on top of it)!1 point
-
this argentinian dentist is using Macintoch computers with XP ..... virtual machine ? what purpose ? https://youtu.be/c7udrrz9VMk?t=5151 point
-
RVKROOTS.EXE: KB2917500 https://support.microsoft.com/en-us/help/2917500/microsoft-security-advisory-improperly-issued-digital-certificates-could-allow-spoofing or the Internet Archive if the above link ever goes down or gets deleted: https://web.archive.org/web/20131215073232/https://support.microsoft.com/kb/2917500 (direct download: https://web.archive.org/web/20131216214109/http://download.microsoft.com/download/0/E/6/0E60F1EB-4E0A-4D3A-B4D1-20D9D405499A/rvkroots.exe) IMAPI_XP_SRV2003_x86.EXE: KB952011 The original page is dead, so you'll have to use the Internet Archive: https://web.archive.org/web/20121111064508/http://www.microsoft.com/en-us/download/details.aspx?id=19622 (direct download: https://web.archive.org/web/20121111064508/http://download.microsoft.com/download/4/D/C/4DC0907E-38FF-4CF6-A155-B45C4EF39C35/IMAPI_XP_SRV2003_x86.exe)1 point




.png.3c9dc4f3b1255c45b307f0e781486565.thumb.png.22664a2751ea68c4eca6477931bbc3b9.png)